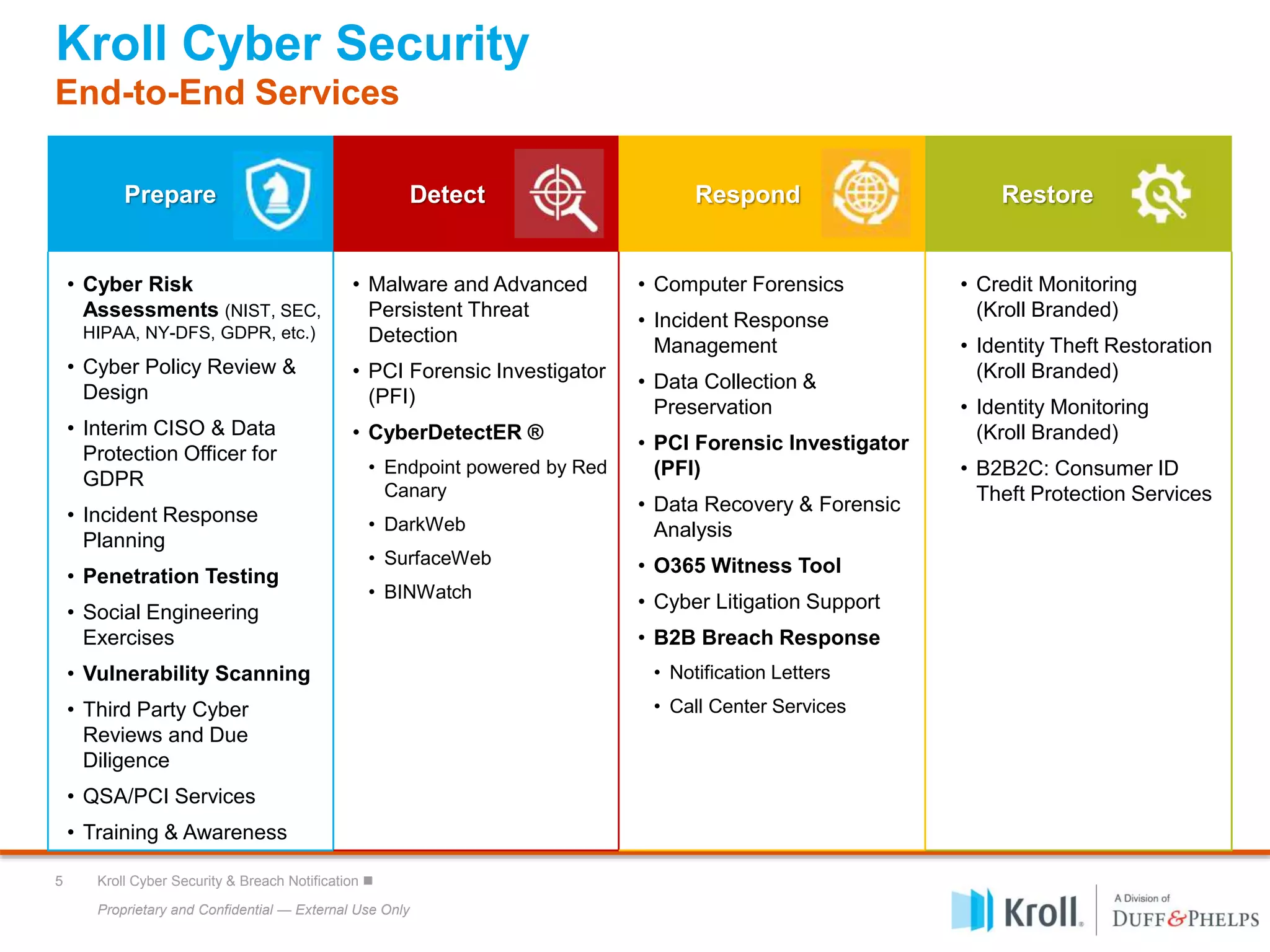
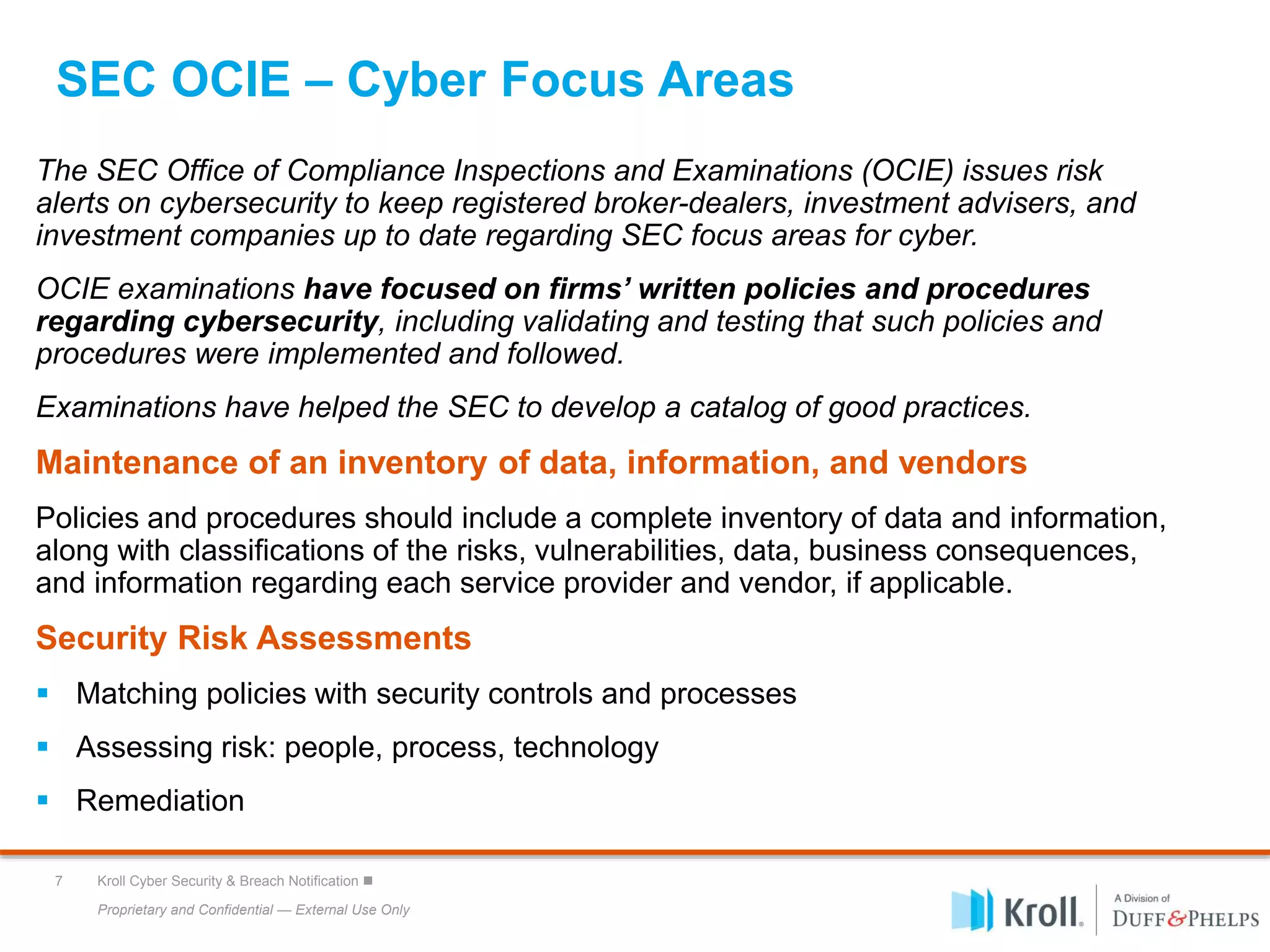
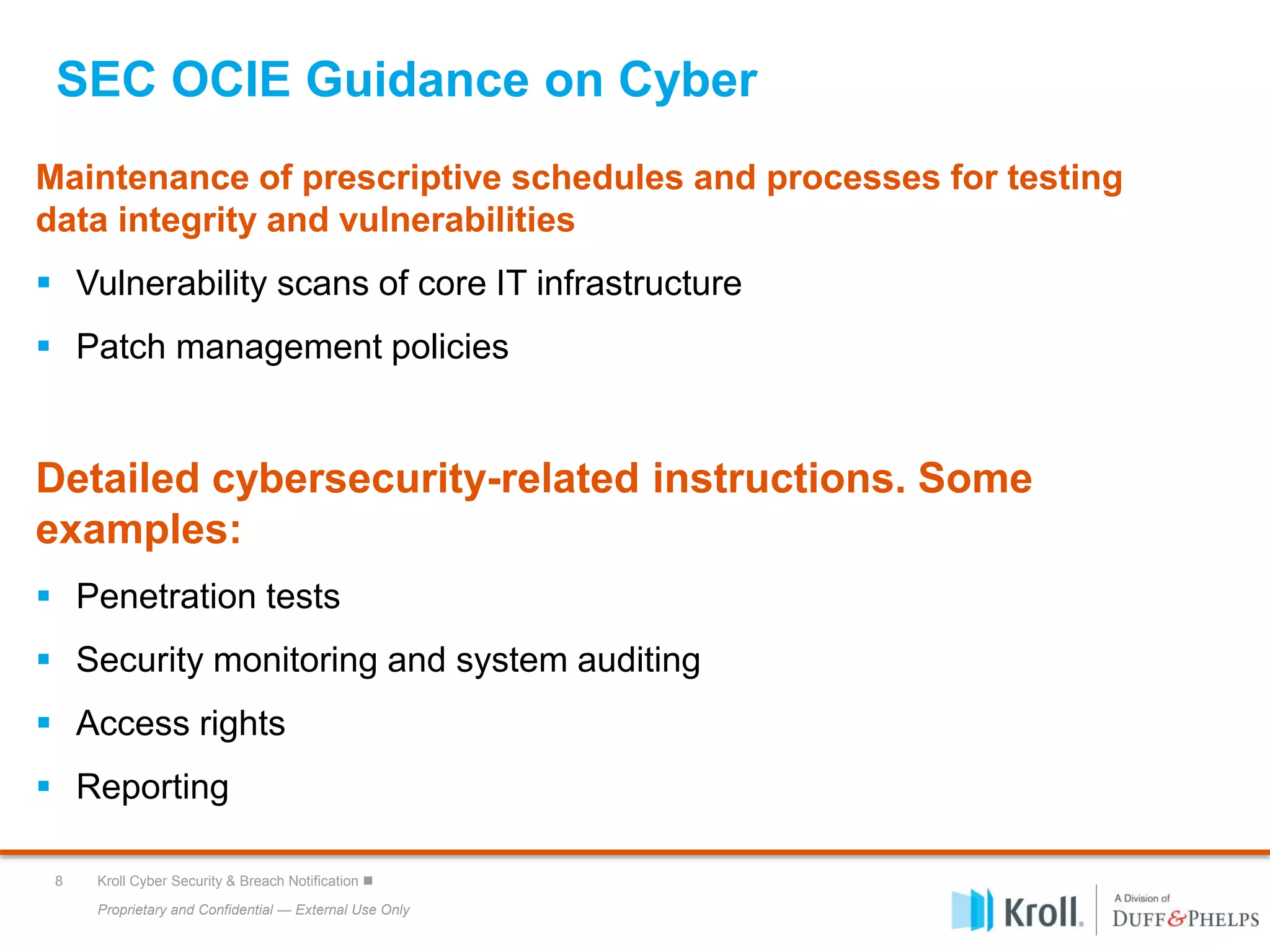
The document outlines Kroll's cyber security services, focusing on SEC cybersecurity guidance and best practices for managing cyber risk. Key areas of emphasis include risk assessments, incident response planning, and compliance with SEC regulations, alongside insights into the evolving cyber threat landscape. It highlights the importance of maintaining robust cybersecurity policies, employee training, and preparation against data breaches for organizations of all sizes.