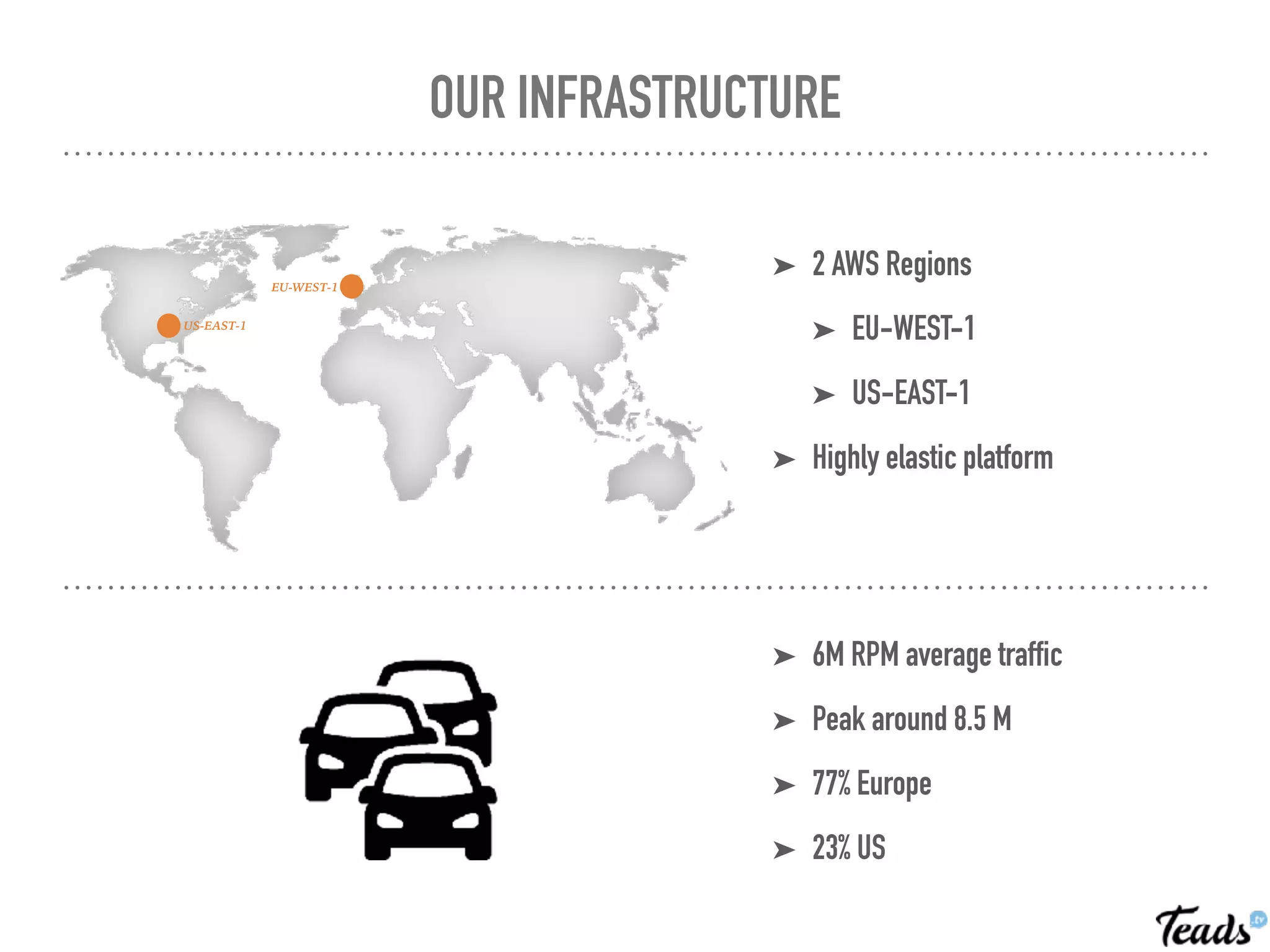
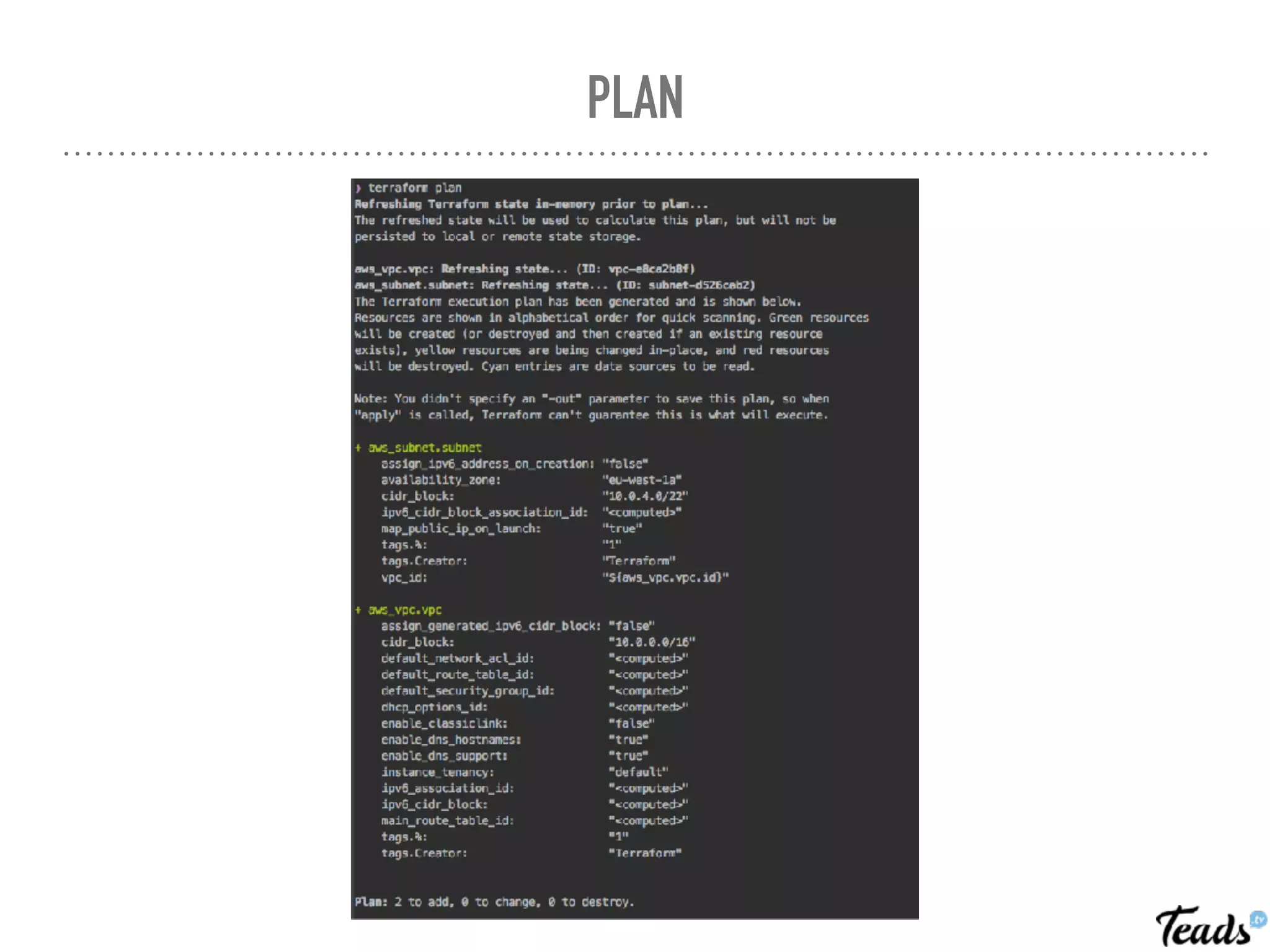
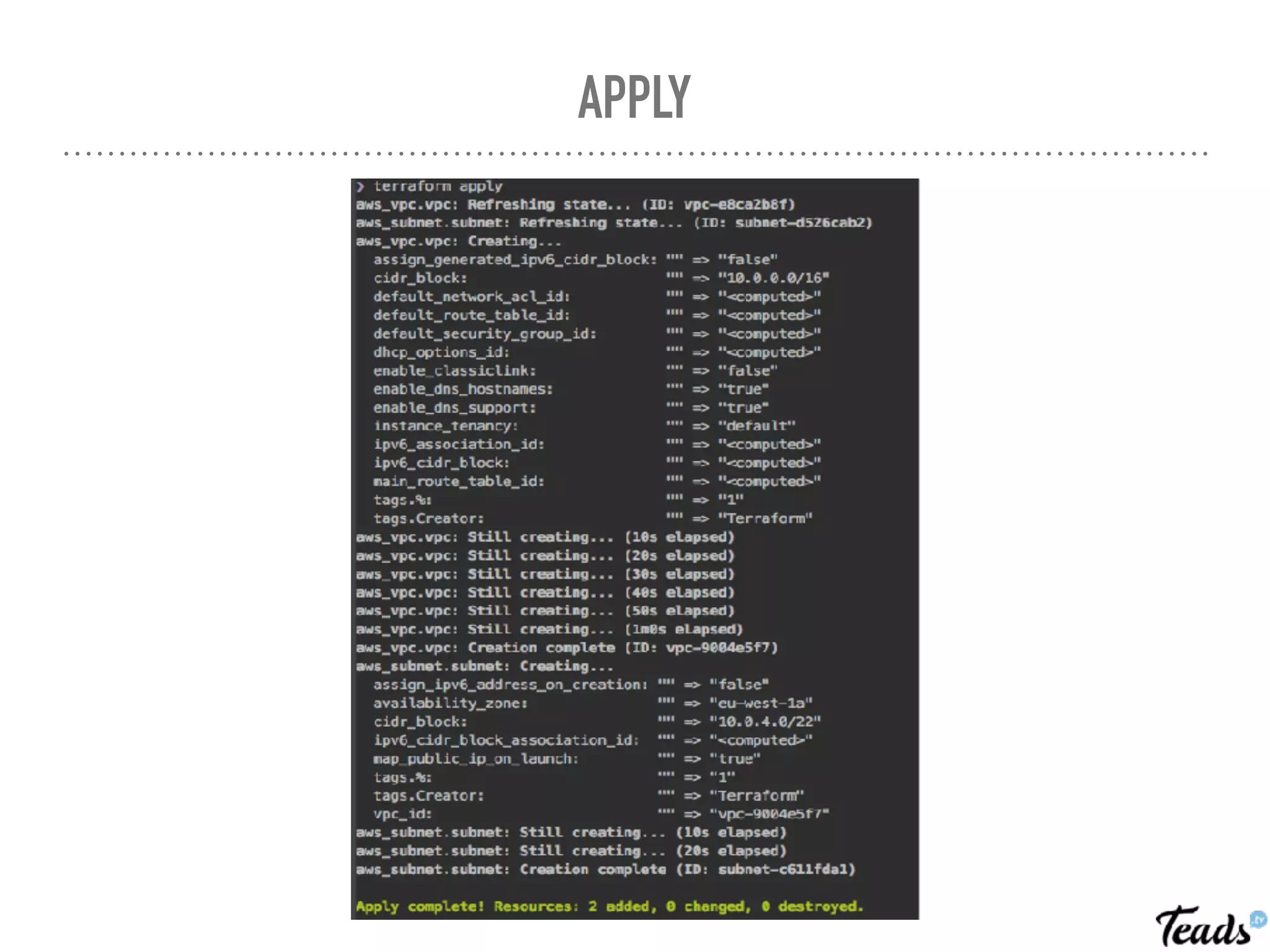
