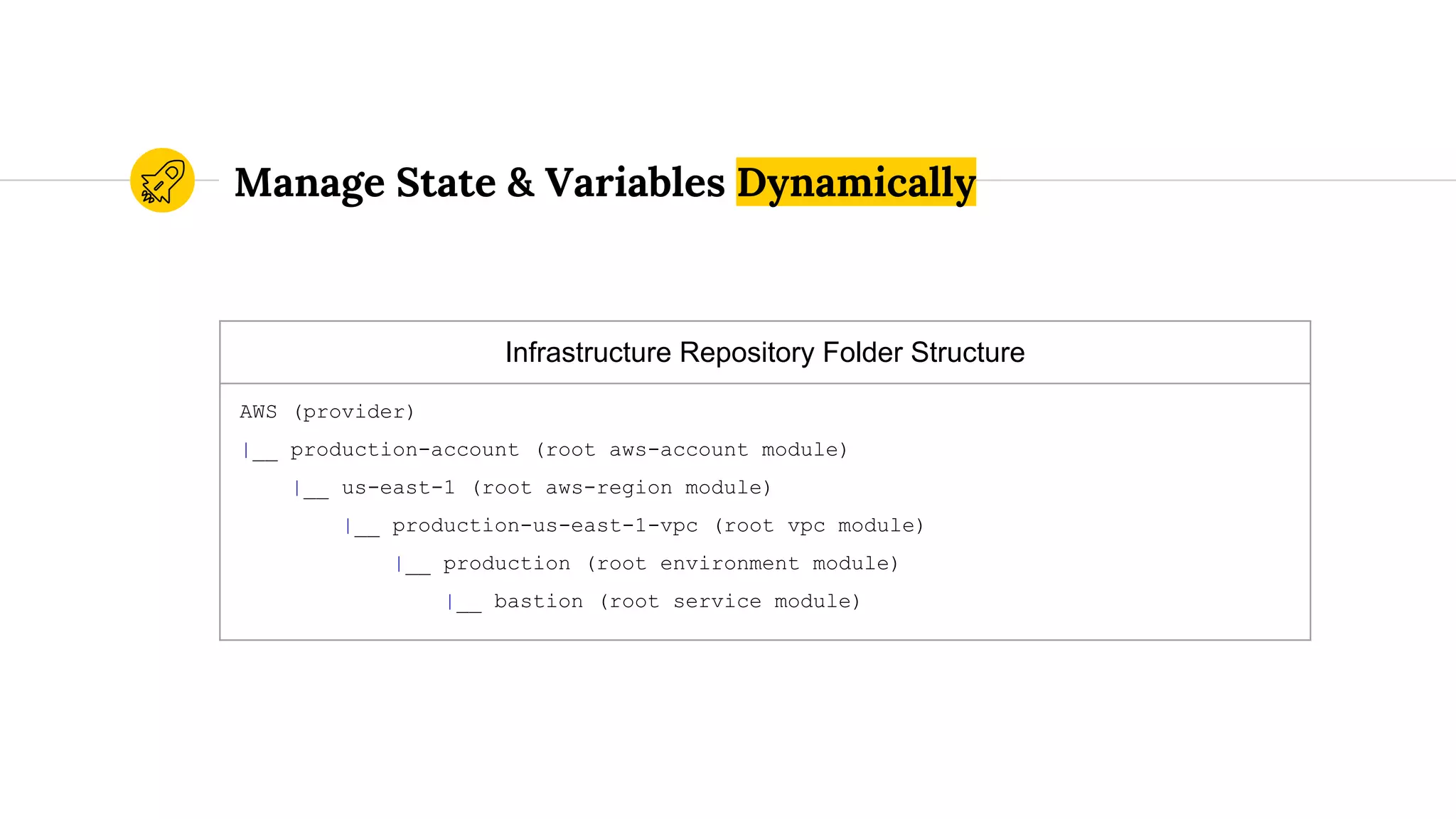
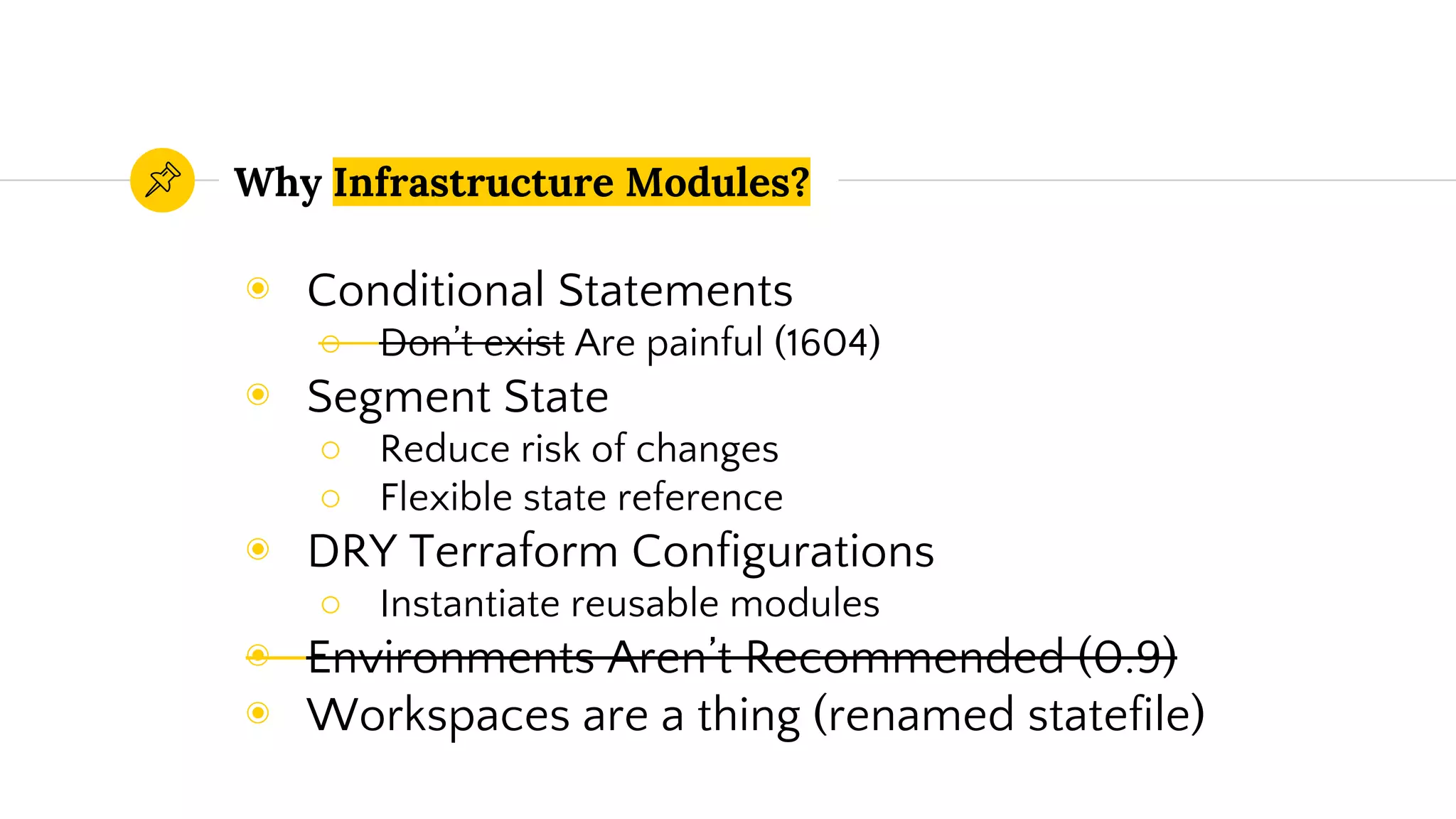
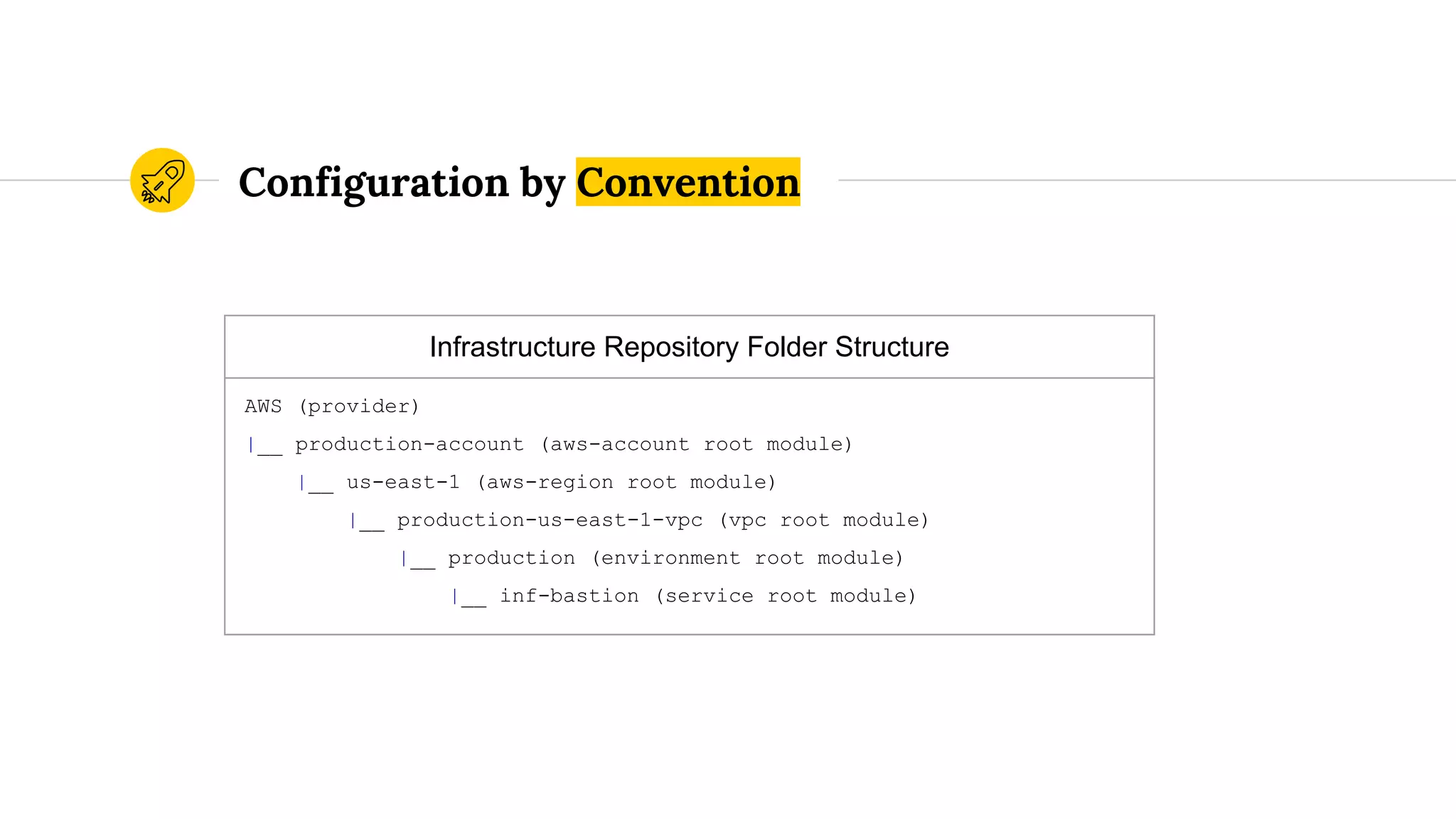
The document discusses best practices for using Terraform at scale, focusing on reducing complexity and increasing modularity in infrastructure as code. It emphasizes the importance of parameterization, naming conventions, and the structuring of Terraform repositories to maintain organization and manageability. Additionally, it presents code samples for AWS resource provisioning, highlighting Terraform’s capabilities to automate the creation and management of cloud resources.










