The Internet of Things Isn't Coming, It's Here
•
0 likes•1,216 views
Sponsored by ForeScout, Webtorials surveyed IT professionals worldwide who are responsible for enterprise communications networks regarding their view about the prevalence and security of the Internet of Things (IoT). Here are some of the findings. For the full report, visit: https://www.forescout.com/iot-security-survey-results/
Report
Share
Report
Share
Download to read offline
Recommended
ForeScout IoT Enterprise Risk Report

Commissioned by ForeScout, the IoT Enterprise Risk Report
employed the skills of Samy Kamkar, one of the world’s leading ethical hackers, to investigate the security risks posed by the Internet of Things (IoT) devices in enterprise environments. Check out his findings.
For more information visit: http://resources.forescout.com/insecurity_of_things_lp_social.html.
Shining a Light on Shadow Devices

Along with the burgeoning Internet of Things comes a new reality: billions of invisible devices connected to private networks. These “shadow devices” enlarge your attack surface and, if left in the dark, expose your organization to malware propagation and theft of critical resources. Learn more: https://www.forescout.com/shining-light-shadow-devices/
Symantec and ForeScout Delivering a Unified Cyber Security Solution

Tom Blauvelt from Symantec and Sean Telles and Chris Dullea from ForeScout share how both companies together can deliver a unified cyber security solution.
SC Magazine & ForeScout Survey Results

Enterprise CISOs Demand More Integration & Automation From Their Existing IT Security Tools
Transforming Smart Building Cybersecurity Strategy for the Age of IoT

Using a smart building as their case study, Forescout Research Labs investigated how IoT devices can be leveraged as an entry point to a building’s network, where legacy OT assets, IT systems and IoT devices all intersect. Key findings from our research include:
• How the IoT is impacting the organizational threat landscape
• The additional risks that IoT devices introduce
• How to evolve your cybersecurity strategy for the age of IoT
Throughwave Day 2015 - ForeScout Automated Security Control

สไลด์จากงาน Throughwave Day 2015 สำหรับผู้ที่สนใจสามารถติดต่อได้ที่โทร 02-210-0969 หรืออีเมลล์ info@throughwave.co.th
How Secure Is Your Building Automation System? 

Explore common vulnerabilities in building automation systems (BAS), how these vulnerabilities could be exploited, and steps that organizations can take to improve the cybersecurity of their BAS.
Recommended
ForeScout IoT Enterprise Risk Report

Commissioned by ForeScout, the IoT Enterprise Risk Report
employed the skills of Samy Kamkar, one of the world’s leading ethical hackers, to investigate the security risks posed by the Internet of Things (IoT) devices in enterprise environments. Check out his findings.
For more information visit: http://resources.forescout.com/insecurity_of_things_lp_social.html.
Shining a Light on Shadow Devices

Along with the burgeoning Internet of Things comes a new reality: billions of invisible devices connected to private networks. These “shadow devices” enlarge your attack surface and, if left in the dark, expose your organization to malware propagation and theft of critical resources. Learn more: https://www.forescout.com/shining-light-shadow-devices/
Symantec and ForeScout Delivering a Unified Cyber Security Solution

Tom Blauvelt from Symantec and Sean Telles and Chris Dullea from ForeScout share how both companies together can deliver a unified cyber security solution.
SC Magazine & ForeScout Survey Results

Enterprise CISOs Demand More Integration & Automation From Their Existing IT Security Tools
Transforming Smart Building Cybersecurity Strategy for the Age of IoT

Using a smart building as their case study, Forescout Research Labs investigated how IoT devices can be leveraged as an entry point to a building’s network, where legacy OT assets, IT systems and IoT devices all intersect. Key findings from our research include:
• How the IoT is impacting the organizational threat landscape
• The additional risks that IoT devices introduce
• How to evolve your cybersecurity strategy for the age of IoT
Throughwave Day 2015 - ForeScout Automated Security Control

สไลด์จากงาน Throughwave Day 2015 สำหรับผู้ที่สนใจสามารถติดต่อได้ที่โทร 02-210-0969 หรืออีเมลล์ info@throughwave.co.th
How Secure Is Your Building Automation System? 

Explore common vulnerabilities in building automation systems (BAS), how these vulnerabilities could be exploited, and steps that organizations can take to improve the cybersecurity of their BAS.
Frost & Sullivan Report

Continuous Monitoring and Threat Mitigation with Next Generation NAC. For more information, visit: http://ow.ly/Tn7e30117gx
Top 7 Security Measures for IoT Systems 

Since, IoT systems of interrelated computing devices, mechanical or digital machines, which enables data transfer over a network without requiring human to human or human to computer interaction. So these are top 7 security measures which are most effective in order to enhance productivity for delivering better customer experience by minimizing the operational costs.
Zero Trust Cybersecurity for Microsoft Azure Cloud 

Block Armour offers a holistic Zero Trust cybersecurity solution for Microsoft Azure based hybrid IT environments
DSS ITSEC Conference 2012 - Forescout NAC #1

Presentation from Riga, Latvia. "Data Security Solutions" Ltd. ITSEC Conference.
IOT Security

A look at the main security risks and impact related to IOT devices as well as what are the key steps to improve IOT security.
Next-generation Zero Trust Cybersecurity for the Space Age

Space infrastructure has become an integral part of everyday life, with individuals, businesses and governments relying overwhelmingly on it. However, despite the space industry’s technical sophistication, its cybersecurity efforts have lagged behind that of other high-tech sectors.
Block Armour has developed a next-gen Zero Trust Cybersecurity solution explicitly designed for connected devices, integrated IoT systems and related communication networks. And, is extending the solution to deliver Zero Trust Cybersecurity for Software-defined Space based Systems.
2016 Top 10 Critical Infrastructures and SCADA/ICS Cyber Security Vulnerabili...

