The document proposes a method of encrypting messages in DNA and implanting the encrypted DNA into a person for covert message transmission. Key points:
- They were inspired by Alan Turing's work encrypting messages and want to create a biological code using DNA sequences.
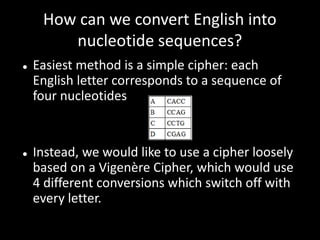
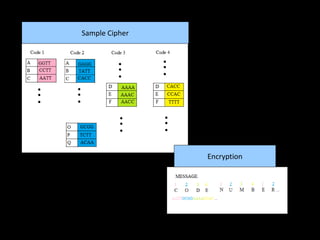
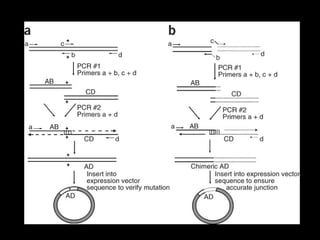
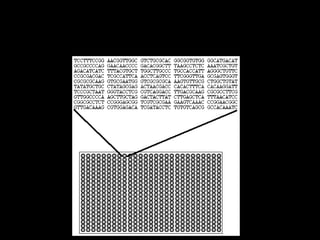
- The message would be encrypted into a DNA sequence and inserted into a cell, which would then be implanted into an individual. This would doubly protect the message through encryption and indistinguishability from the person's normal cells.
- They refer to this method as "Nucleotide Cryptology" and believe it could be used to send hidden messages.