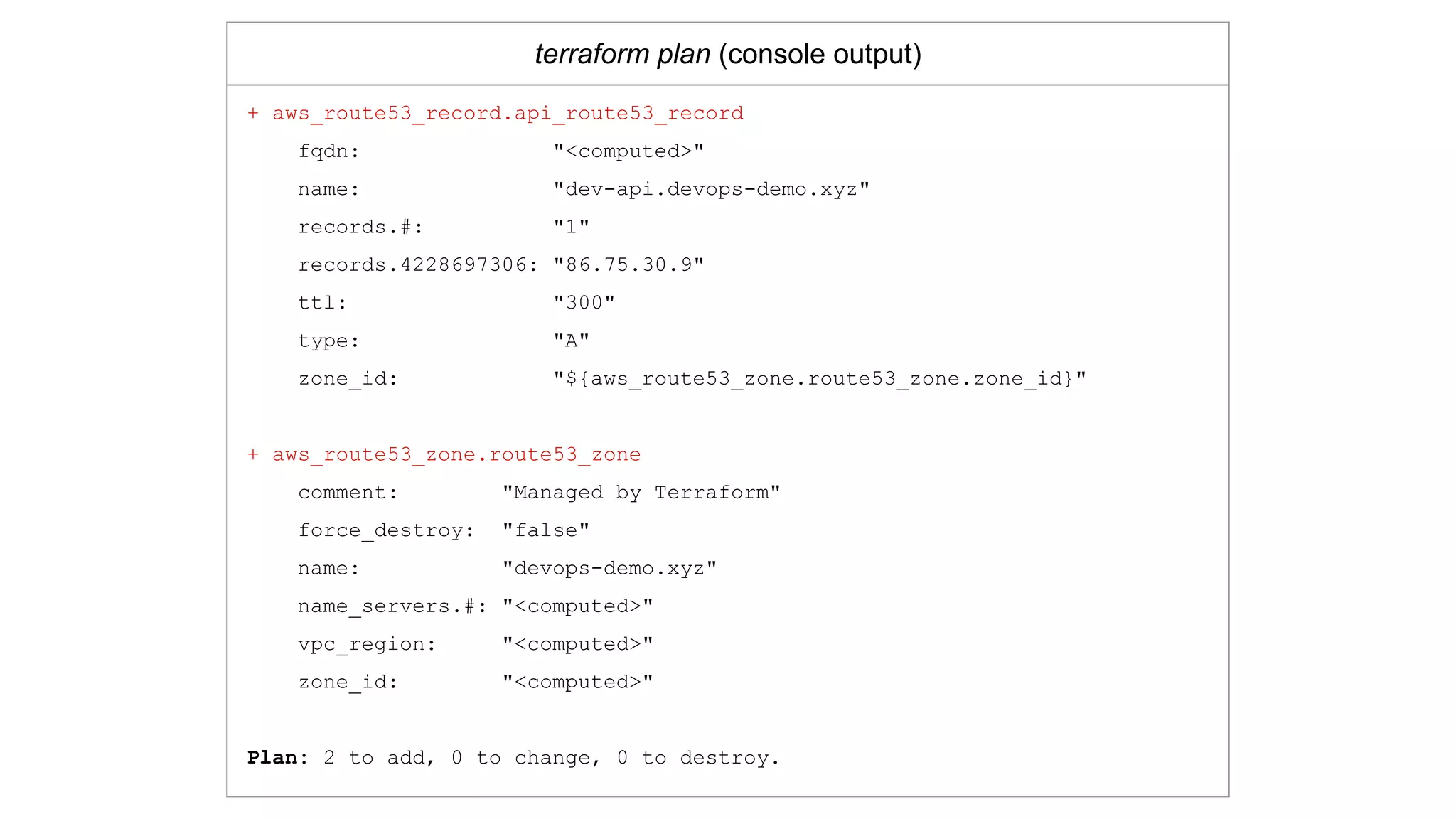
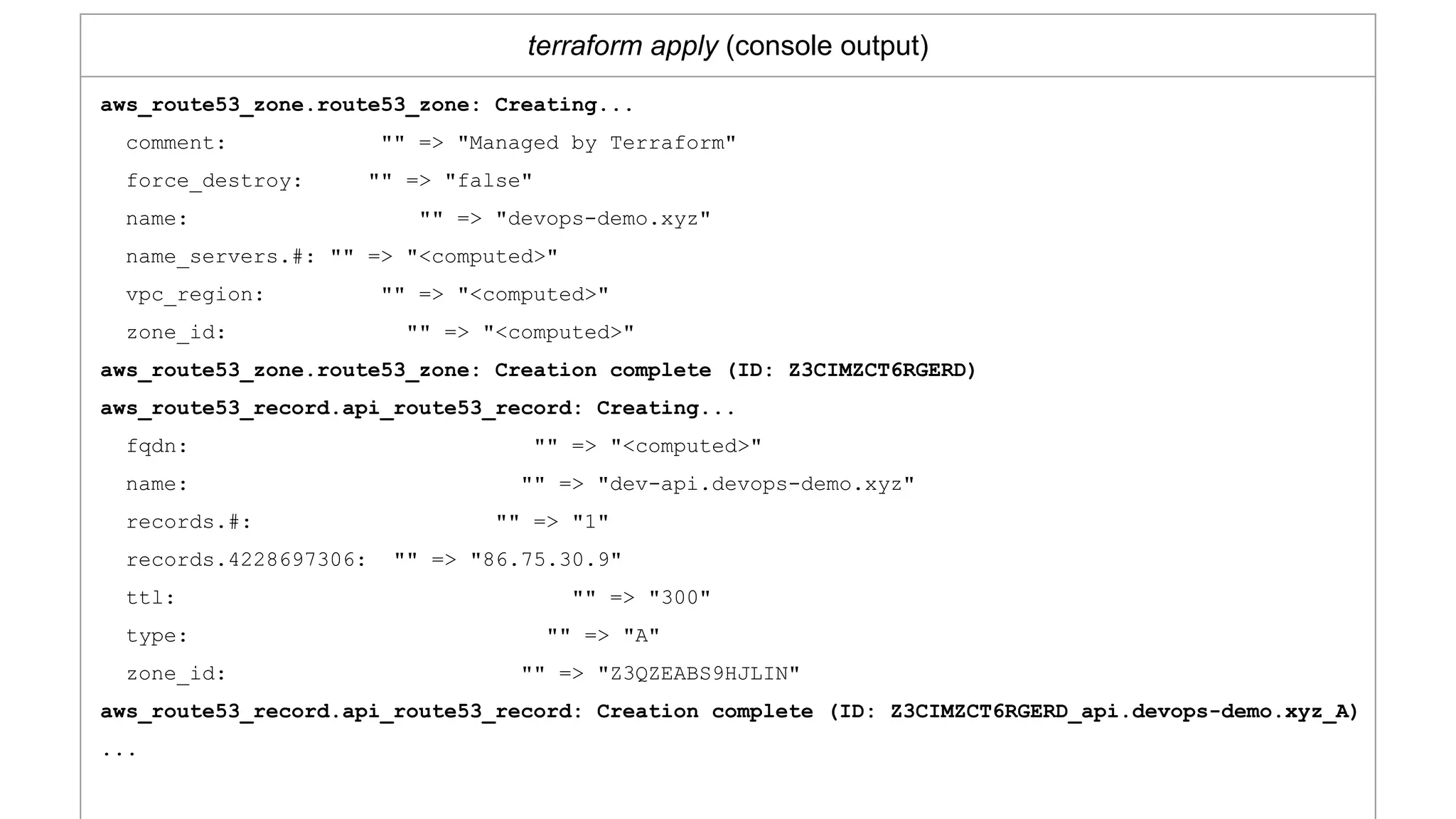
![AWS Route53 Provisioners
route53.tf
resource "aws_route53_zone" "route53_zone" {
name = "devops-demo.xyz"
}
resource "aws_route53_record" "api_route53_record" {
zone_id = "${aws_route53_zone.route53_zone.zone_id}"
name = "dev-api.devops-demo.xyz"
type = "A"
ttl = "300"
records = ["86.75.30.9"]
}](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-26-2048.jpg)
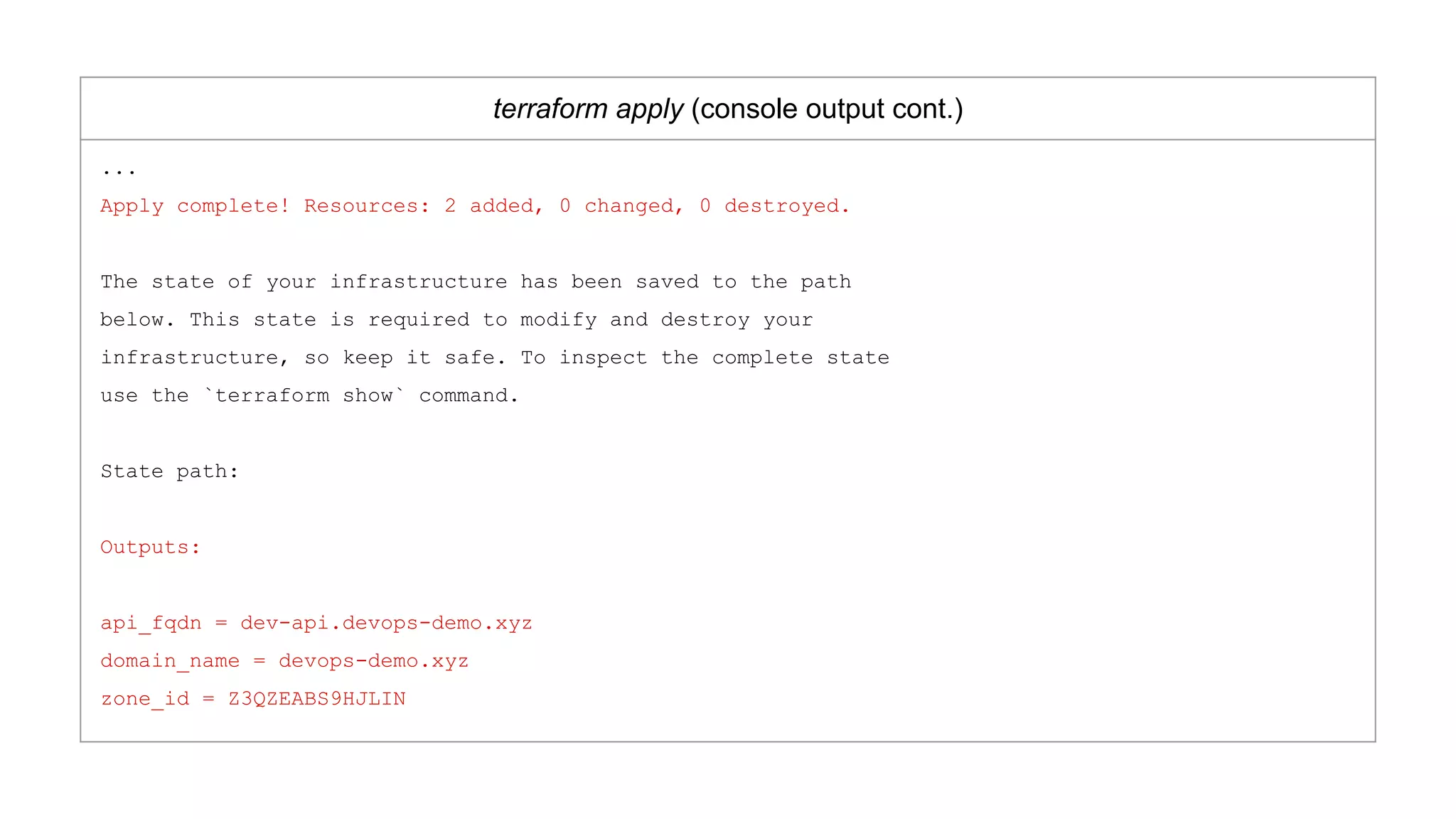
![AWS Route53 Provisioners
route53.tf