Check Point Software Technologies Ltd. - 2016 Top 10 Critical Infrastructures and SCADA/ICS Cyber Security Vulnerabilities & Threats
Network Access Control Market Trends, Technological Analysis and Forecast Rep...

Global Network Access Control Market was estimated over USD 551.6 million in 2014 and is anticipated to be worth USD 4.39 billion by 2022, with a CAGR at 30.2%. Increasing rate of data thefts and cyber-attacks have resulted in the development of Network Access Control that provide solution to combat these problems. NAC solutions have been accepted on a large scale at a rapid pace in order to ensure safety from malware attacks, hackers and malicious software thereby leading to a need for secure network infrastructure.
Solution: Block Armour Secure Remote Access for WFH

The Covid-19 pandemic has compelled organizations to allow large sections of the workforce to work from home. A majority of enterprises have deployed a VPN to provide remote access and ensure business continuity. However, traditional VPNs were never designed for today's highly distributed and hybrid IT environments and could expose enterprise applications and sensitive data on the corporate network to malware, ransomware, and other cyberattacks. Learn how Block Armour's #ZeroTrust security solution with integrated 2-factor authentication mitigates the risk of unauthorized access, prevents malware propagation and enables secure and compliant remote access for employees working from home due to Covid-19.
SCADA Security: The Five Stages of Cyber Grief

Every time a new information technology finds its way into production, it seems as though we end up repeating the same process – security vulnerabilities will be discovered and disclosed in that technology, and users and vendors will deny that the risks are significant. Only after major attacks occur do we really start to see efforts to address the inherent risks in a systematic way.
We’re falling into this exact same trap again with Industrial Control and SCADA systems, but in this case the problem is worse, because the inherent nature of control systems prevents us from applying many of the strategies that have been used to protect other kinds of computer networks.
Join Lancope’s Director of Security Research, Tom Cross, for a look at the five stages of grief that organizations seem to pass through as they come to terms with security risks, and how far we’ve come regarding Industrial Control Systems.
Hear about:
The state of Control Systems security vulnerabilities
Attack activity that is prompting a change in perspective
The unique, long-term challenges associated with protecting SCADA networks
How anomaly detection can play a key role in protecting SCADA systems now
Iot(security)

the ppt describes about the basics of iot,its applications, security challenges , hacks and the solutions to the security challenges
The Internet of Everything is Here

The idea of a more connected world is an exciting prospect. The proliferation of Internet-enabled cars, appliances, medical devices, thermostats, and so on has already changed the way we live and will only continue grow. Unfortunately, these devices are expanding an already large attack surface, and cybercriminals are eager to exploit them.
If we do not prepare for this influx of new, specialized devices on our networks, the Internet of Things (IoT) will leave gaping holes in our cybersecurity practices. But securing these many devices is a daunting task for even the bravest security professional.
Join Keith Wilson of Cisco Security for a webinar to discuss the security challenges related to IoT. Topics covered include:
-Why IoT devices can be difficult to secure
-Industries already affected by this trend such as health care, manufacturing, financial services and retail
-The various approaches to securing these devices
-How you can best keep IoT devices from becoming a security liability
Security Testing for IoT Systems

IoT Systems provide powerful, flexible features for IT systems — tracking, monitoring, and other data sharing. Today’s IoT devices utilize microservices and APIs that make them easy to put into production. But securing them isn’t as easy.
This webinar will look at security risks of IoT devices, interfaces, and implementations. We’ll provide practical steps and checklists any DevOps team can use to make their IoT components as secure as possible. We’ll also cover some testing best practices that can be done pre- and post-production to verify security and resilience on an ongoing basis.
CASE STUDY: How Block Armour enabled secure remote access to on- premise as ...

Due to the #covid19 pandemic, organizations were faced with an unprecedented, novel challenge of ensuring business continuity without endangering employee health and safety. Presenting our latest case study about how we enabled secure remote access to on-premise as well as SaaS applications for the employees of a Fortune 500 Oil and Gas firm subsidiary with minimal changes in their existing IT environment.
Internet of Things Security Patterns

Presented at Internet of Things Stream Conference 2015 in San Francisco by Mark Benson on April 2nd, 2015.
ABSTRACT: The growth of IoT is occurring at an incredible rate, justly raising alarms about security and privacy issues as we become increasingly reliant on these intelligent, interconnected devices in our lives and businesses. How are we to protect billions of devices from attacks and intrusions that could compromise our personal privacy, public safety, or business viability? Building an IoT solution involves securing sensors, devices, networks, cloud platforms, web applications, and mobile applications for diverse industries. This presentation examines the landscape of emerging security challenges posed by connected devices and offers a catalog of security deployment patterns that have been successfully used by some of the world’s most well known OEMs to deploy connected product fleets.
IoT Security – Executing an Effective Security Testing Process 

