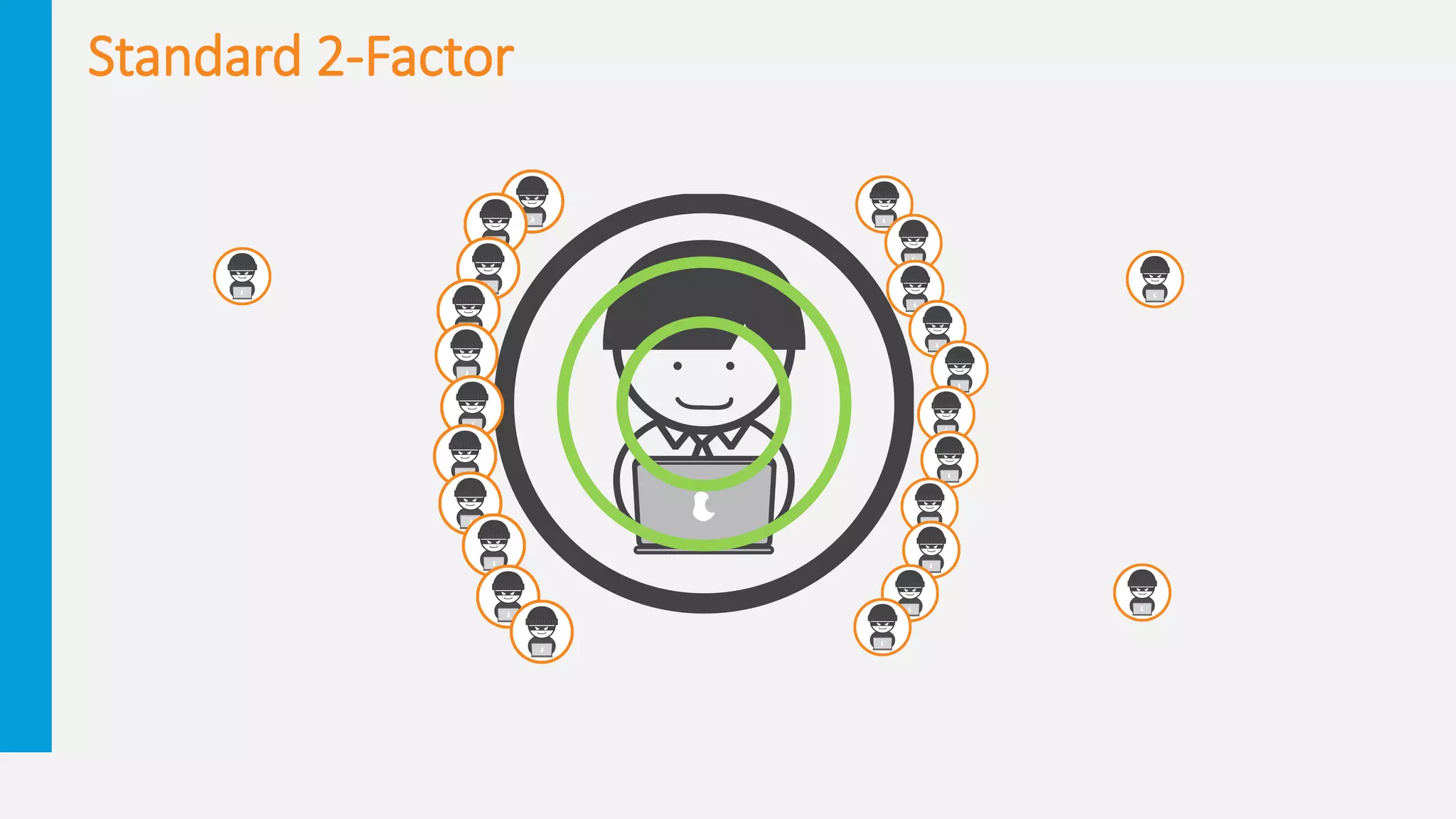
1. The document discusses the misuse of stolen credentials and the need to go beyond