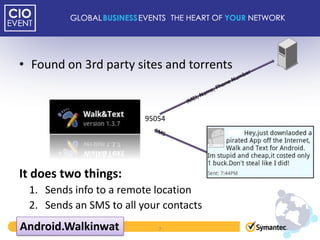
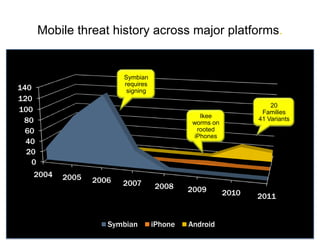
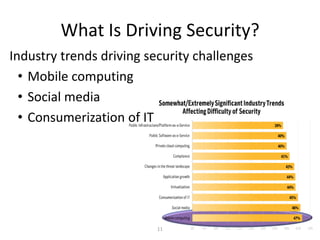
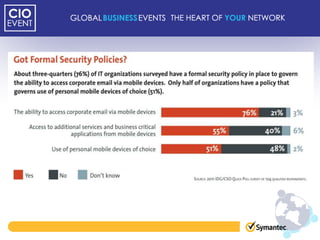
This document discusses mobile adoption and security challenges in 2012. It notes that mobile data usage has increased 4,000% and drivers for businesses include quick app development, employee productivity and cost savings. However, mobile use also presents security risks like malware, lost devices accessing private information, and blurring of personal and business data. The document examines trends in the mobile threat landscape and outlines the top mobile security practices for organizations, including protecting device information, authentication, and maintaining security policies.