Deral Heiland CISSP, serves as a the Research Lead (IoT) for Rapid7. Deral has over 20 years of experience in the Information Technology field, and has held multiple positions including: Senior Network Analyst, Network Administrator, Database Manager, Financial Systems Manager and Senior Information Security Analyst. Over the last 10+ years Deral’s career has focused on security research, security assessments, penetration testing, and consulting for corporations and government agencies. Deral also has conducted security research on a numerous technical subjects, releasing white papers, security advisories, and has presented the information at numerous national and international security conferences including Blackhat, Defcon, Shmoocon, DerbyCon, RSAC, Hack In Paris. Deral has been interviewed by and quoted by several media outlets and publications including ABC World News Tonight, BBC, Consumer Reports, MIT Technical Review, SC Magazine, Threat Post and The Register.
IoT Security Challenges

As the need for digital transformation continues, IoT development and adoption for both enterprises and consumers are also on the rise. One of the main challenges in allowing multiple device connectivity is cybersecurity. Here are the challenges enterprises are facing when ensuring security for their IoT connections.
IoT Security Briefing FBI 07 23-2017 final

Briefing given to the FBI in July 2017 regarding Cybersecurity threats.
SC Magazine & ForeScout Survey Results

Enterprise CISOs Demand More Integration & Automation From Their Existing IT Security Tools
ForeScout: Our Approach

Take a look at what some of our customers and employees have to say about ForeScout Technologies!
More Related Content
What's hot
Frost & Sullivan Report

Continuous Monitoring and Threat Mitigation with Next Generation NAC. For more information, visit: http://ow.ly/Tn7e30117gx
Top 7 Security Measures for IoT Systems 

Since, IoT systems of interrelated computing devices, mechanical or digital machines, which enables data transfer over a network without requiring human to human or human to computer interaction. So these are top 7 security measures which are most effective in order to enhance productivity for delivering better customer experience by minimizing the operational costs.
Zero Trust Cybersecurity for Microsoft Azure Cloud 

Block Armour offers a holistic Zero Trust cybersecurity solution for Microsoft Azure based hybrid IT environments
DSS ITSEC Conference 2012 - Forescout NAC #1

Presentation from Riga, Latvia. "Data Security Solutions" Ltd. ITSEC Conference.
IOT Security

A look at the main security risks and impact related to IOT devices as well as what are the key steps to improve IOT security.
Next-generation Zero Trust Cybersecurity for the Space Age

Space infrastructure has become an integral part of everyday life, with individuals, businesses and governments relying overwhelmingly on it. However, despite the space industry’s technical sophistication, its cybersecurity efforts have lagged behind that of other high-tech sectors.
Block Armour has developed a next-gen Zero Trust Cybersecurity solution explicitly designed for connected devices, integrated IoT systems and related communication networks. And, is extending the solution to deliver Zero Trust Cybersecurity for Software-defined Space based Systems.
2016 Top 10 Critical Infrastructures and SCADA/ICS Cyber Security Vulnerabili...

Check Point Software Technologies Ltd. - 2016 Top 10 Critical Infrastructures and SCADA/ICS Cyber Security Vulnerabilities & Threats
Network Access Control Market Trends, Technological Analysis and Forecast Rep...

Global Network Access Control Market was estimated over USD 551.6 million in 2014 and is anticipated to be worth USD 4.39 billion by 2022, with a CAGR at 30.2%. Increasing rate of data thefts and cyber-attacks have resulted in the development of Network Access Control that provide solution to combat these problems. NAC solutions have been accepted on a large scale at a rapid pace in order to ensure safety from malware attacks, hackers and malicious software thereby leading to a need for secure network infrastructure.
Solution: Block Armour Secure Remote Access for WFH

The Covid-19 pandemic has compelled organizations to allow large sections of the workforce to work from home. A majority of enterprises have deployed a VPN to provide remote access and ensure business continuity. However, traditional VPNs were never designed for today's highly distributed and hybrid IT environments and could expose enterprise applications and sensitive data on the corporate network to malware, ransomware, and other cyberattacks. Learn how Block Armour's #ZeroTrust security solution with integrated 2-factor authentication mitigates the risk of unauthorized access, prevents malware propagation and enables secure and compliant remote access for employees working from home due to Covid-19.
SCADA Security: The Five Stages of Cyber Grief

Every time a new information technology finds its way into production, it seems as though we end up repeating the same process – security vulnerabilities will be discovered and disclosed in that technology, and users and vendors will deny that the risks are significant. Only after major attacks occur do we really start to see efforts to address the inherent risks in a systematic way.
We’re falling into this exact same trap again with Industrial Control and SCADA systems, but in this case the problem is worse, because the inherent nature of control systems prevents us from applying many of the strategies that have been used to protect other kinds of computer networks.
Join Lancope’s Director of Security Research, Tom Cross, for a look at the five stages of grief that organizations seem to pass through as they come to terms with security risks, and how far we’ve come regarding Industrial Control Systems.
Hear about:
The state of Control Systems security vulnerabilities
Attack activity that is prompting a change in perspective
The unique, long-term challenges associated with protecting SCADA networks
How anomaly detection can play a key role in protecting SCADA systems now
Iot(security)

the ppt describes about the basics of iot,its applications, security challenges , hacks and the solutions to the security challenges
The Internet of Everything is Here