standard two-factor authentication.
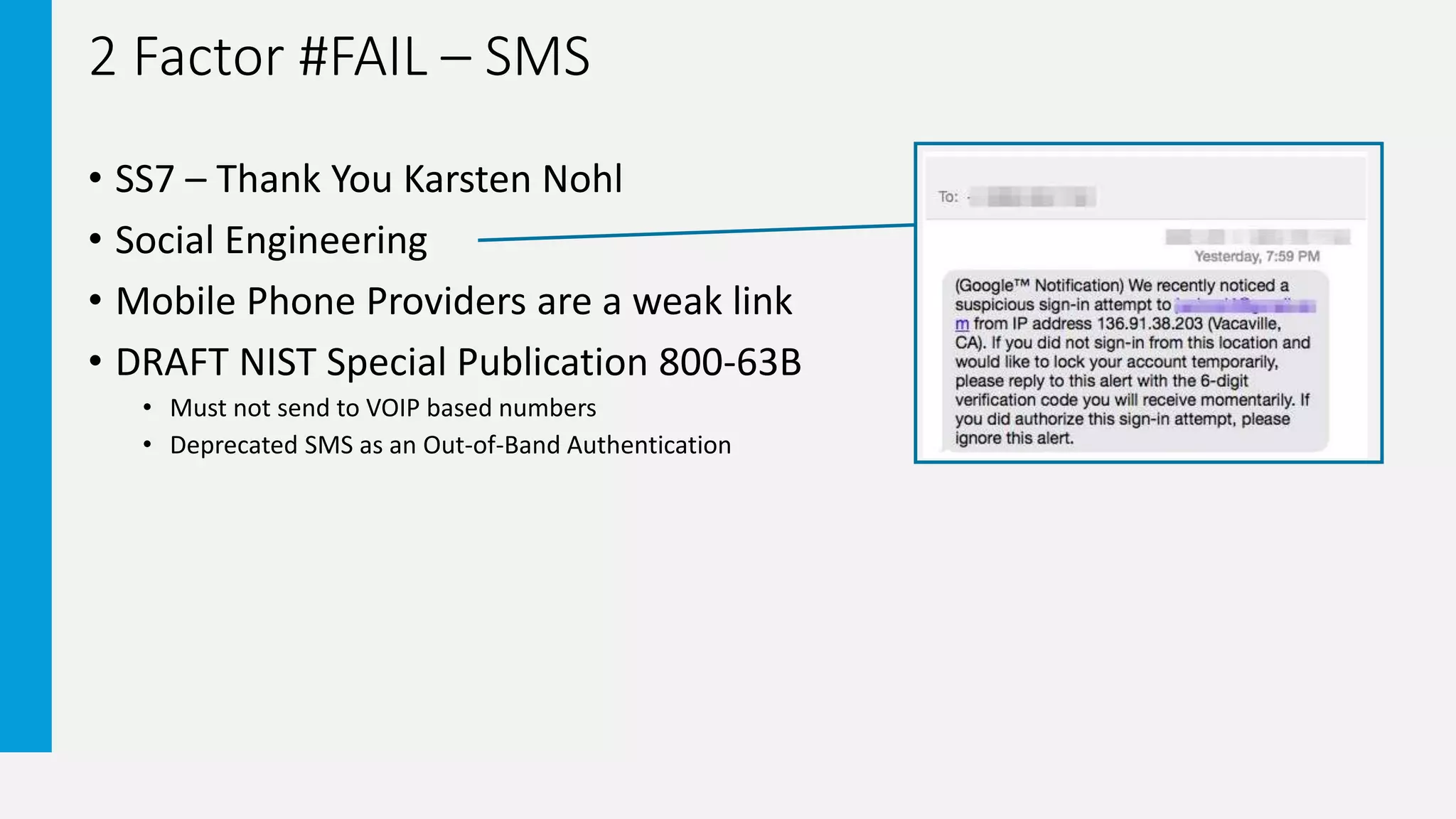
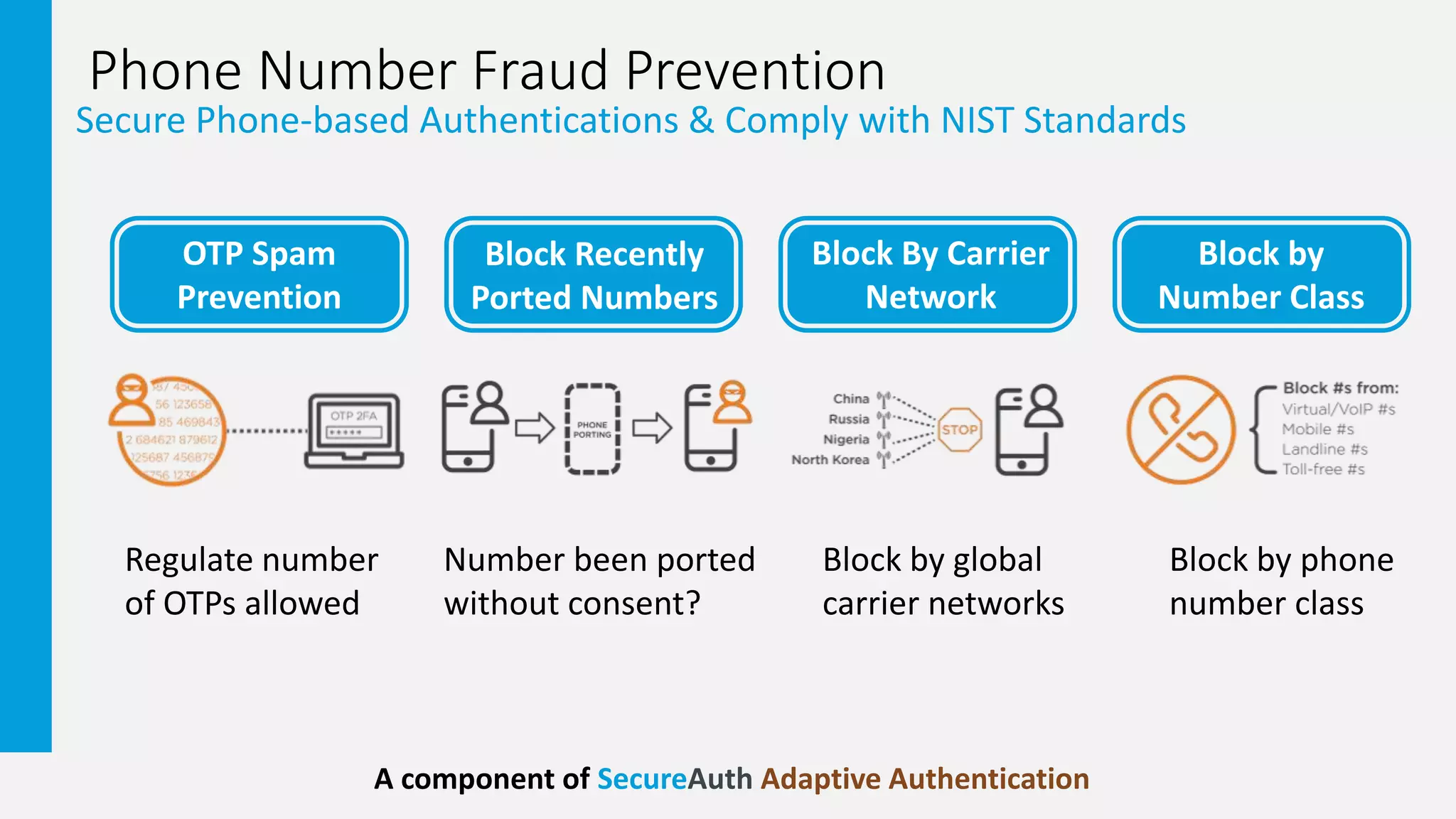
