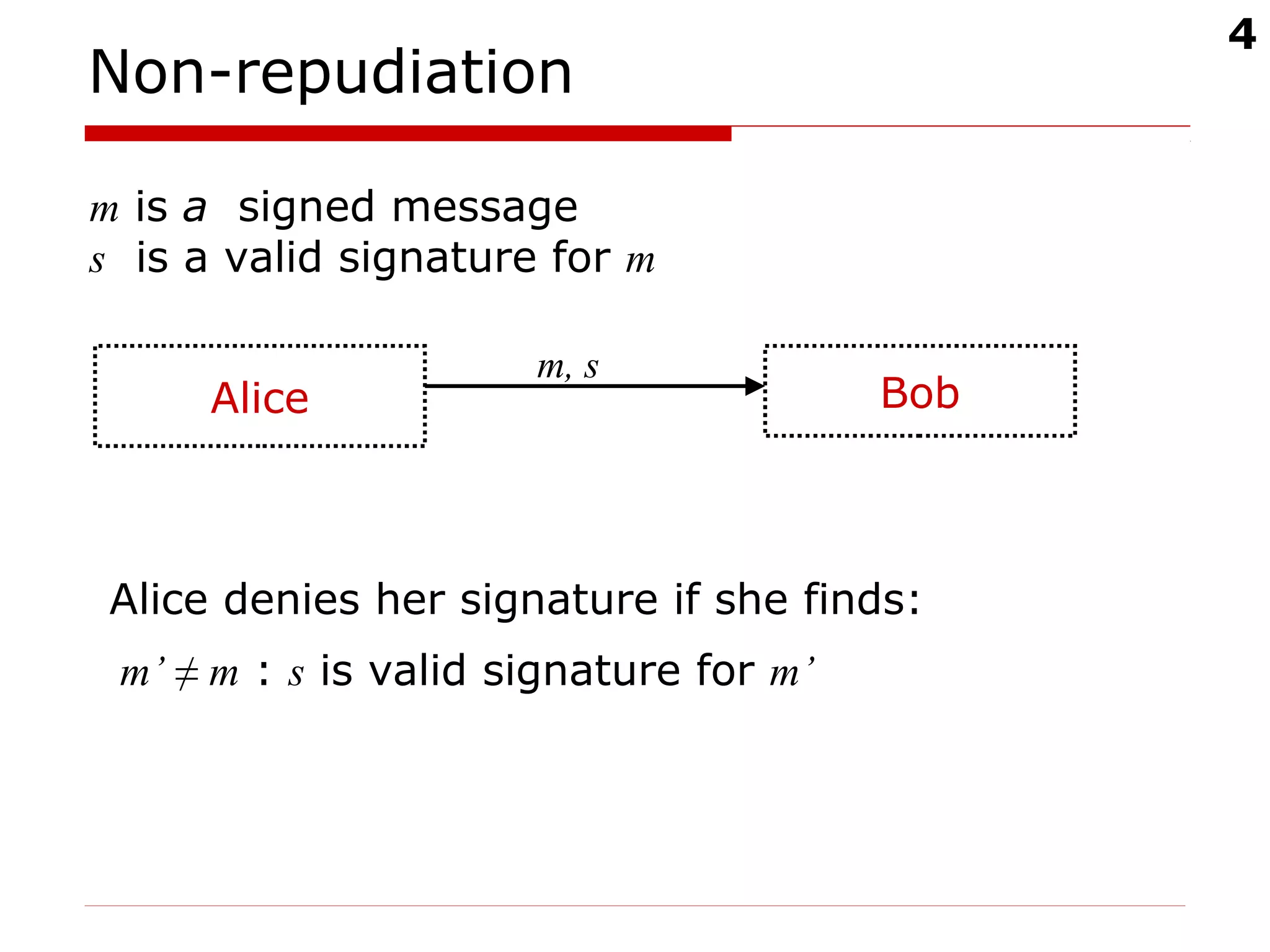
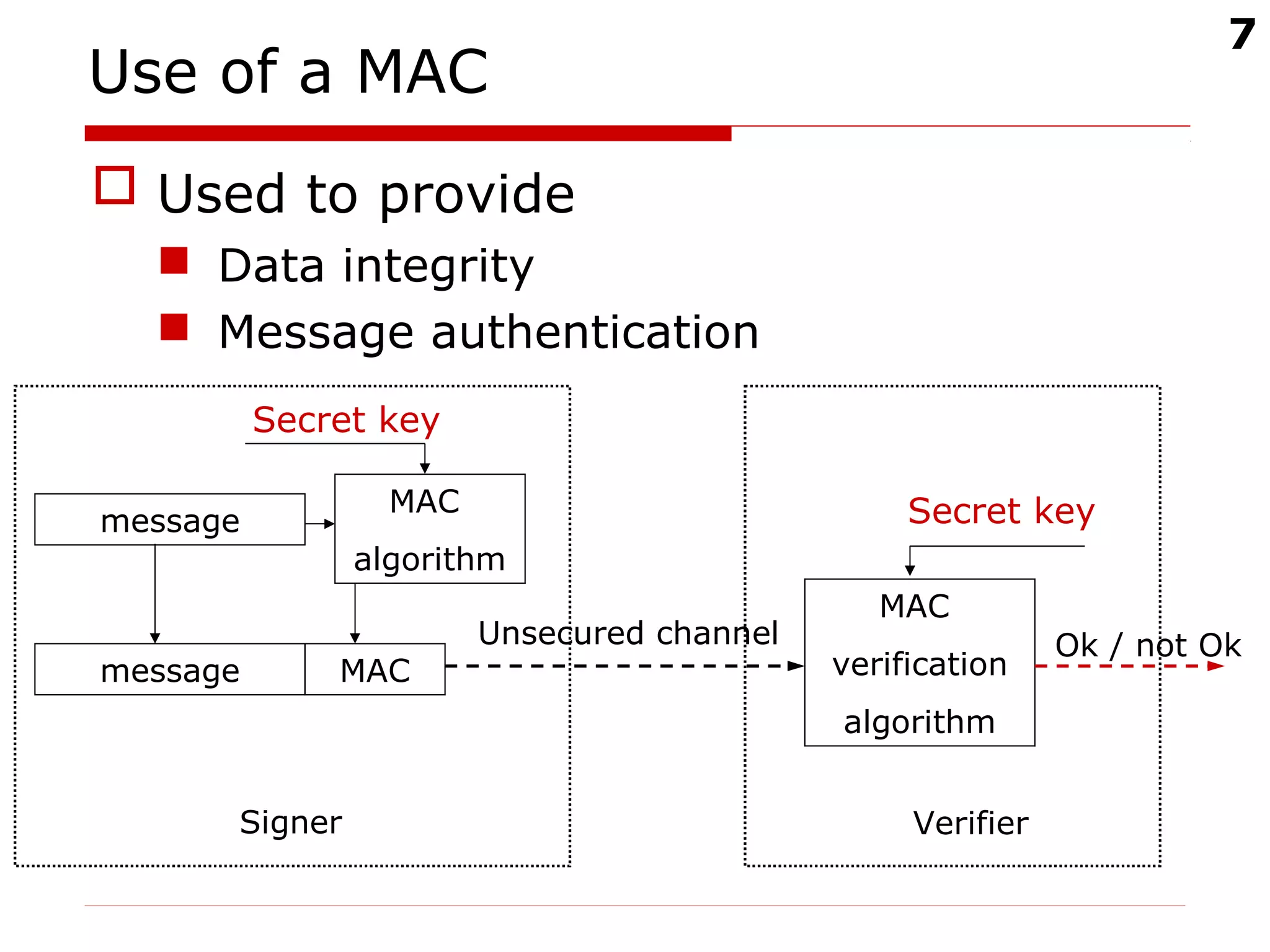
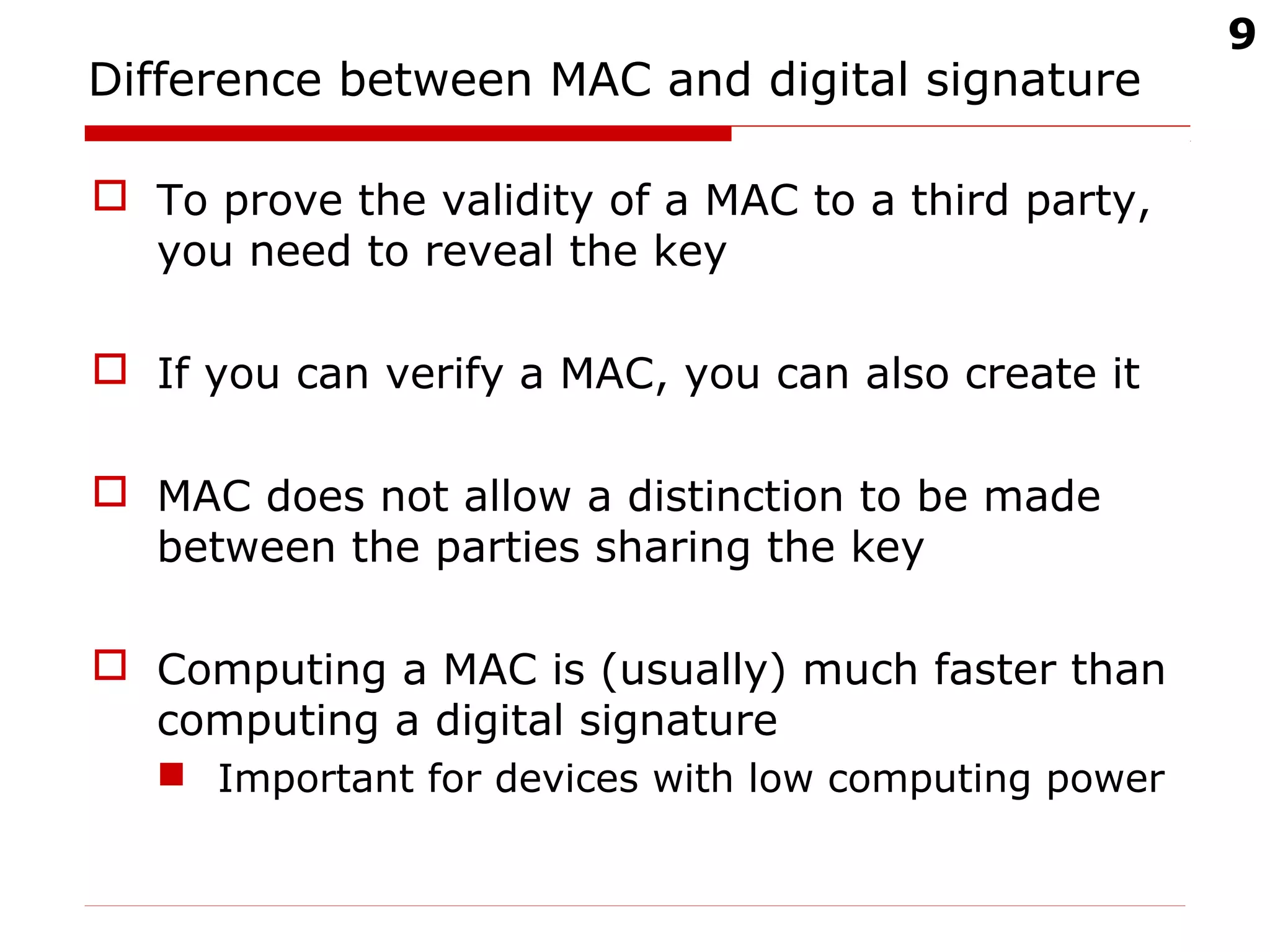
The document discusses digital signatures and message authentication codes (MACs), focusing on their cryptographic goals such as data integrity and non-repudiation. It explains the RSA digital signature algorithm and the Elliptic Curve Digital Signature Algorithm (ECDSA), including their key generation, signing, and verification processes. Additionally, it highlights the differences between MACs and digital signatures, emphasizing the performance characteristics and potential attacks on RSA signatures.