The idea of a more connected world is an exciting prospect. The proliferation of Internet-enabled cars, appliances, medical devices, thermostats, and so on has already changed the way we live and will only continue grow. Unfortunately, these devices are expanding an already large attack surface, and cybercriminals are eager to exploit them.
If we do not prepare for this influx of new, specialized devices on our networks, the Internet of Things (IoT) will leave gaping holes in our cybersecurity practices. But securing these many devices is a daunting task for even the bravest security professional.
Join Keith Wilson of Cisco Security for a webinar to discuss the security challenges related to IoT. Topics covered include:
-Why IoT devices can be difficult to secure
-Industries already affected by this trend such as health care, manufacturing, financial services and retail
-The various approaches to securing these devices
-How you can best keep IoT devices from becoming a security liability
Security Testing for IoT Systems

IoT Systems provide powerful, flexible features for IT systems — tracking, monitoring, and other data sharing. Today’s IoT devices utilize microservices and APIs that make them easy to put into production. But securing them isn’t as easy.
This webinar will look at security risks of IoT devices, interfaces, and implementations. We’ll provide practical steps and checklists any DevOps team can use to make their IoT components as secure as possible. We’ll also cover some testing best practices that can be done pre- and post-production to verify security and resilience on an ongoing basis.
CASE STUDY: How Block Armour enabled secure remote access to on- premise as ...

Due to the #covid19 pandemic, organizations were faced with an unprecedented, novel challenge of ensuring business continuity without endangering employee health and safety. Presenting our latest case study about how we enabled secure remote access to on-premise as well as SaaS applications for the employees of a Fortune 500 Oil and Gas firm subsidiary with minimal changes in their existing IT environment.
Internet of Things Security Patterns

Presented at Internet of Things Stream Conference 2015 in San Francisco by Mark Benson on April 2nd, 2015.
ABSTRACT: The growth of IoT is occurring at an incredible rate, justly raising alarms about security and privacy issues as we become increasingly reliant on these intelligent, interconnected devices in our lives and businesses. How are we to protect billions of devices from attacks and intrusions that could compromise our personal privacy, public safety, or business viability? Building an IoT solution involves securing sensors, devices, networks, cloud platforms, web applications, and mobile applications for diverse industries. This presentation examines the landscape of emerging security challenges posed by connected devices and offers a catalog of security deployment patterns that have been successfully used by some of the world’s most well known OEMs to deploy connected product fleets.
IoT Security – Executing an Effective Security Testing Process 

Deral Heiland CISSP, serves as a the Research Lead (IoT) for Rapid7. Deral has over 20 years of experience in the Information Technology field, and has held multiple positions including: Senior Network Analyst, Network Administrator, Database Manager, Financial Systems Manager and Senior Information Security Analyst. Over the last 10+ years Deral’s career has focused on security research, security assessments, penetration testing, and consulting for corporations and government agencies. Deral also has conducted security research on a numerous technical subjects, releasing white papers, security advisories, and has presented the information at numerous national and international security conferences including Blackhat, Defcon, Shmoocon, DerbyCon, RSAC, Hack In Paris. Deral has been interviewed by and quoted by several media outlets and publications including ABC World News Tonight, BBC, Consumer Reports, MIT Technical Review, SC Magazine, Threat Post and The Register.
IoT Security Challenges

As the need for digital transformation continues, IoT development and adoption for both enterprises and consumers are also on the rise. One of the main challenges in allowing multiple device connectivity is cybersecurity. Here are the challenges enterprises are facing when ensuring security for their IoT connections.
IoT Security Briefing FBI 07 23-2017 final

Briefing given to the FBI in July 2017 regarding Cybersecurity threats.
What's hot (20)
Zero Trust Cybersecurity for Microsoft Azure Cloud 

Zero Trust Cybersecurity for Microsoft Azure Cloud
Next-generation Zero Trust Cybersecurity for the Space Age

Next-generation Zero Trust Cybersecurity for the Space Age
2016 Top 10 Critical Infrastructures and SCADA/ICS Cyber Security Vulnerabili...

2016 Top 10 Critical Infrastructures and SCADA/ICS Cyber Security Vulnerabili...
Network Access Control Market Trends, Technological Analysis and Forecast Rep...

Network Access Control Market Trends, Technological Analysis and Forecast Rep...
Solution: Block Armour Secure Remote Access for WFH

Solution: Block Armour Secure Remote Access for WFH
CASE STUDY: How Block Armour enabled secure remote access to on- premise as ...

