This document presents an analysis of deception and countermeasures in the Android user interface. It discusses how malicious applications can use GUI confusion attacks to disguise themselves as other applications. It then analyzes such attacks using state exploration tools and proposes approaches for detecting malicious applications through static analysis. Finally, it discusses potential defensive mechanisms like establishing a trusted path for users to identify the actual application in use.






![GUI confusion Attack
7
Institute of Informatics Georg-August-Universitaet Goettingen, Germany
Department of Security Course: Security and Privacy in Smartphones
Category Attack vector
Drawn on top
UI-interception draw-over
Non-UI-interception draw-over
Toast message
App switch
StartActivity API
Screen pinning
MoveTastTo APIs
KillBackgroundProcesses API
Back / power button (passive)
Sit and wait (passive)
Fullscreen
Non-“immersive” fullscreen
“immersive” fullscreen
“inescapable” fullscreen
Enhancing techniques getRunning Tasks API
Reading the system log
Accessing proc file system
App repackaging
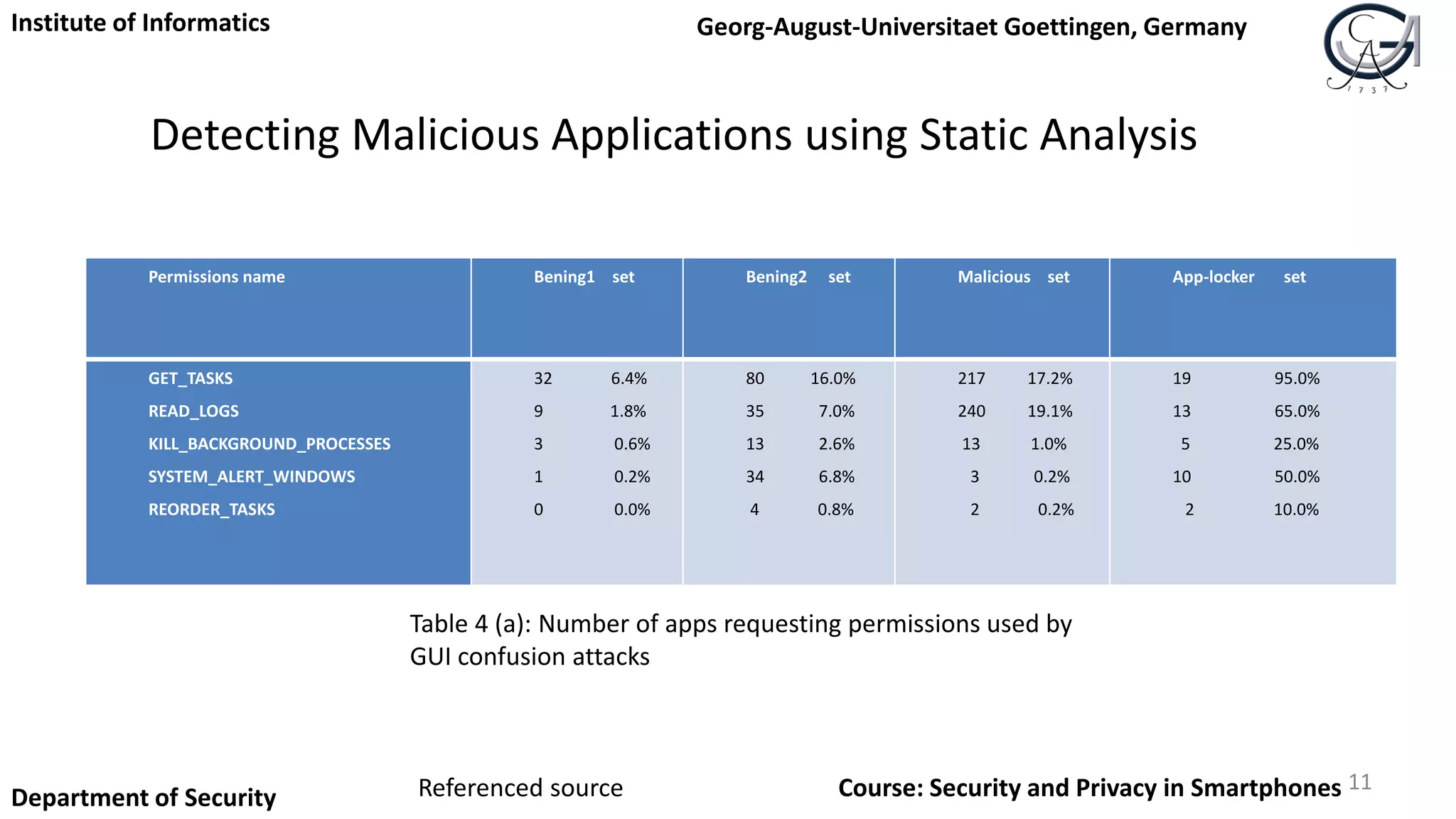
Table 1: [2] Attack vectors and enhancing techniques.