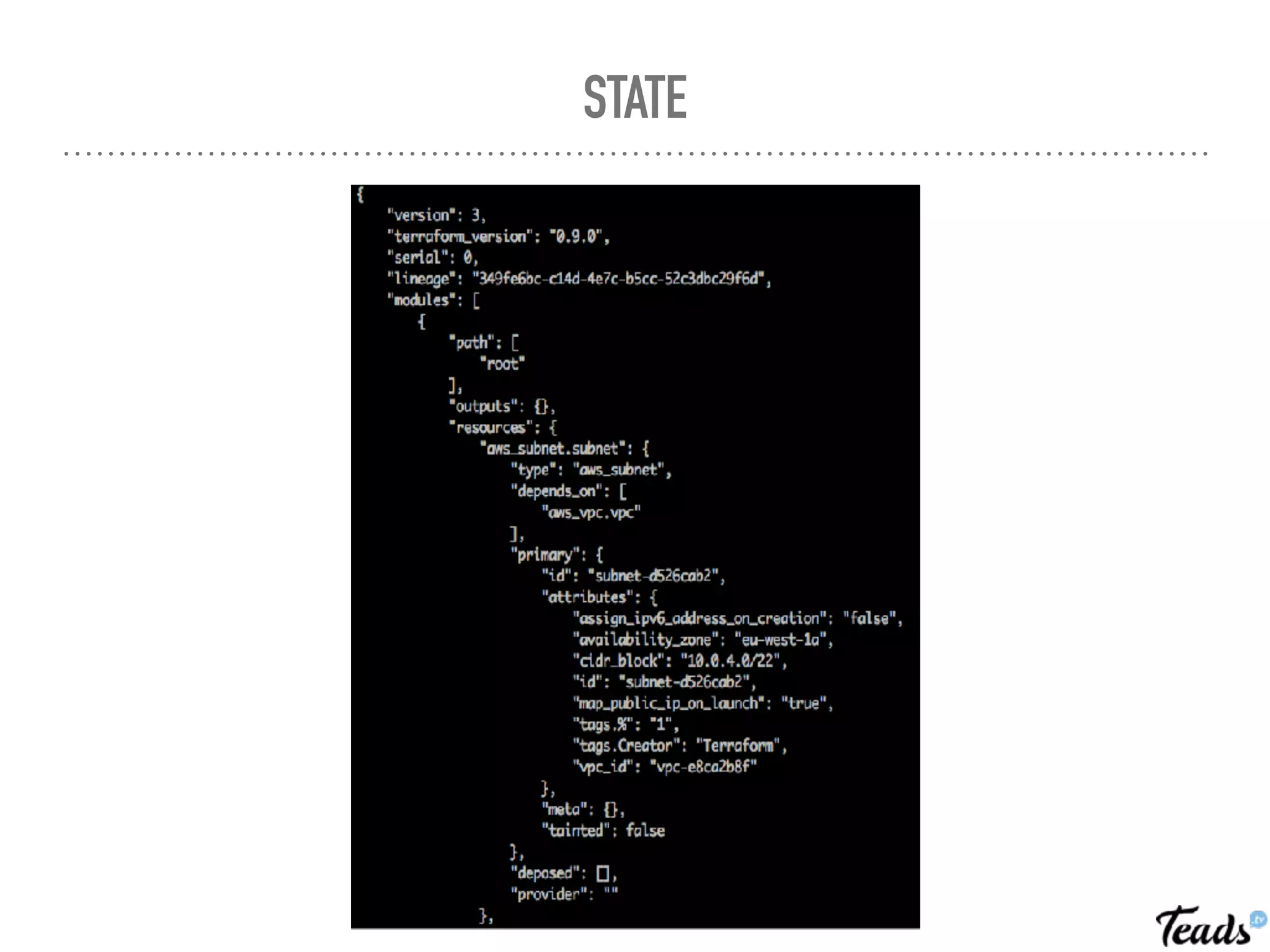
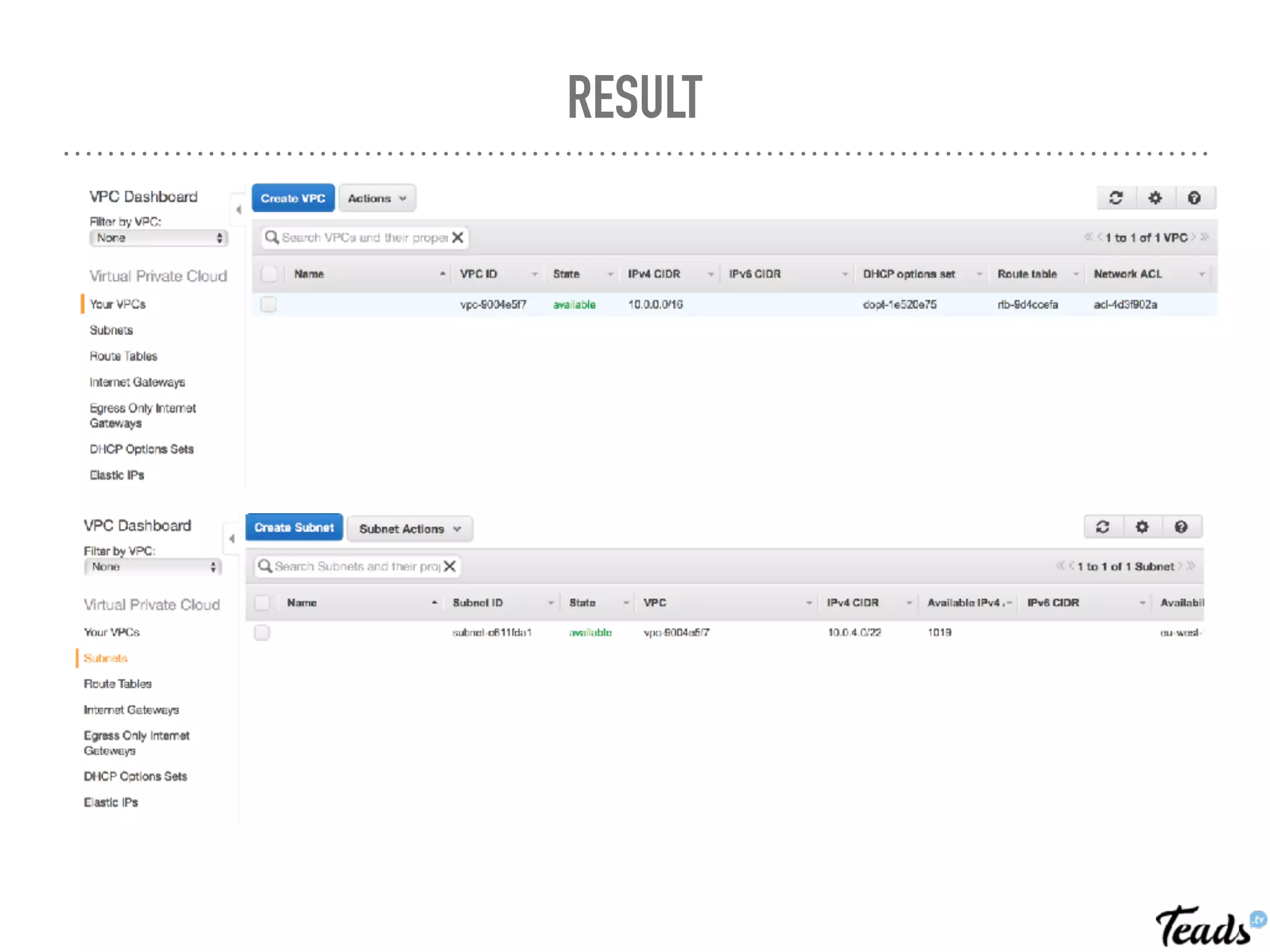
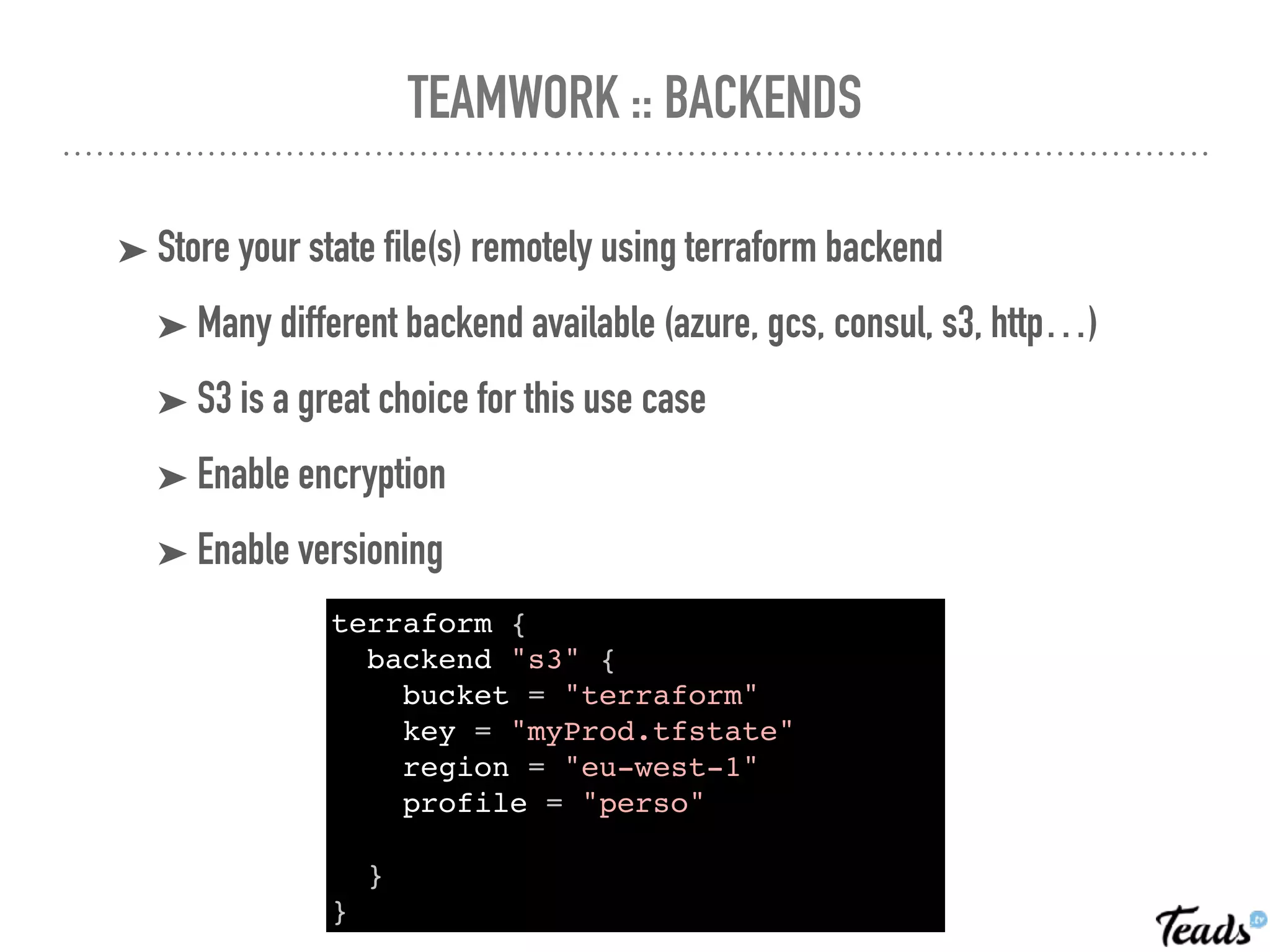