CASE STUDY: How Block Armour enabled secure remote access to on- premise as ...
IoT Security – Executing an Effective Security Testing Process 

IoT Security – Executing an Effective Security Testing Process
Viewers also liked
SC Magazine & ForeScout Survey Results

Enterprise CISOs Demand More Integration & Automation From Their Existing IT Security Tools
ForeScout: Our Approach

Take a look at what some of our customers and employees have to say about ForeScout Technologies!
Internet of Things

In this presentation, Vishali, talks about the impact of IoT on the world in the next five years.
Introduction To AWS IoT - SoCalCodeCamp Nov 2016

Slide deck for Socal CodeCamp 2016 in USC Campus on AWS Internet of Things
Why NAC and Why Not NAC

Network Access Control (NAC) can protect your network from insecure endpoints and enforce security policies. Yet deploying NAC can be a huge challenge. Does it make sense for your organization to take the plunge? Find out how to answer that question by understanding how open standards enable technology that helps ensure endpoint compliance with integrity policies at, and after, network connection.
Report to the NAC

12.11.29
Information Technology Infrastructure Committee (ITIC)
Title: Report to the NAC
Demystifying TrustSec, Identity, NAC and ISE

This presentation will help demystify the technology behind Cisco TrustSec System, including the Identity Service Engine.
Physical/Network Access Control

Make presence in a building or area a policy in accessing network resources by integrating physical and network access through the Trusted Computing Group's IF-MAP communications standard.
Agri-IoT: A Semantic Framework for Internet of Things-enabled Smart Farming A...

With the recent advancement of the Internet of Things (IoT), it is now possible to process a large number of sensor data streams using different large-scale IoT platforms. These IoT frameworks are used to collect, process and analyse data streams in real-time and facilitate provision of smart solutions
designed to provide decision support. Existing IoT-based solutions are mainly domain-dependent, providing stream processing and analytics focusing on specific areas (smart cities, healthcare etc.). In the context of agri-food industry, a variety of external parameters belonging to different domains (e.g. weather conditions, regulations etc.) have a major influence over the food supply chain, while flexible and adaptive IoT frameworks, essential to truly realize the concept of smart farming, are currently inexistent. In this presentation, we propose Agri-IoT, a semantic framework for IoT-based smart farming applications, which supports reasoning over
various heterogeneous sensor data streams in real-time. Agri-
IoT can integrate multiple cross-domain data streams, providing
a complete semantic processing pipeline, offering a common
framework for smart farming applications. Agri-IoT supports
large-scale data analytics and event detection, ensuring seamless interoperability among sensors, services, processes, operations, farmers and other relevant actors, including online information sources and linked open datasets and streams available on the Web.
Internet of things (IoT)

Internet of things is a network of objects which can share information with each other and take appropriate action.
Machine Learning for Dummies

Introduction to Machine Learning
, The ML Philosophy,
Advantages
, Applications and ML Algorithms
Internet of Things (IoT) - We Are at the Tip of An Iceberg

You are likely benefitting from The Internet of Things (IoT) today, whether or not you’re familiar with the term. If your phone automatically connects to your car radio, or if you have a smartwatch counting your steps, congratulations! You have adopted one small piece of a very large IoT pie, even if you haven't adopted the name yet.
IoT may sound like a business buzzword, but in reality, it’s a real technological revolution that will impact everything we do. It's the next IT Tsunami of new possibility that is destined to change the face of technology, as we know it. IoT is the interconnectivity between things using wireless communication technology (each with their own unique identifiers) to connect objects, locations, animals, or people to the Internet, thus allowing for the direct transmission of and seamless sharing of data.
IoT represents a massive wave of technical innovation. Highly valuable companies will be built and new ecosystems will emerge from bridging the offline world with the online into one gigantic new network. Our limited understanding of the possibilities hinders our ability to see future applications for any new technology. Mainstream adoption of desktop computers and the Internet didn’t take hold until they became affordable and usable. When that occurred, fantastic and creative new innovation ensued. We are on the cusp of that tipping point with the Internet of Things.
IoT matters because it will create new industries, new companies, new jobs, and new economic growth. It will transform existing segments of our economy: retail, farming, industrial, logistics, cities, and the environment. It will turn your smartphone into the command center for the both digital and physical objects in your life. You will live and work smarter, not harder – and what we are seeing now is only the tip of the iceberg.
Viewers also liked (20)
Eliminate Silos to Enhance Critical Infrastructure Protection by Jasvir Gill

Eliminate Silos to Enhance Critical Infrastructure Protection by Jasvir Gill
Network Access Control as a Network Security Solution

Network Access Control as a Network Security Solution
Agri-IoT: A Semantic Framework for Internet of Things-enabled Smart Farming A...

