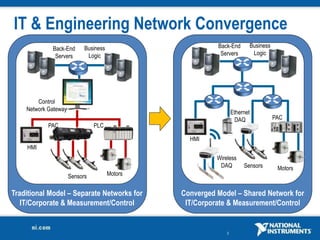
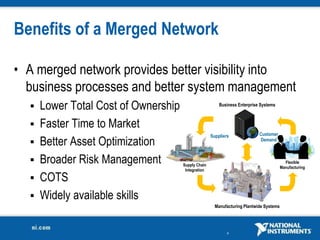
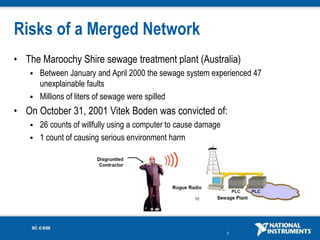
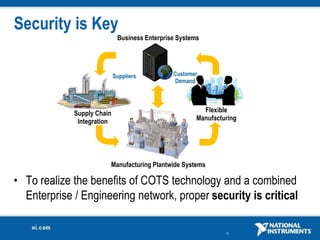
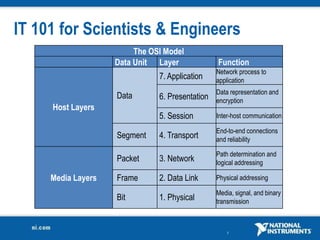
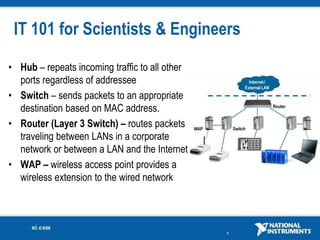
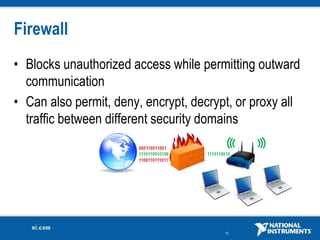
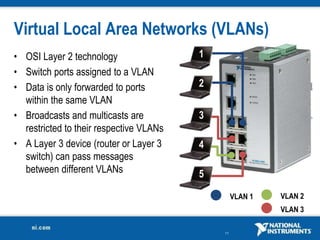
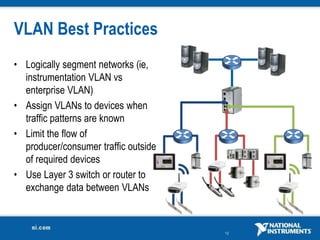
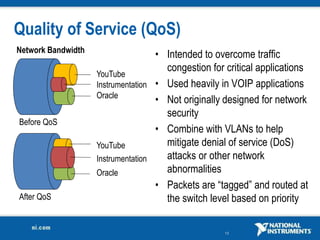
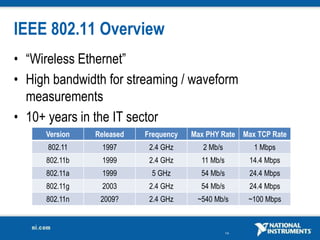
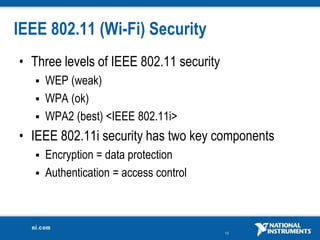
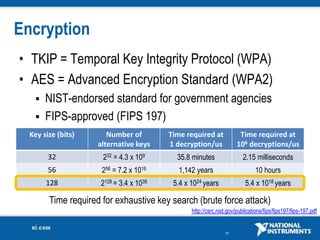
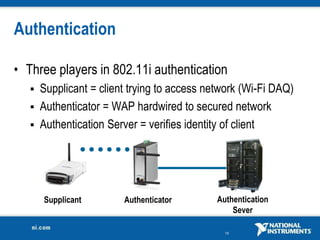
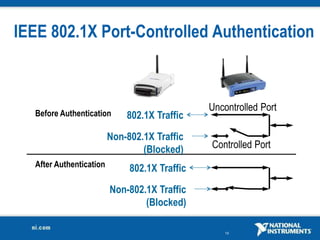
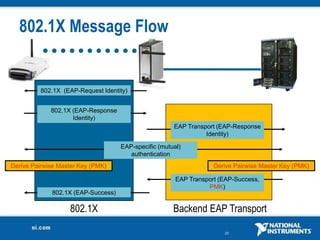
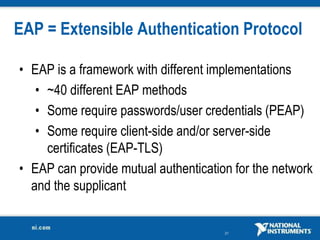
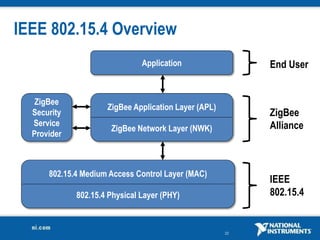
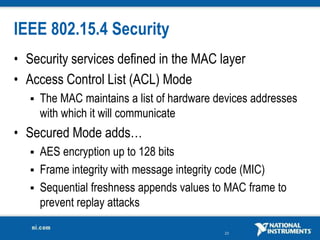
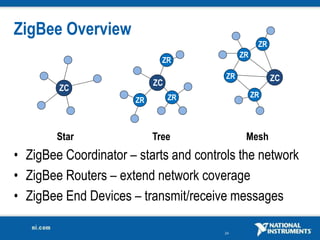
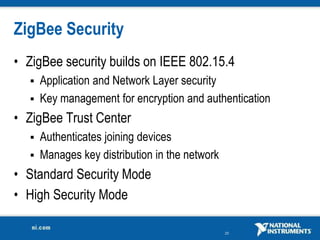
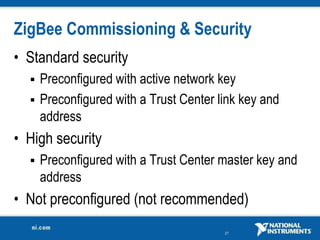
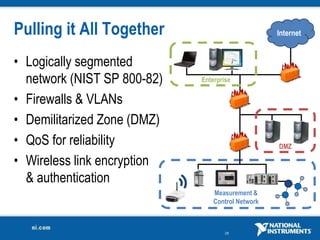
The document discusses network security considerations for merging IT and engineering networks. It provides an overview of common network security technologies for wired and wireless networks, including firewalls, VLANs, QoS, 802.11i/WPA2 encryption and authentication for wireless, and 802.15.4 security incorporated in ZigBee networks. The document emphasizes that properly implementing these security standards is critical to realizing the benefits of convergence while managing risks to process control and measurement systems.