resource "aws_route53_zone" "route53_zone" {
name = "devops-demo.xyz"
}
resource "aws_route53_record" "api_route53_record" {
zone_id = "${aws_route53_zone.route53_zone.zone_id}"
name = "dev-api.devops-demo.xyz"
type = "A"
ttl = "300"
records = ["86.75.30.9"]
}](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-27-2048.jpg)
![route53.tf
resource "aws_route53_zone" "route53_zone" {
name = "devops-demo.xyz"
}
resource "aws_route53_record" "api_route53_record" {
zone_id = "${aws_route53_zone.route53_zone.zone_id}"
name = "dev-api.devops-demo.xyz"
type = "A"
ttl = "300"
records = ["86.75.30.9"]
}
AWS Route53 Provisioners](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-28-2048.jpg)
![route53.tf
resource "aws_route53_zone" "route53_zone" {
name = "devops-demo.xyz"
}
resource "aws_route53_record" "api_route53_record" {
zone_id = "${aws_route53_zone.route53_zone.zone_id}"
name = "dev-api.devops-demo.xyz"
type = "A"
ttl = "300"
records = ["86.75.30.9"]
}
AWS Route53 Provisioners](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-29-2048.jpg)
![route53.tf
resource "aws_route53_zone" "route53_zone" {
