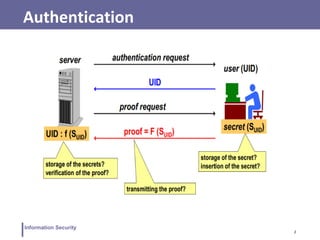
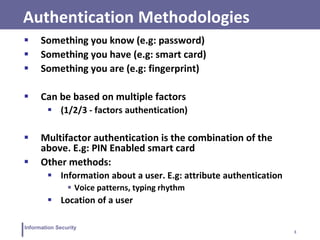
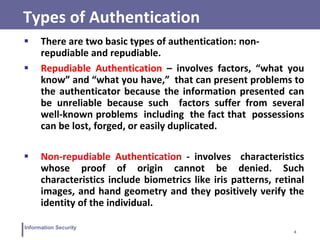
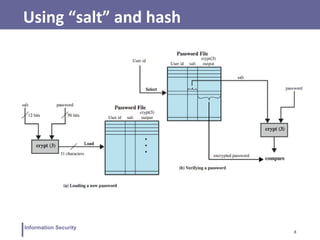
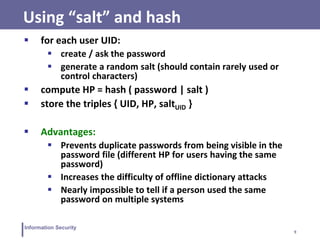
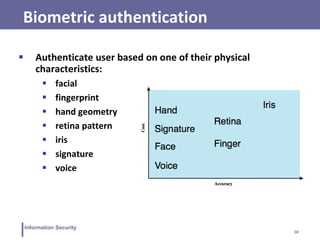
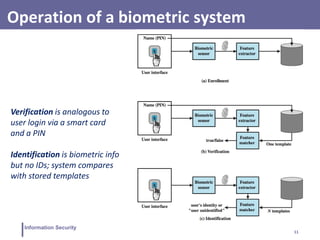
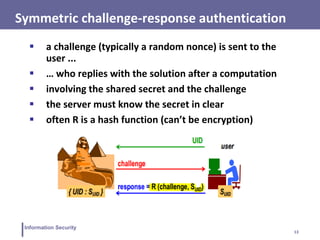
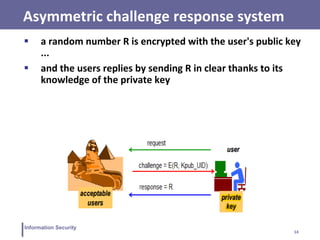
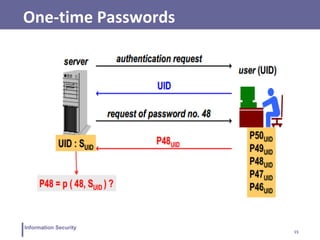
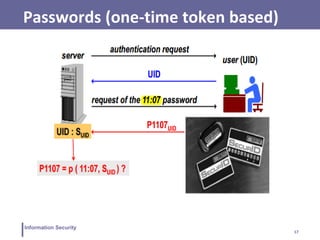
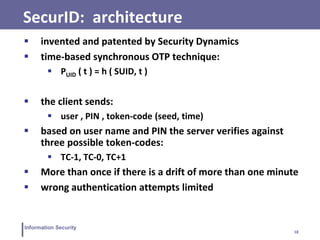
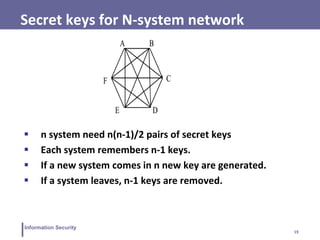
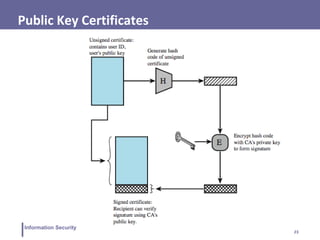
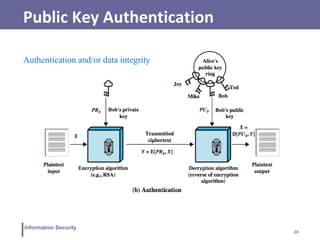
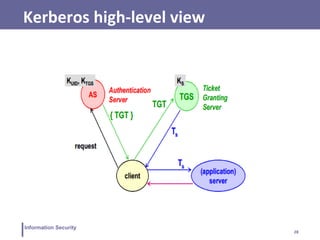
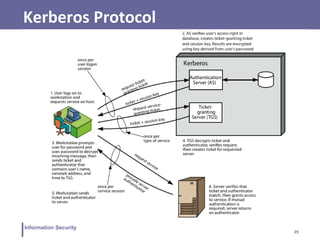
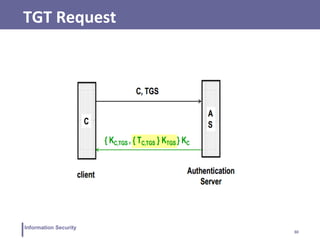
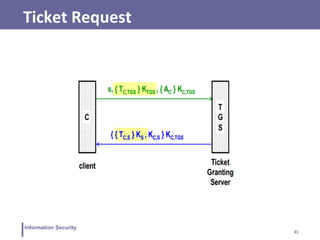
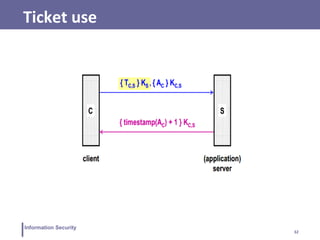
This document discusses various topics related to information security and authentication. It begins by defining authentication and describing common authentication methodologies like passwords, smart cards, and biometrics. It then distinguishes between repudiable and non-repudiable authentication and describes authentication mechanisms like basic authentication, challenge-response, and centralized authentication. The document also covers password-based authentication techniques like hashing passwords with salt, biometrics, one-time passwords, public key infrastructure, Kerberos, and other authentication systems.