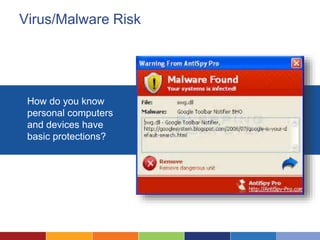
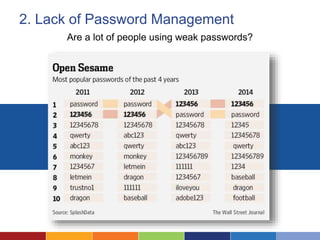
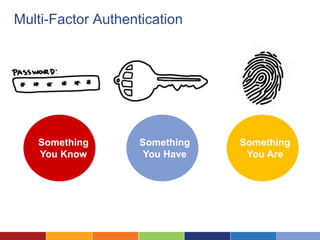
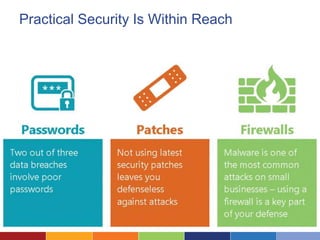
The document discusses the importance of data security for nonprofits, highlighting common risks, risky practices, and strategies to mitigate potential data breaches. It outlines steps for assessing security risks, establishing policies, and implementing better practices like password management and secure cloud storage. Additionally, it emphasizes the need for regular training and the creation of incident response plans to ensure organizational preparedness against security threats.