Agri-IoT: A Semantic Framework for Internet of Things-enabled Smart Farming A...
Internet of Things (IoT) - We Are at the Tip of An Iceberg

Internet of Things (IoT) - We Are at the Tip of An Iceberg
Similar to The Internet of Things Isn't Coming, It's Here
The Evolution of Cybercrime

How underground markets for stolen data and hacking tools are driving cybercrime today, and some of the possible security responses, defenses, and strategies
Survey: Insider Threats and Cyber Security

A survey of 310 IT security professionals taken at the Infosecurity Europe trade show by Imperva. The survey found that when it comes to insider threats, over half (58 percent) of the IT security professionals were deeply concerned about careless users who unwittingly put their organization’s data at risk.
Federal Webinar: Best Practices and Tools for Reducing Insider Threats

Our presenter discussed and demonstrated best practices to help detect and combat insider threats, including information about implementing the right tools, along with continuous monitoring of systems and networks to aid in mitigation and prevention. Monitoring data can help agencies make informed decisions, safeguard against insider threats, and quickly identify and fix vulnerabilities. He also suggested ideas that we believe will help to enforce good information security habits within your organization to help improve your agency’s security posture.
During this interactive webinar, attendees learned:
How event monitoring, performance monitoring, and log management can be utilized to help detect and prevent threats, and help ensure that devices are operating and being used properly
How configuration management can be leveraged to help prevent errors and reduce vulnerabilities
How the implementation of Security Incident and Event Management (SIEM) tools can better equip agencies to quickly detect and respond to security threats
How to track devices and users on your network, and maintain historic data for forensics
Ideas about building security into your IT community with daily activities and conversations
How an approach styled after a secure development lifecycle can lead to improved security practices
Considerations for a secure internet of things for cities and communities

Short 15 minute presentation at the NIST GCTC Kick-off.
The Internet Is a Dog-Eat-Dog World, and Your App Is Clad in Milk-Bone Underwear

Presentation at the 2016 Big Sky Developers' Conference.
Overview of the dismal state of security on the Web, some suggestions for better app development processes to mitigate problems.
GISEC 2015 Your Network in the Eyes of a Hacker - DTS Solution

Mohamed Bedewi, Offense Security Division Head and Sr. Penetration Testing Consultant at DTS presented also during one of the security sessions titled - "Your Network in the Eyes of a Hacker – The 0ff3ns!v3 Version" which raised a few eyebrows to say the least. The presentation slides can be found here….
The Threat Is Real. Protect Yourself.

Presentation on current security trends, prevention and detection. This presentation was initially given at a WatchGuard partner event for Equinox IT. http://www.equinoxits.com/
The Internet is a dog-eat-dog world and your app is clad in Milk Bone underwear

A comprehensive review of privacy and security threats to software applications, and how to adopt secure coding practices to address these threats.
The State of Threat Detection 2019

As cyber criminals and nation-states continue to improve the sophistication of attacks that bypass traditional preventive defenses, organizations must evolve their security defenses to reduce dwell time. Join Fidelis Advisor, and ex CIA CTO, Bob Flores and Fidelis Senior Manager, Tom Clare as they delve into the results of The 2018 State of Threat Detection Report and discuss what the research means for organizations large and small across the globe.
Cybercrime future perspectives

Presentation by Charl van der Walt, Jaco van Graan and Roelof Temmingh at ISEC in 2000.
The presentation begins with a discussion on commercial crime statics and trends. Security fundamentals such as encryption and the four pillars of information security are discussed. The presentation ends with a series of discussions on the seven steps of the security process.
Sonatype's 2013 OSS Software Survey

Over 9 billion components will be downloaded this year from the Sonatype Central Repository, representing a fundamental shift from "writing" to "assembling" applications.
Three thousand (3000) respondents to Sonatype's 2013 OSS Software Survey reported that at least 80% of their applications are comprised of components. Learn how this major shift to component assembly is driving the need for much more sophisticated component management. http://www.sonatype.com/clm/why-clm
5 things it should be doing (but isn't!)

Insider Threat has become a very "real" issue for organizations of all sizes and across all industries. The focus of these malicious attacks (from insiders, outsiders and malware) is often human generated data such as documents. IT can reduce their risk of exposure by taking on a few minor, yet impactful tasks.
Federal Webinar: Leverage IT Operations Monitoring and Log Data to Reduce Ins...

According to the fourth annual Federal Cybersecurity Survey from SolarWinds and Market Connections, insider threats are the leading source of threats to federal agencies. Human error is one of the most common insider threats, followed by abuse of privileges, and theft. The increased sophistication of threats, volume of attacks, and end-user policy violations make agencies more vulnerable than ever. In this webinar, we discussed how implementing the right tools, as well as continuously monitoring systems and networks, can provide the data to make informed decisions and help agencies safeguard against insider threats, and quickly identify and fix vulnerabilities.
During this webinar our presenters discussed:
The 2017 SolarWinds Federal Cybersecurity Survey, and the top sources of threats
How the right tools and technologies can provide IT infrastructure data to help safeguard against malicious and non-malicious internal threats, including:
Utilizing fault, performance, and log management data to help ensure that devices are continuously monitored and operating correctly
Leveraging configuration management to help prevent errors and reduce vulnerabilities
How the implementation of Security Incident and Event Management (SIEM) tools can better equip agencies to quickly detect and respond to security threats and help to reduce vulnerability, including:
Utilizing log data to detect malicious or out-of-policy actions, fine-tune firewall configurations, and monitor Active Directory® changes
How to track devices and users on your network and maintain historic data for forensics
Assessment and Threats: Protecting Your Company from Cyber Attacks

In the second of six presentations in this series on cyber security, we explore the different types of malware and explain the first steps your company can take to avoid the threat of cyberattacks.
CyberSecurity Update Slides

