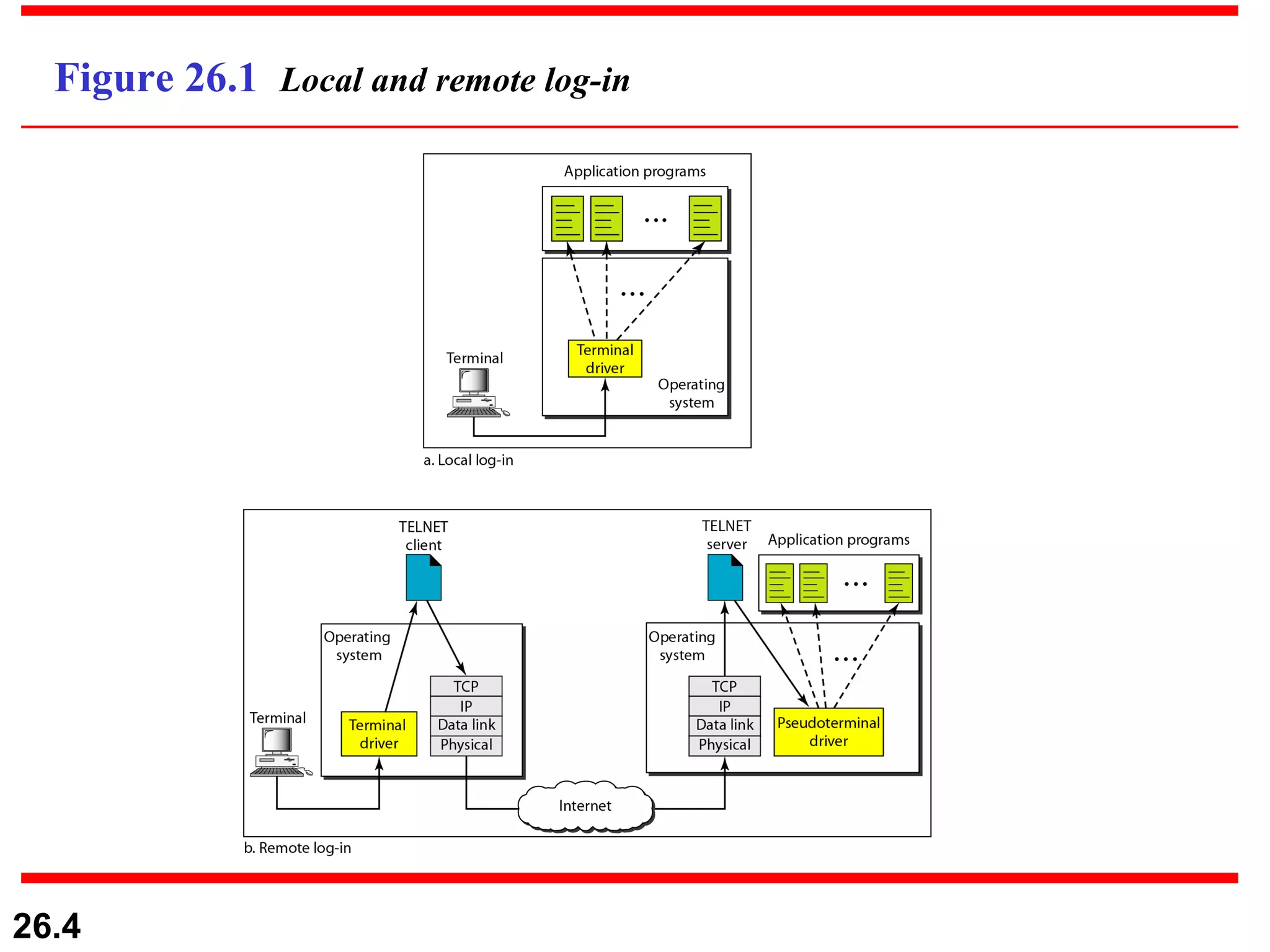
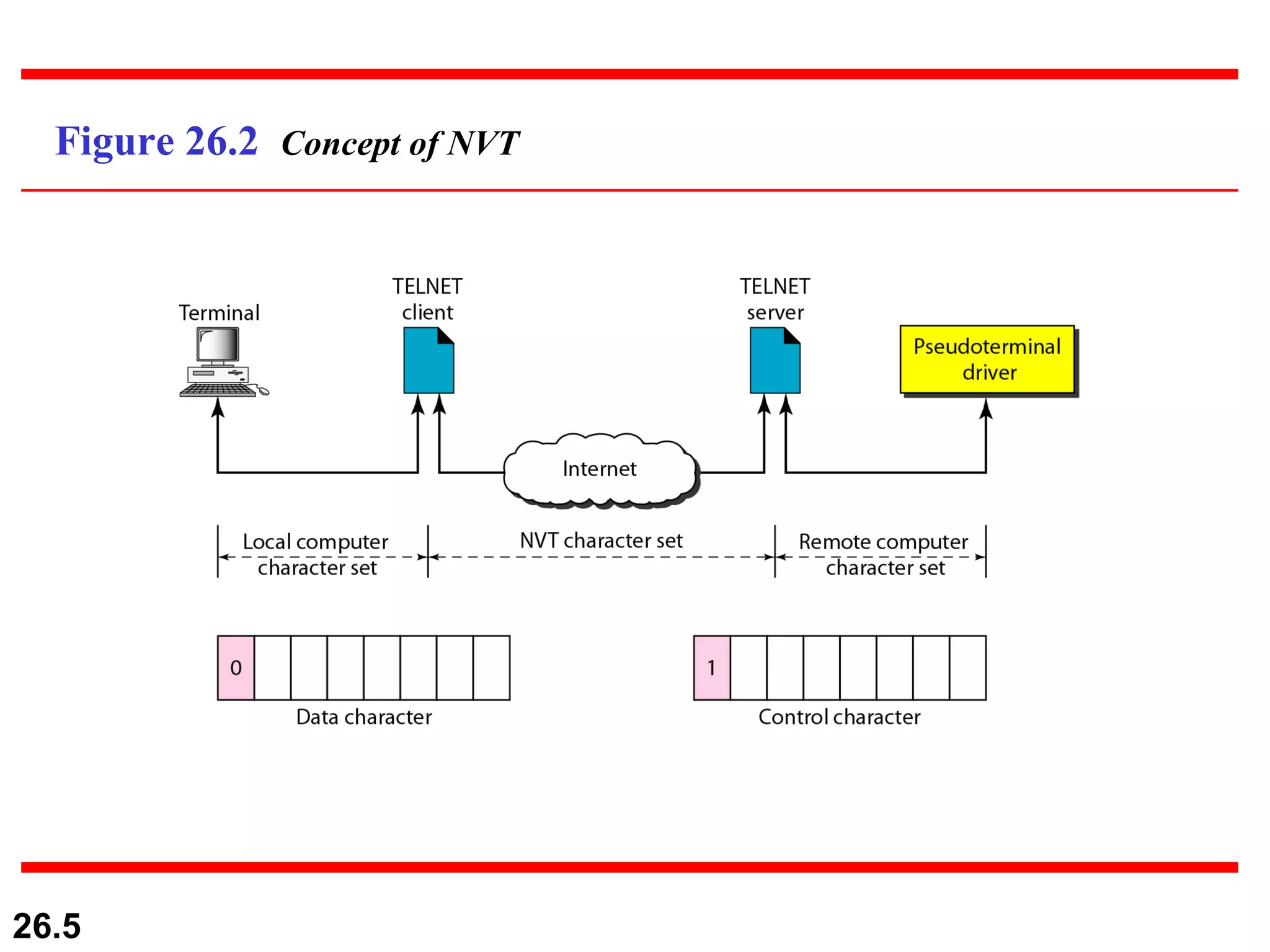
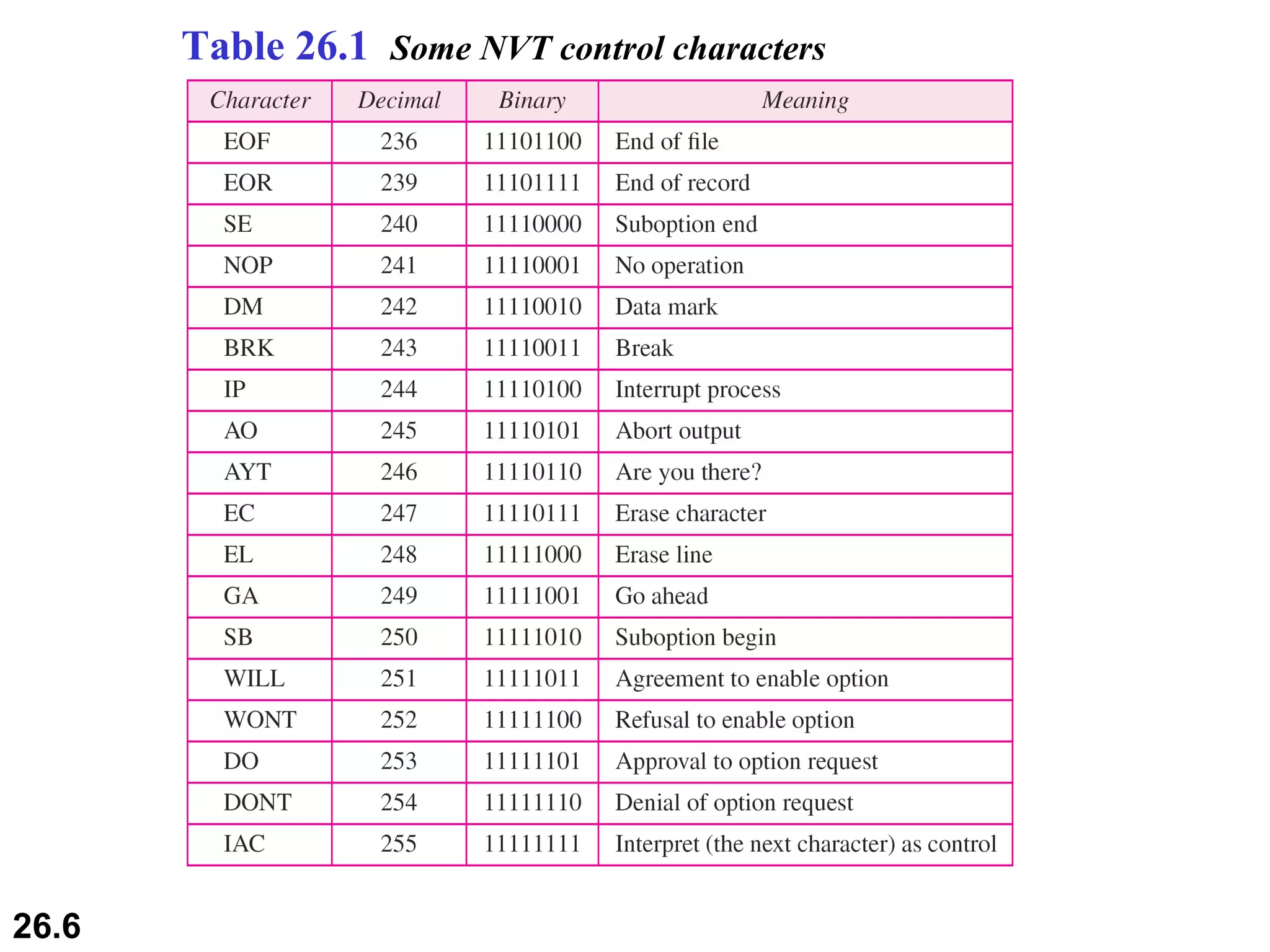
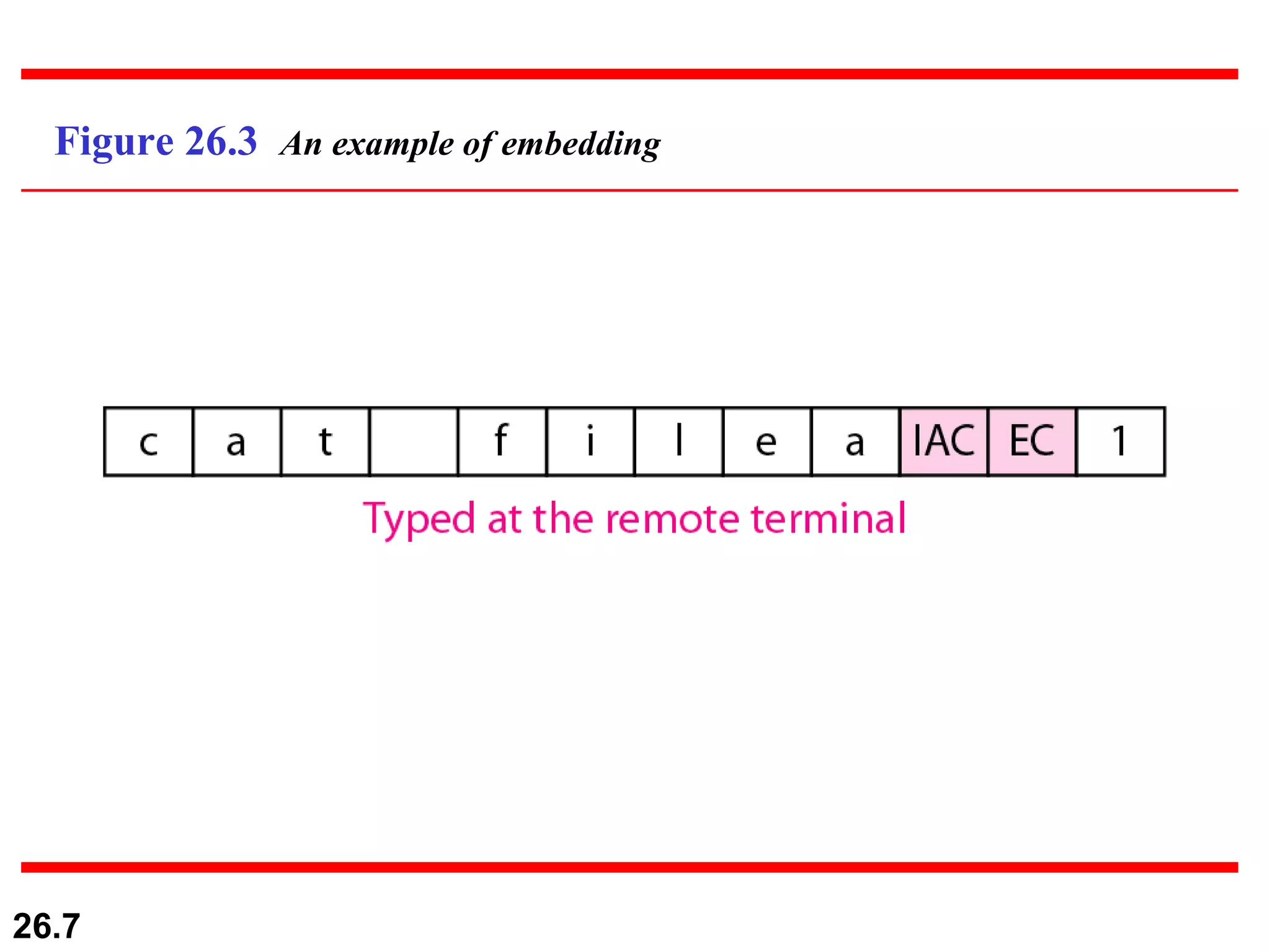
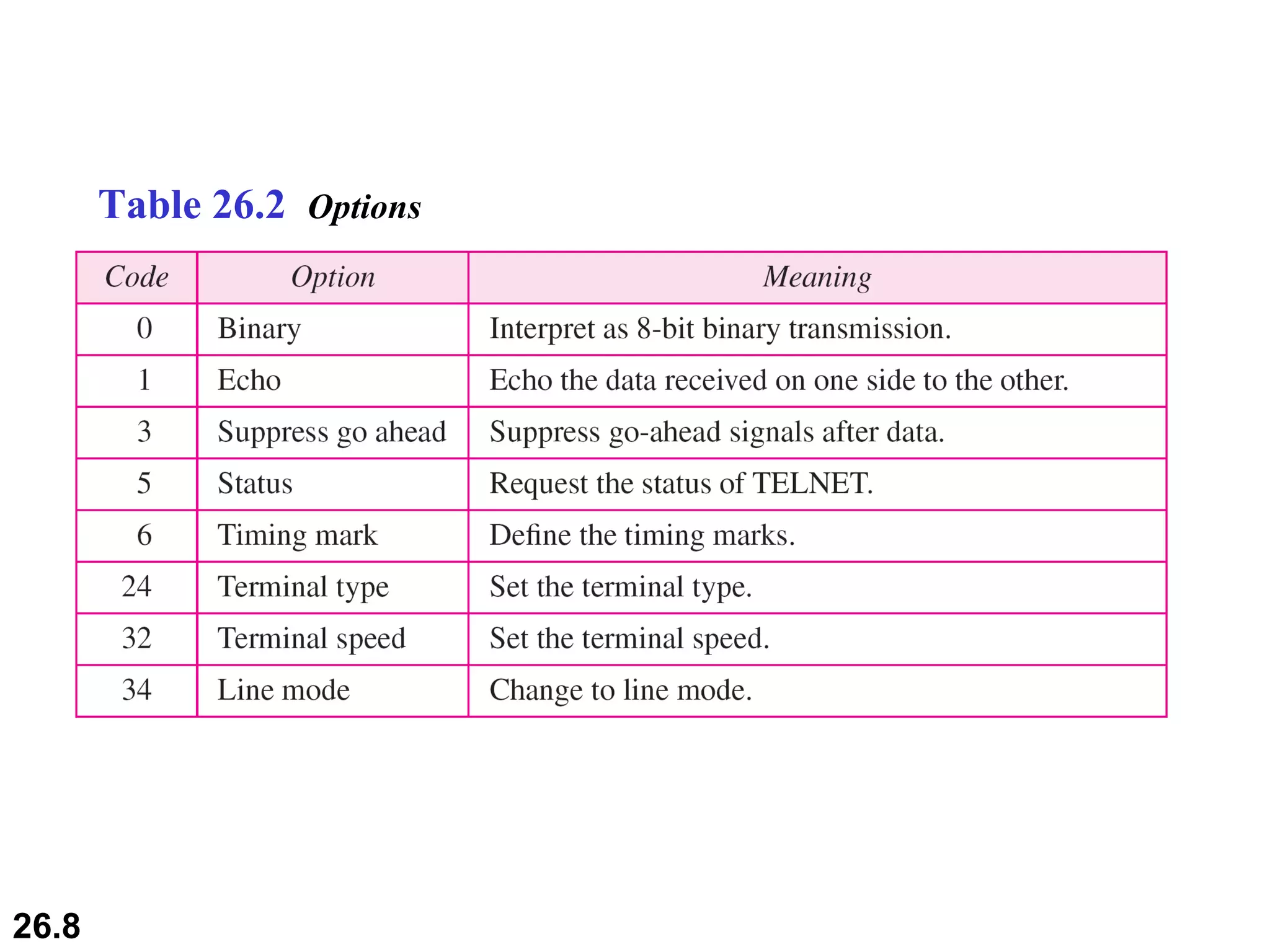
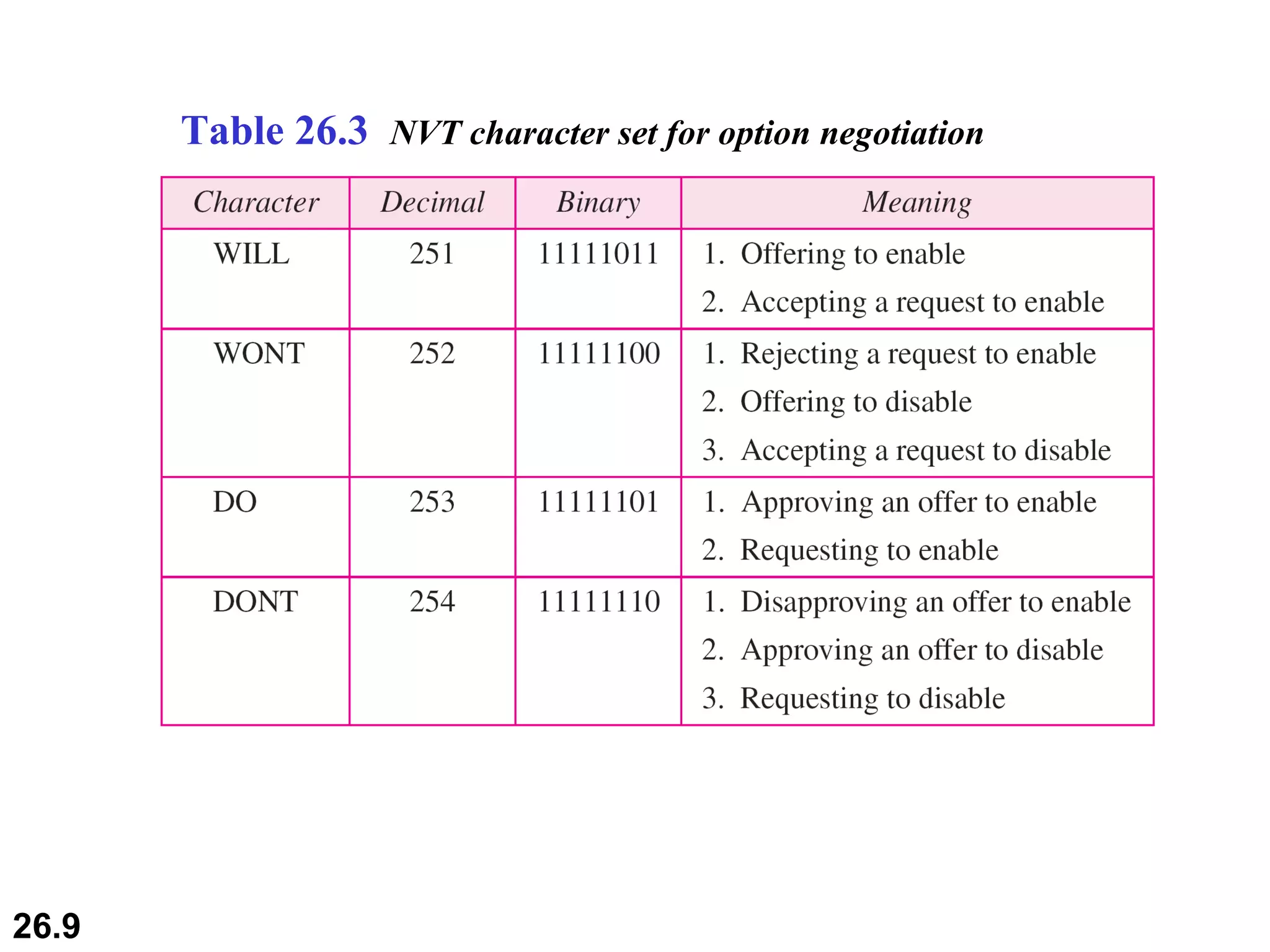
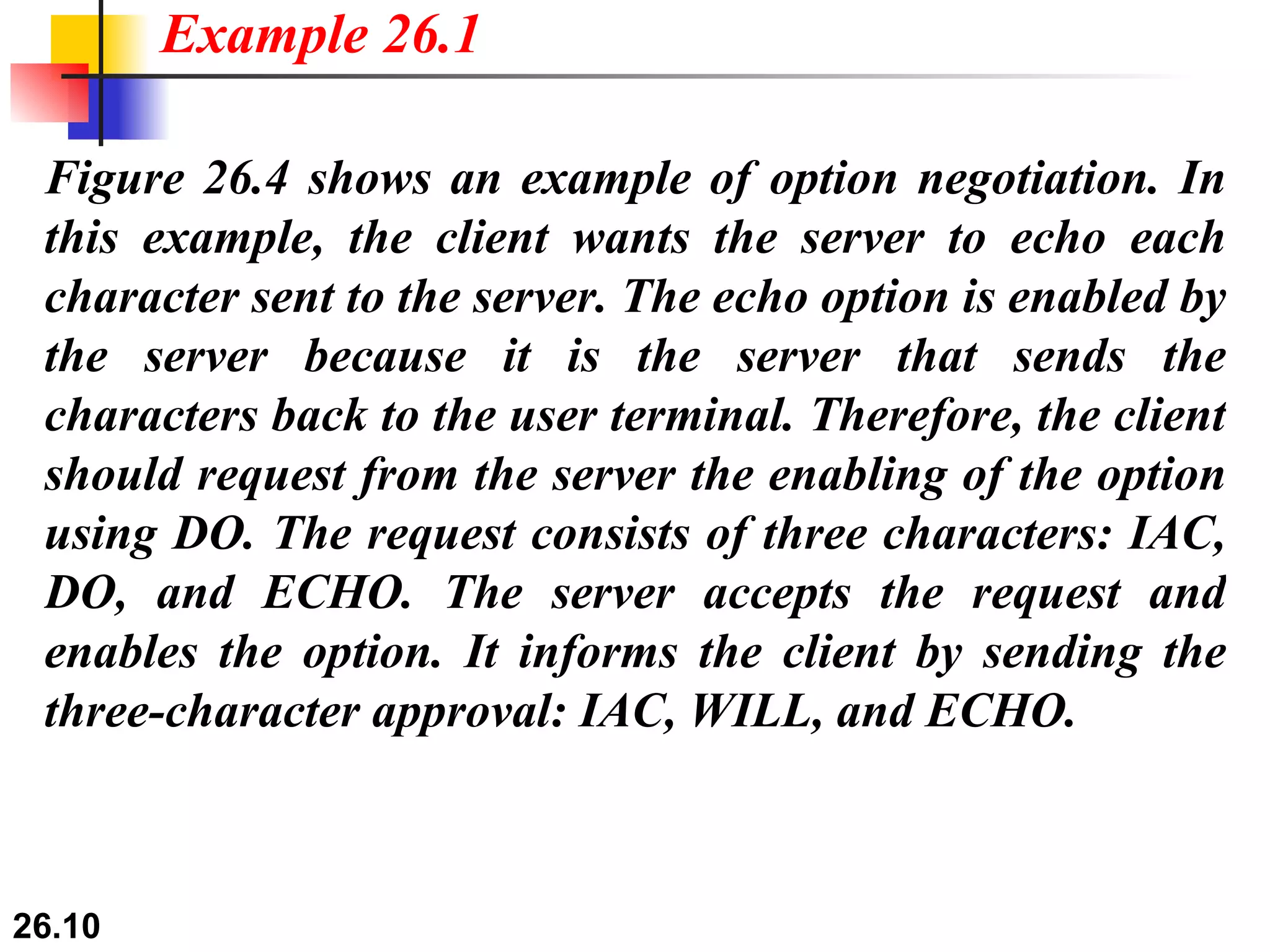