![15
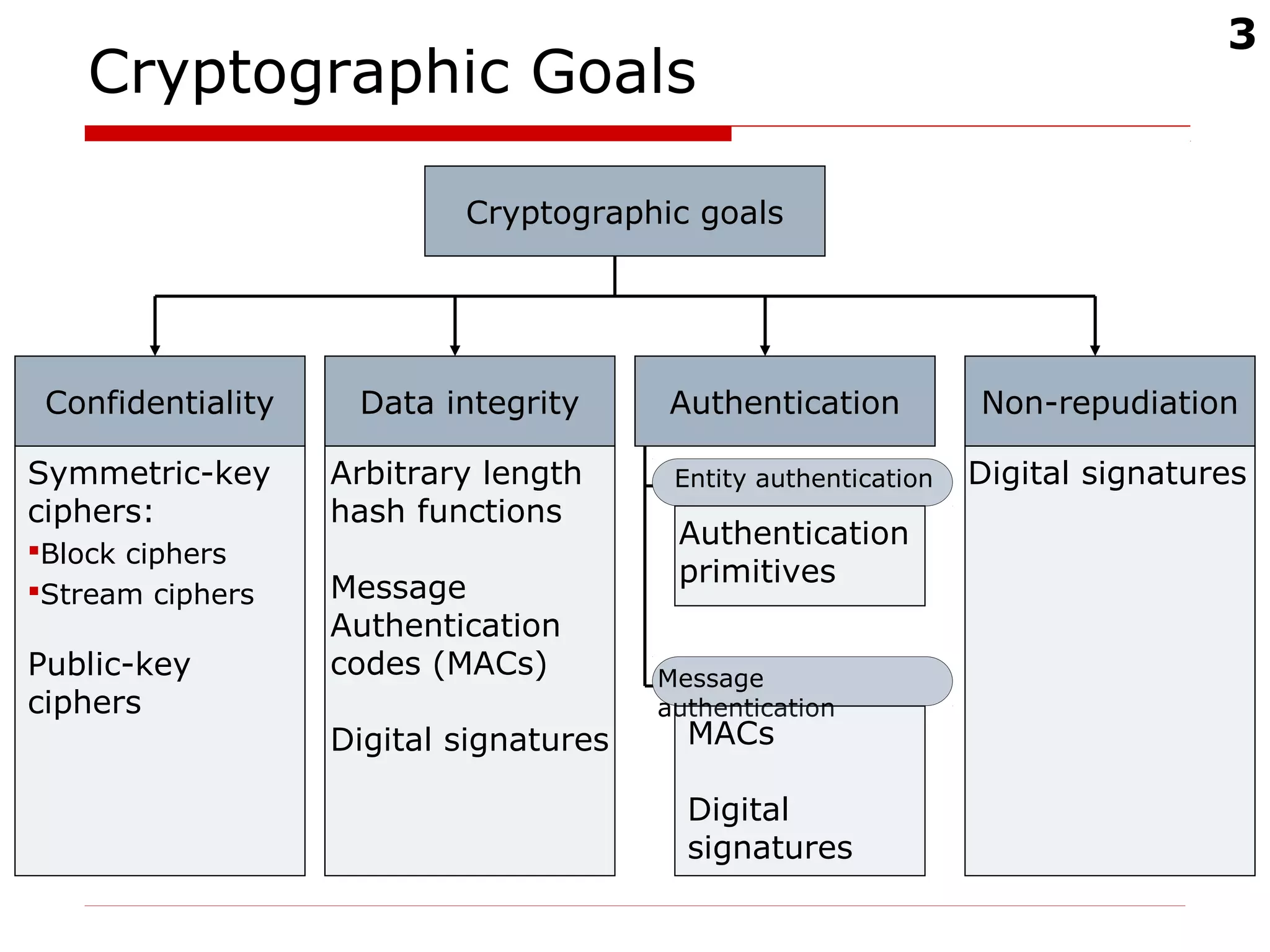
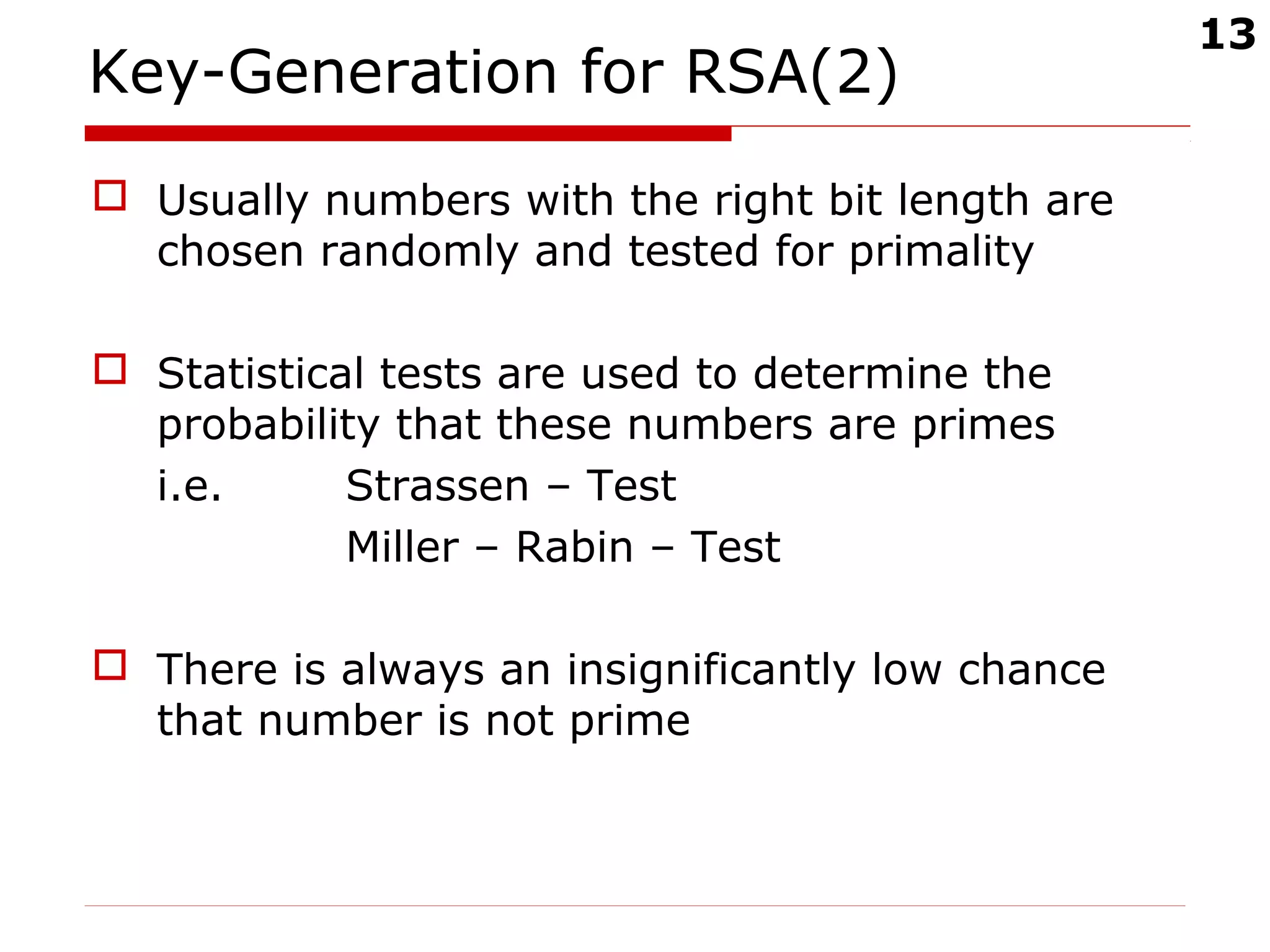
RSA signature generation and verification
To sign a message A should:
Compute:
where R(m) is a redundancy function
Compute:
A’s signature for m is s
To verify A’s signature and recover m, B should:
Obtain A’s authentic public key (n, e)
Compute:
Verify that ; if not, reject the signature
Recover
]n,[),m(Rm~ 10 −= rangetheinintegeran
nmodm~s d
=
nmodsm~ e
=
RMm~ ∈
)m~(Rm 1−
=
Mm∈](https://image.slidesharecdn.com/signyourd-digitalsignature-190515164739/75/Signyourd-digital-signature-certificate-provider-15-2048.jpg)
![17
RSA signature example
Alice
p=5 q=7 n = 35 φ(n) = 4·6=24
e = 5; d: ed = 5d=1 mod 24 => d = 5
Public key: (n=35, e=5) Private key: d=5
M = [0, n-1]
For all m Є M R(m)=m
m = 26; R(m) = 26 s = 265
mod 35 = 31
Bob:
R(m) = 315
mod 35 = 26 Є [0, n-1]
m = R-1
(m) = 26
=m~
=m~](https://image.slidesharecdn.com/signyourd-digitalsignature-190515164739/75/Signyourd-digital-signature-certificate-provider-17-2048.jpg)