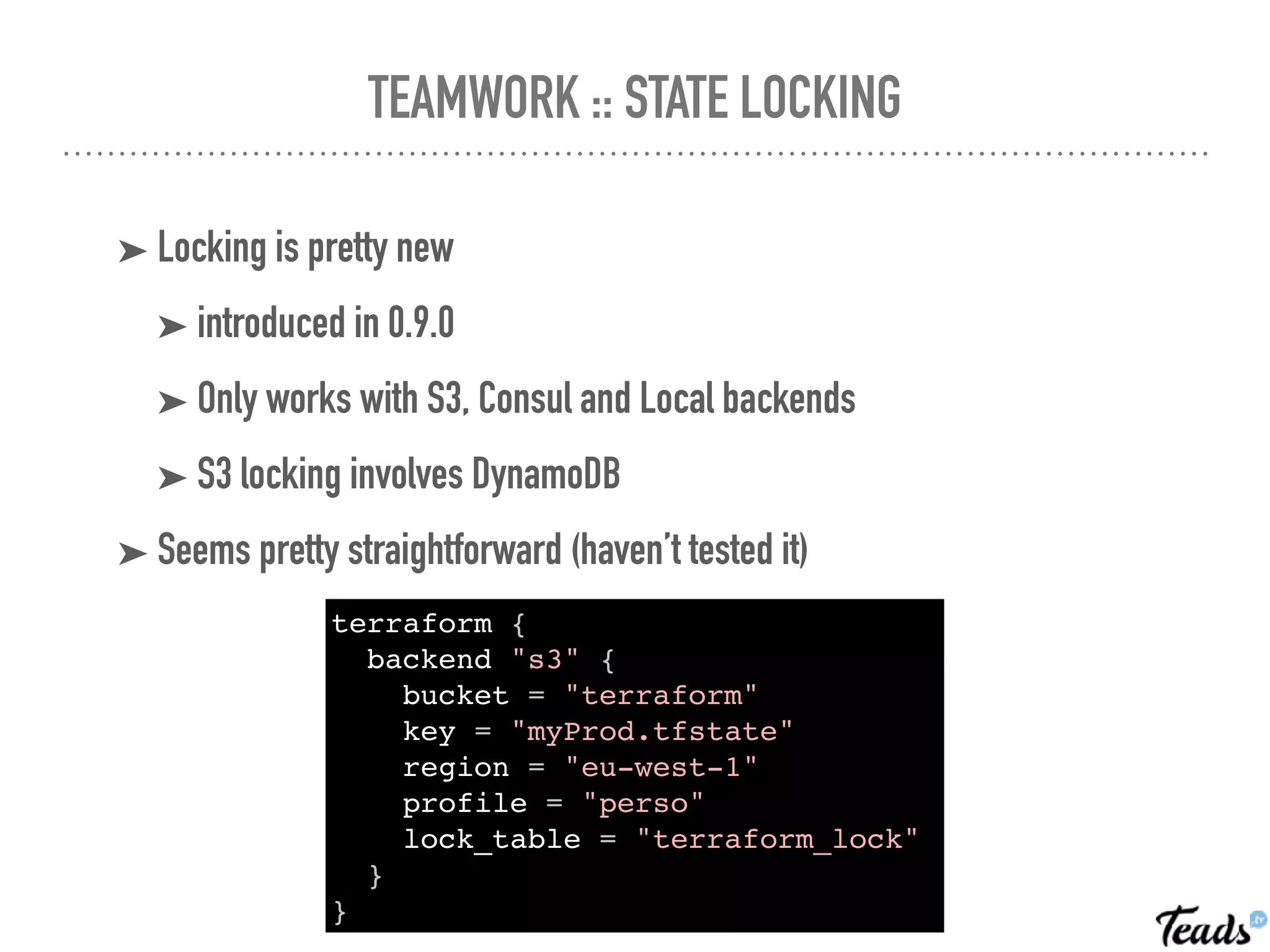
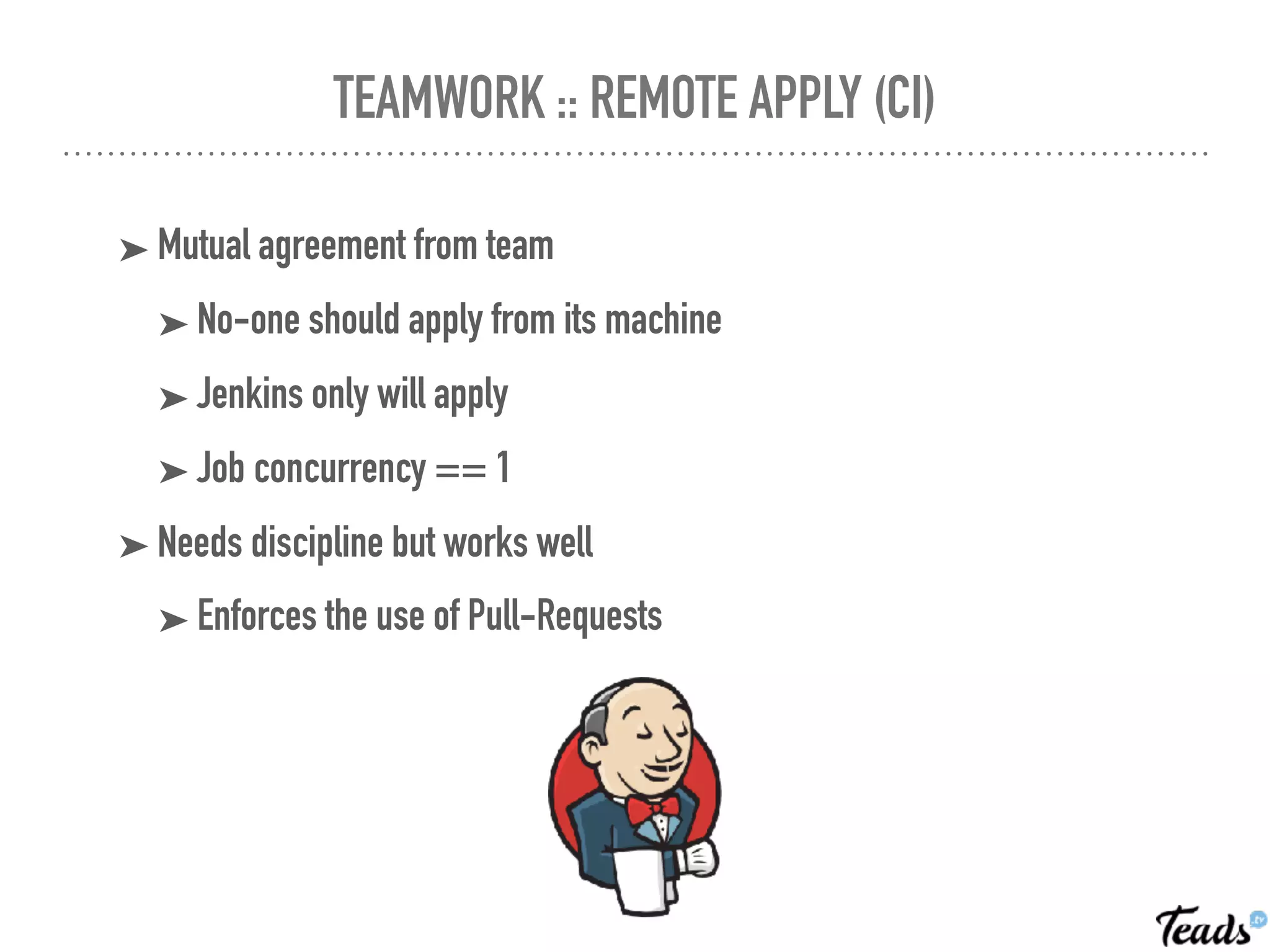
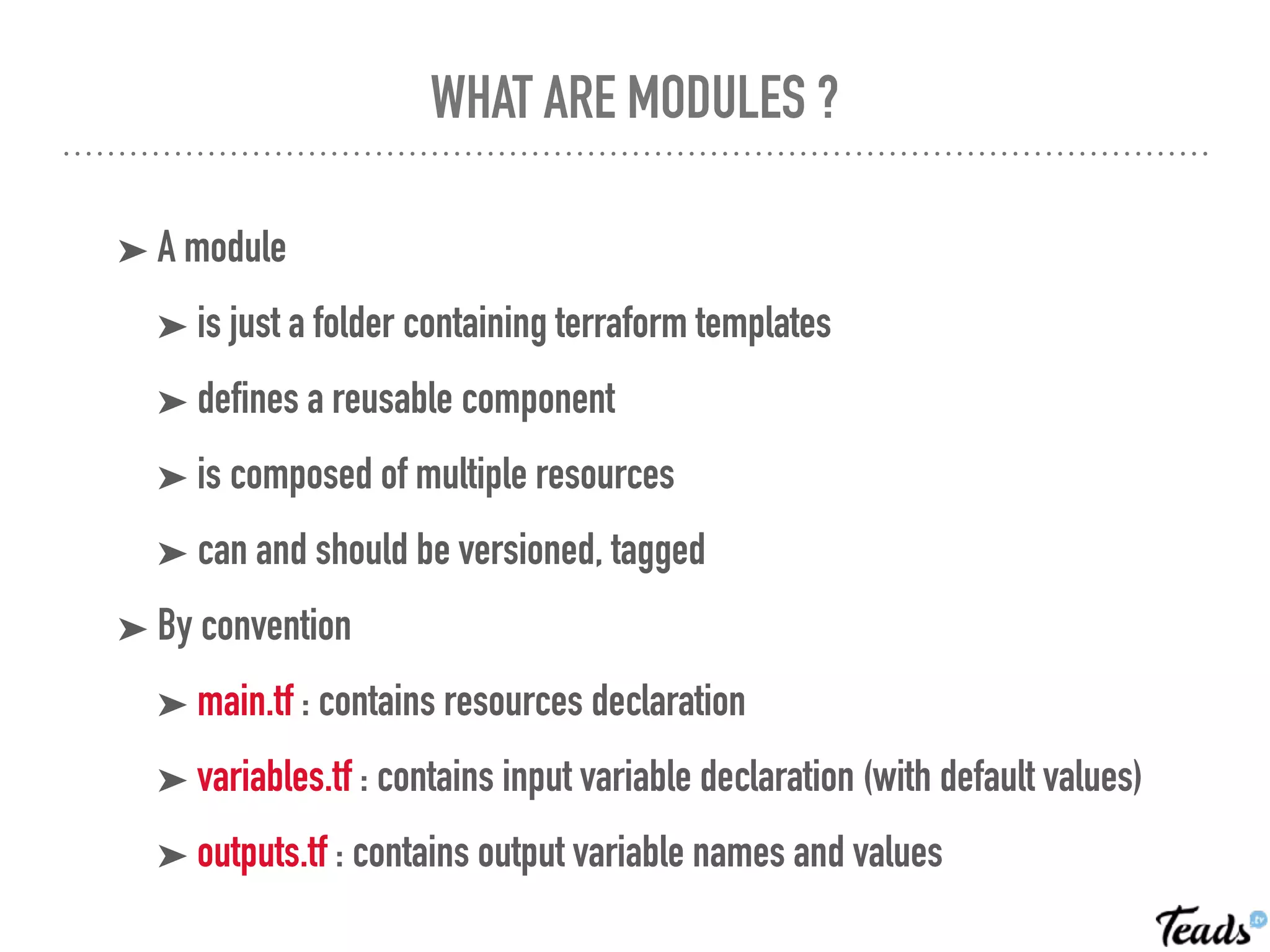
The document discusses the implementation of Infrastructure as Code (IaC) using Terraform for managing infrastructure across multiple AWS regions, emphasizing the benefits of automation, team collaboration, and version control. It covers topics like module creation for reusable components, state management using remote backends, and best practices for managing changes in a CI/CD environment. Additionally, it highlights potential challenges associated with Terraform's active development and compatibility issues.