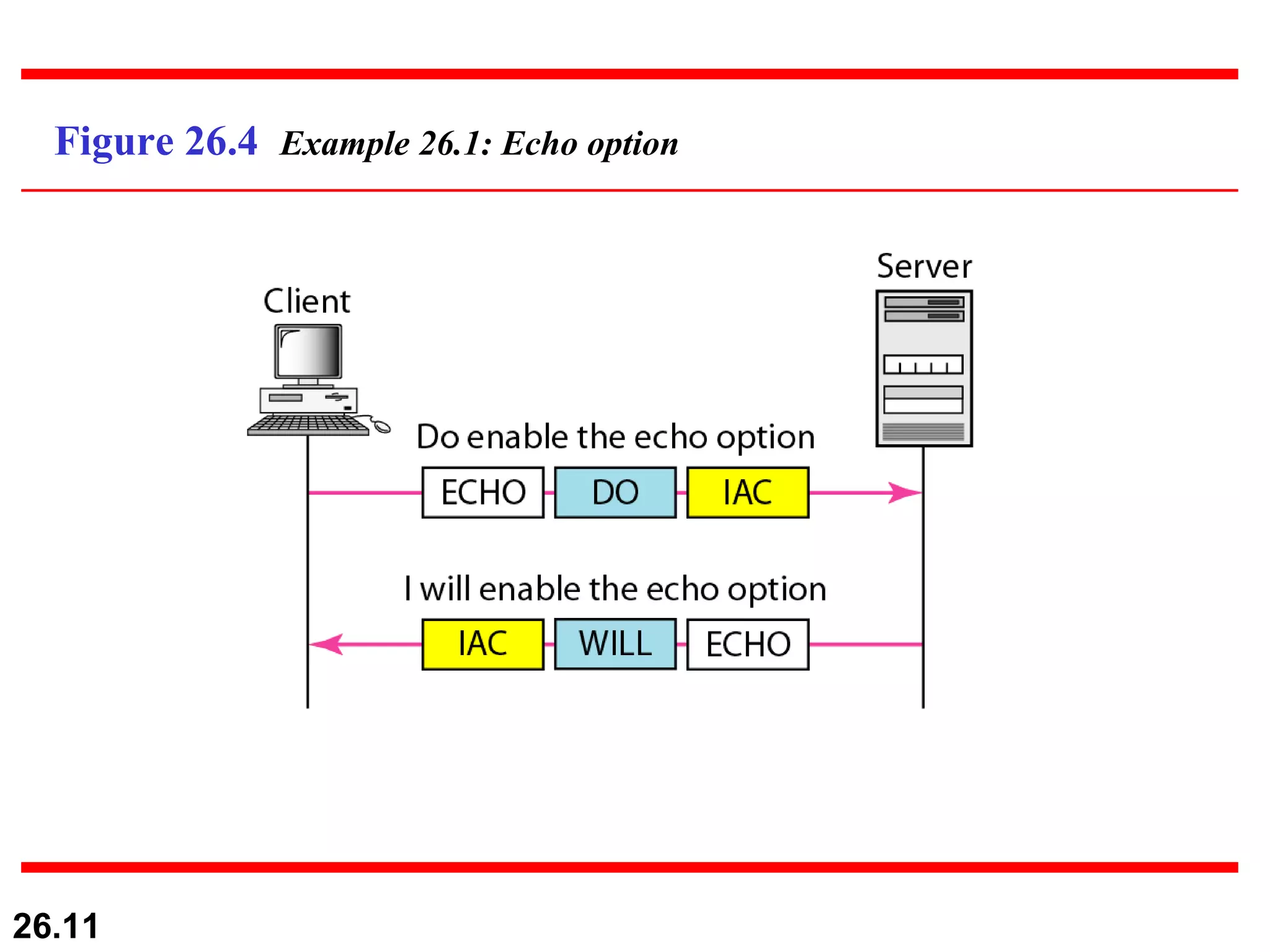
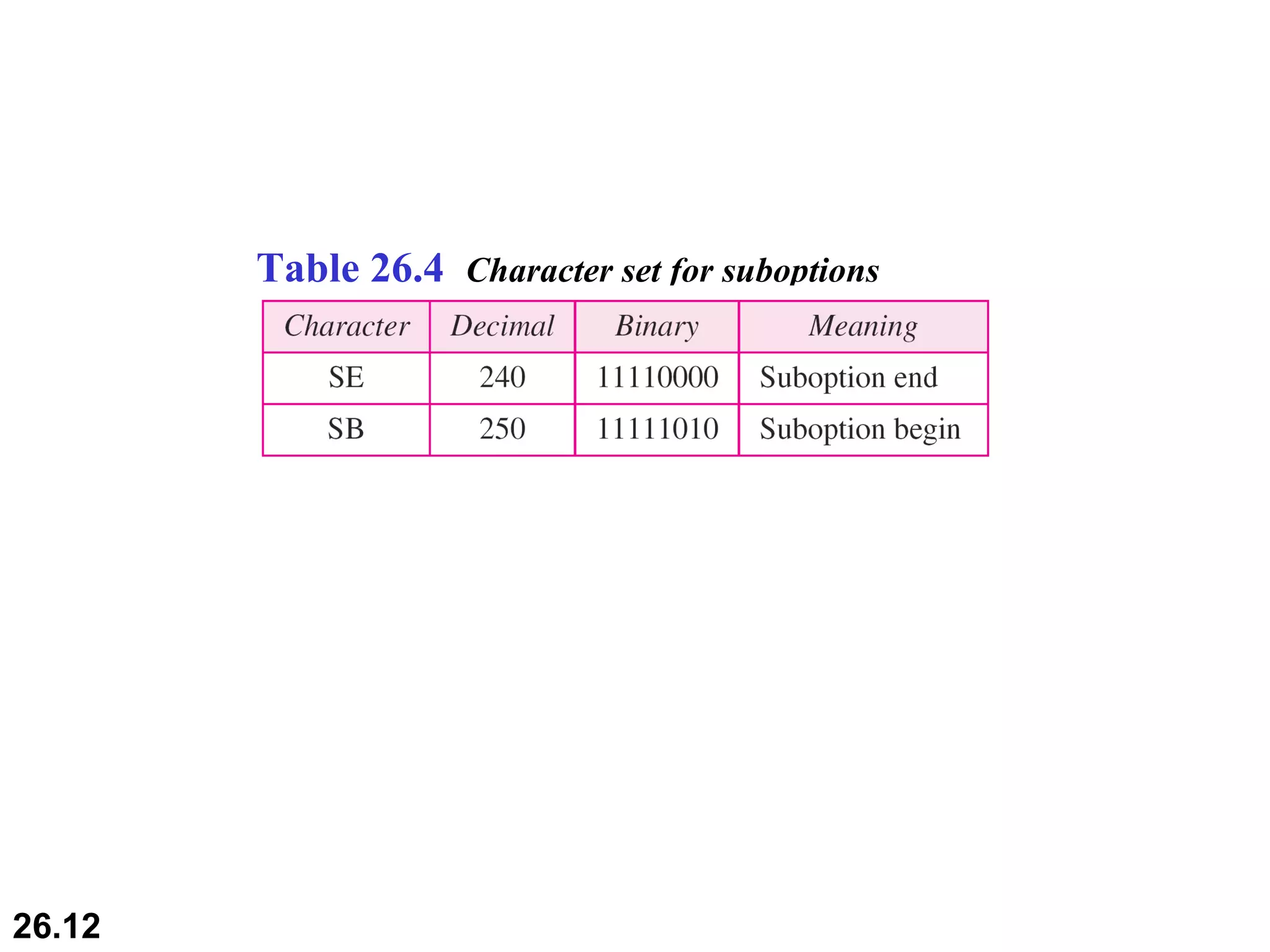
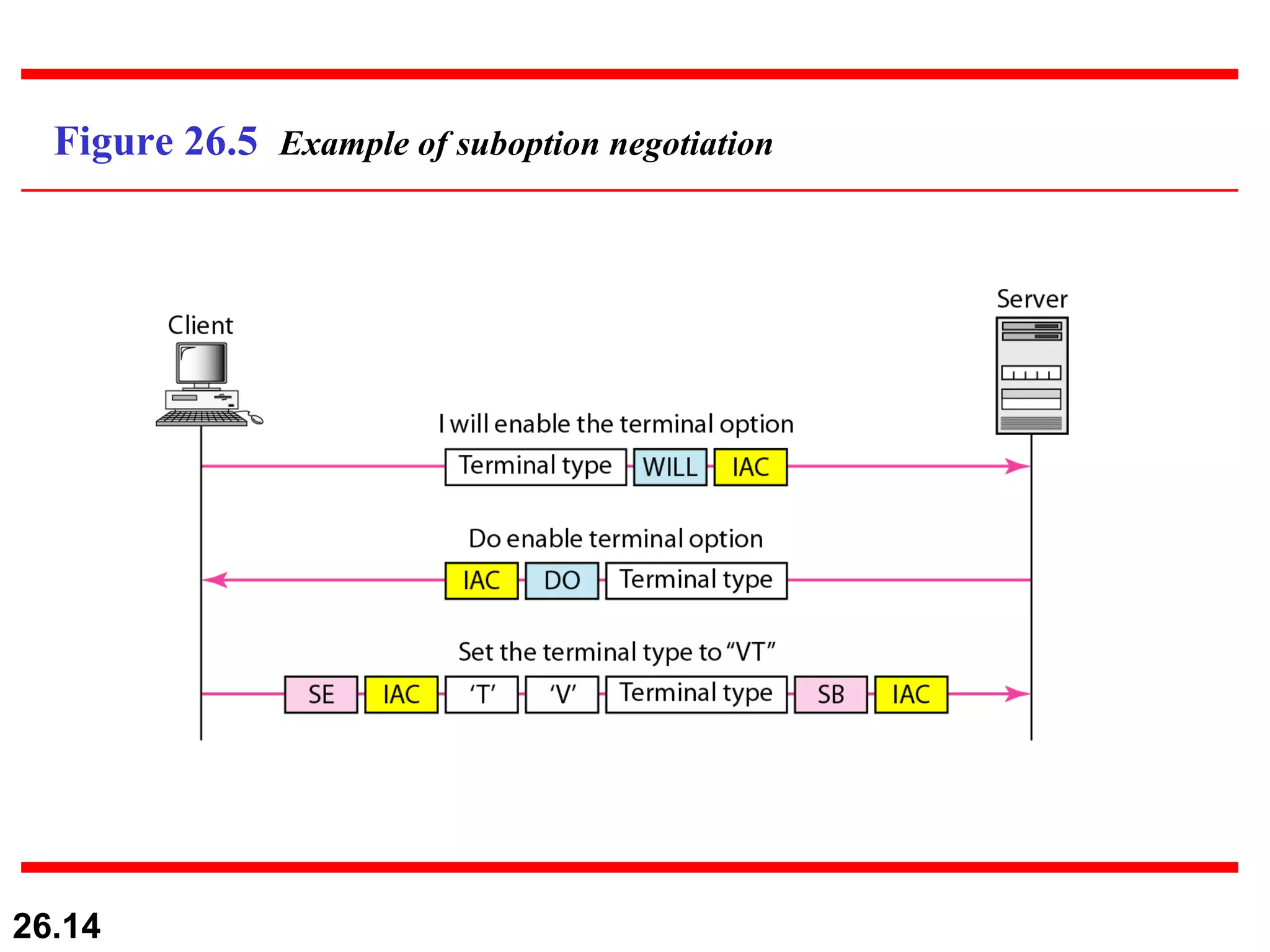
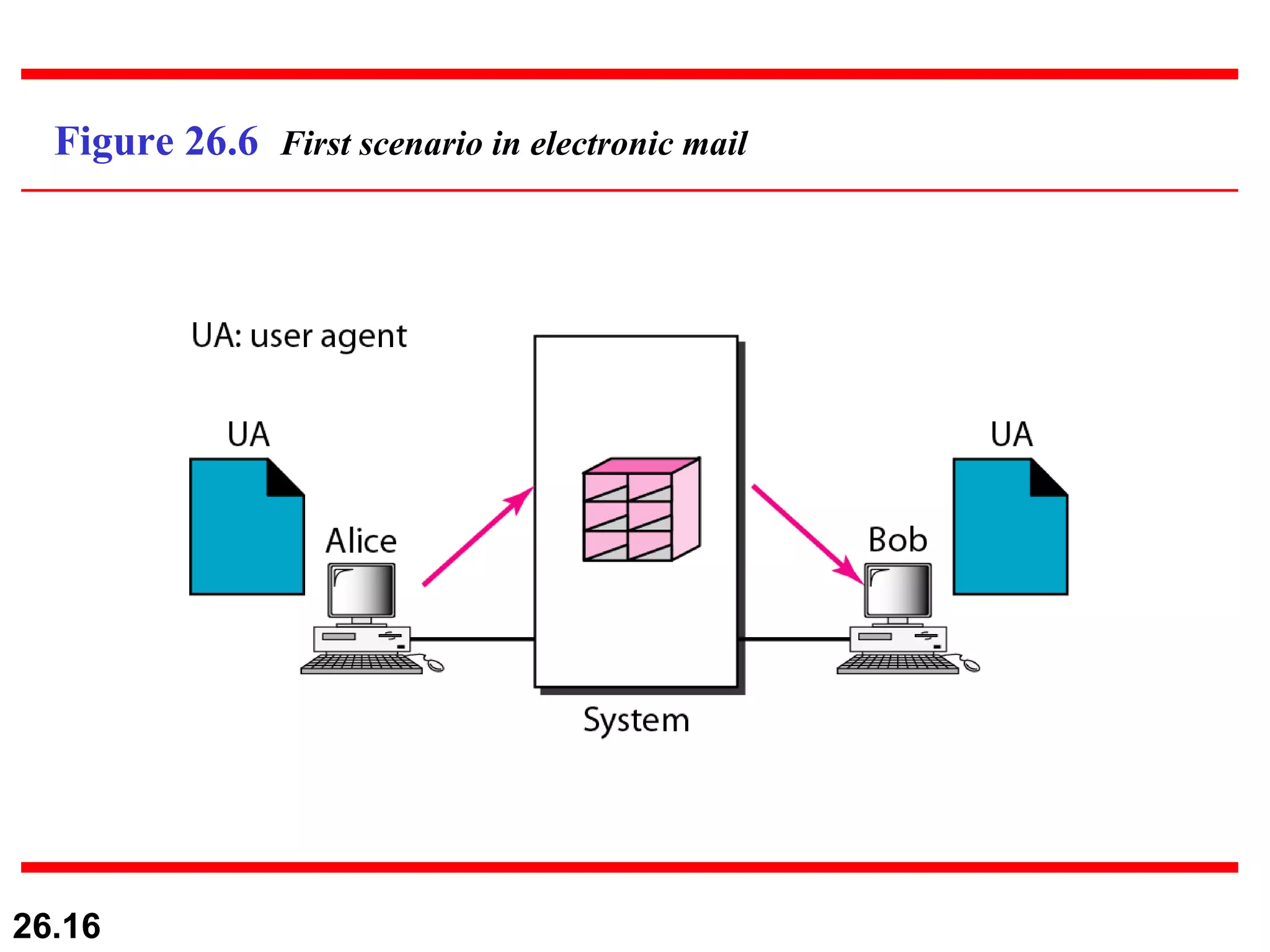
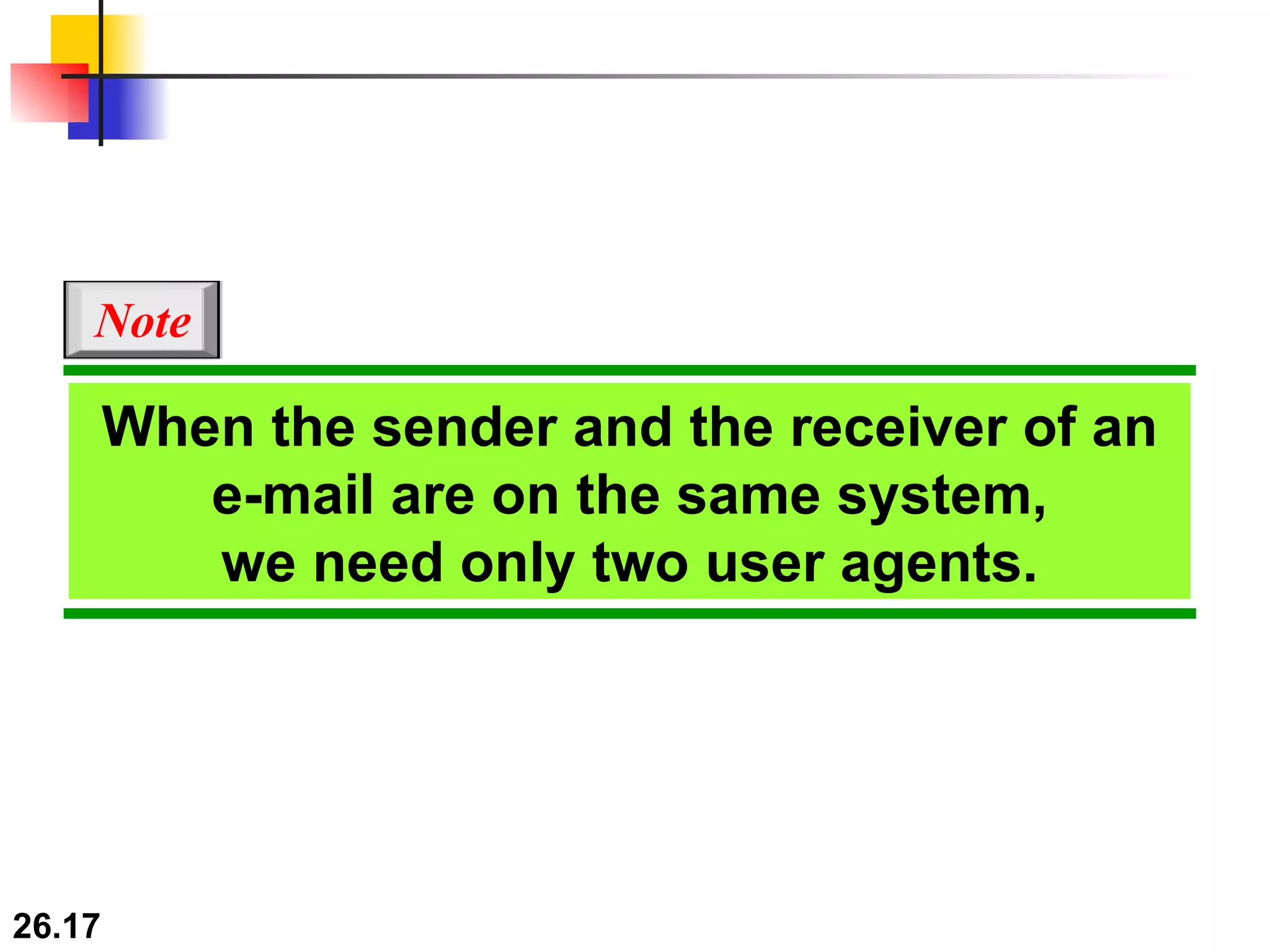
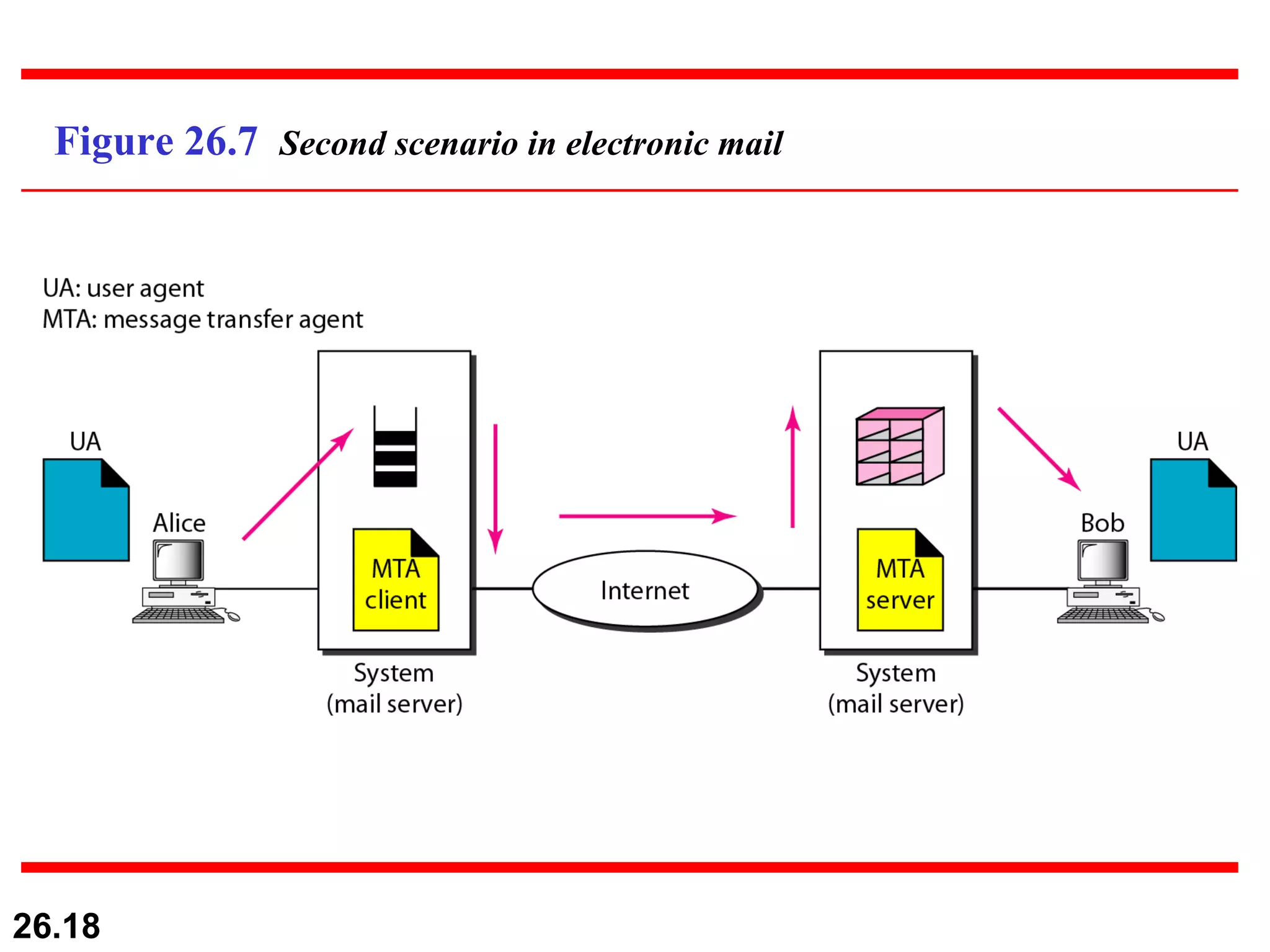