Referenced source
addView API
PRIORITY_PHONE flag
Click-jacking
Interesting exception
GUI mimic
Active and Passive
app
Drawn on top activity without permissions
Locks the specific app
REORDER_TASKS permissions
Other attack vectors used
User believe app switch occured, in fact, its
not
tabnabbing
SYSTEM_UI_FLAG_IM
MERSIVE
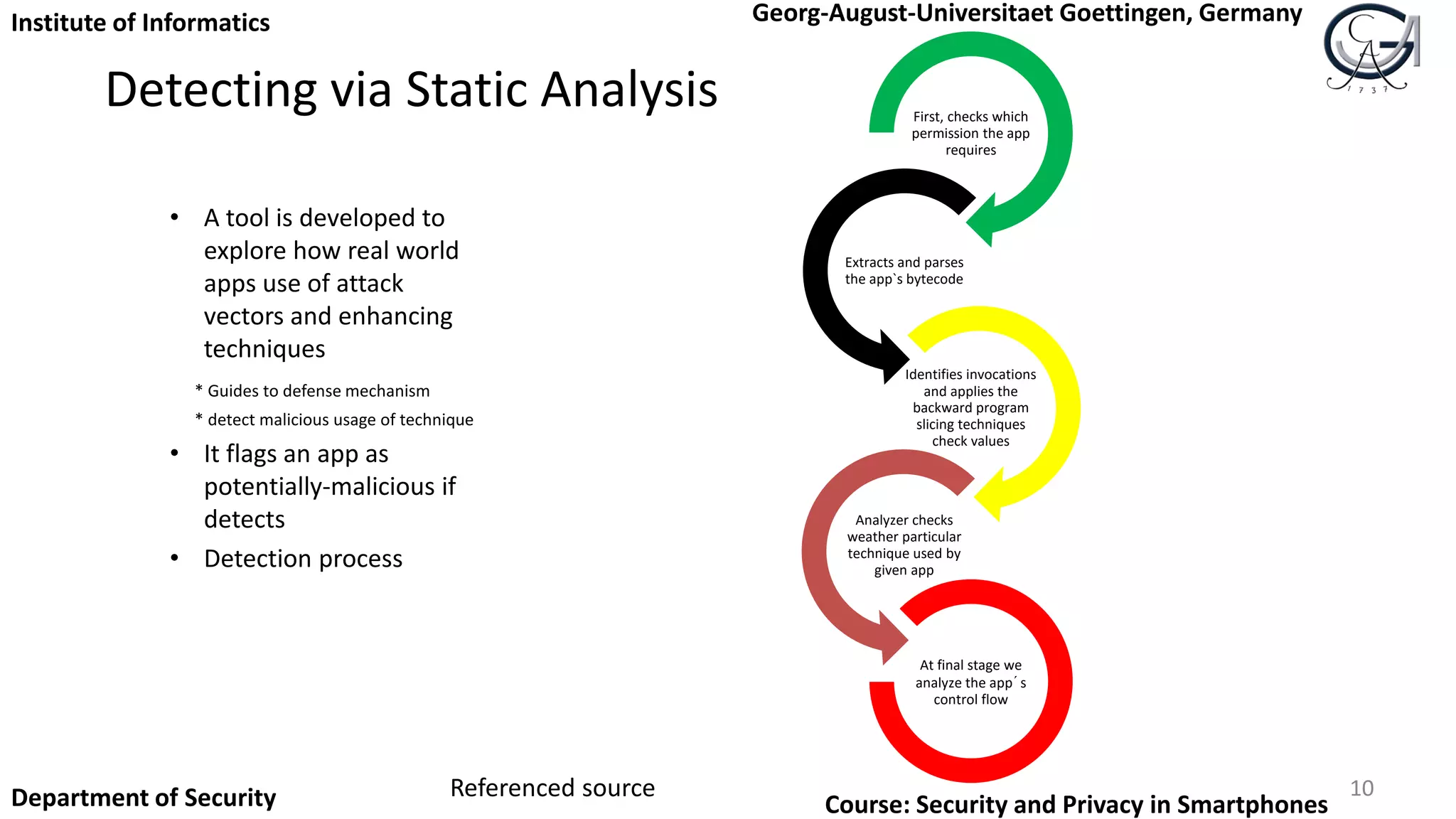
Techinque in detect how user
interacts with the system
GET_TASKS, name of the top Activity.
