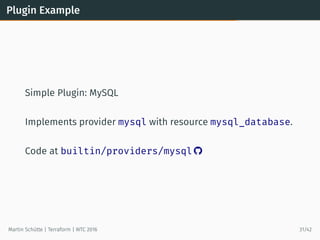
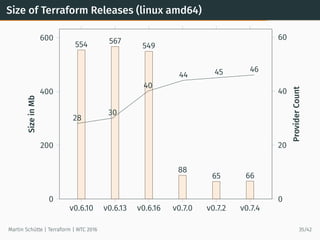
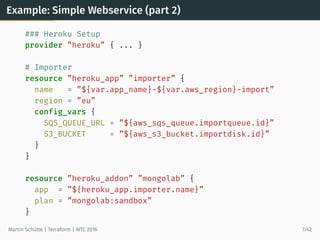
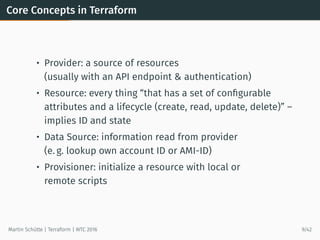
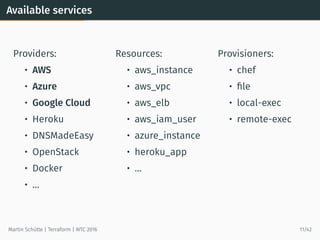
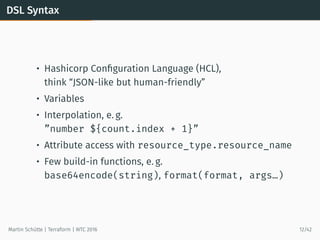
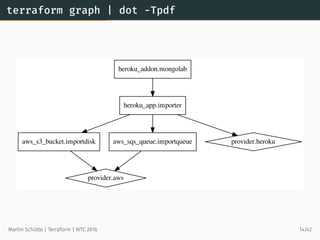
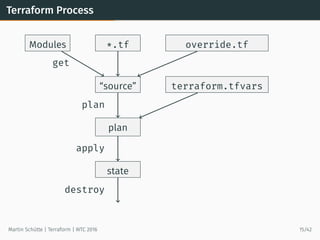
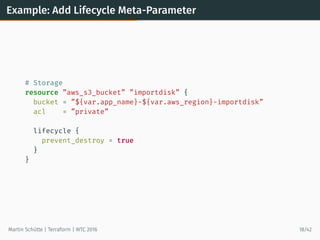
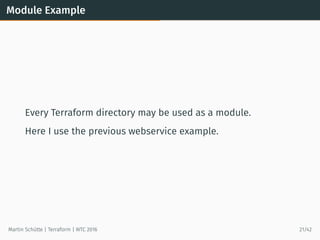
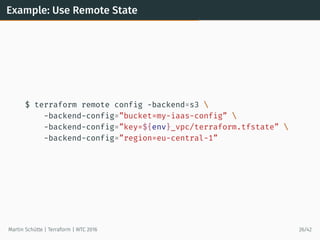
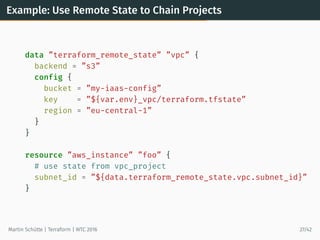
This document provides an overview of Terraform, an open-source tool for building, changing, and versioning infrastructure safely and efficiently. It discusses Terraform's core concepts including providers, resources, data sources, and modules. An example demonstrates creating AWS SQS and S3 resources and a Heroku app using Terraform configuration files. The document also covers Terraform's workflow, features like remote state and provisioning, and compares it to similar configuration management tools.






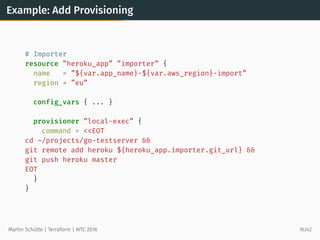



![Using a Module Example (part 2)
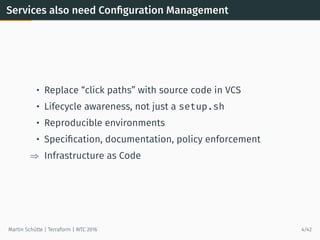
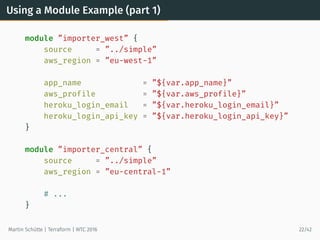
# Main App, using modules
resource ”heroku_app” ”main” {
name = ”${var.app_name}-main”
region = ”eu”
config_vars {
IMPORTER_URL_LIST = <<EOT
[ ”${module.importer_west.importer_url}”,
”${module.importer_central.importer_url}” ]
EOT
}
}
output ”main_url” {
value = ”${heroku_app.main.web_url}”
}
Martin Schütte | Terraform | WTC 2016 23/42](https://image.slidesharecdn.com/20161026-wtc-terraform-print-161026064316/85/Terraform-Cloud-Configuration-Management-WTC-IPC-16-25-320.jpg)


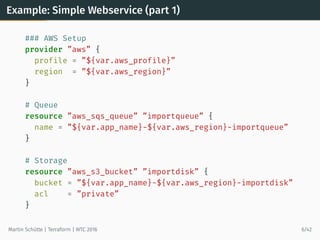
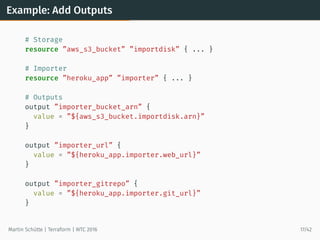
![Example: Using Data Source
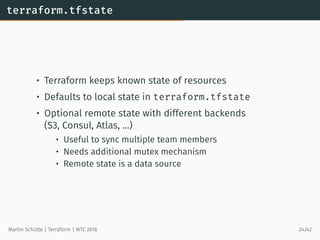
# searches for most recent tagged AMI in own account
data ”aws_ami” ”webami” {
most_recent = true
owners = [”self”]
filter {
name = ”tag:my_key”
values = [”my_value”]
}
}
# use AMI
resource ”aws_instance” ”web” {
instance_type = ”t2.micro”
ami = ”${data.aws_ami.webami.id}”
}
Martin Schütte | Terraform | WTC 2016 29/42](https://image.slidesharecdn.com/20161026-wtc-terraform-print-161026064316/85/Terraform-Cloud-Configuration-Management-WTC-IPC-16-31-320.jpg)