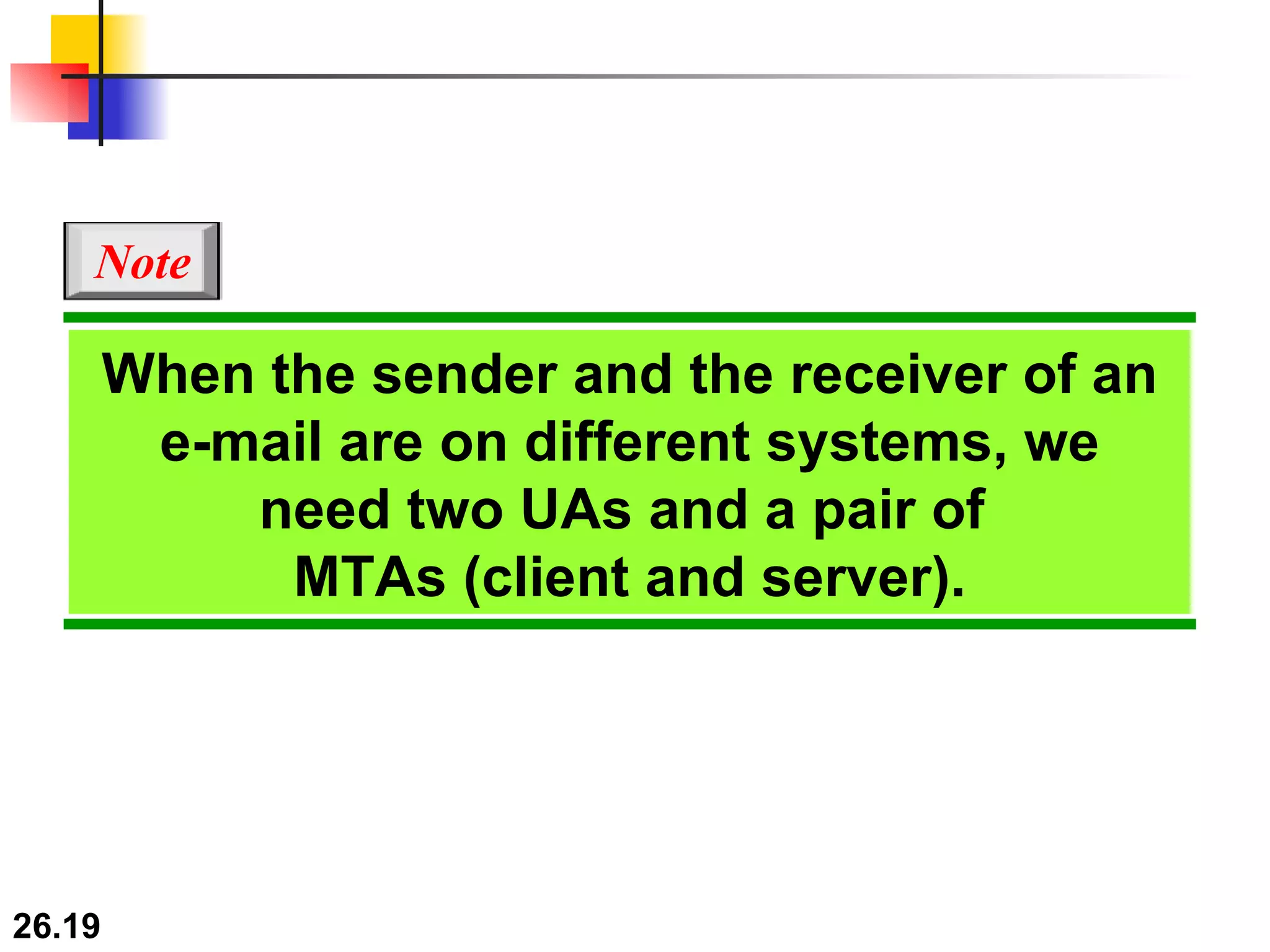
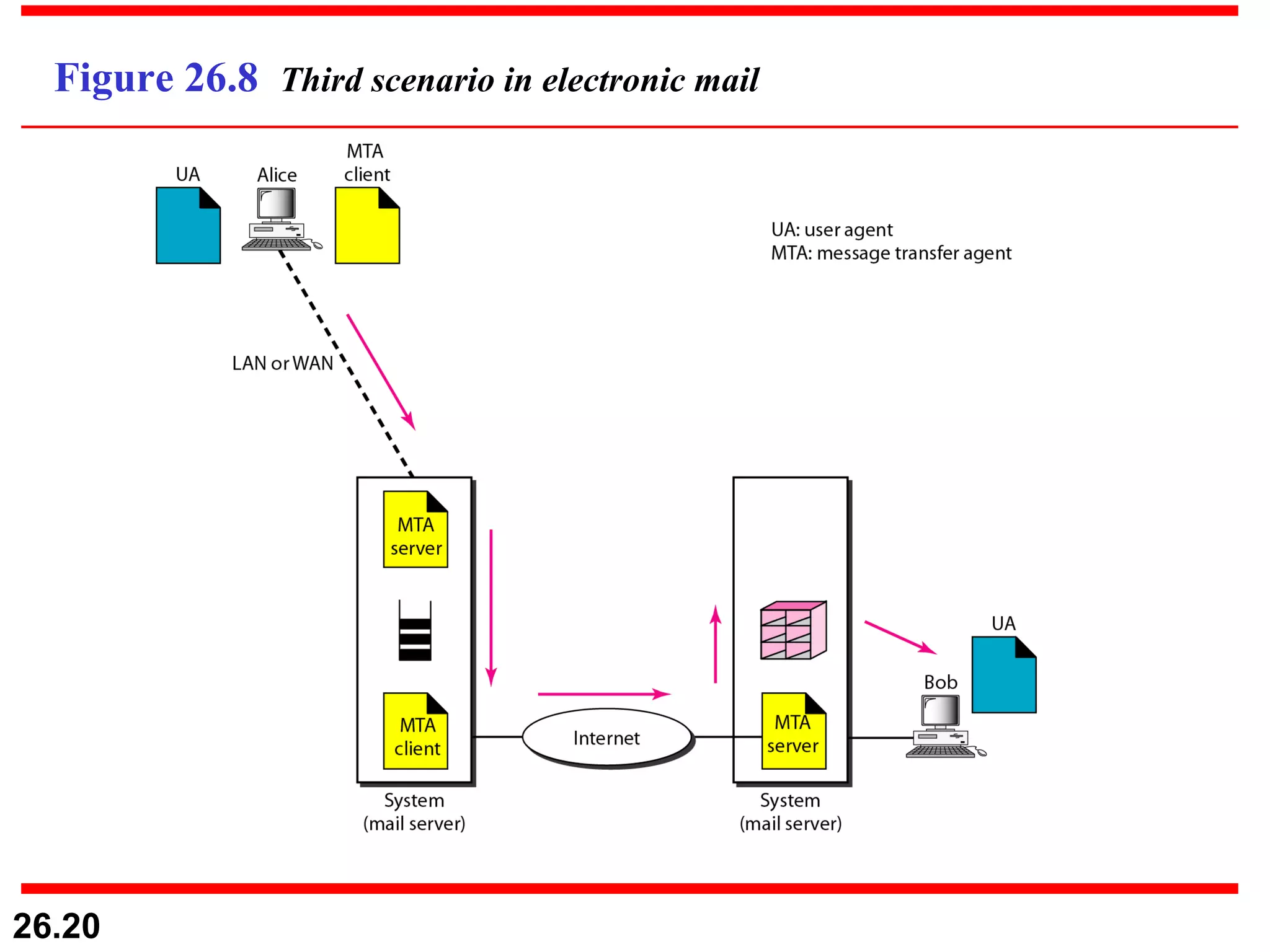
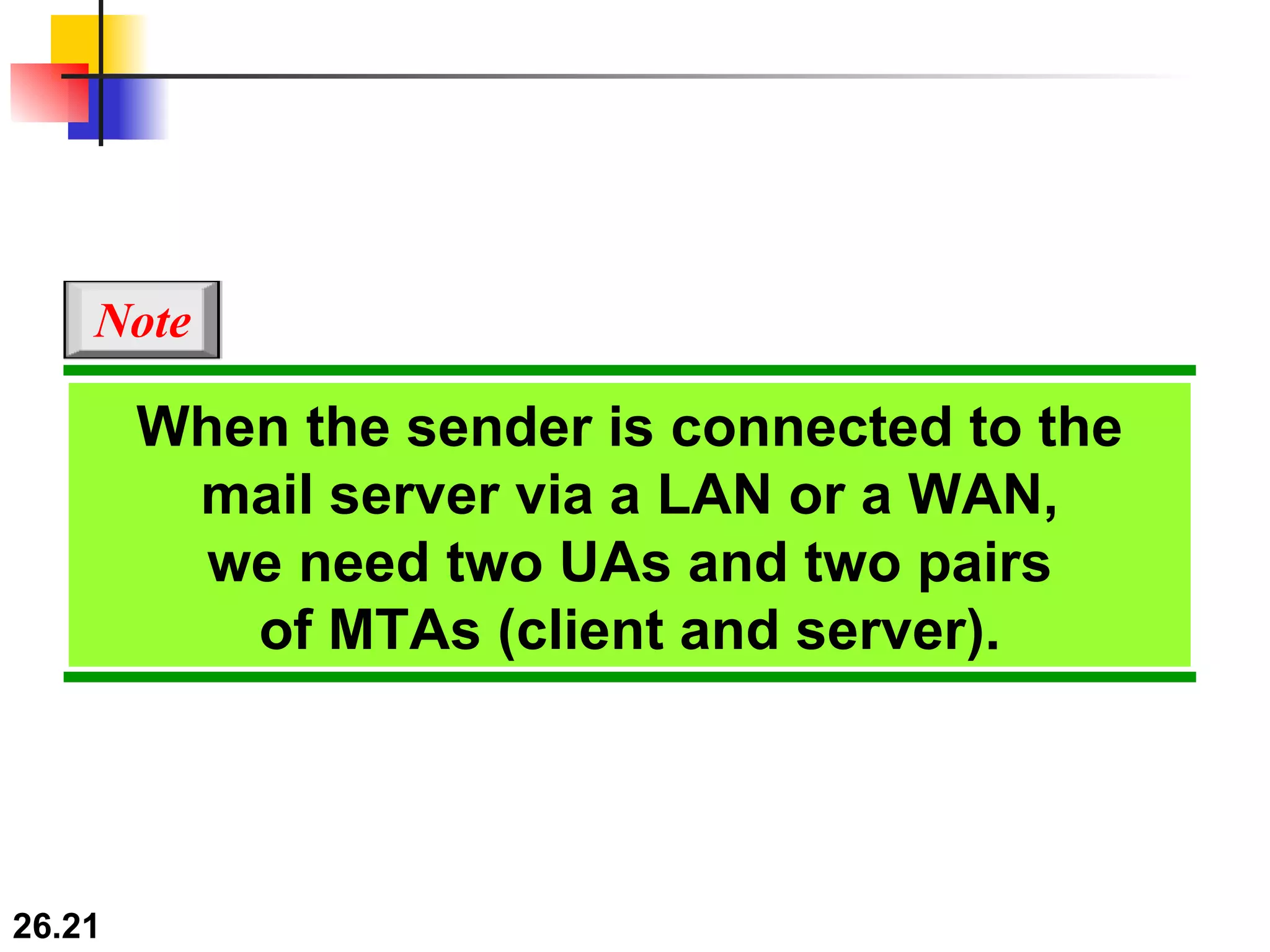
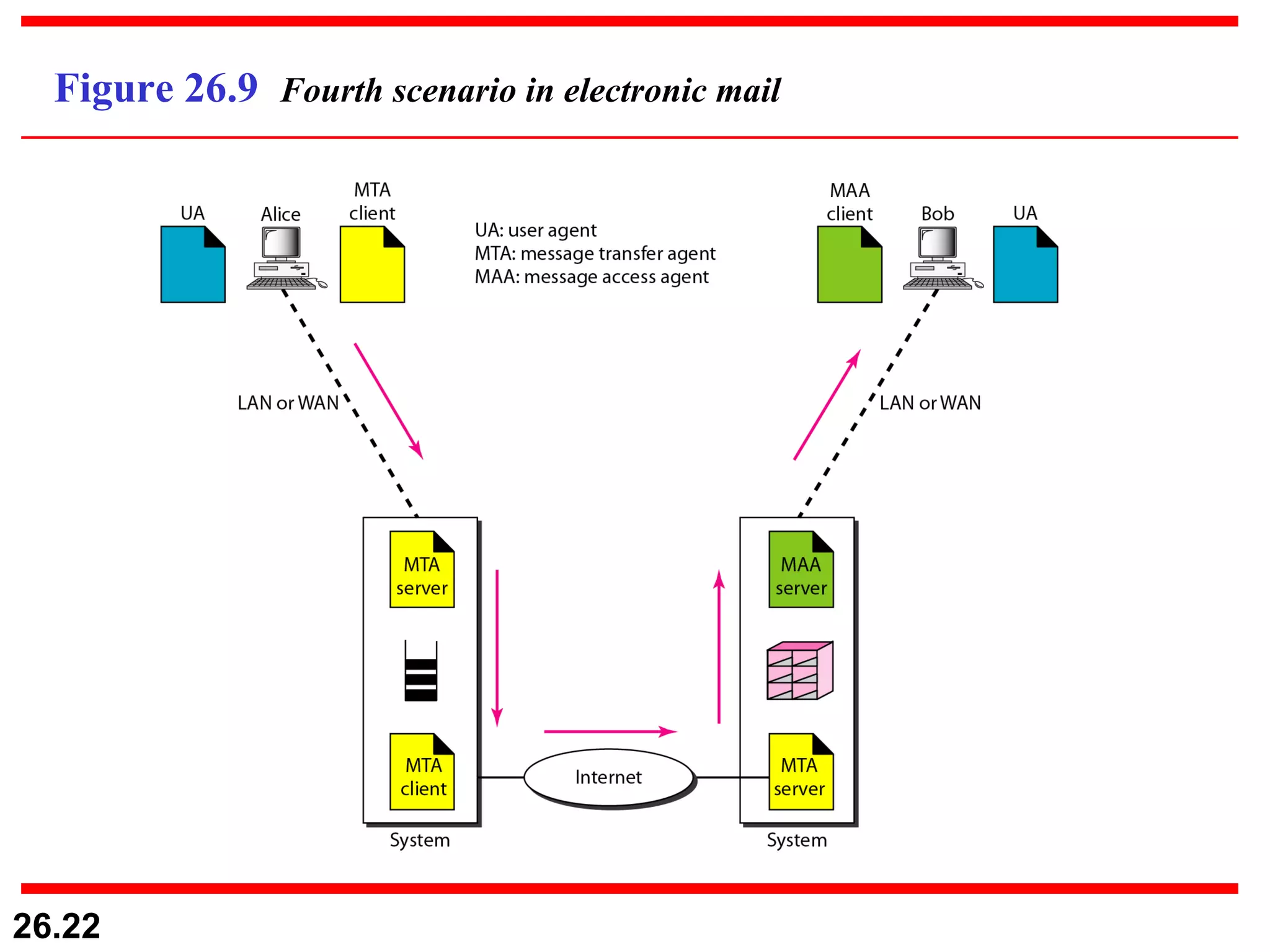
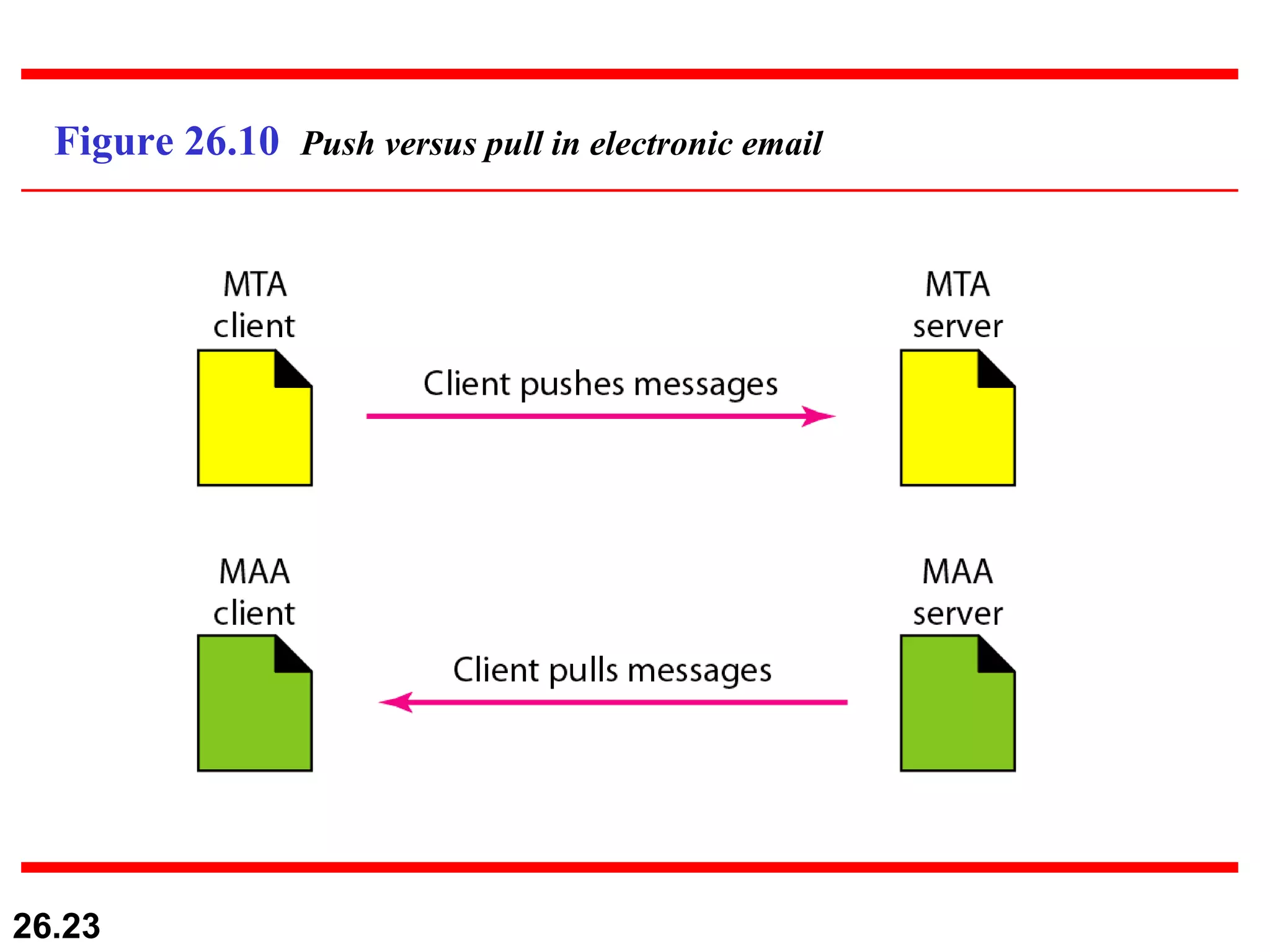
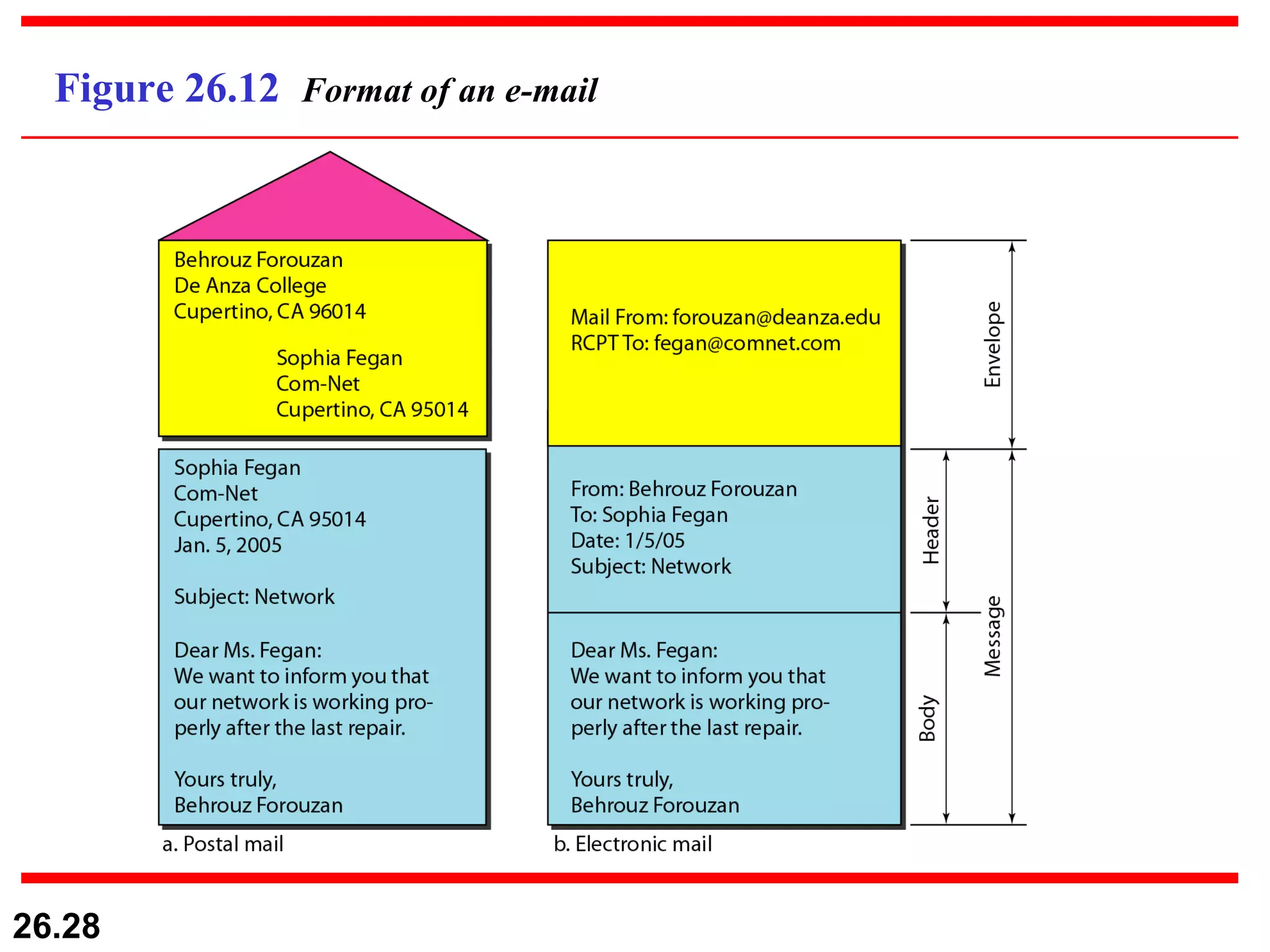
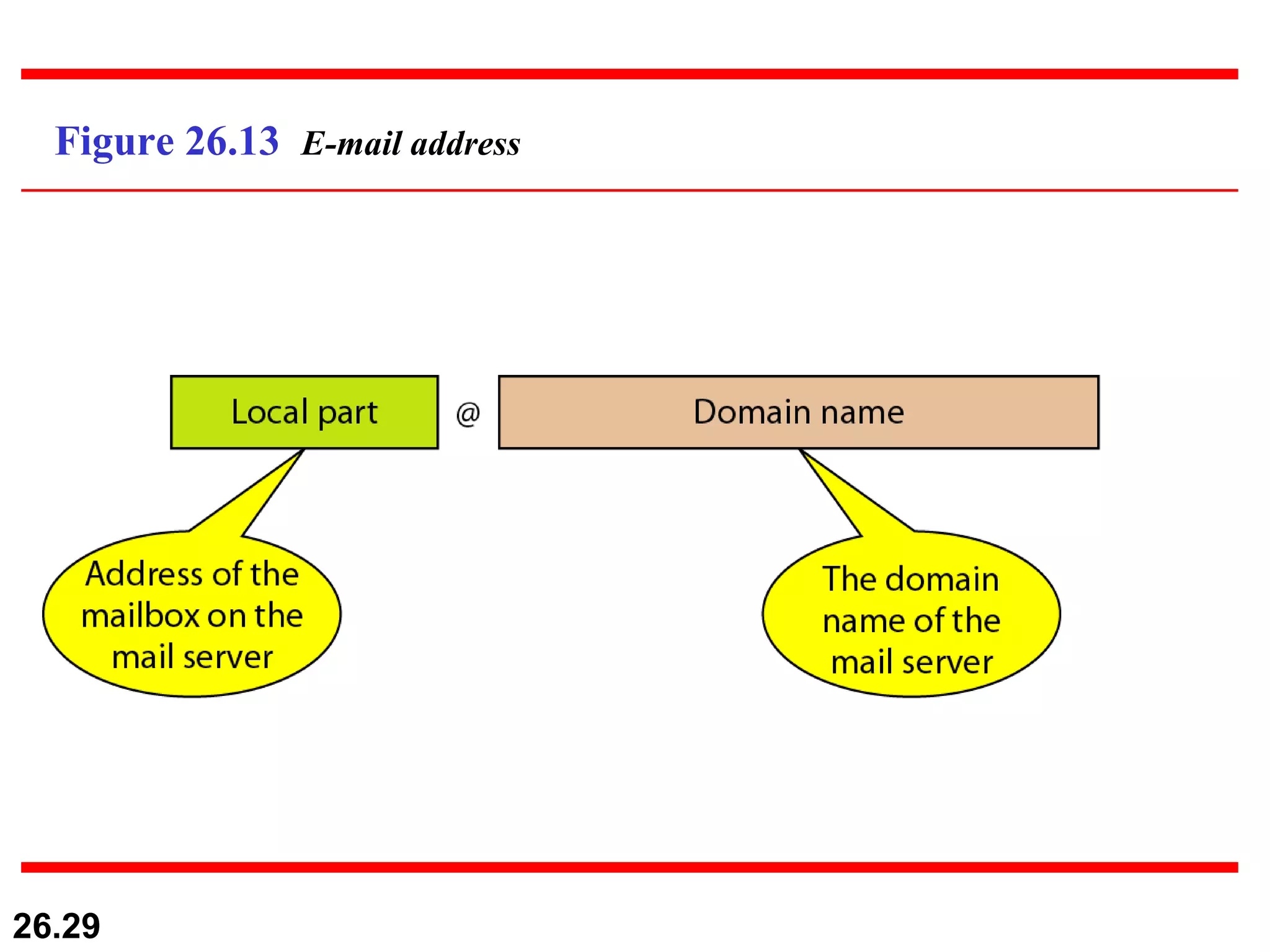
