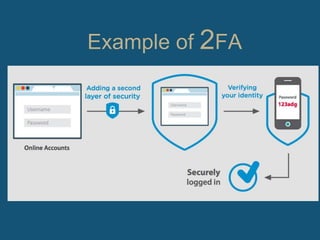
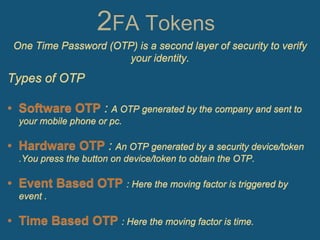
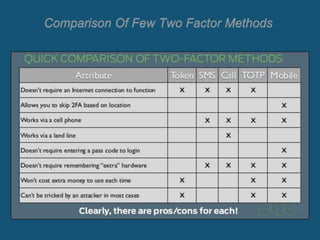
The document discusses two-factor authentication (2FA) as a more secure alternative to single-factor authentication using just a username and password. 2FA provides an additional layer of security beyond just one credential by requiring two separate factors, such as something you know (a password) plus something you have (a token, smart card, or biometrics). While 2FA is more secure, it can also be slower and require the user to have their second authentication factor available at all times. Popular services like Facebook and Dropbox have implemented 2FA options to better protect user accounts and data.