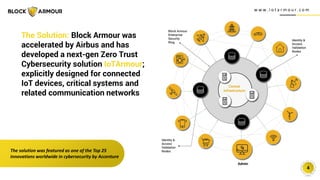
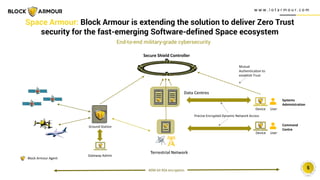
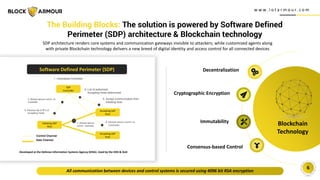
Block Armour has developed a next-gen zero trust cybersecurity solution powered by software-defined perimeter (SDP) architecture and blockchain technology to secure space infrastructure and communication networks. The shift towards software-defined systems presents an opportunity to address longstanding security vulnerabilities in the space industry, which is increasingly targeted by cyberattacks. The market for space technology is projected to reach $558 billion by 2026, and Block Armour is forging strategic alliances to enhance security in this rapidly growing sector.