name = "devops-demo.xyz"
}
resource "aws_route53_record" "api_route53_record" {
zone_id = "${aws_route53_zone.route53_zone.zone_id}"
name = "dev-api.devops-demo.xyz"
type = "A"
ttl = "300"
records = ["86.75.30.9"]
}
AWS Route53 Provisioners](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-30-2048.jpg)
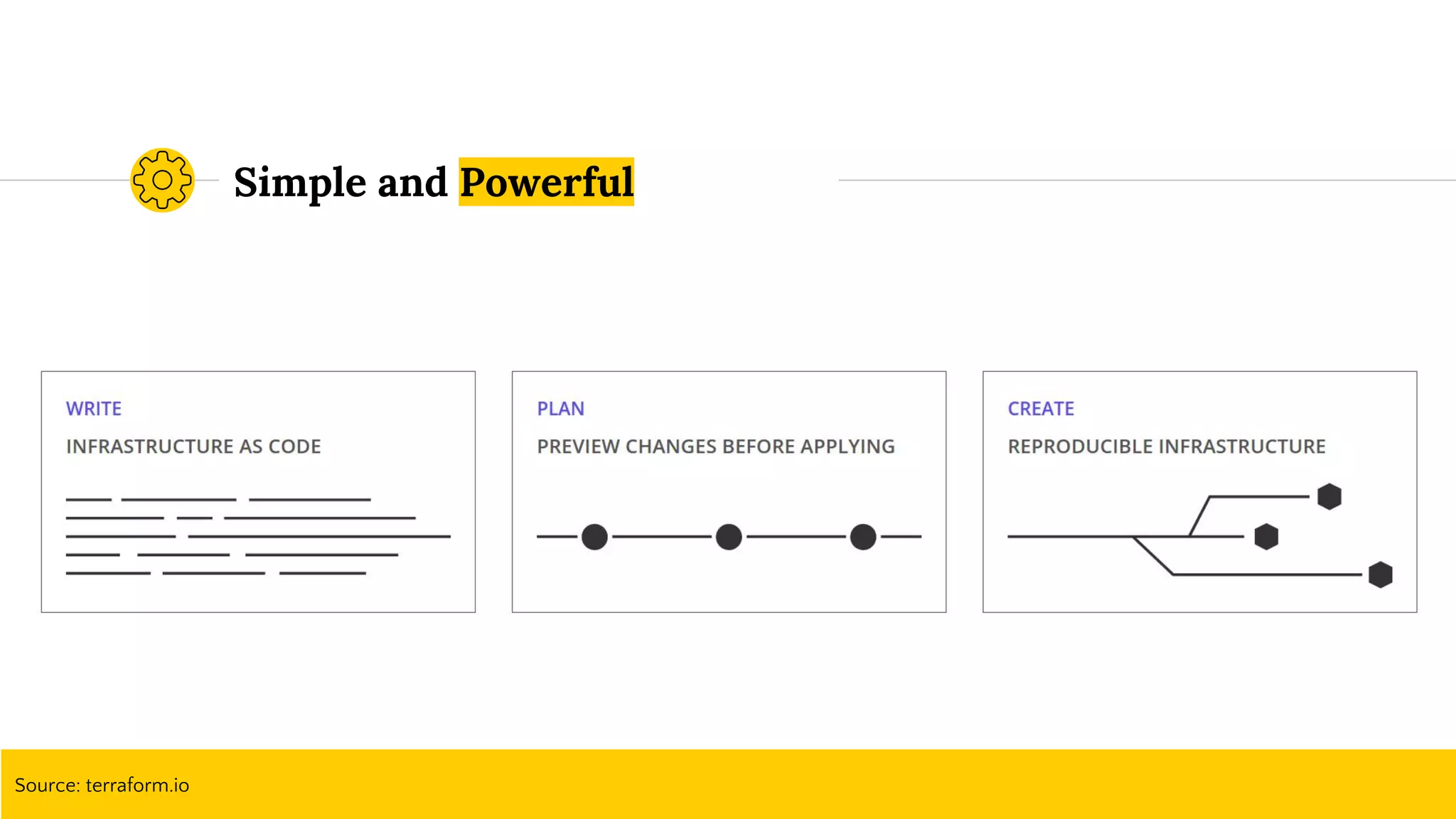
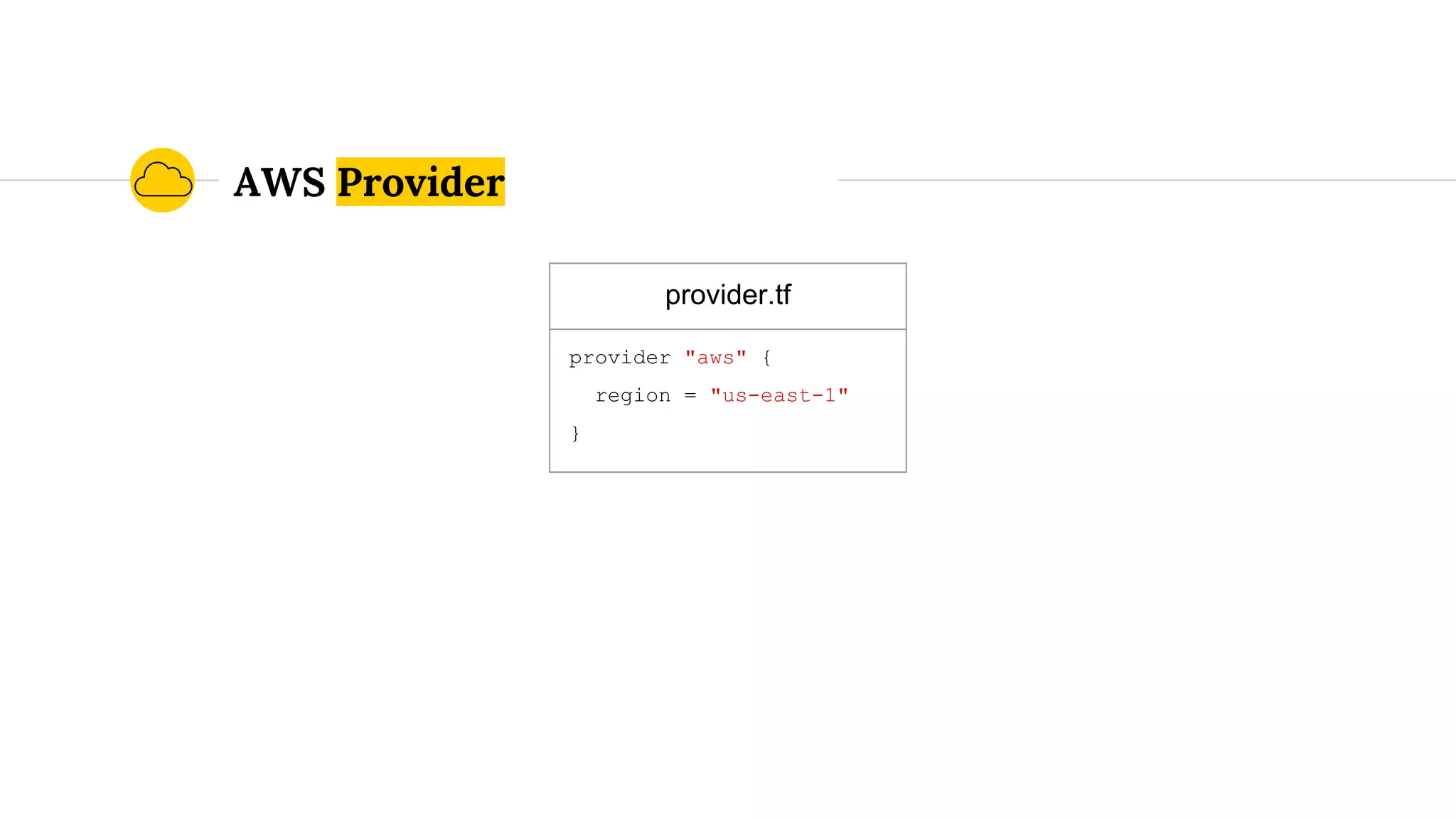
![Parameterize To Stay DRY
provider.tf
provider "aws" {
region = "us-east-1"
}
route53.tf
resource "aws_route53_zone" "route53_zone" {
name = "devops-demo.xyz"
}