Organizations are increasingly looking to their Internal Auditors to provide independent assurance about cyber risks and the organization's ability to defend against cyber attacks. With information technology becoming an inherent critical success factor for every business and the emerging cyber threat landscape, every internal auditor needs to equip themselves on IT audit essentials and cyber issues.
In part 14 of our Cyber Security Series you will learn about the current cyber risks and attack methods from Richard Cascarino, including:
Where are we now and Where are we going?
Current Cyberrisks
• Data Breach and Cloud Misconfigurations
• Insecure Application User Interface (API)
• The growing impact of AI and ML
• Malware Attack
• Single factor passwords
• Insider Threat
• Shadow IT Systems
• Crime, espionage and sabotage by rogue nation-states
• IoT
• CCPA and GDPR
• Cyber attacks on utilities and public infrastructure
• Shift in attack vectors
Webinar: Insights from CYREN's 2015-Q3 Cyber Threat Report

Presentation Material of the Live Webinar Event on November 4, 2015: Preview the Findings from CYREN's Newest Cyber Threats Report
Threat Detection Algorithms Make Big Data into Better Data 

These slides - based on the webinar featuring David Monahan, research director at leading IT analyst firm Enterprise Management Associates (EMA), and Wade Williamson, director of product marketing at Vectra Networks - explain how threat detection algorithms can replace your Big Data with better data.
Learn how algorithms can improve incident response, reduce risk and improve ROI.
Similar to The Internet of Things Isn't Coming, It's Here (20)
Federal Webinar: Best Practices and Tools for Reducing Insider Threats

Federal Webinar: Best Practices and Tools for Reducing Insider Threats
Considerations for a secure internet of things for cities and communities

Considerations for a secure internet of things for cities and communities
The Internet Is a Dog-Eat-Dog World, and Your App Is Clad in Milk-Bone Underwear

The Internet Is a Dog-Eat-Dog World, and Your App Is Clad in Milk-Bone Underwear
GISEC 2015 Your Network in the Eyes of a Hacker - DTS Solution

GISEC 2015 Your Network in the Eyes of a Hacker - DTS Solution
The Internet is a dog-eat-dog world and your app is clad in Milk Bone underwear

The Internet is a dog-eat-dog world and your app is clad in Milk Bone underwear
Federal Webinar: Leverage IT Operations Monitoring and Log Data to Reduce Ins...

Federal Webinar: Leverage IT Operations Monitoring and Log Data to Reduce Ins...
Assessment and Threats: Protecting Your Company from Cyber Attacks

Assessment and Threats: Protecting Your Company from Cyber Attacks
Webinar: Insights from CYREN's 2015-Q3 Cyber Threat Report

Webinar: Insights from CYREN's 2015-Q3 Cyber Threat Report
Threat Detection Algorithms Make Big Data into Better Data 

Threat Detection Algorithms Make Big Data into Better Data
Recently uploaded
原版仿制(uob毕业证书)英国伯明翰大学毕业证本科学历证书原版一模一样

原版纸张【微信:741003700 】【(uob毕业证书)英国伯明翰大学毕业证】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
test test test test testtest test testtest test testtest test testtest test ...

salamsasalamlamsalamsalamsalamsalamsalamsalamsalam
1比1复刻(bath毕业证书)英国巴斯大学毕业证学位证原版一模一样

原版纸张【微信:741003700 】【(bath毕业证书)英国巴斯大学毕业证学位证】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
急速办(bedfordhire毕业证书)英国贝德福特大学毕业证成绩单原版一模一样

原版纸张【微信:741003700 】【(bedfordhire毕业证书)英国贝德福特大学毕业证成绩单】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
1.Wireless Communication System_Wireless communication is a broad term that i...

Wireless communication involves the transmission of information over a distance without the help of wires, cables or any other forms of electrical conductors.
Wireless communication is a broad term that incorporates all procedures and forms of connecting and communicating between two or more devices using a wireless signal through wireless communication technologies and devices.
Features of Wireless Communication
The evolution of wireless technology has brought many advancements with its effective features.
The transmitted distance can be anywhere between a few meters (for example, a television's remote control) and thousands of kilometers (for example, radio communication).
Wireless communication can be used for cellular telephony, wireless access to the internet, wireless home networking, and so on.
How to Use Contact Form 7 Like a Pro.pptx

Contact Form 7 is a popular plugins for WordPress. This is an introduction into its features and usage.
Multi-cluster Kubernetes Networking- Patterns, Projects and Guidelines

Talk presented at Kubernetes Community Day, New York, May 2024.
Technical summary of Multi-Cluster Kubernetes Networking architectures with focus on 4 key topics.
1) Key patterns for Multi-cluster architectures
2) Architectural comparison of several OSS/ CNCF projects to address these patterns
3) Evolution trends for the APIs of these projects
4) Some design recommendations & guidelines for adopting/ deploying these solutions.
ER(Entity Relationship) Diagram for online shopping - TAE

https://bit.ly/3KACoyV
The ER diagram for the project is the foundation for the building of the database of the project. The properties, datatypes, and attributes are defined by the ER diagram.
The+Prospects+of+E-Commerce+in+China.pptx

The Prospects of E-commerce in China,www.cfye-commerce.shop
History+of+E-commerce+Development+in+China-www.cfye-commerce.shop

History+of+E-commerce+Development+in+China-www.cfye-commerce.shop
This 7-second Brain Wave Ritual Attracts Money To You.!