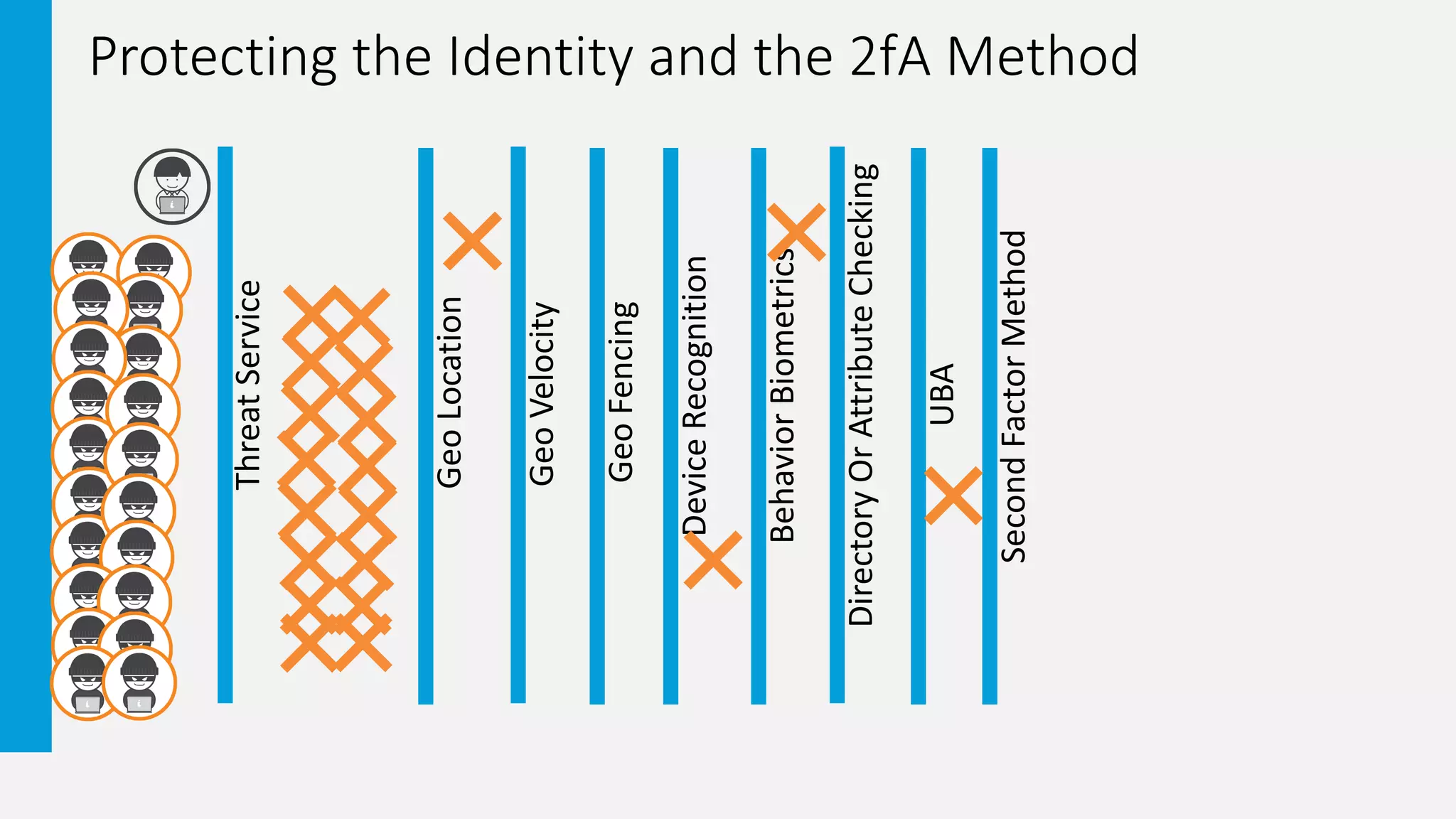
2. It provides examples of how two-factor authentication can fail, such as through SMS interception, social engineering of knowledge-based authentication questions, and users wrongly accepting authentication requests.
