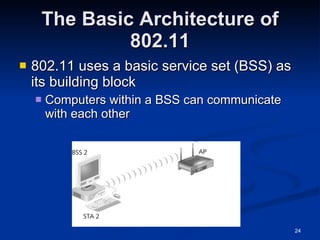
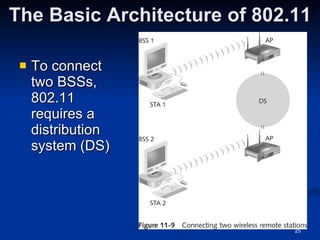
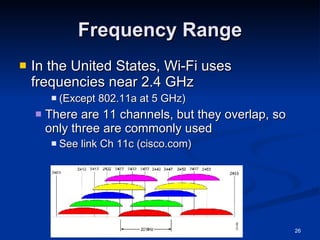
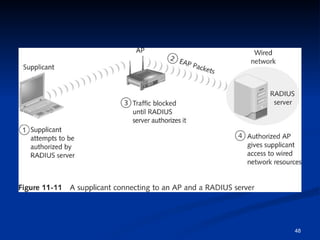
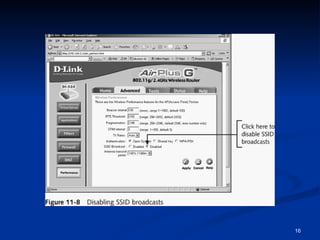
This document provides an overview of wireless networking standards and security. It describes wireless technology components like access points and wireless network interface cards. It explains wireless networking standards established by IEEE like 802.11b, 802.11g, and 802.11n. The document also covers wireless authentication methods including wired equivalent privacy (WEP), Wi-Fi protected access (WPA), 802.1X, and protocols like EAP, PPP, and CHAP. It discusses vulnerabilities of early security standards and improvements made by newer standards to strengthen wireless network security.




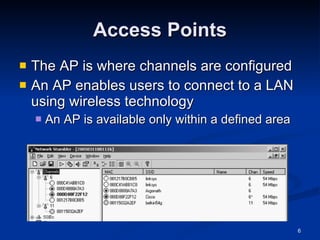

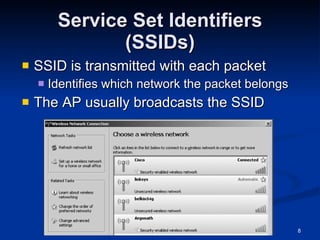

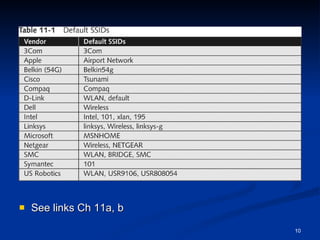



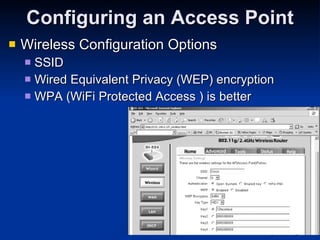




![IEEE: CCSF Student Chapter Next meeting: Thurs, Nov 6, 2008 in Sci 37, 5:00 pm Email [email_address] for more info](https://image.slidesharecdn.com/ch11-090816003223-phpapp01/85/Ch11-Hacking-Wireless-Networks-it-slideshares-blogspot-com-20-320.jpg)