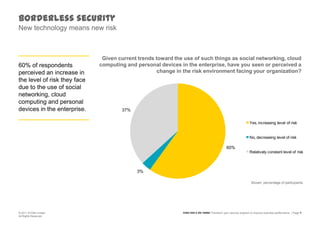
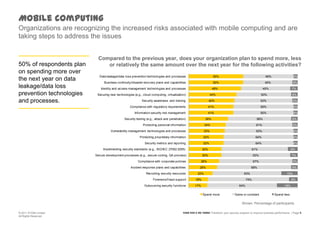
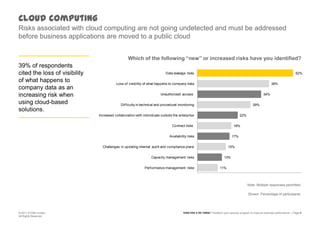
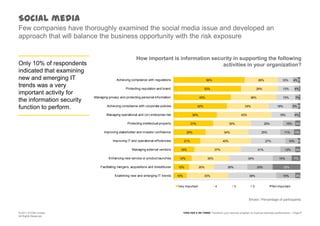
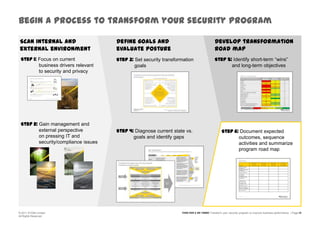
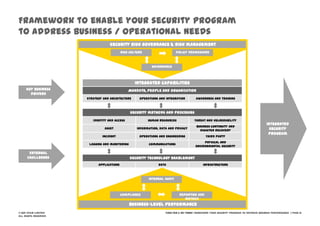
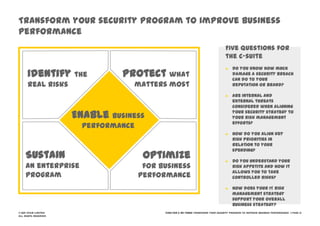
The document discusses information security challenges in today's borderless world of increased mobile and cloud computing use. It notes that while organizations recognize new risks from these technologies, many are not adjusting policies or security awareness accordingly. The presentation recommends that organizations establish comprehensive risk management programs, conduct risk assessments, take an information-centric view of security, and increase security controls, awareness and outsourcing to address risks from mobile, cloud and social media use. It also provides a framework to transform security programs to better protect important data and enable business needs.