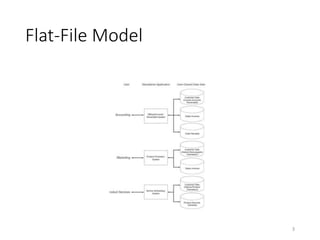
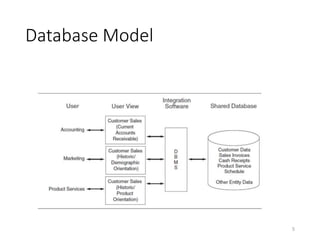
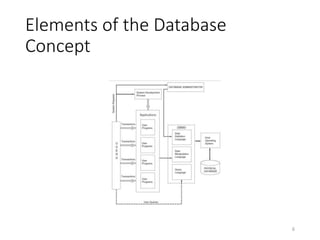
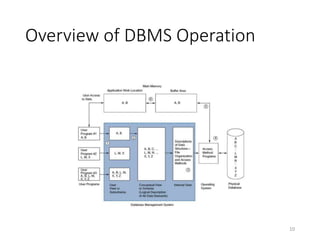
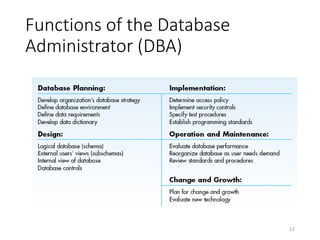
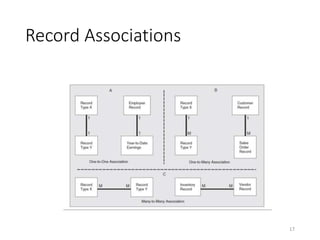
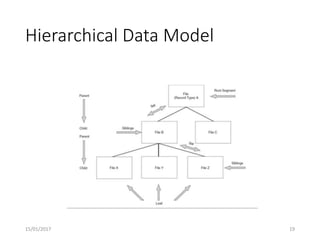
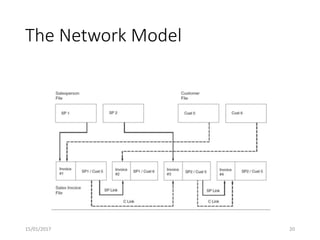
This document discusses database systems and auditing databases. It covers the problems with flat file data management that led to database systems, the components and models of databases including hierarchical, network and relational models. It also discusses centralized, partitioned and replicated database deployment, database administration, access controls, backup controls and audit procedures for testing controls.