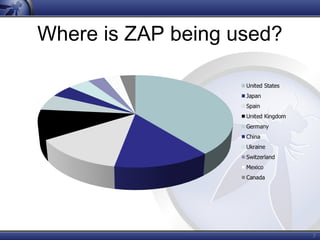
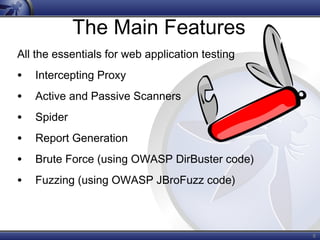
ZAP (Zed Attack Proxy) is an open source web application penetration testing tool that is easy to use, cross-platform, and has been downloaded over 6,300 times. It includes features like an intercepting proxy, active and passive scanners, a spider, and report generation that allow it to test web applications for vulnerabilities. ZAP has an active international development community, is improving rapidly with new releases, and has the potential to introduce more people to application security best practices.