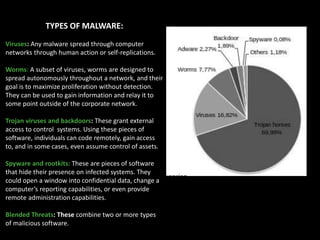
The document outlines the importance of conducting a thorough assessment of a company's cyber security, starting with an inventory of networks and devices. It emphasizes the need for monitoring and understanding different types of malware threats, including viruses, worms, and trojans. The text also highlights the necessity of evaluating vulnerabilities through penetration testing and continual monitoring to protect against cyber threats.