READ_LOGS
Retrive the list of app running by listing /proc
Process of modifying existing app](https://image.slidesharecdn.com/securityandprivacyinsmartphones1-151012154916-lva1-app6891/75/Security-and-privacy-in-smartphones-7-2048.jpg)
![State exploration tools
• Study how a main GUI APIs used to mount GUI confusion attacks
• Drawn on top even if belongs to different apps
1) entirly covers the device´s screen.
2) No permission accesing close or navigation bar.
A) Study of the “startActivity API“.
8
Institute of Informatics Georg-August-Universitaet Goettingen, Germany
Department of Telematics Course: Security and Privacy in SmartphonesReferenced source
Component type Active, Service, Content Provider, Broadcast Receiver
LaunchMode attribute Standard, SingleTop, singleTask, singleInstance
StartActivity flags MULTIPLE_TASK, NEW_TASK, CLEAR_TASK,
CLEAR_TOP_FRONT, SINGLE_TOP; TASK_ON_HOME
REORDER_TO_FRONT, PREVIOUS_IS_TOP
Table 2: [4] Component types, flags, and launchMode values tested by our tool](https://image.slidesharecdn.com/securityandprivacyinsmartphones1-151012154916-lva1-app6891/75/Security-and-privacy-in-smartphones-8-2048.jpg)
![State exploration tools
API exploration tools effectively helps to detect critical situaltions like “inescapble“ fullscreen
possibility.
B) Study of “inescapable“ fullscreen Windows
* Removing the SYSTEM_ERROR type.
9
Institute of Informatics Georg-August-Universitaet Goettingen, Germany
Department of Security Course: Security and Privacy in Smartphones
