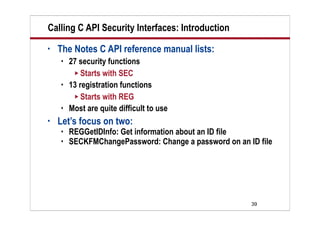
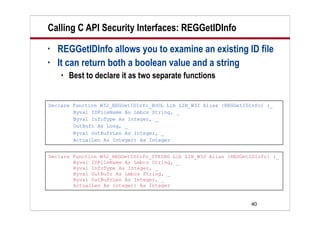
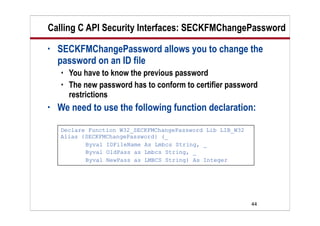
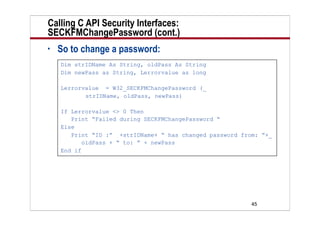
This document provides an overview of using the Lotus Notes C API security interfaces from LotusScript. It discusses two specific C API functions - REGGetIDInfo and SECKFMChangePassword. REGGetIDInfo allows you to examine an existing ID file and retrieve information such as whether it is hierarchical or a certifier. SECKFMChangePassword is used to change a password on an ID file. The document includes LotusScript code examples for calling these functions and retrieving the returned values. It defines several constants needed to specify the type of information to retrieve from the ID file.




















![29
Application Roles Layer
• Roles are set within the ACL and:
Allow internal-application “grouping” of users
Are usually used to allow access to:
Particular design elements
Reader/Author fields in documents
For instance, applications usually have “Administrator” roles
@IsMember(“[Administrator]”; @userRoles)](https://image.slidesharecdn.com/devbuchaneverythingyouneedtoknowaboutagentdesign-130608162733-phpapp01/85/Dev-buchan-everything-you-need-to-know-about-agent-design-29-320.jpg)
![30
Reader/Author Fields Layer
• Reader fields dictate who is allowed to read this
document
• Author fields dictate who is allowed to modify a
document, if their ACL level is set to “Author”
• You may have more than one Reader/Author field in a
document
• You may have more than one item in the field
• You may embed Roles into this field
e.g., “[Administrators]”: “LocalDomainAdmins”: “*/Acme”](https://image.slidesharecdn.com/devbuchaneverythingyouneedtoknowaboutagentdesign-130608162733-phpapp01/85/Dev-buchan-everything-you-need-to-know-about-agent-design-30-320.jpg)
![31
Reader/Author Fields: Best Practices
• Common mistakes include:
Losing access to documents
NOT setting the Reader/Access field as an Array from
LotusScript
“LocalDomainAdmins; [Administrators]” will NOT work!
Not setting the Reader/Author field flag in LotusScript
Not using canonicalized names in fields
Trying to use only one Reader/Author field
• There are lots of programmers out there who do NOT
know how to do this
Don’t be one of those!](https://image.slidesharecdn.com/devbuchaneverythingyouneedtoknowaboutagentdesign-130608162733-phpapp01/85/Dev-buchan-everything-you-need-to-know-about-agent-design-31-320.jpg)
![32
Reader/Author Fields: Example
Public Function setAuthorsField( doc As NotesDocument, _
fieldName As String, newName As String) As Integer
Dim nn As New NotesName(newName)
Dim S(2) As String
S(0) = "LocalDomainAdmins"
S(1) = "[Administrators]"
S(2) = nn.Canonical
Dim itm As NotesItem
Set itm = doc.ReplaceItemValue(fieldName, S)
Itm.IsReaders = True
End Function](https://image.slidesharecdn.com/devbuchaneverythingyouneedtoknowaboutagentdesign-130608162733-phpapp01/85/Dev-buchan-everything-you-need-to-know-about-agent-design-32-320.jpg)