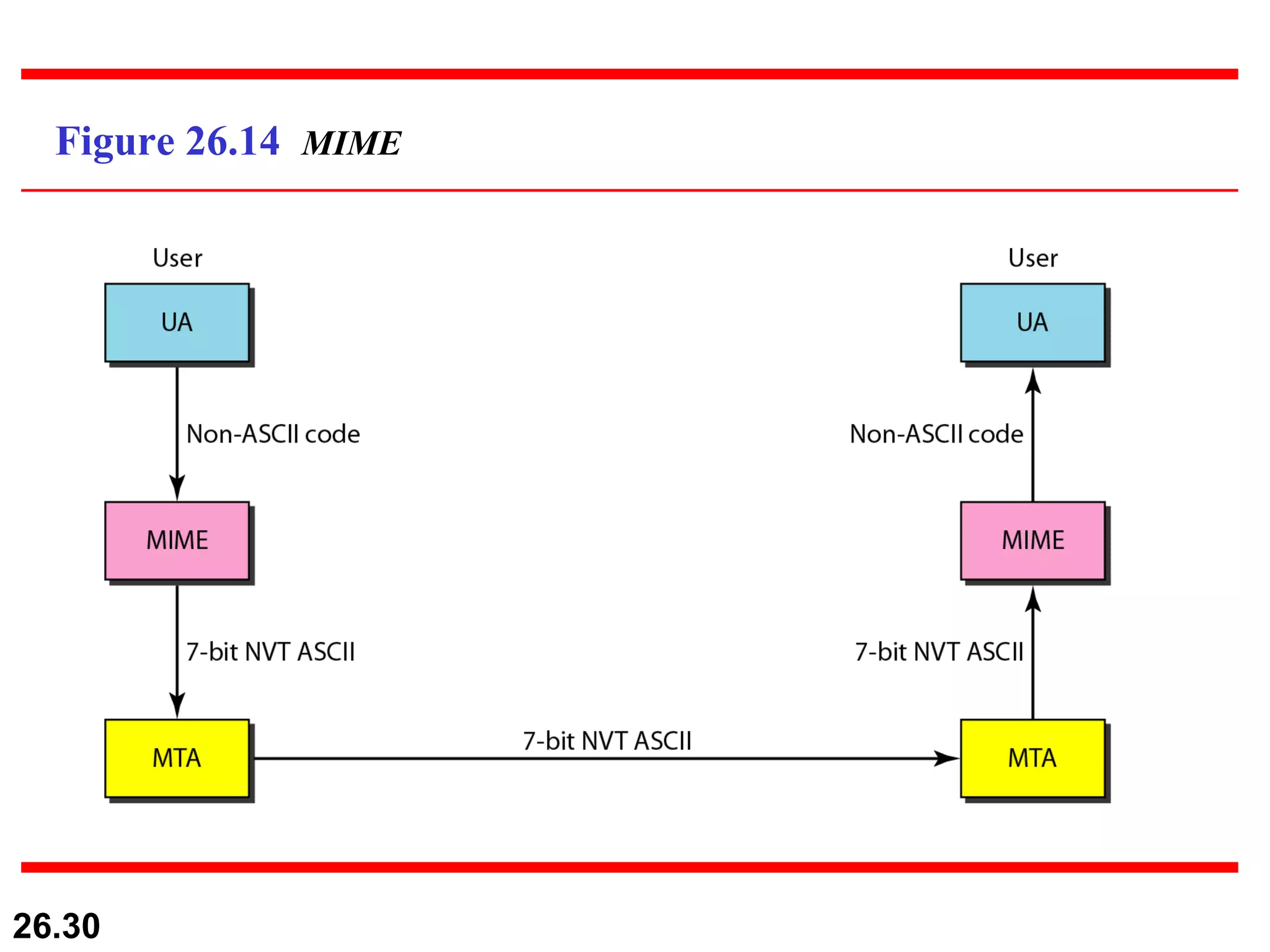
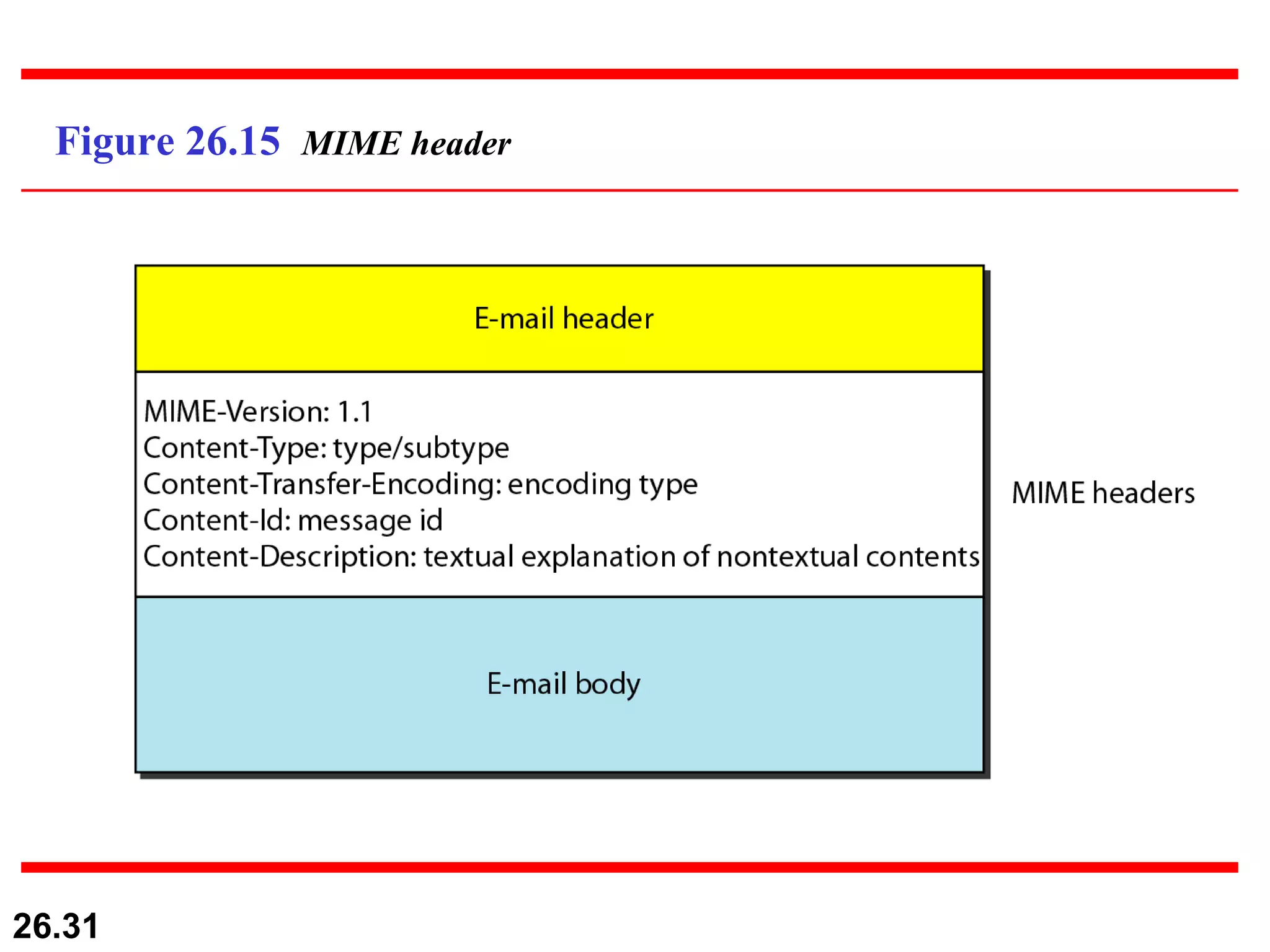
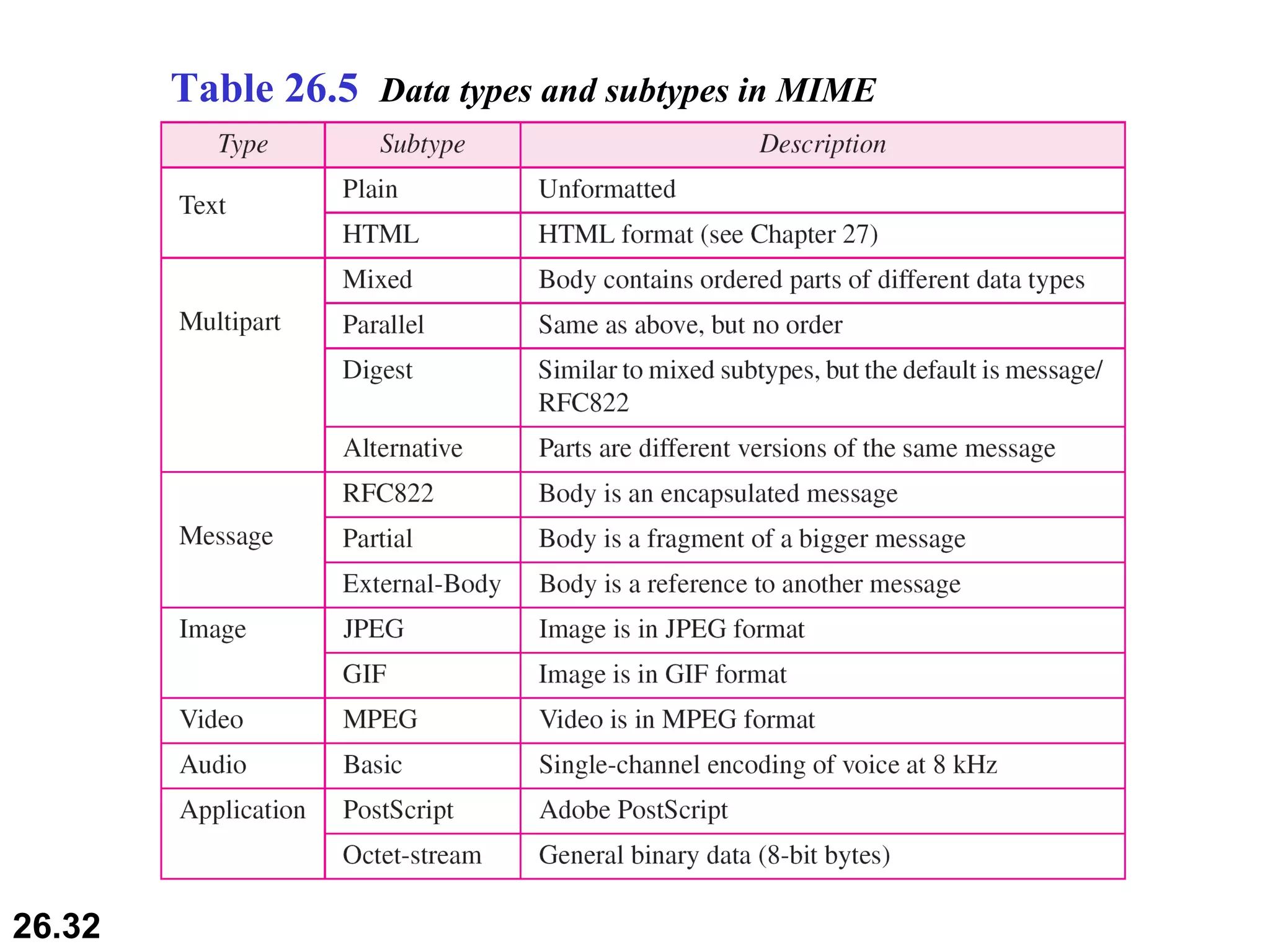
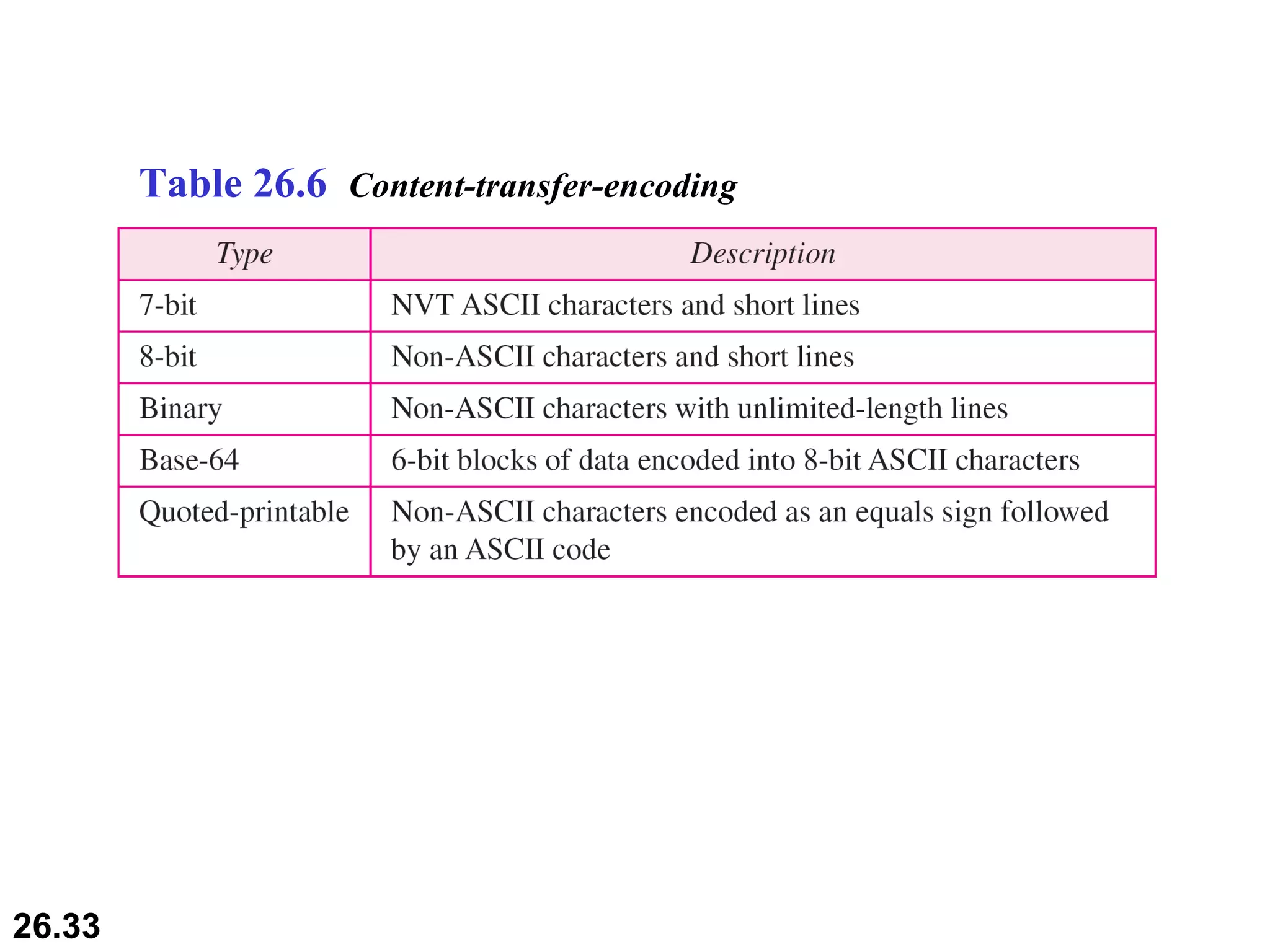
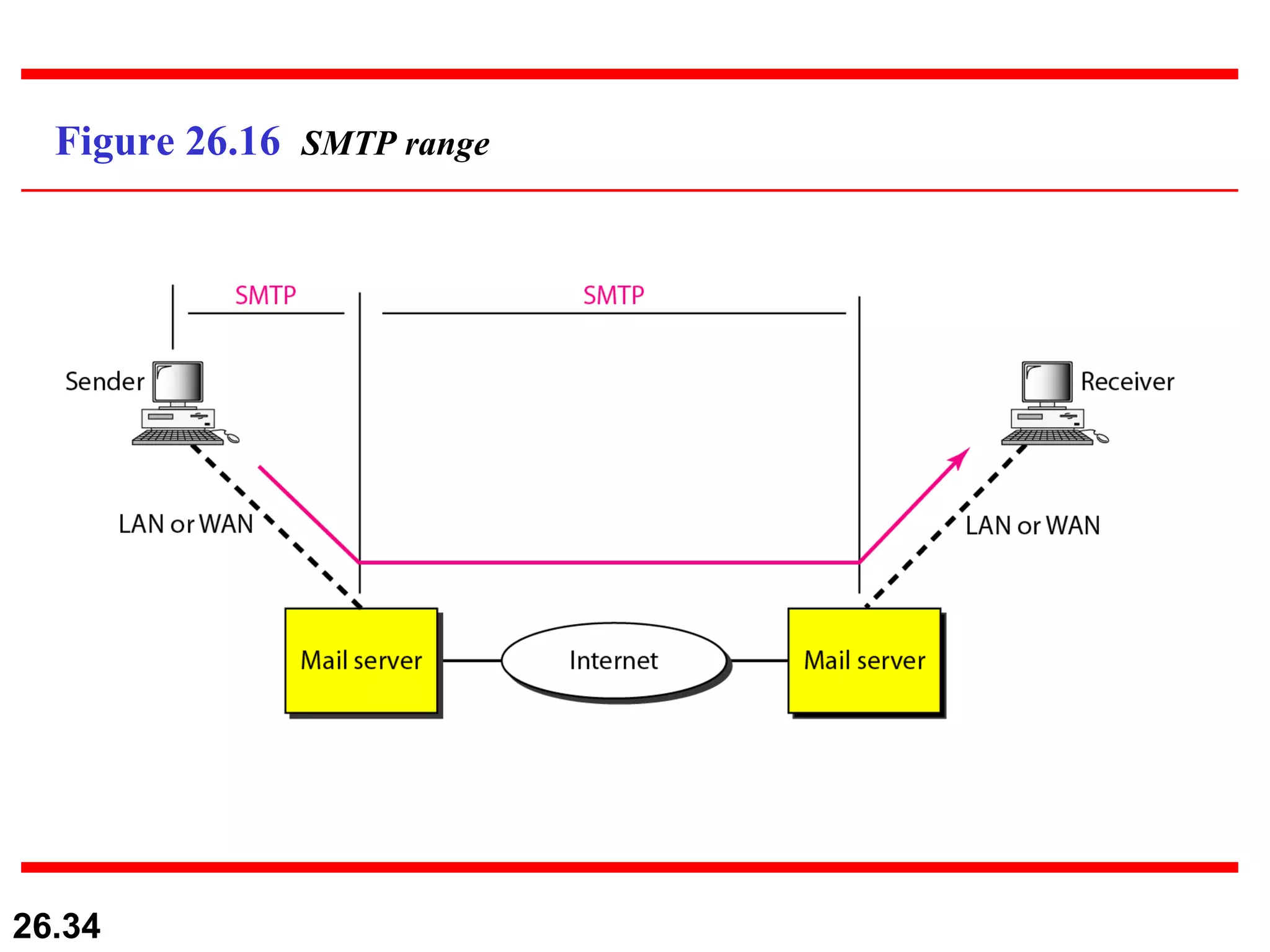
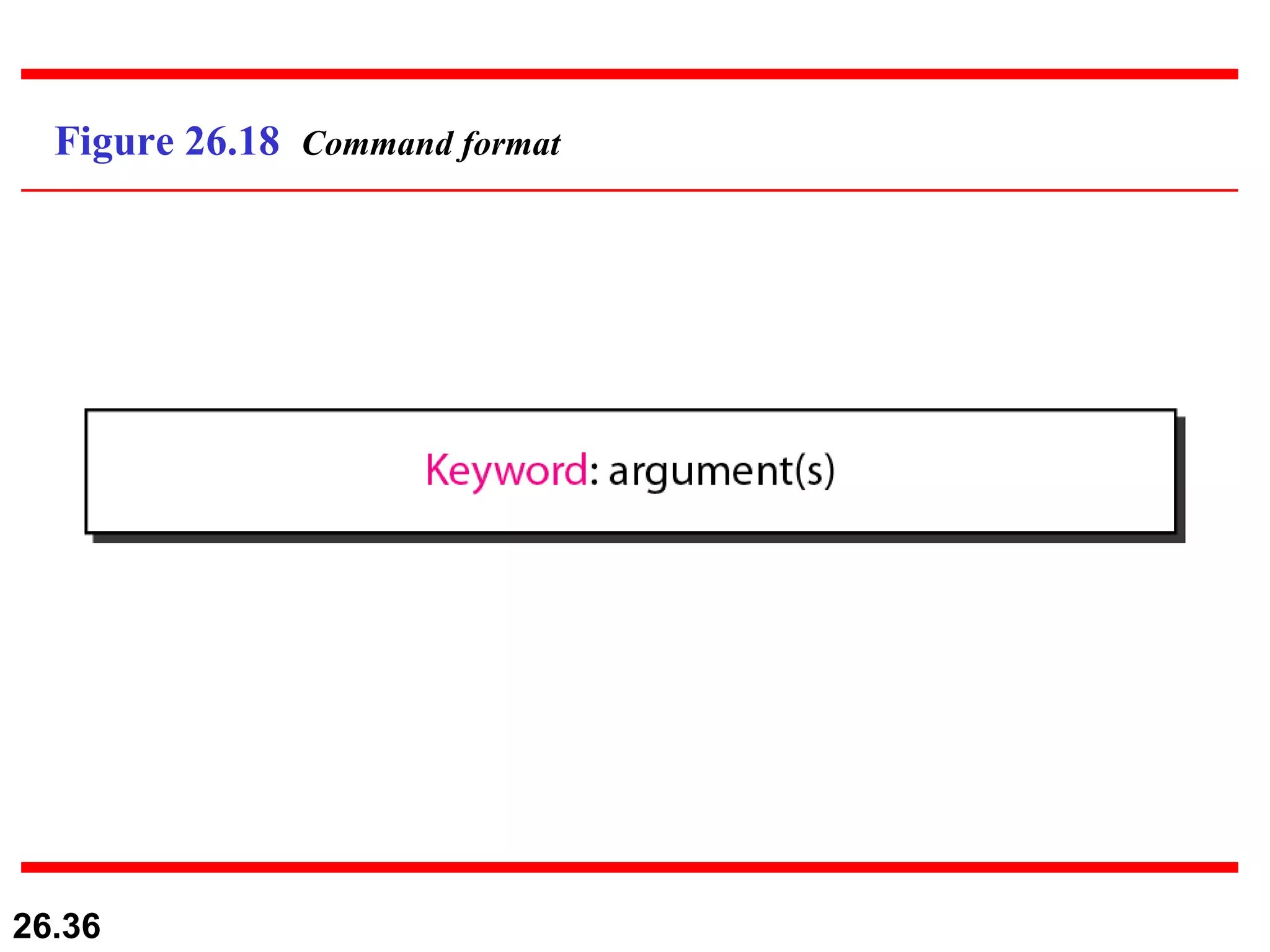
