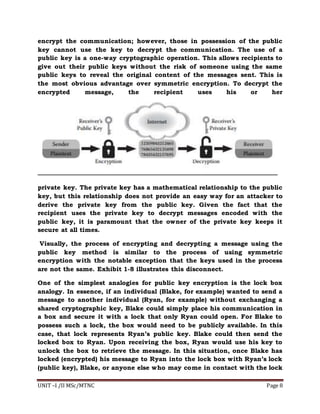
This document contains a question bank with answers related to cyber security. It discusses topics like the CIA triad of confidentiality, integrity and availability, authentication and authorization. It also defines terms like availability, integrity, non-repudiation and confidentiality. Examples are provided for different authentication factors like something you know, something you have and something you are. The document also discusses symmetric and asymmetric encryption, firewalls and the fundamentals of the domain name system.