TYPEs TOAST; SYSTEM_ERROR, PHONE,
PRIORITY_PHONE, SYSTEM_ALERT,
SYSTEM_OVERLAY
Layout flags IN_SCREEN; NO_LIMITS
System-UI Visibility flags HIDE_NAVIGATION, FULLSCREEN,
LAYOUT_FULLSCREEN, IMMERSIVE,
IMMERSIVE_STICKY
Table 3: [4] Window types and flags
Referenced source
SYSTEM_ERROR
+
NO_LIMITS
Covers entire
screen in 4.3
version
Patch is used to
address this
problem
SYSTEM_ERROR
+
System-UI Visibility flags uses
“Immersive“ to create
“inescapable“ fullscreen is
introduced in Android 4.4
version
Same parameters are
verified in 5.0
version](https://image.slidesharecdn.com/securityandprivacyinsmartphones1-151012154916-lva1-app6891/75/Security-and-privacy-in-smartphones-9-2048.jpg)





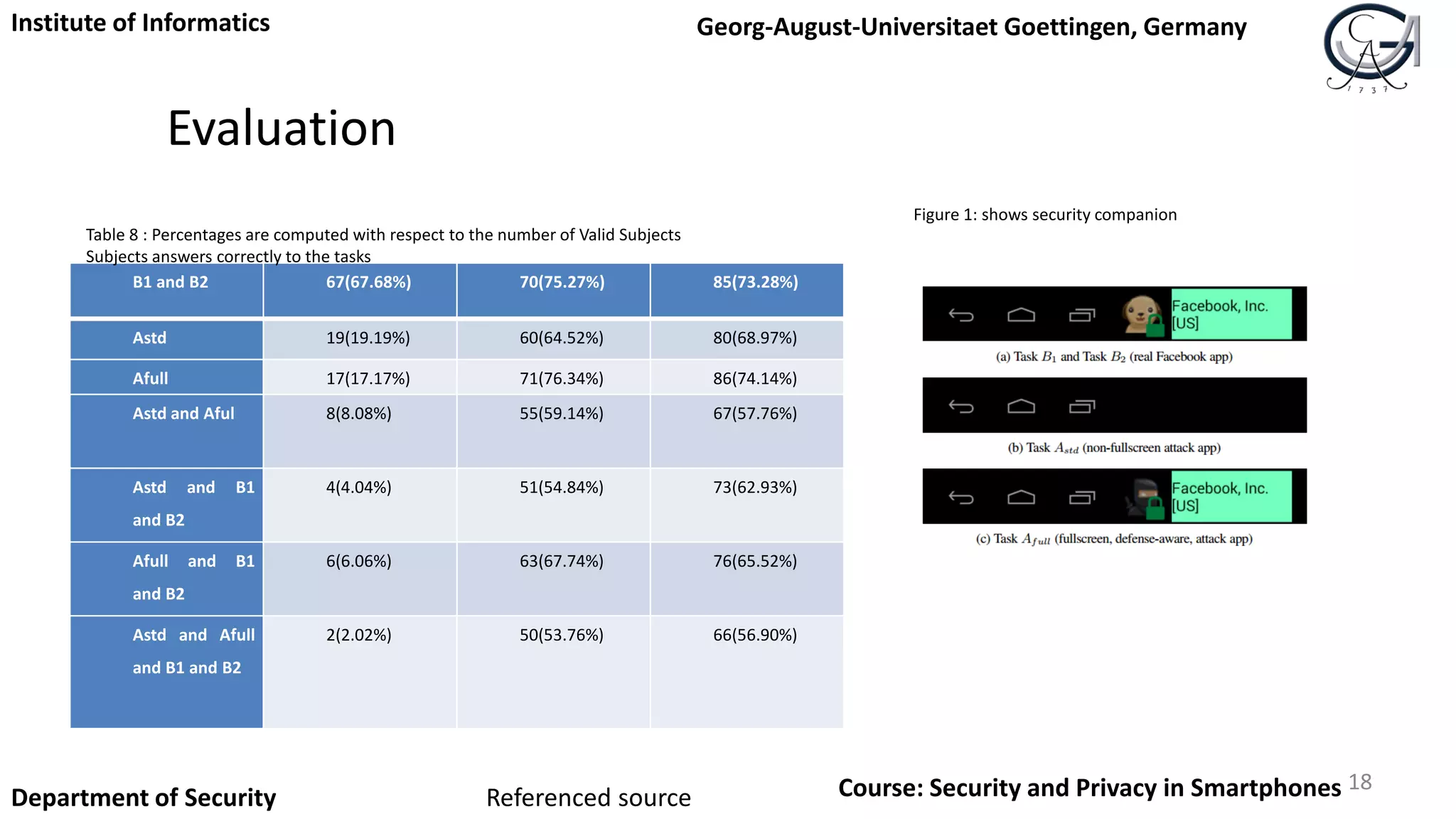
![Evaluation
17
Institute of Informatics Georg-August-Universitaet Goettingen, Germany
Department of Security Course: Security and Privacy in SmartphonesReferenced source
Group 1:
Stock
Android
Group 2:
Defensive
activity
Subject not
aware of
attacks
Group 3:
Defensive
activity
Subjects
aware of
attacks
Total
subjects
113 102 132
Valid
subjects
99 93 116
TABLE 7: [4] Results of the experiments with Amazon Turk
• The effectivness of GUI confusion attacks
• How helpful our defense mechanism to the
users in finding malicious apps](https://image.slidesharecdn.com/securityandprivacyinsmartphones1-151012154916-lva1-app6891/75/Security-and-privacy-in-smartphones-17-2048.jpg)

![References
• Bianchi, Antonio, Jacopo Corbetta, Luca Invernizzi, Yanick Fratantonio, Christopher Kruegel, and Giovanni Vigna.