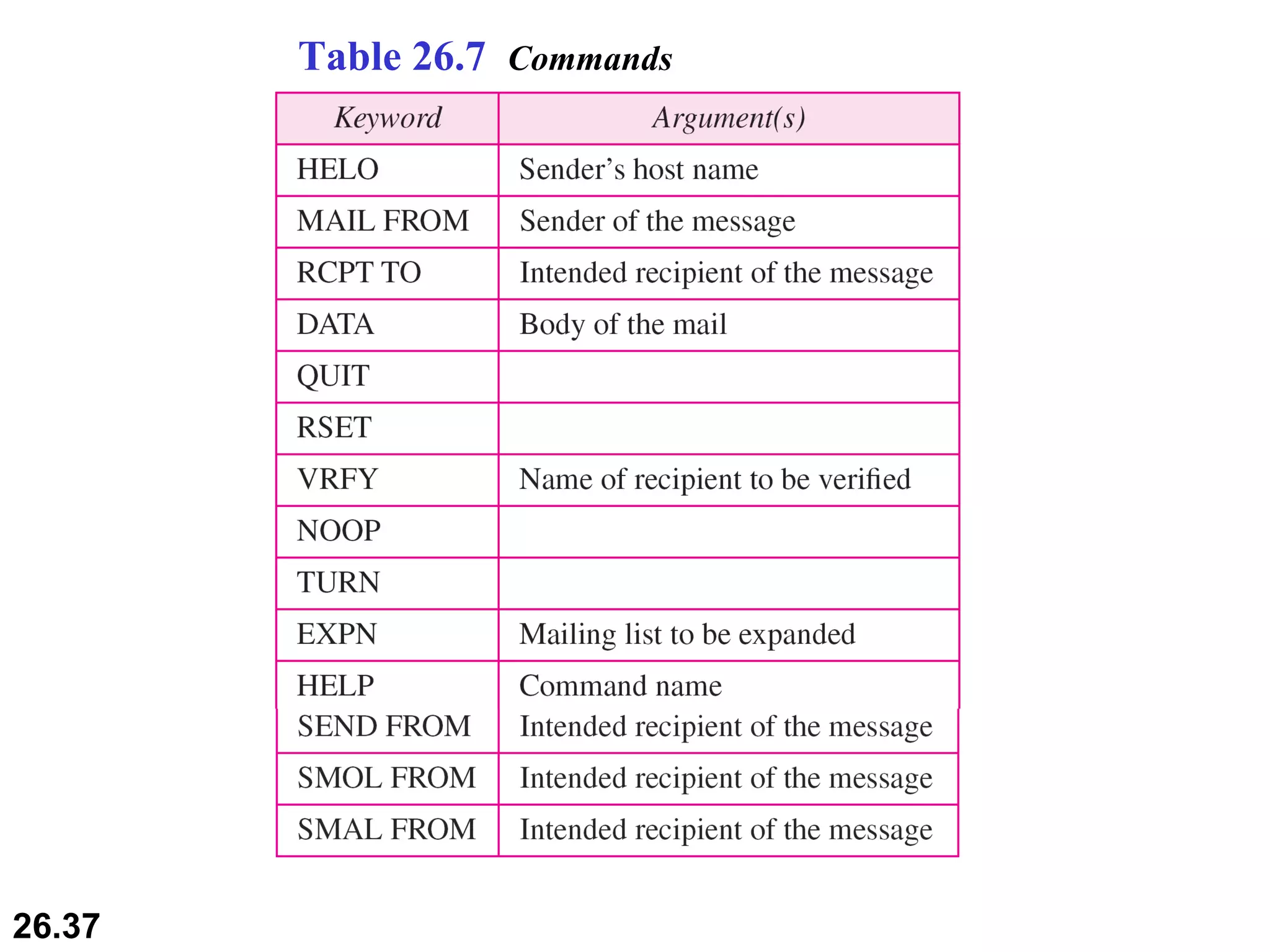
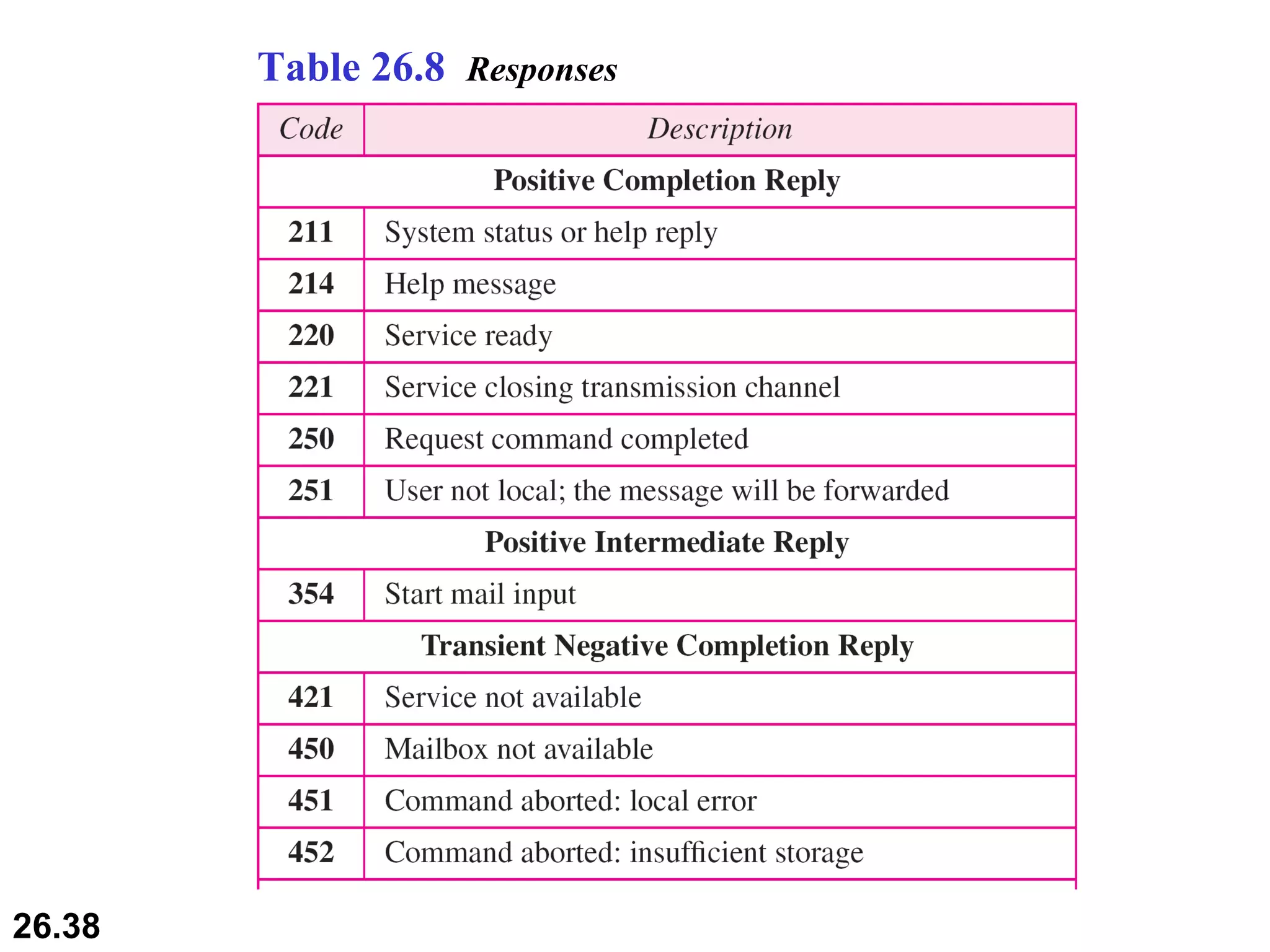
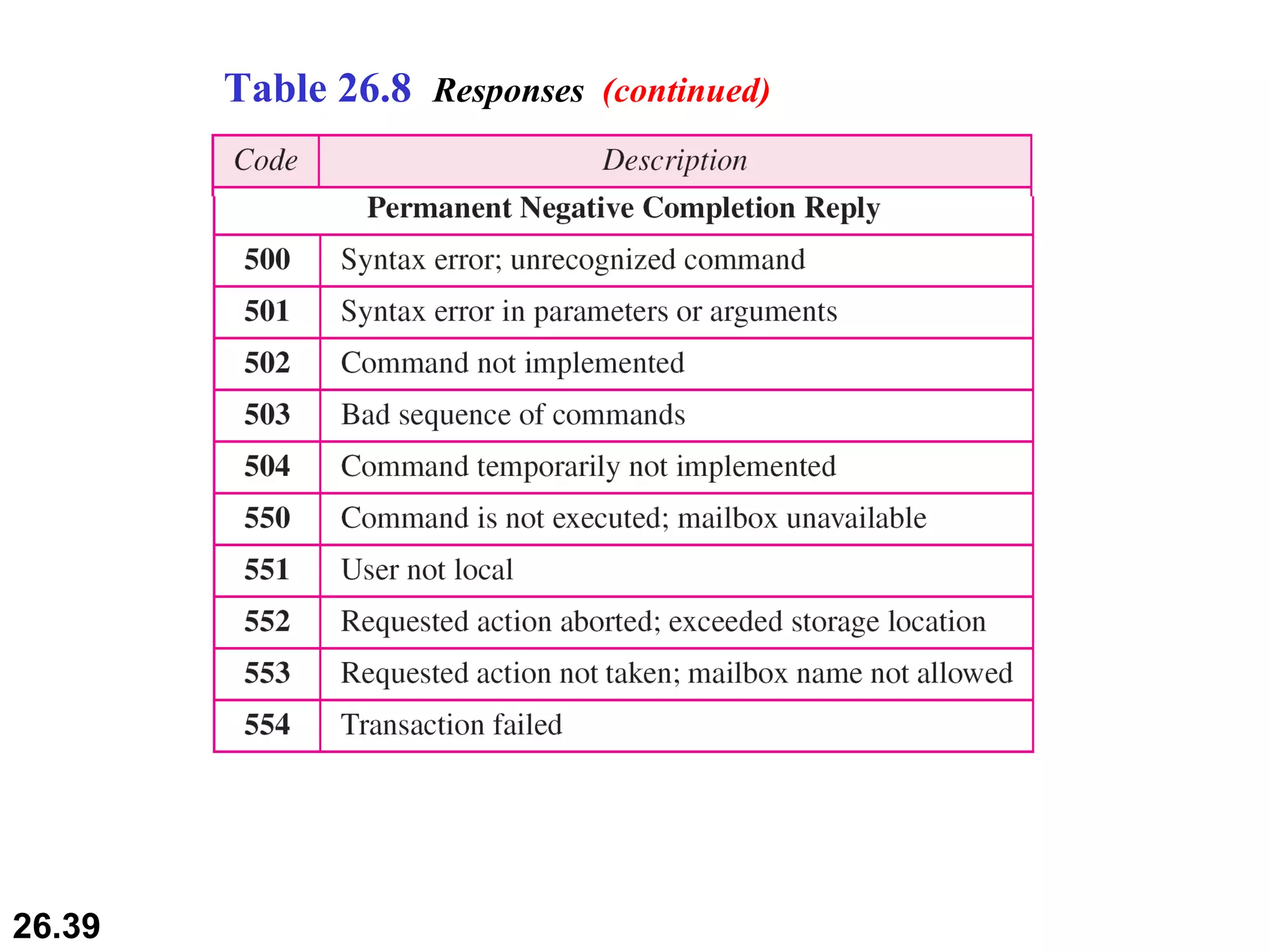
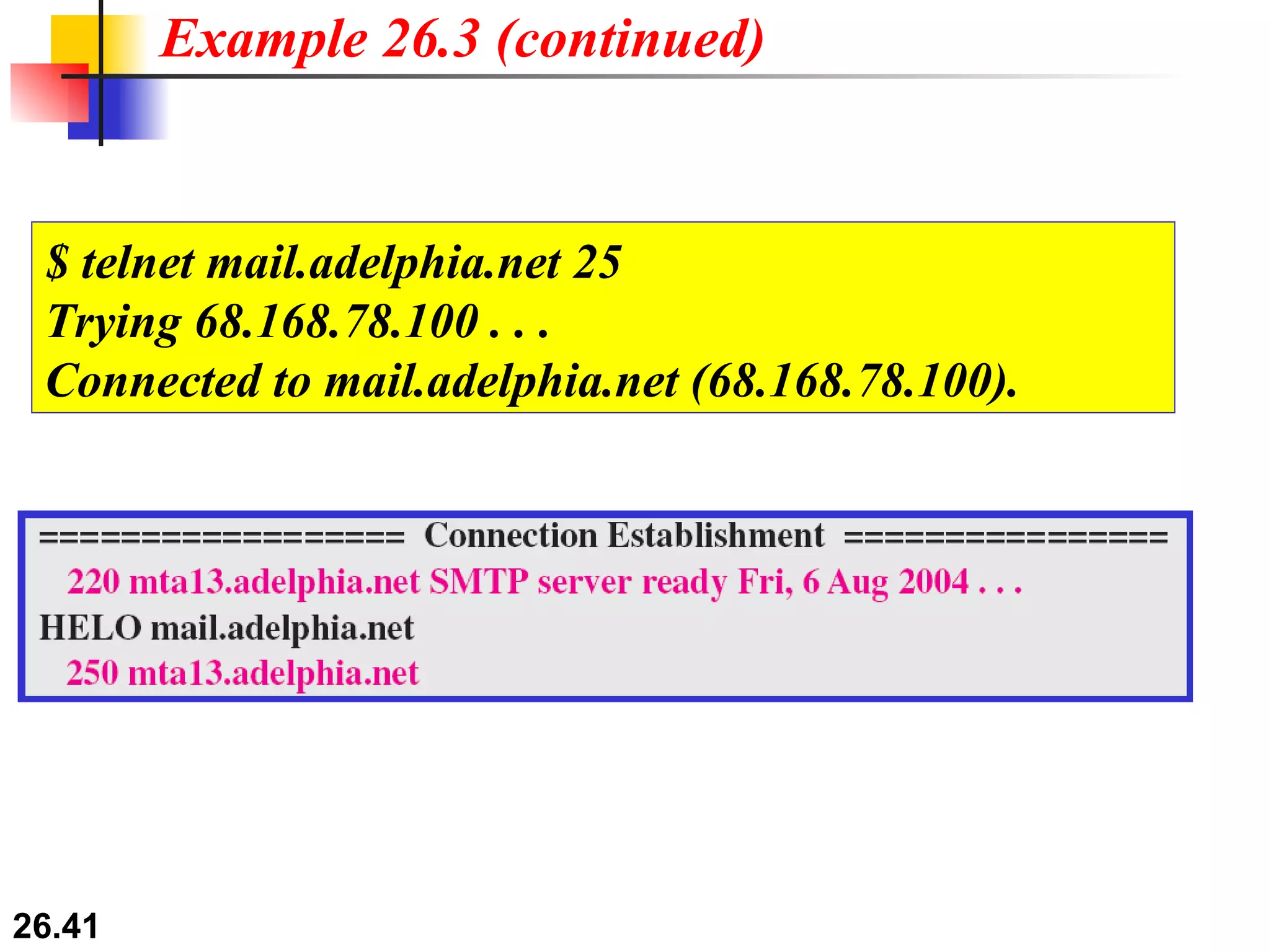
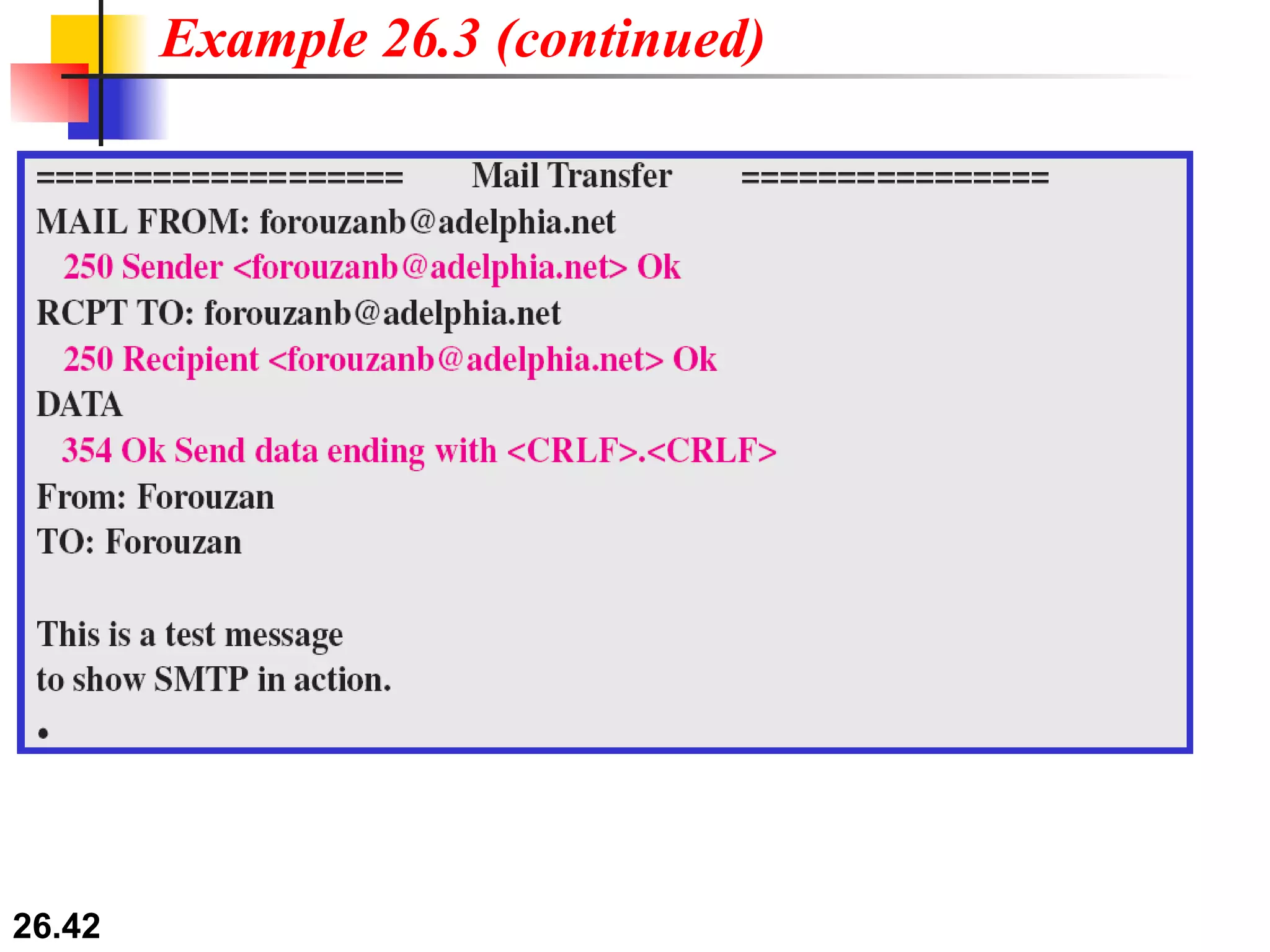
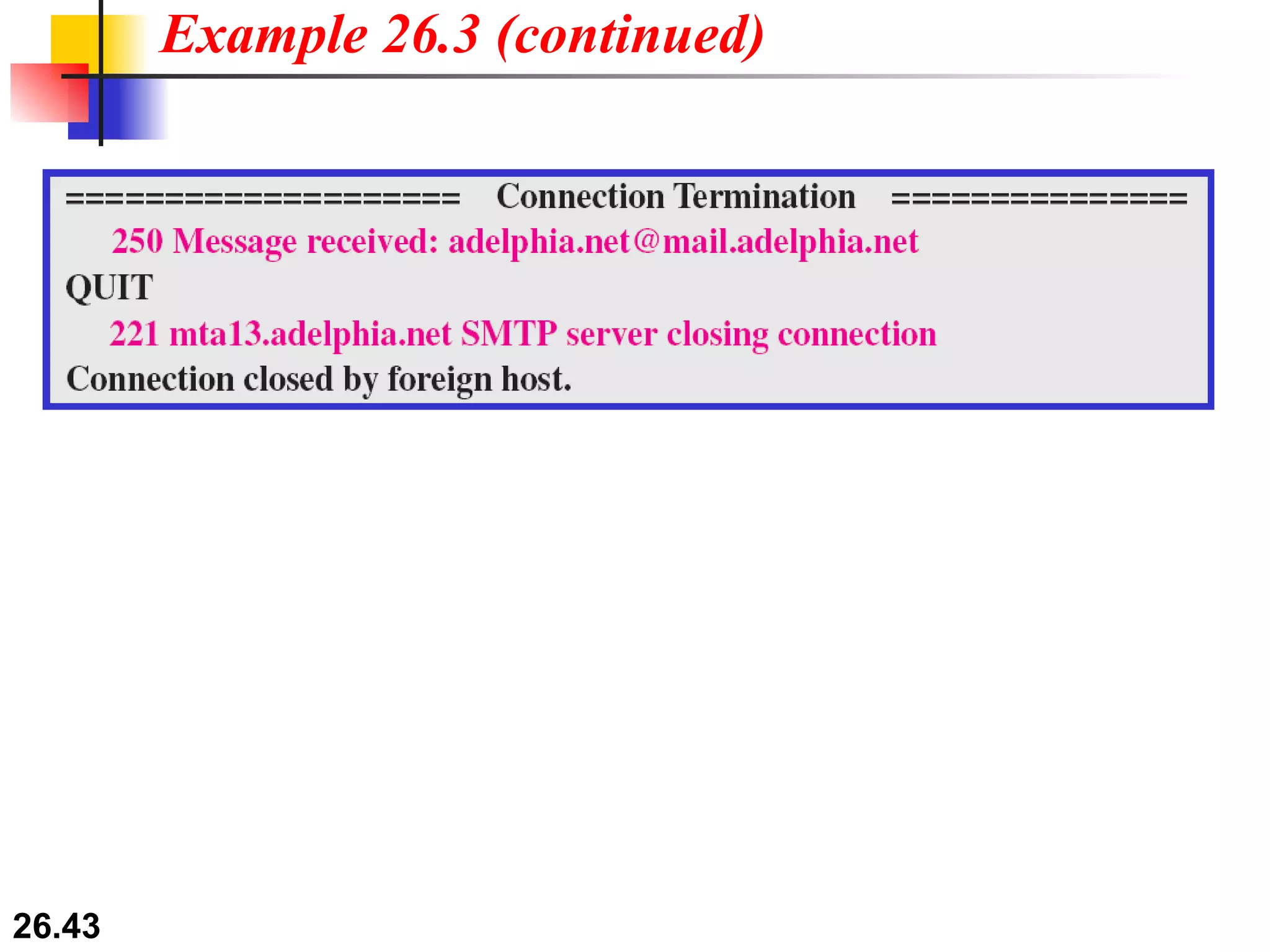
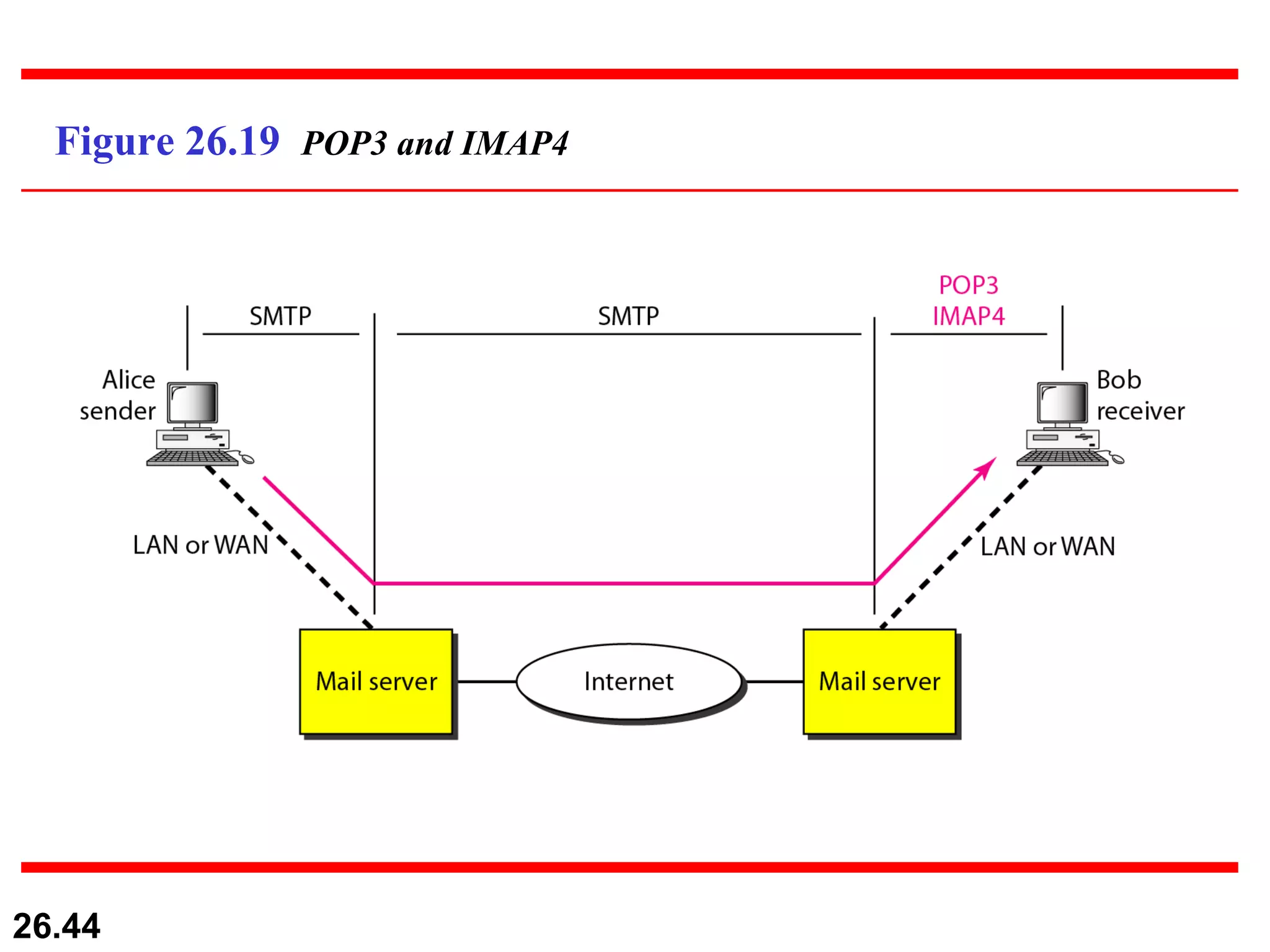