resource "aws_route53_record" "api_route53_record" {
zone_id = "${aws_route53_zone.route53_zone.zone_id}"
name = "dev-api.devops-demo.xyz"
type = "A"
ttl = "300"
records = ["86.75.30.9"]
}](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-34-2048.jpg)
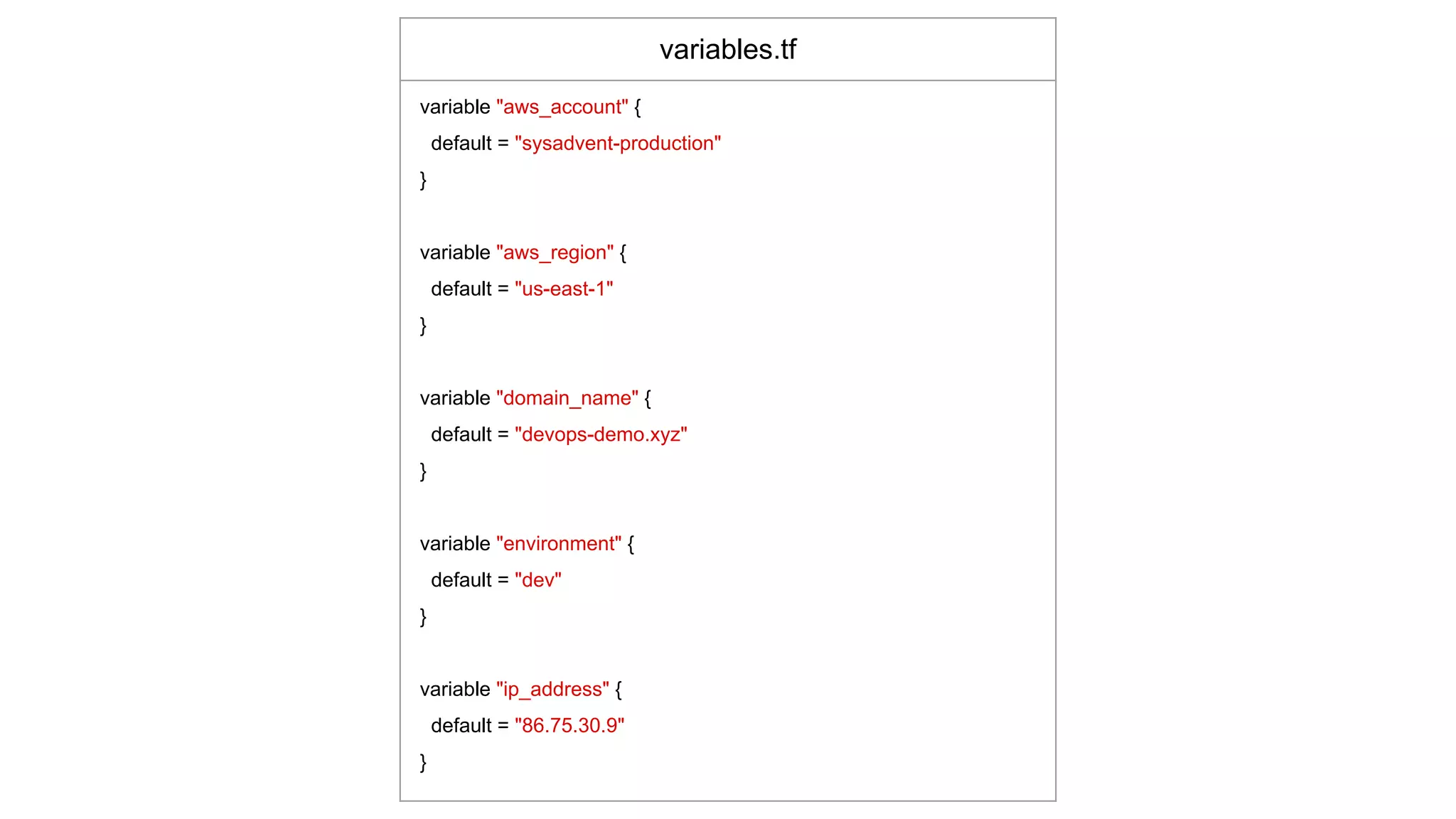
![Input Variables
provider.tf
provider "aws" {
region = "${var.aws_region}"
}
route53.tf
resource "aws_route53_zone" "route53_zone" {
name = "${var.domain_name}"
}
resource "aws_route53_record" "api_route53_record" {
zone_id = "${aws_route53_zone.route53_zone.zone_id}"
name = "${var.environment}-api.${var.domain_name}"
