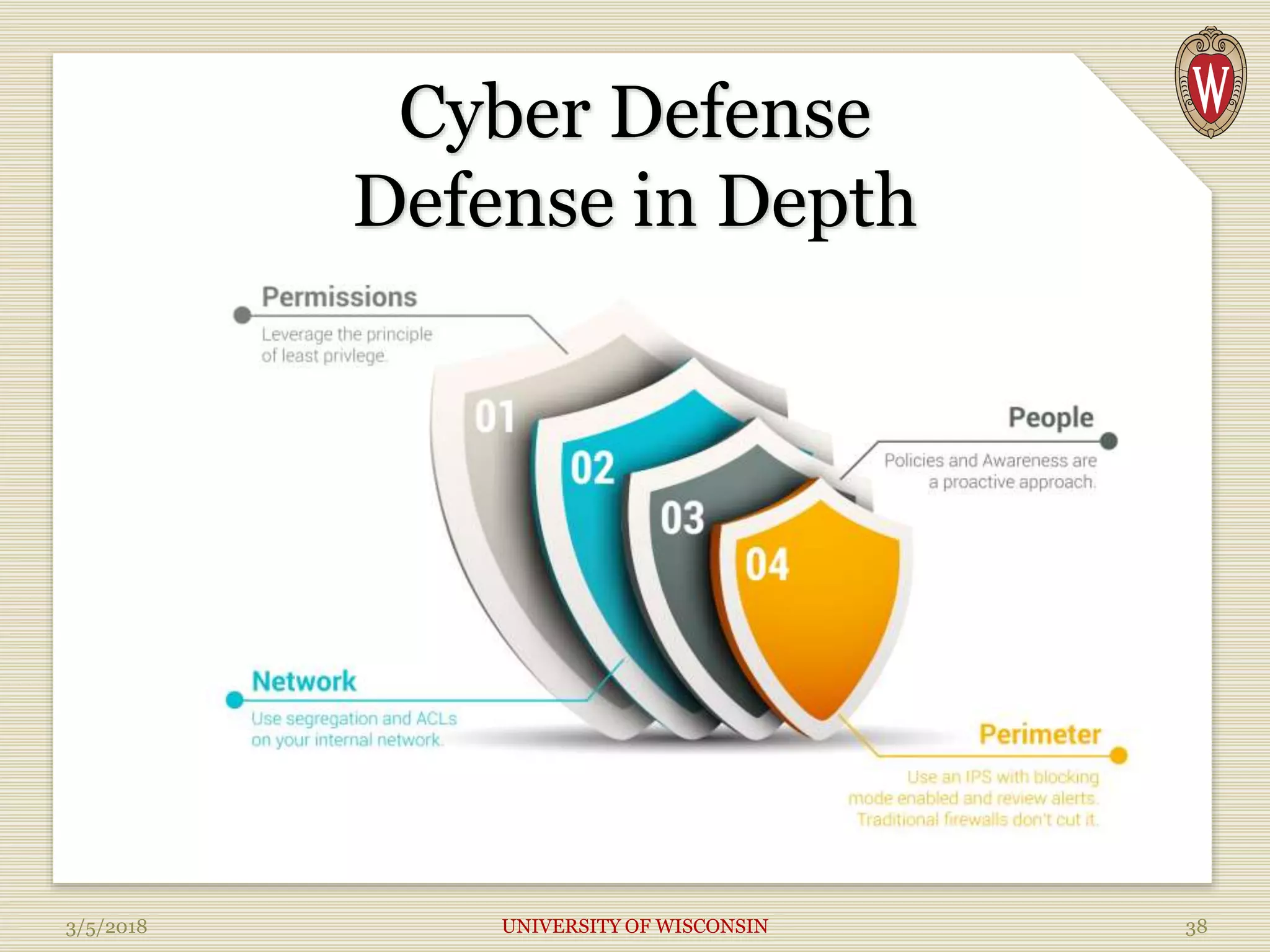
The document discusses the significance of cyberwarfare, highlighting how reliant society is on information technology, which can be manipulated and attacked. It outlines various types of cyber offenses and attacks, the challenges faced in detecting and preventing these threats, and the necessary changes for effective cyber defense. Additionally, it emphasizes the personal impact of cyberwarfare and the importance of establishing a stronger digital identity and chain of custody.