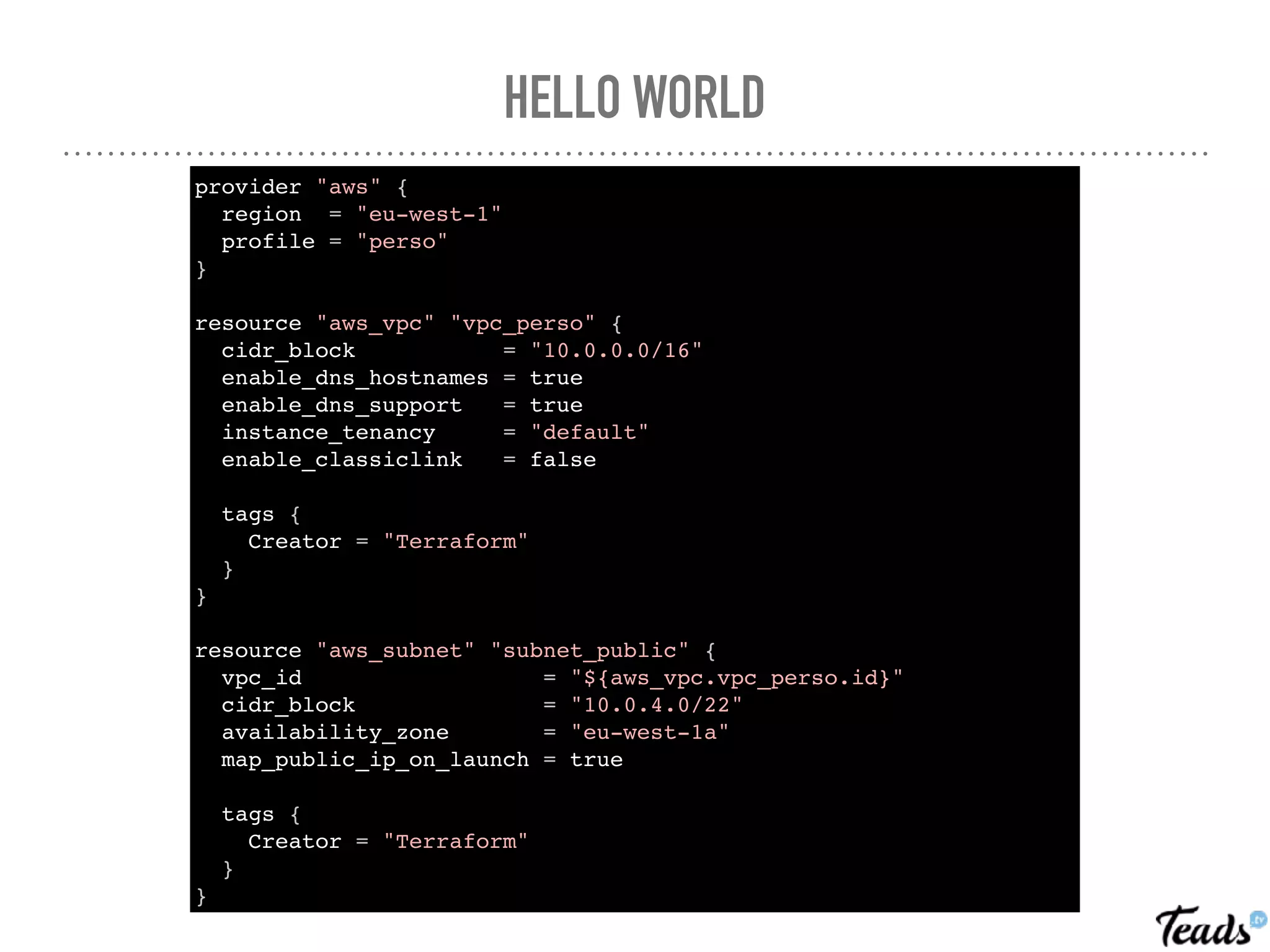


![MODULE DECLARATION :: MAIN.TF
#VPC
resource "aws_vpc" "vpc" {
cidr_block = "${var.vpc_cidr}"
enable_dns_hostnames = true
enable_dns_support = true
instance_tenancy = "default"
enable_classiclink = false
}
# DHCP options
# This is important to populate search section in /etc/resolv.conf
resource "aws_vpc_dhcp_options" "vpc_dhcp_options" {
domain_name = "${var.domain_name}.${var.env} ${var.aws_region}.compute.internal"
domain_name_servers = ["AmazonProvidedDNS"]
}
# DHCP association
# the option needs to be associated with the VPC
resource "aws_vpc_dhcp_options_association" "vpc_dhcp_options_association" {
vpc_id = "${aws_vpc.vpc.id}"
dhcp_options_id = "${aws_vpc_dhcp_options.vpc_dhcp_options.id}"
}
# Internet Gateway, required so that instances get access/be accessed from the Internet
resource "aws_internet_gateway" "internet_gateway" {
vpc_id = "${aws_vpc.vpc.id}"
}
# S3 VPC endpoint, required so that instances with private IPs can get access to S3
resource "aws_vpc_endpoint" "s3_endpoint" {
vpc_id = "${aws_vpc.vpc.id}"
service_name = "com.amazonaws.${var.aws_region}.s3"
}](https://image.slidesharecdn.com/2017-04-12awsmeetup-terraformrex-170412220359/75/Terraform-in-action-21-2048.jpg)