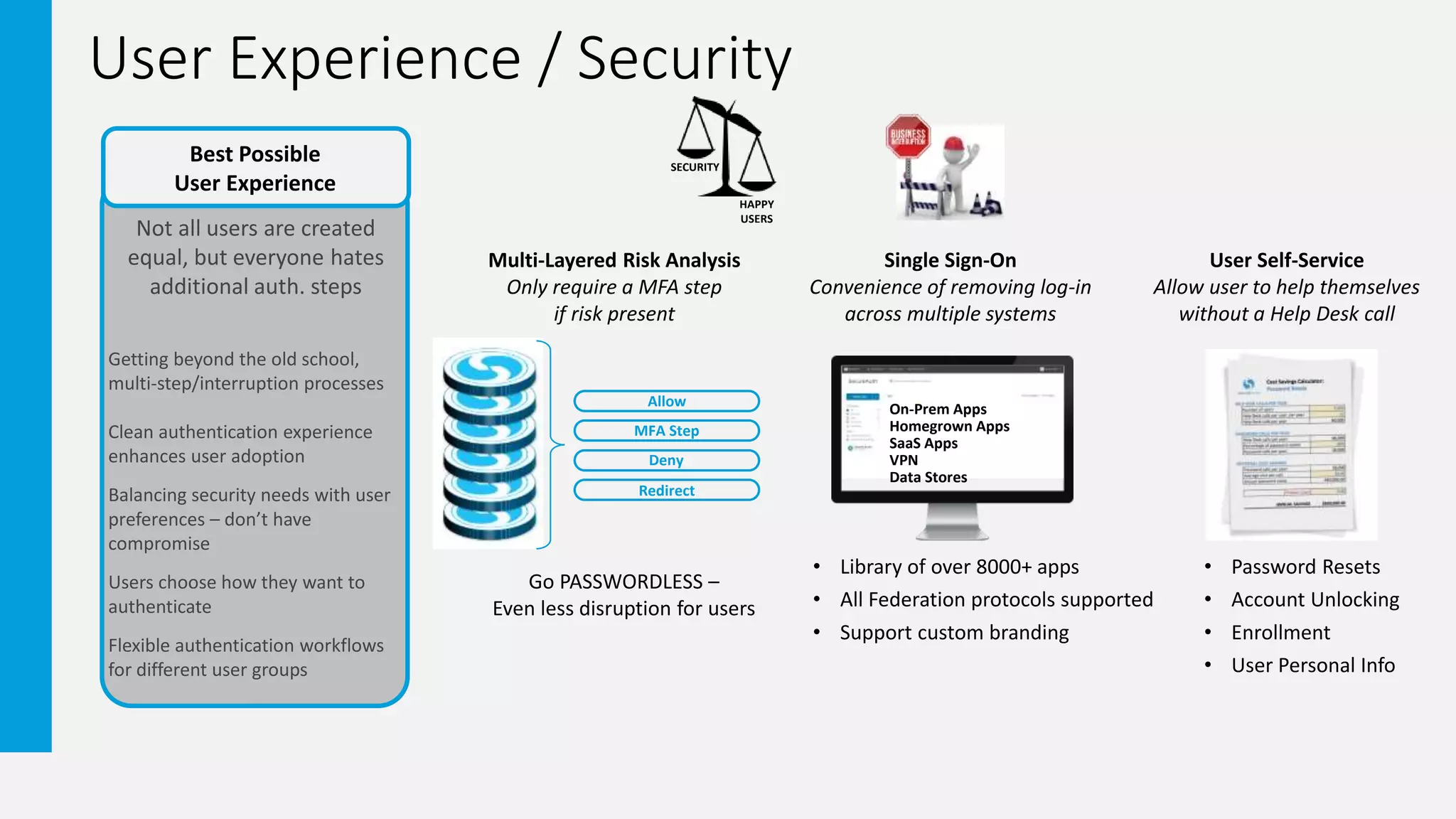
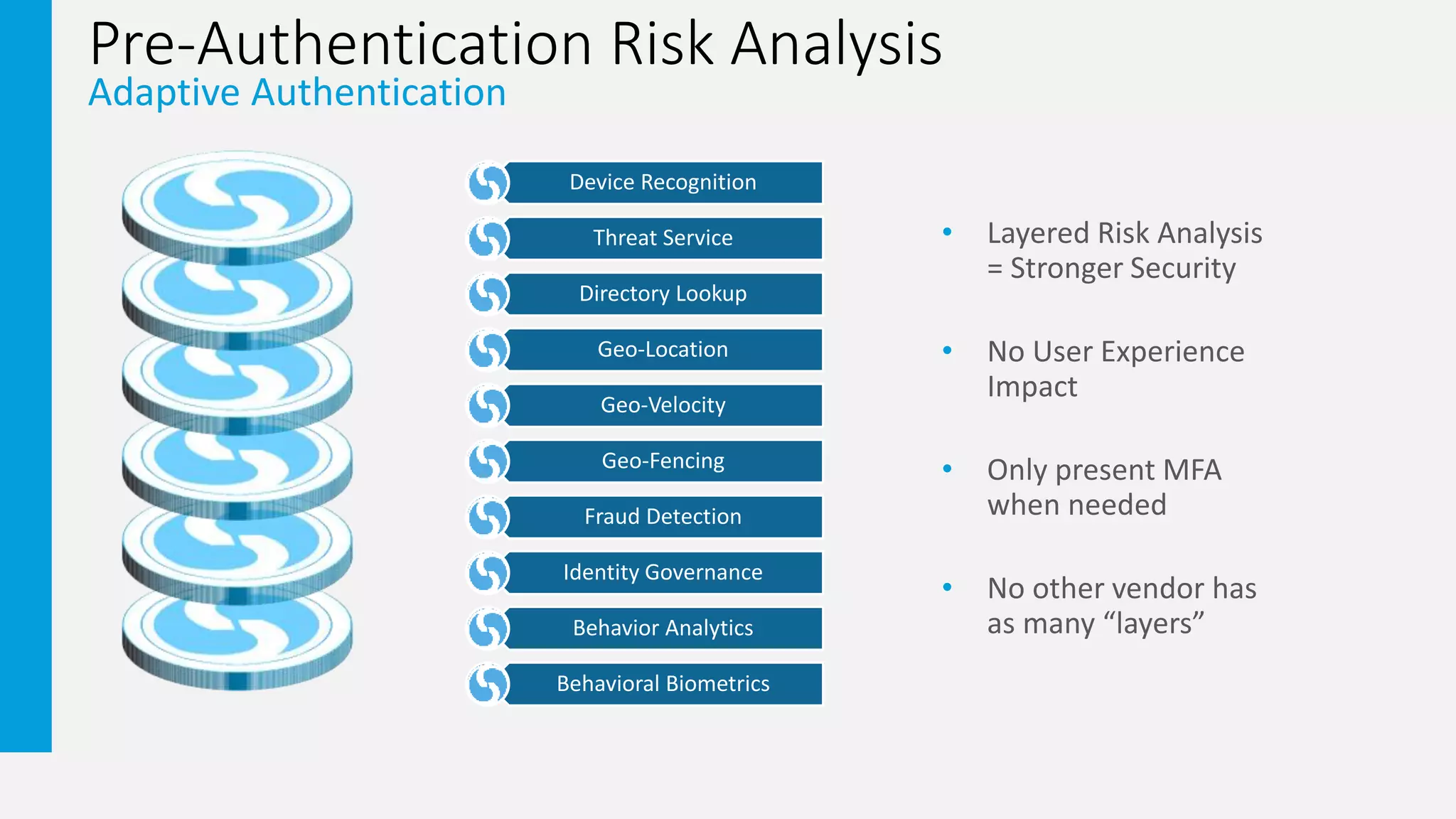
3. The document promotes an adaptive authentication approach using multiple layers of risk analysis and a wide range of authentication methods to strengthen security with minimal user impact.