type = "A"
ttl = "300"
records = ["${var.ip_address}”]
}](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-35-2048.jpg)
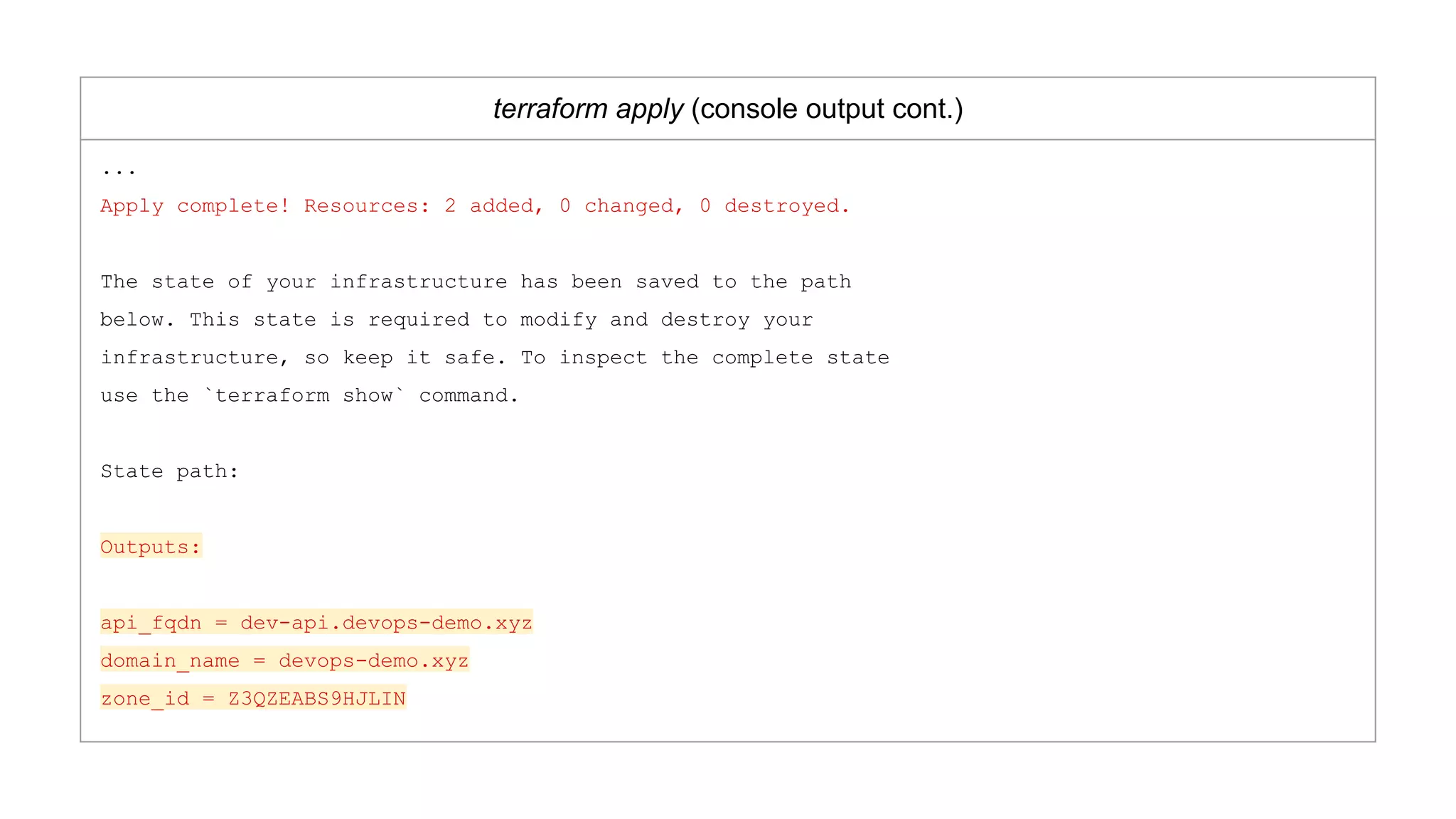
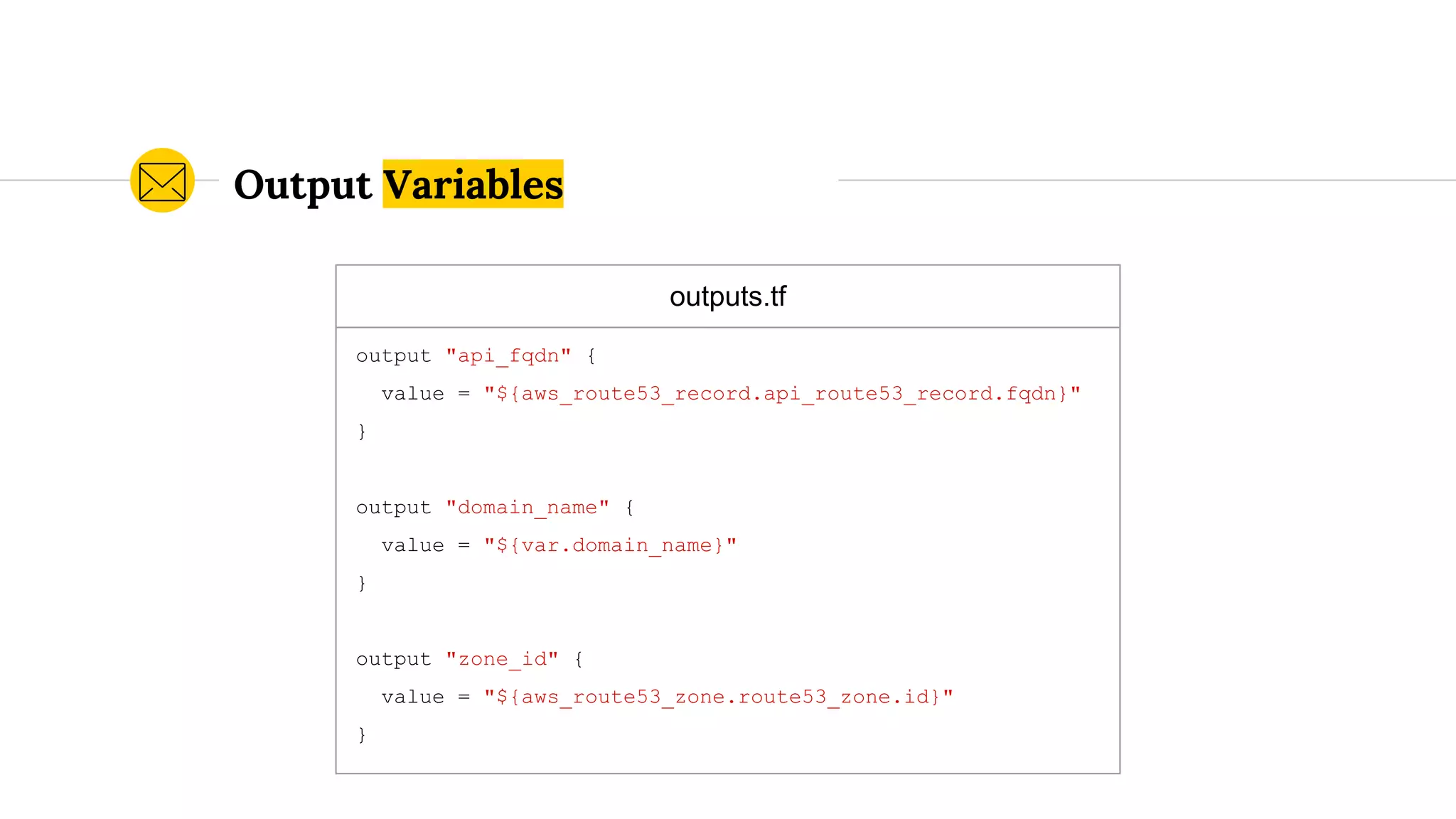
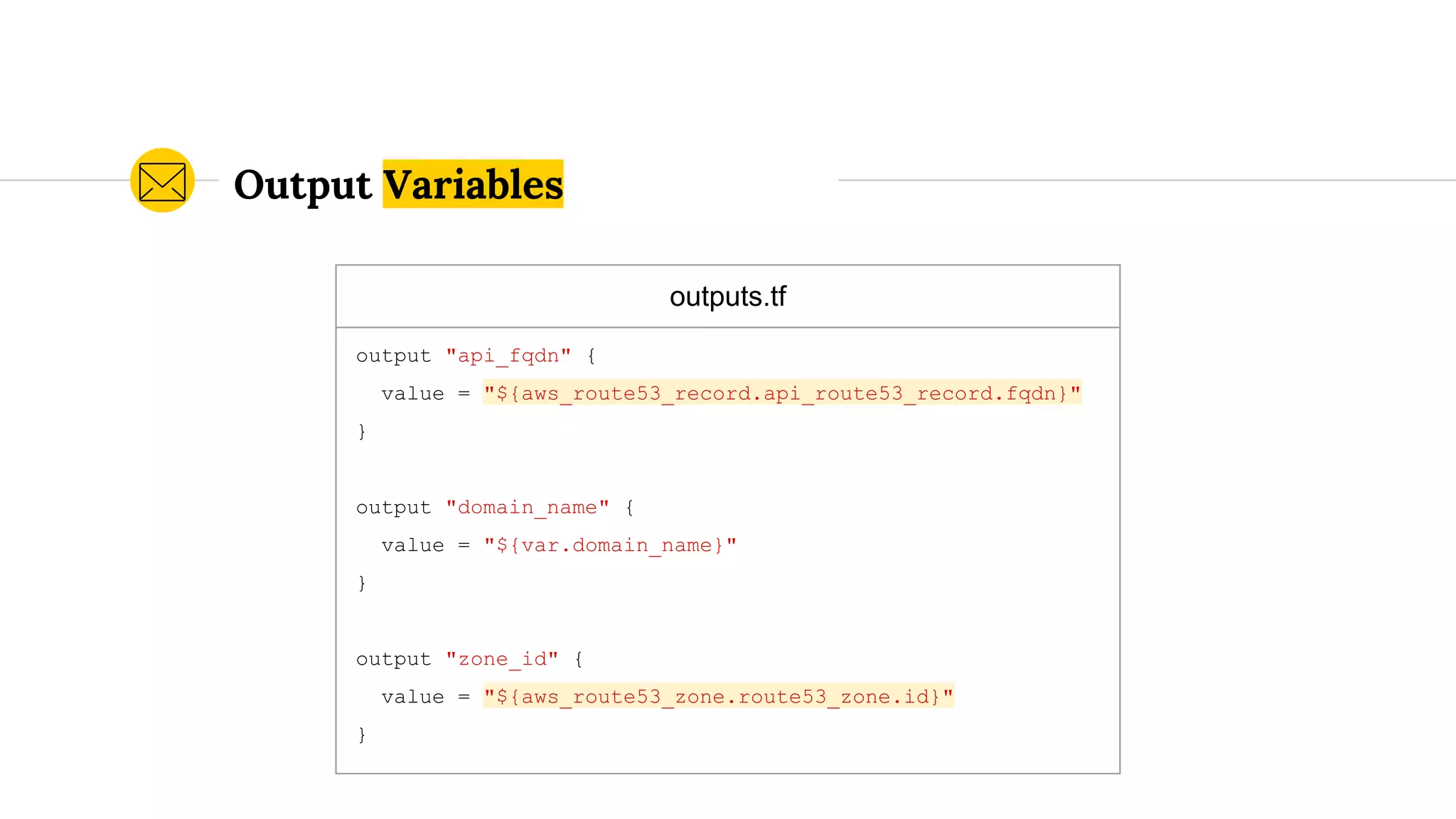
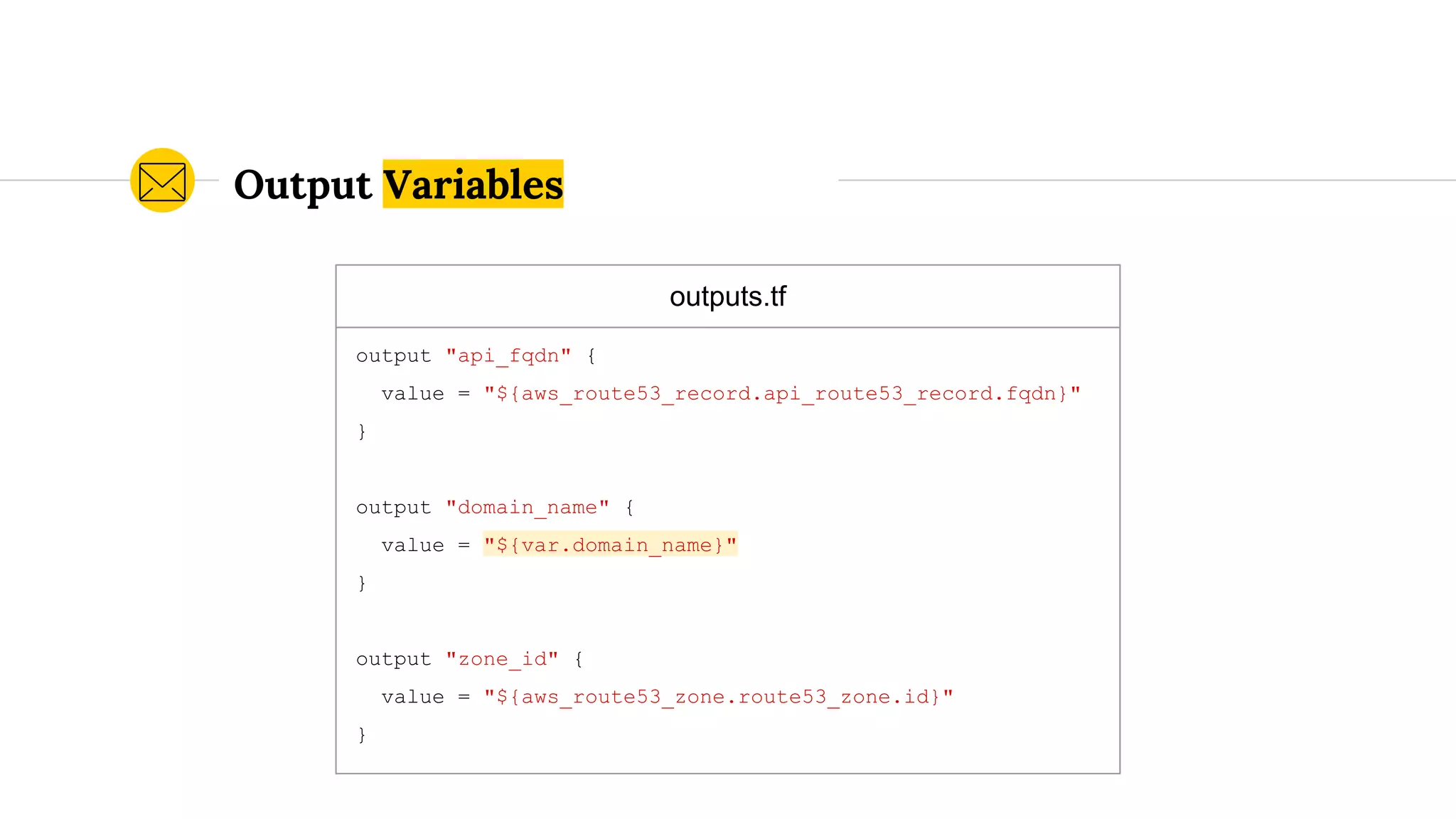


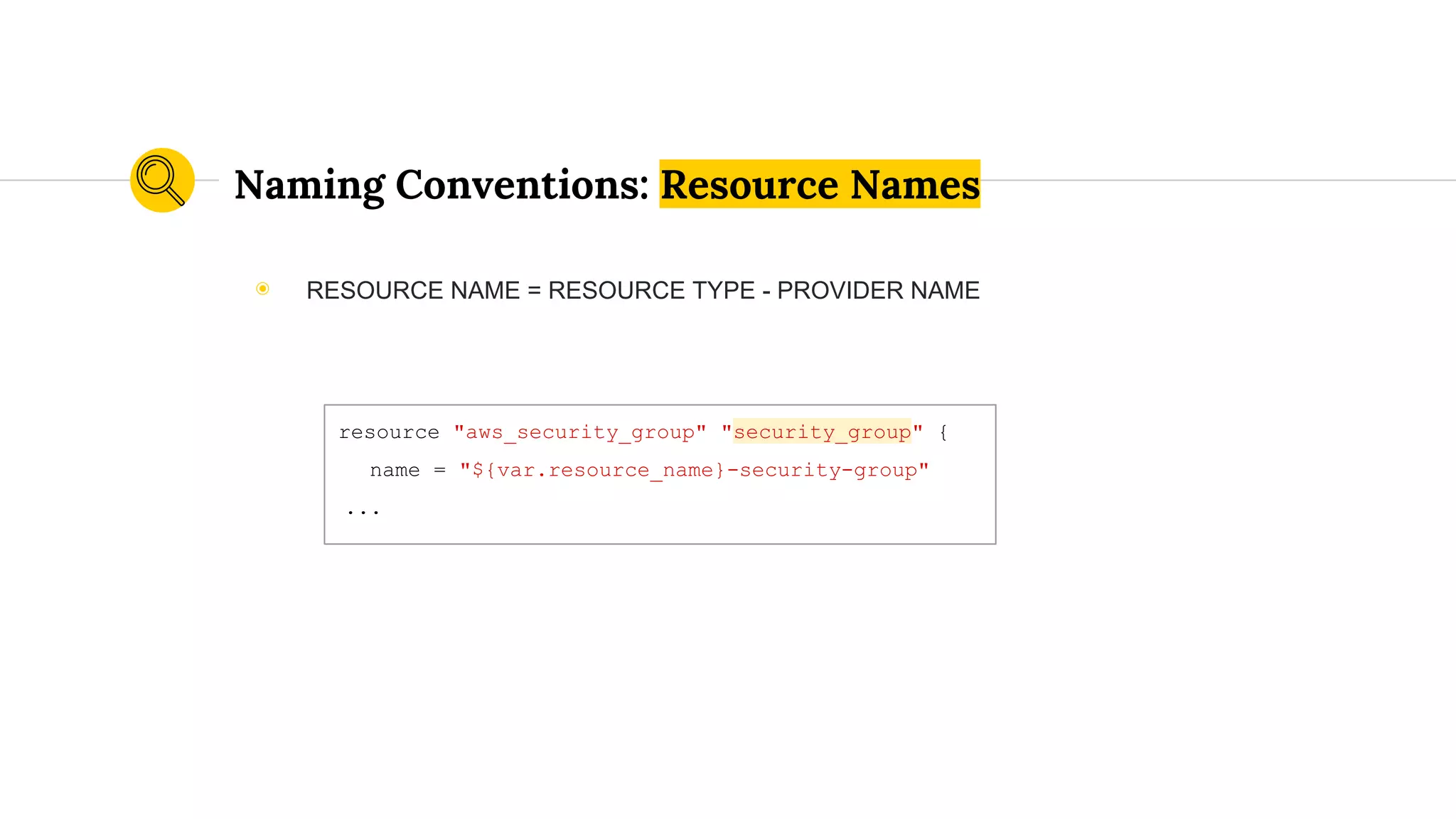
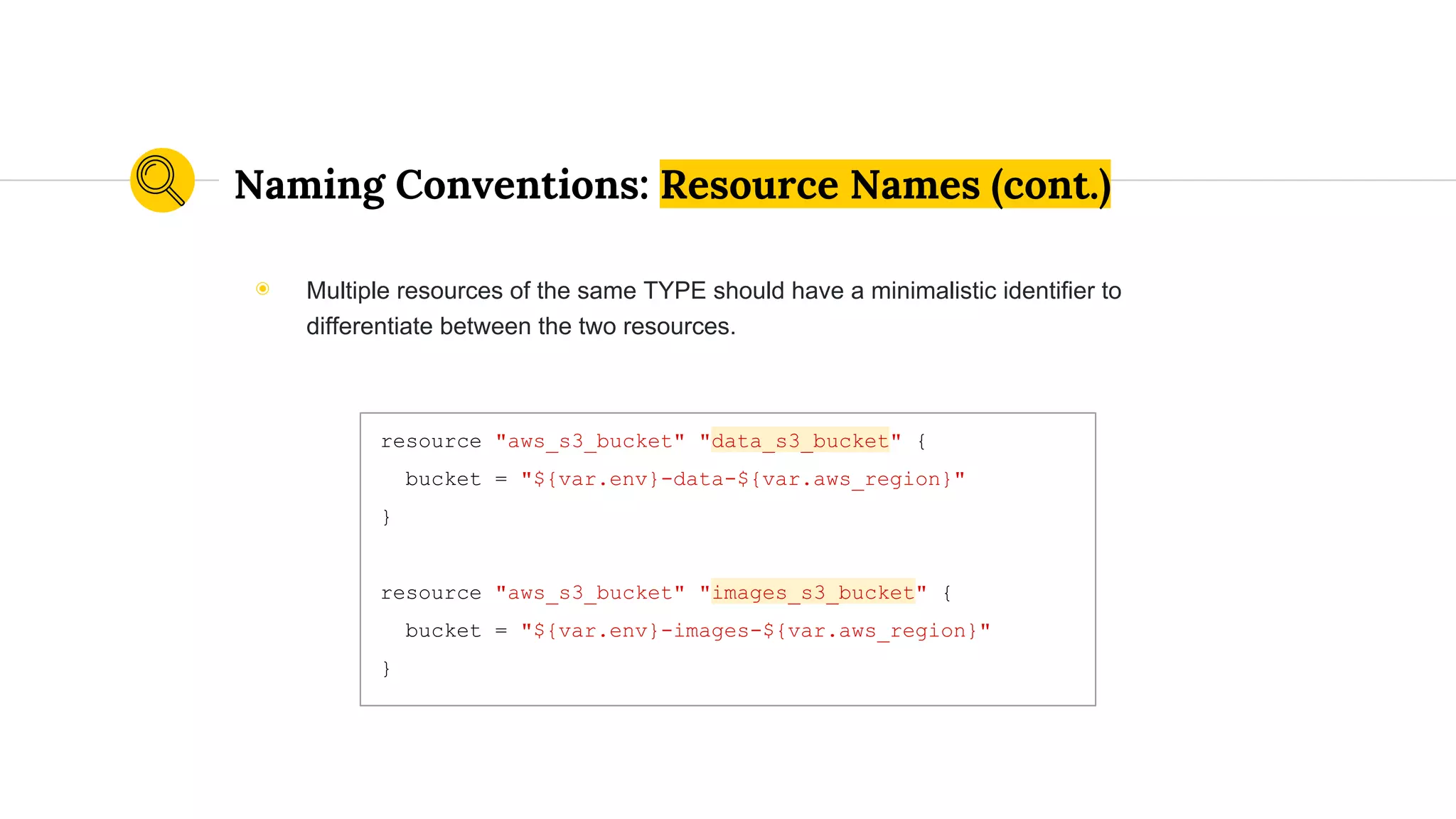
![When to Use an Underscore
resource "aws_route53_record" "api_route53_record" {
zone_id = "${aws_route53_zone.route53_zone.zone_id}"
name = "${var.environment}-api.${var.domain_name}"