Discover the power of a simple 7-second brain wave ritual that can attract wealth and abundance into your life. By tapping into specific brain frequencies, this technique helps you manifest financial success effortlessly. Ready to transform your financial future? Try this powerful ritual and start attracting money today!
Recently uploaded (16)
test test test test testtest test testtest test testtest test testtest test ...

test test test test testtest test testtest test testtest test testtest test ...
Living-in-IT-era-Module-7-Imaging-and-Design-for-Social-Impact.pptx

Living-in-IT-era-Module-7-Imaging-and-Design-for-Social-Impact.pptx
guildmasters guide to ravnica Dungeons & Dragons 5...

guildmasters guide to ravnica Dungeons & Dragons 5...
1.Wireless Communication System_Wireless communication is a broad term that i...

1.Wireless Communication System_Wireless communication is a broad term that i...
Multi-cluster Kubernetes Networking- Patterns, Projects and Guidelines

Multi-cluster Kubernetes Networking- Patterns, Projects and Guidelines
ER(Entity Relationship) Diagram for online shopping - TAE

ER(Entity Relationship) Diagram for online shopping - TAE
History+of+E-commerce+Development+in+China-www.cfye-commerce.shop

History+of+E-commerce+Development+in+China-www.cfye-commerce.shop
This 7-second Brain Wave Ritual Attracts Money To You.!

This 7-second Brain Wave Ritual Attracts Money To You.!
The Internet of Things Isn't Coming, It's Here
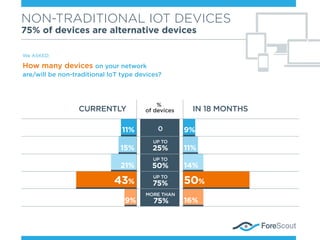
- 1. NON-TRADITIONAL IOT DEVICES 75% of devices are alternative devices We ASKED: How many devices on your network are/will be non-traditional loT type devices? IN 18 MONTHSCURRENTLY 9% 50% 14% 16% 11% UP TO 25% UP TO 50% UP TO 75% MORE THAN 75% 0 9% 43% 21% 15% 11% % of devices
- 2. CONFIDENT 15% We ASKED: How confident are you that you know all the loT devices that are connected to your network as soon as they are connected and that you can control these loT devices so cybercriminals can’t use them as doorways into your network? SOME 23% 24% NOT AT ALL ALMOST 15% 23% VERY LITTLE CONFIDENCE LEVEL 75% not confident
- 3. We ASKED: Does your company have security policies on IoT devices? We ASKED: Does your company’s security policy (if any) cover home networks 26% 30% 44% NO YESI DON’T KNOW 22% 45% 33% NO YESI DON’T KNOW (and by extension automation, thermostats, etc) when accessing the corporate network from your home? SECURITY POLICIES Company devices, Home networks & other devices
- 4. We ASKED: What are the top two IoT security challenges your organization faces? 41% says: IT and OT Working Together e.g.: OPERATIONS TECHNOLOGY Acknowledging loT Devices THEY ARE AROUND & NEED TO BE SECURED 34% Solution Availability WHICH ARE INDUSTRY APPROPRIATE 27% Other 4% Lack of Personal Resources25% Investing Budget SECURITY FOR loT DEVICES 34% Organizations’ TOP TWO challenges around loT Security TOP CHALLENGES
- 5. We ASKED: How important is it to: Discover that an loT device is on your network? Classify what type of device it is? Discover or classify without the use of an agent? SLIGHTLY MODERATELY VERY EXTREMELY IMPORTANT UNIMPORTANT CLASSIFY W/O AGENT 4% 10% 22%27% 37% CLASSIFY TYPE OF DEVICE 3% 9% 24%20% 43% DEVICE ON NETWORK 4% 6% 34%18% 37%1. 2. 3. 1. 2. 3. DISCOVER & CLASSIFY Agent, Type & Network
- 6. We ASKED: What describes your organization’s current primary approach to securing loT devices on your network? 44% We have a specialized agent that monitors our network. We have a password on our network. 17% 14% Nothing that I’m aware of. I don’t know. 13% We have another approach. 7% We rely on industry or manufacturer standard methods, such as Wi-Fi, WPA22, Bluetooth protocols, etc. 30% DESCRIBE YOUR APPROACH Securing IoT Devices Connected to the Network
- 7. 0% 100%50% 70%30% DESKTOP PCS IP PHONES PRINTERS SMART PHONES TABLETS/PADS NOTEBOOK PCS IP PBXES VIDEO CONFERENCING VOIP ADAPTERS STORAGE (CLOUD DRIVES) VIDEO SURVEILLANCE SCANNERS DOOR/SECURITY ALARMS SMART TVS VIDEO (CHROMECAST, APPLE TV, ETC) 84 81 76 75 74 73 67 65 61 47 47 46 44 38 33 KNOWN CONNECTED DEVICES Traditional Gateways RISKY We ASKED: Which devices are connected to your network (that you are aware of)?