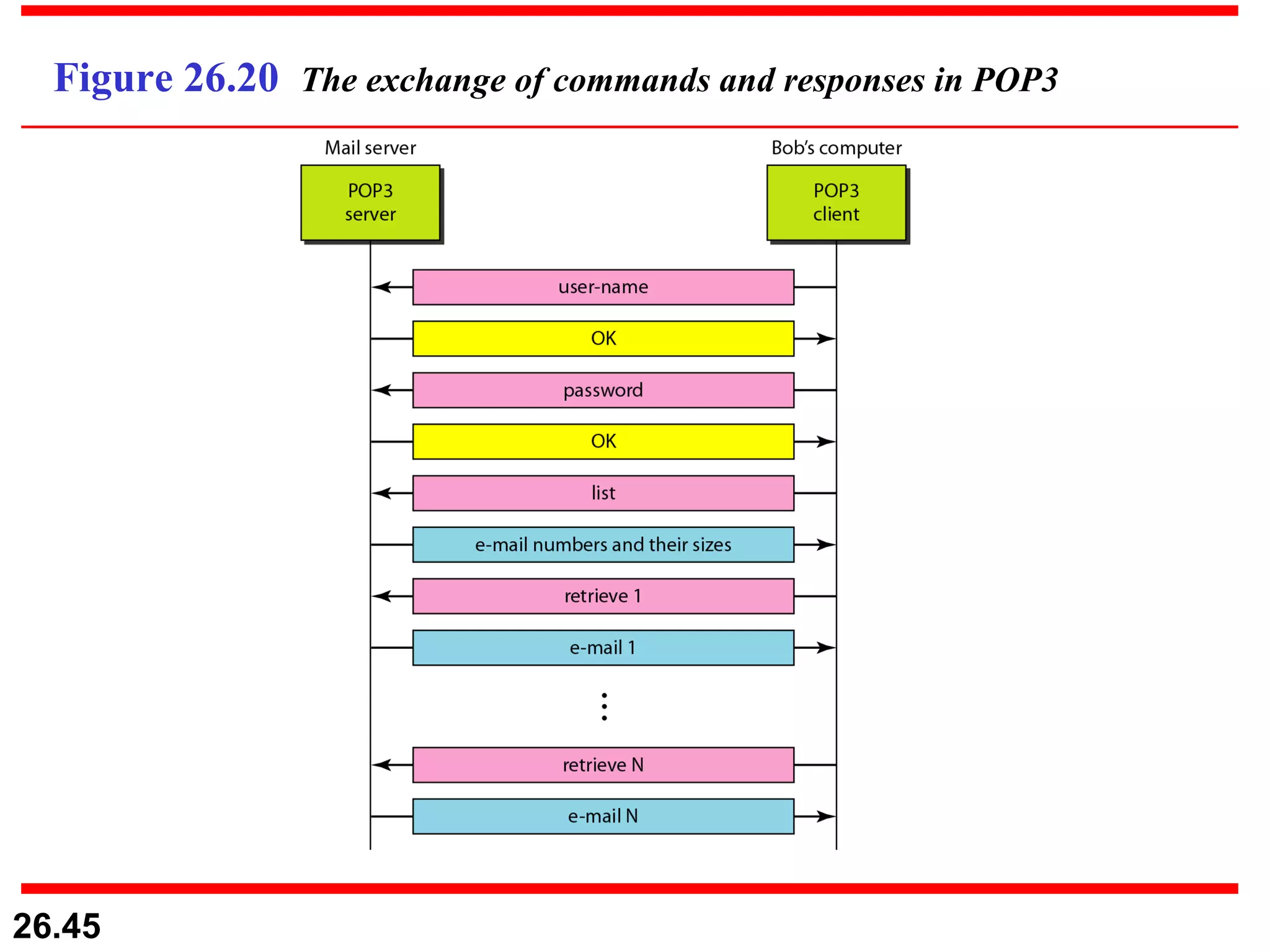
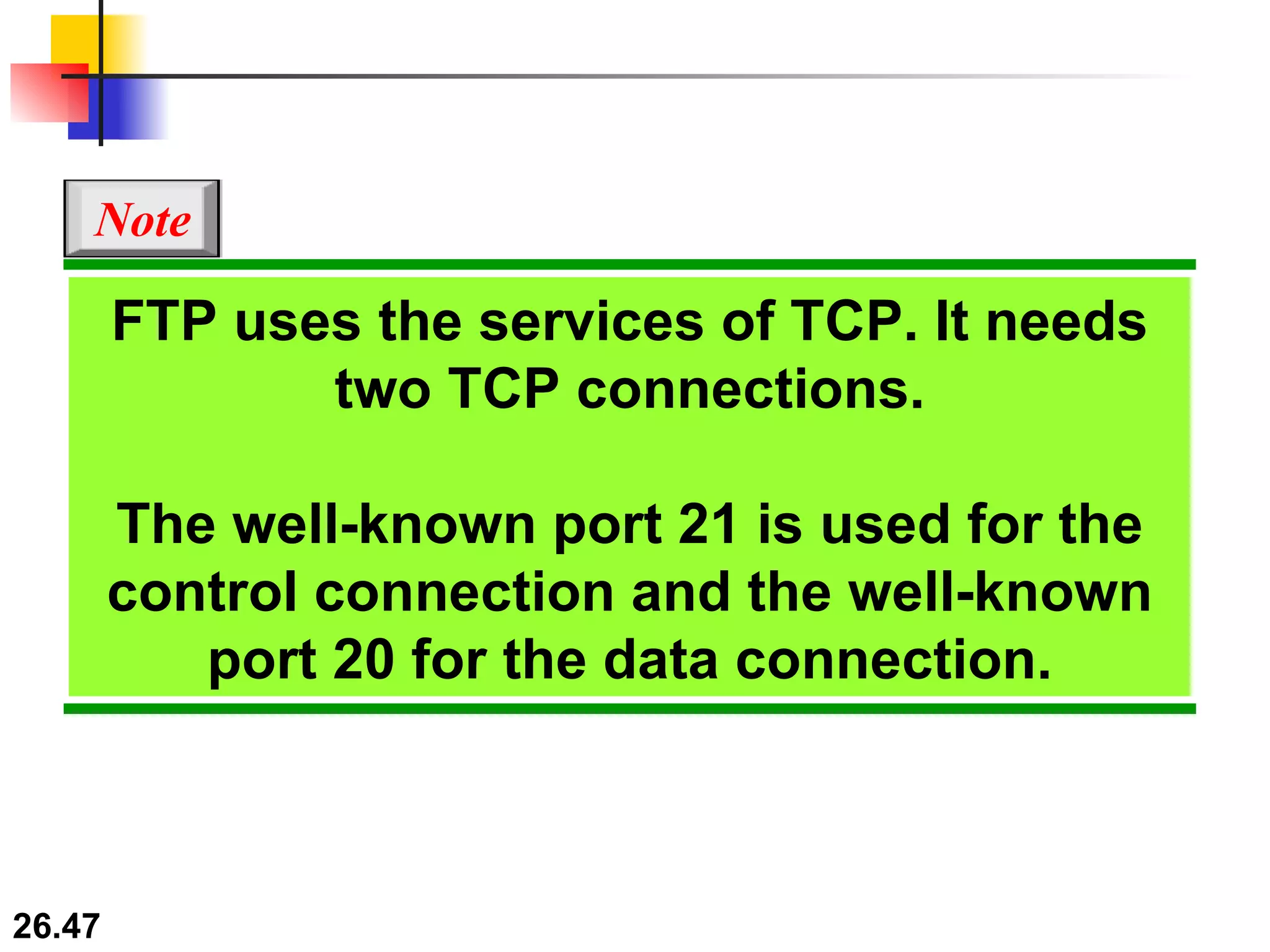
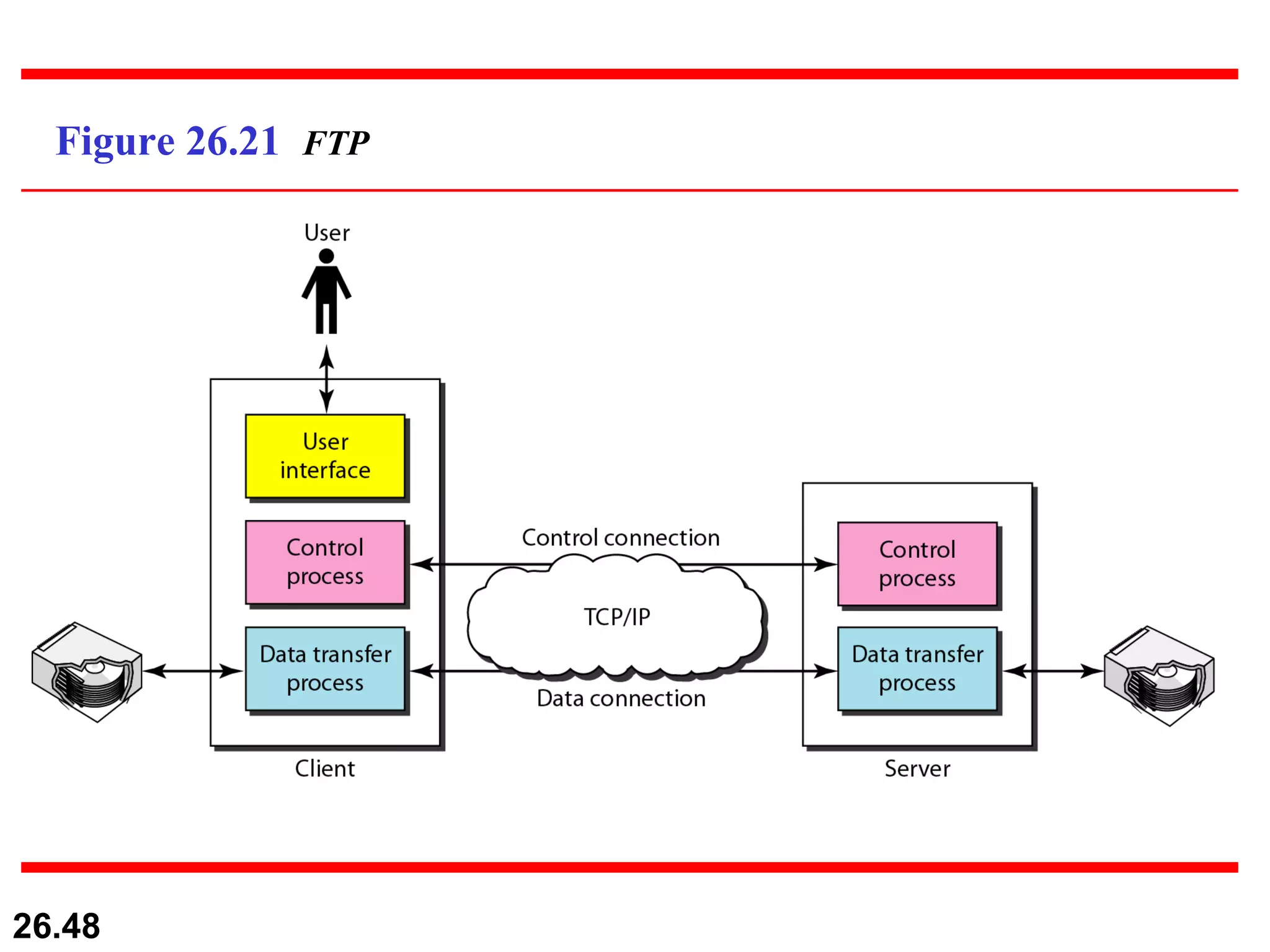
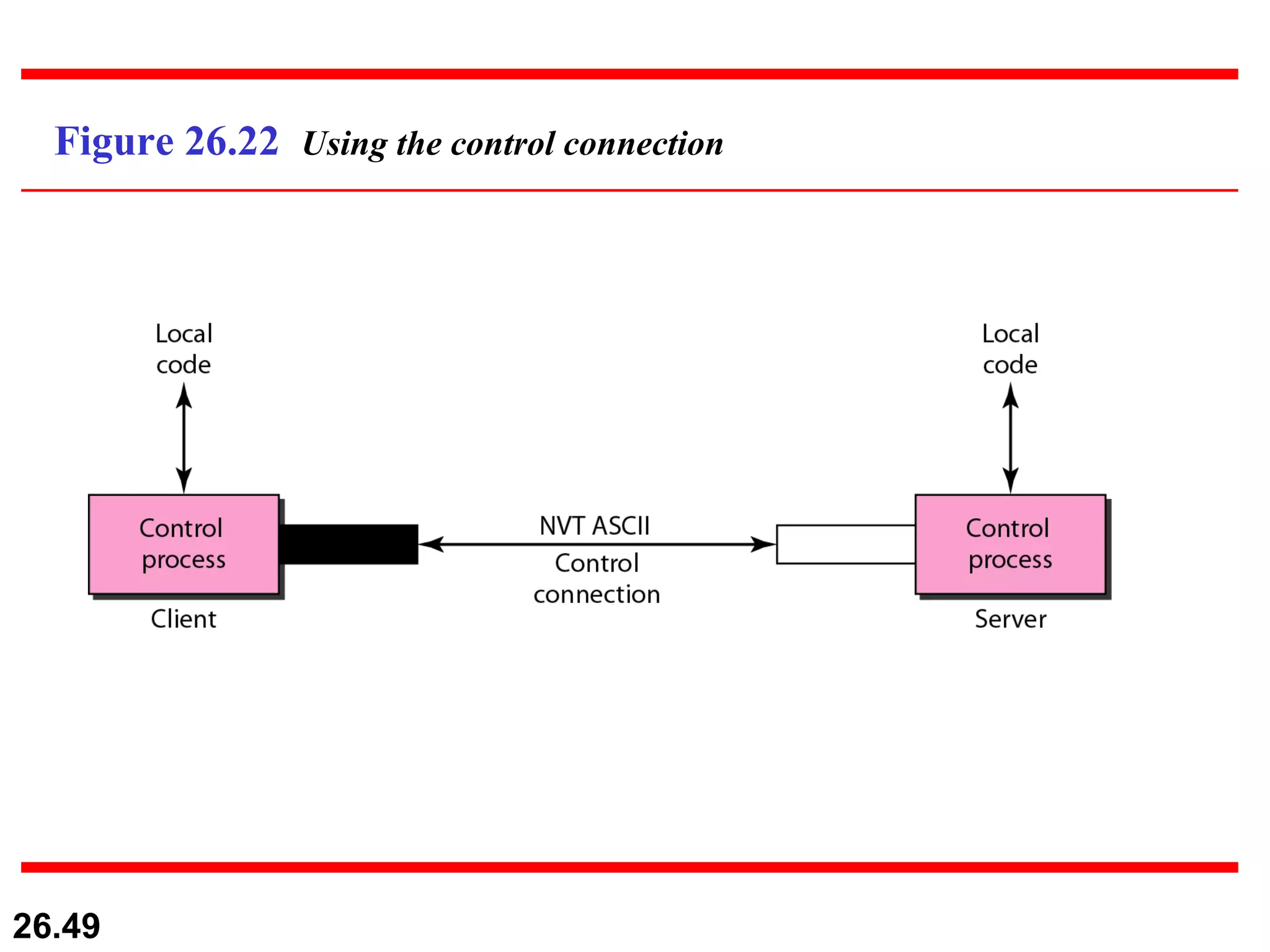
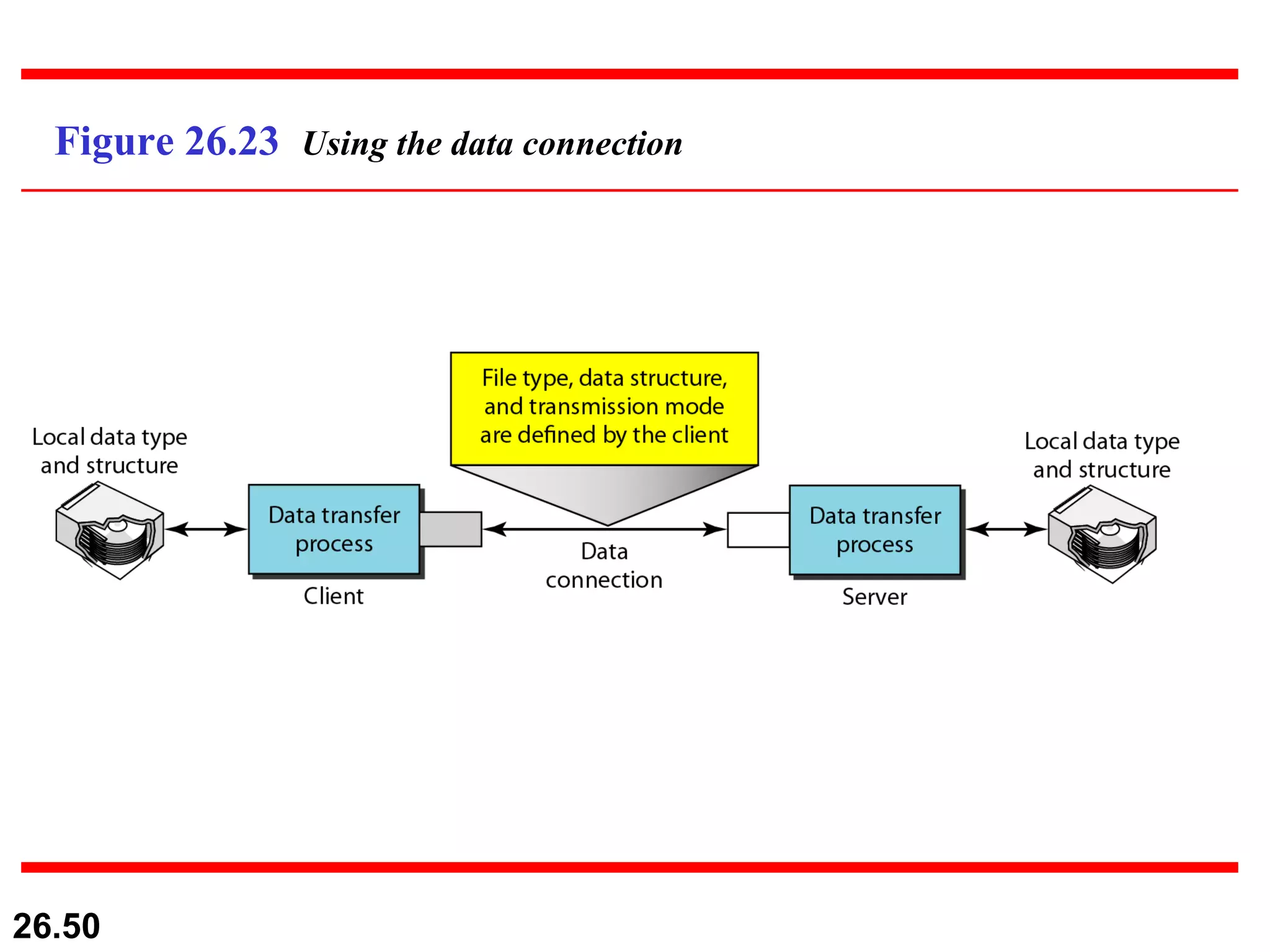
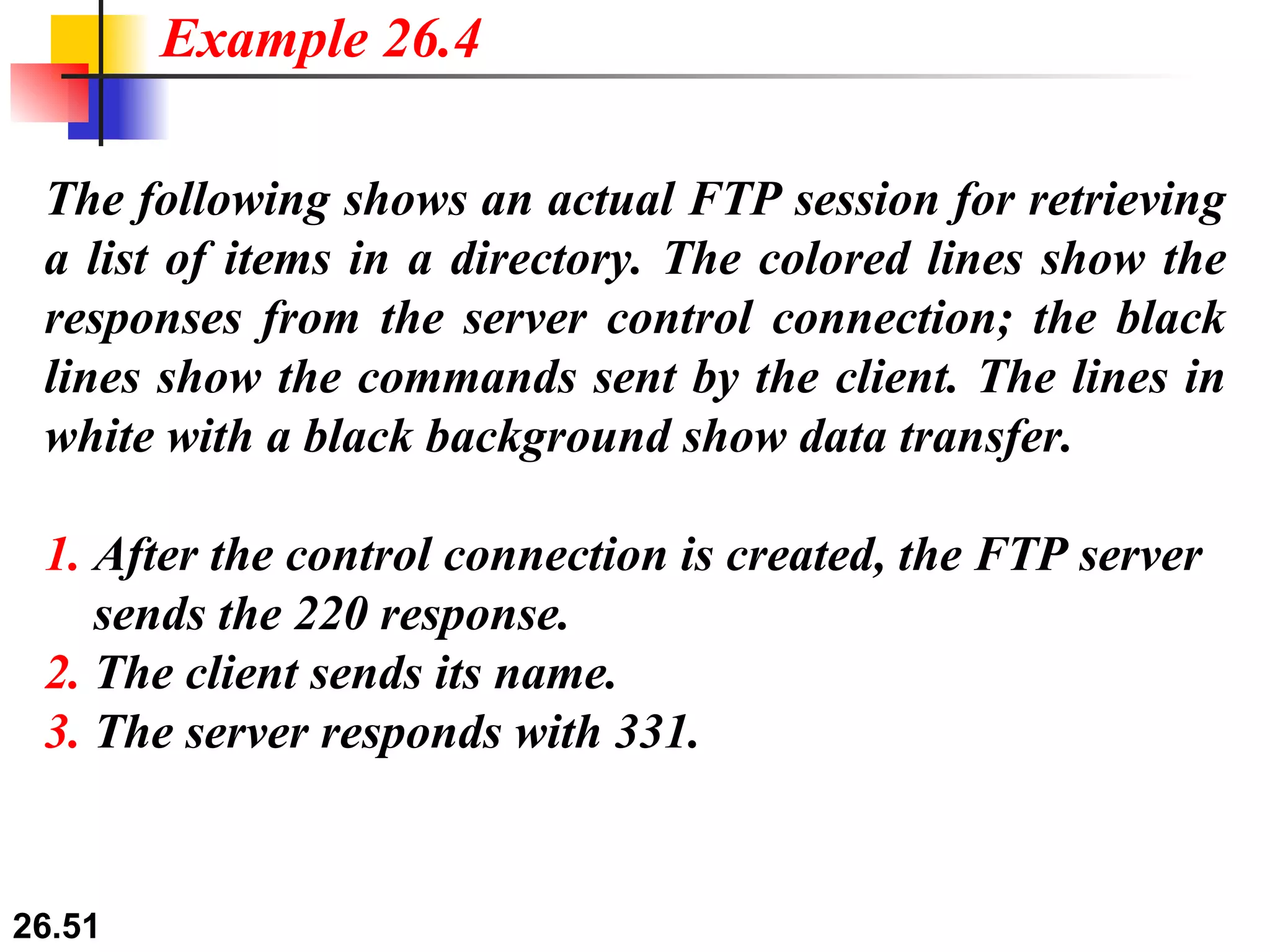