"What the App is That? Deception and Countermeasures in the Android User Interface." (2015).
• Mann, Mr Ian. Hacking the human: social engineering techniques and security countermeasures. Gower
Publishing, Ltd., 2012.
• “Owasp,”[Online]. Available: http://www.owasp.org/index.php/index.php/Static_Code_Analysis
“tutorialspoint,”[Online].Available:http://www.tutorialspoint.com/android/android_application_components.htm.
• M. Niemietz and J. Schwenk, “UI Redressing Attacks on Android Devices,” Black Hat Abu Dhabi, 2012.
• A. P. Felt and D. Wagner, “Phishing on mobile devices,” Web 2.0 Security and Privacy, 2011
• T. Luo, X. Jin, A. Ananthanarayanan, and W. Du, “Touchjacking Attacks on Web in Android, iOS, and Windows
Phone,” in Proceedings of the 5th International Conference on Foundations and Practice of Security (FPS). Berlin,
Heidelberg: Springer-Verlag, 2012, pp. 227–243.
• TrendLabs, “Tapjacking: An Untapped Threat in Android,” http://blog.trendmicro.com/trendlabs-security-
intelligence/tapjacki ng-an-untapped-threat-in-android/, December 2012.
• Q. A. Chen, Z. Qian, and Z. M. Mao, “Peeking into Your App Without Actually Seeing It: UI State Inference and
Novel Android Attacks,” in Proceedings of the 23rd USENIX Security Symposium. Berkeley, CA, USA: USENIX
Association, 2014, pp. 1037–1052.
TrendLabs, “Bypassing Android Permissions: What You Need to Know,” http://blog.trendmicro.com/trendlabs-
security-intelligence/bypassing-android-permissions-what-you-need-to-know/, November 2012.
20
Institute of Informatics Georg-August-Universitaet Goettingen, Germany
Department of Security Course: Security and Privacy in Smartphones](https://image.slidesharecdn.com/securityandprivacyinsmartphones1-151012154916-lva1-app6891/75/Security-and-privacy-in-smartphones-20-2048.jpg)
![References
• S. Jana and V. Shmatikov, “Memento: Learning Secrets from Process Footprints,” in Proceedings of the IEEE
Symposium on Security and Privacy (SP), May 2012, pp. 143–157.
• S. Hanna, L. Huang, E. Wu, S. Li, C. Chen, and D. Song, “Juxtapp: A Scalable System for Detecting Code Reuse
Among Android Applications,” in Proceedings of the 9th International Conference on Detection of Intrusions and
Malware, and Vulnerability Assessment (DIMVA). Berlin, Heidelberg: Springer-Verlag, 2012, pp. 62–81.
• W. Zhou, Y. Zhou, X. Jiang, and P. Ning, “Detecting Repackaged Smartphone Applications in Third-party Android
Marketplaces,” in Proceedings of the Second ACM Conference on Data and Application Security and Privacy
(CODASPY). New York, NY, USA: ACM, 2012, pp. 317–326.
• W. Zhou, X. Zhang, and X. Jiang, “AppInk: Watermarking Android Apps for Repackaging Deterrence,” in Proceedings
of the 8th ACM SIGSAC Symposium on Information, Computer and Communications Security (ASIA CCS). New York,
NY, USA: ACM, 2013, pp. 1–12
• M. Weiser, “Program slicing,” in Proceedings of the 5th international conference on Software engineering. IEEE
Press, 1981, pp. 439–449
• CA/Browser Forum, “Guidelines For The Issuance And Management Of Extended Validation Certificates,” https:
//cabforum.org/wp-content/uploads/Guidelines v1 4 3.pdf, 2013.
• Andriod stackexchange,”[Online].Available:http://android.stackexchange.com/questions/31830/what-is-a-top-
developer-in-google-play.
21
Institute of Informatics Georg-August-Universitaet Goettingen, Germany
Department of Security Course: Security and Privacy in Smartphones](https://image.slidesharecdn.com/securityandprivacyinsmartphones1-151012154916-lva1-app6891/75/Security-and-privacy-in-smartphones-21-2048.jpg)