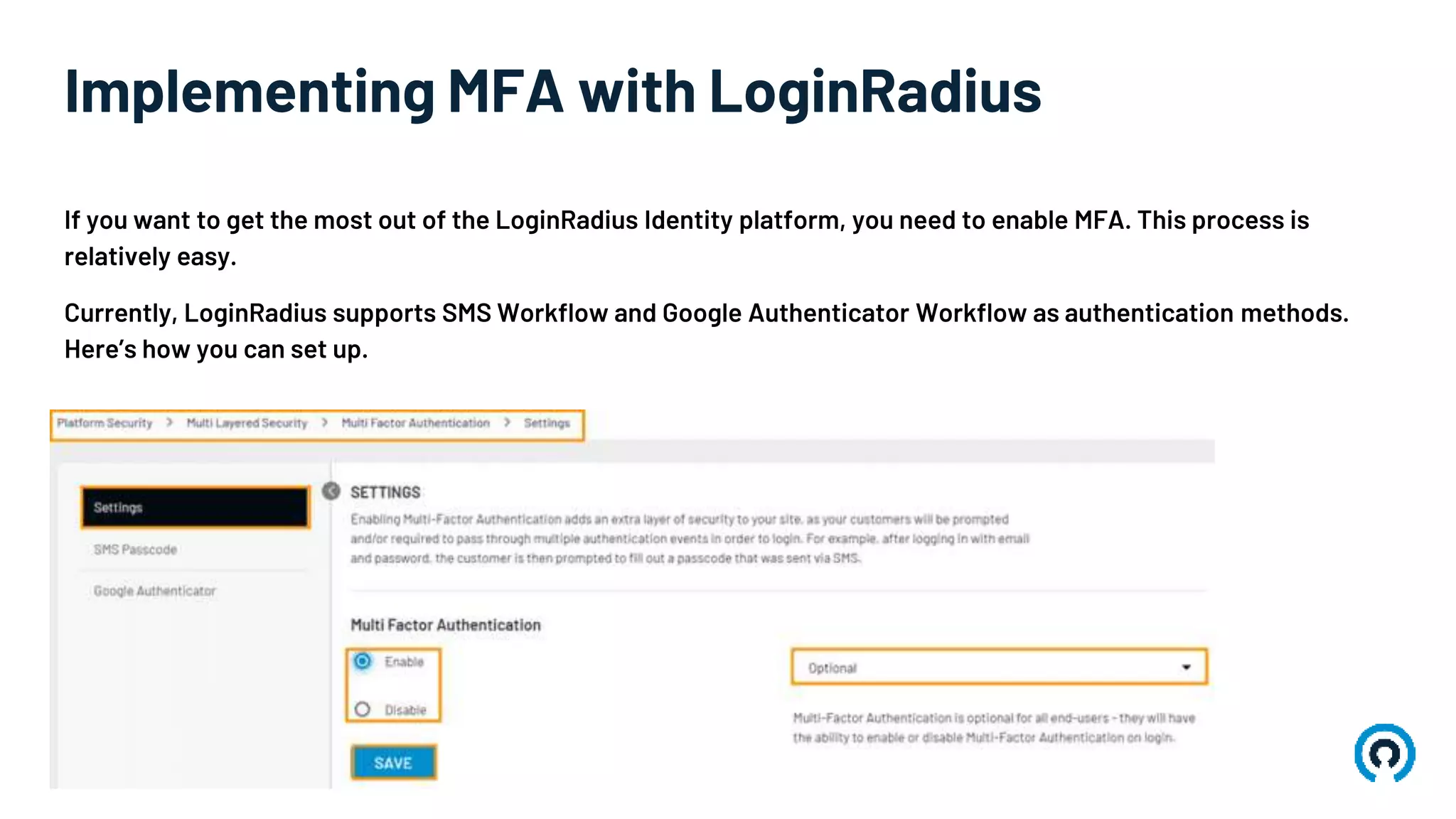
Multi-factor authentication (MFA) enhances digital security by requiring users to provide two or more pieces of evidence from different categories for identity verification. It offers several benefits, including reduced fraud and identity theft, increased consumer trust, and compliance with industry regulations. Implementing MFA is streamlined with platforms like LoginRadius, supporting methods such as SMS and Google Authenticator.