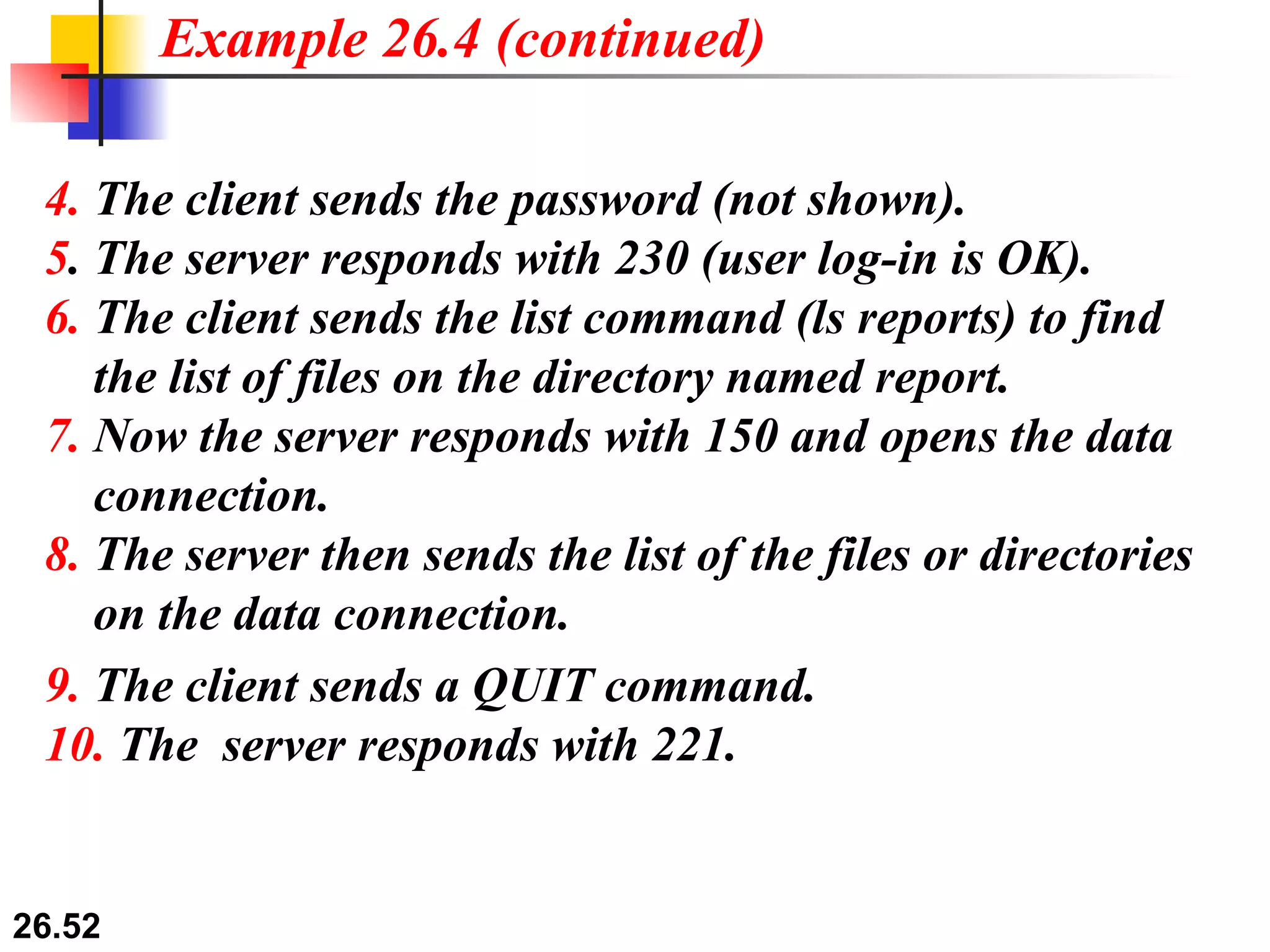
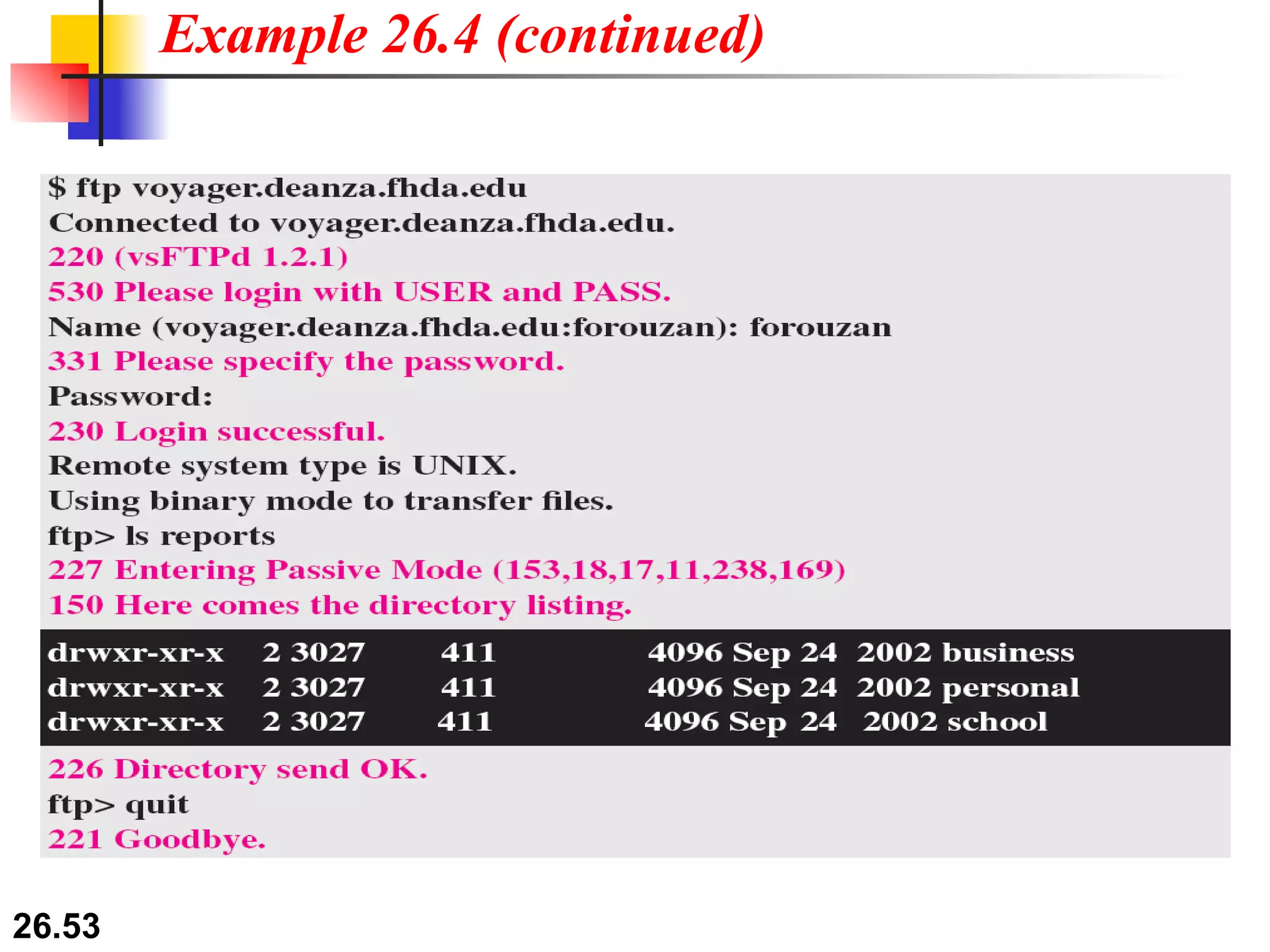
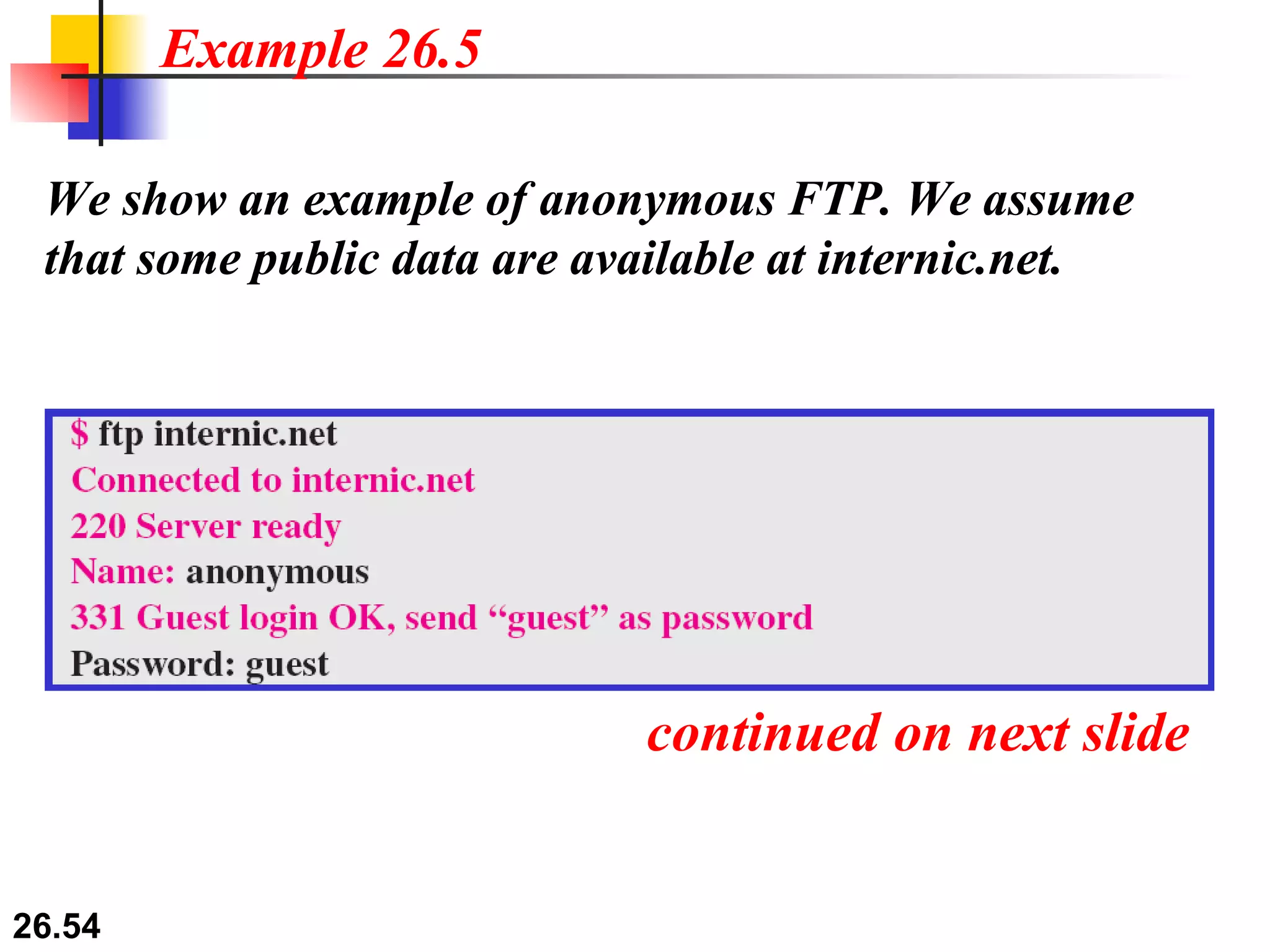
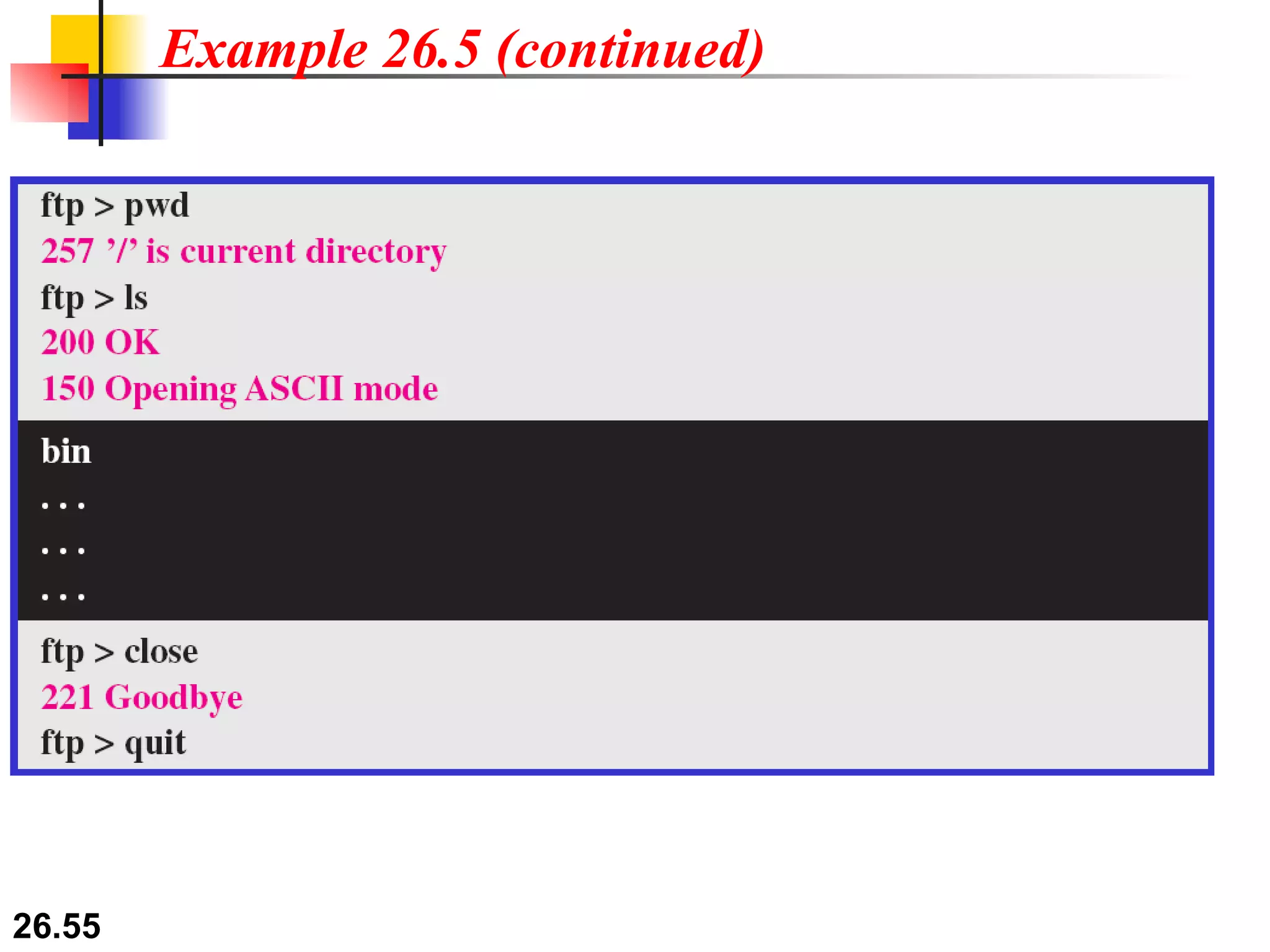
TELNET is a general-purpose client/server application that allows users to access applications on remote computers. Electronic mail is one of the most popular Internet services, using user agents, message transfer agents, and message access agents. File Transfer Protocol (FTP) allows transferring files between computers using separate TCP connections for control commands and data transfer.