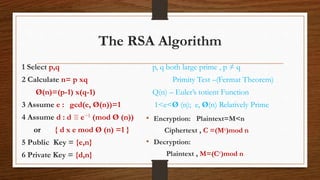
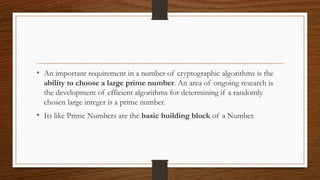
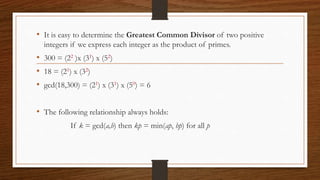
The document discusses the fundamental theorem of arithmetic and its application to the RSA algorithm. It states that every composite number can be uniquely factored into a product of prime numbers. It then explains the key steps of the RSA algorithm, which relies on selecting two large prime numbers and using their relationship to encrypt and decrypt messages. Finally, it discusses how the fundamental theorem relates to concepts like divisibility, greatest common divisors, and representing numbers as products of prime factors.