type = "A"
ttl = "300"
records = ["${var.ip_address}"]
}
◉ Variable Names
◉ Resource Names
◉ Anything Interpolated](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-49-2048.jpg)
![When to Use a Hyphen
resource "aws_route53_record" "api_route53_record" {
zone_id = "${aws_route53_zone.route53_zone.zone_id}"
name = "${var.environment}-api.${var.domain_name}"
type = "A"
ttl = "300"
records = ["${var.ip_address}"]
}
◉ Resources Being Created](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-50-2048.jpg)
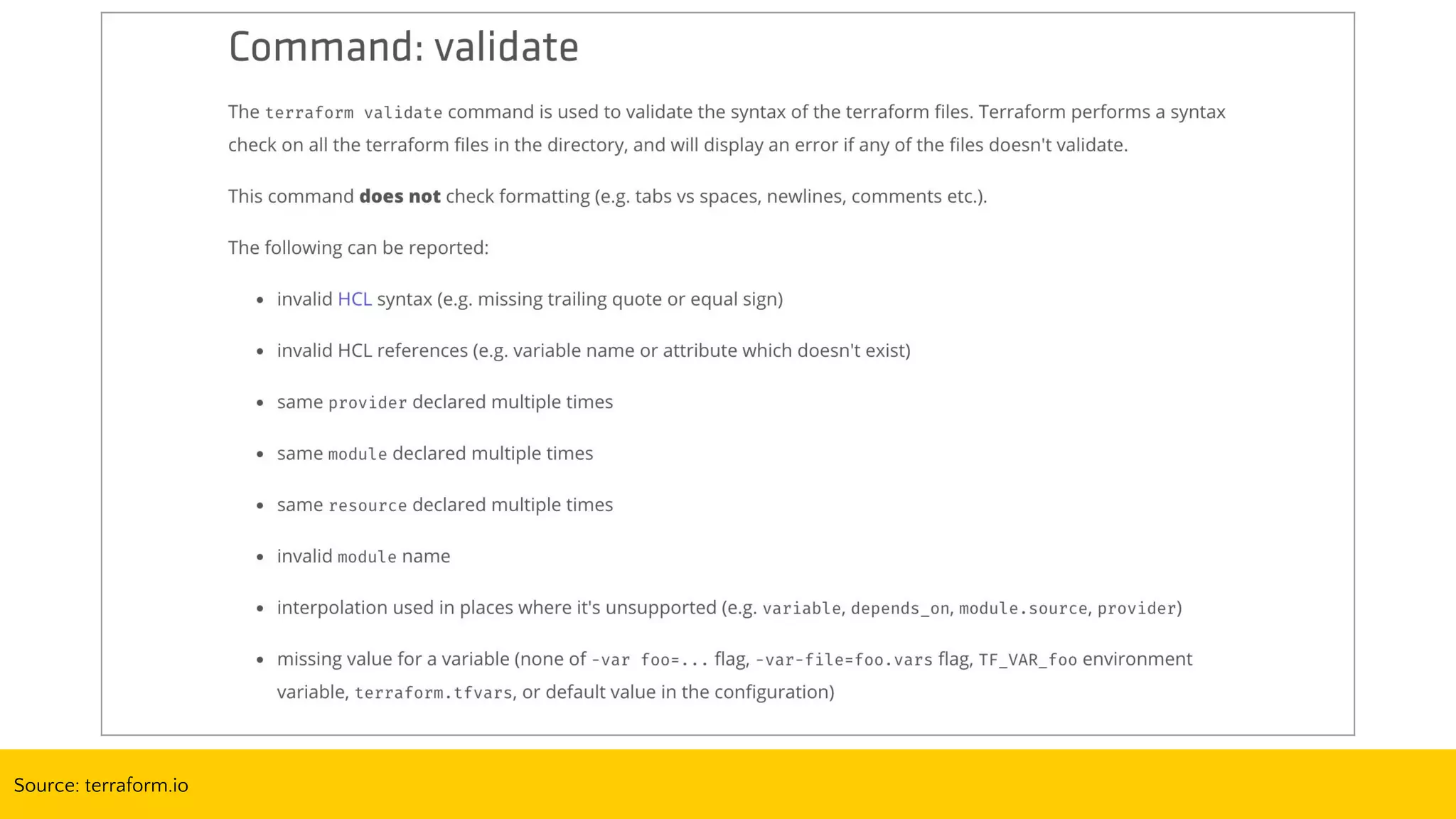
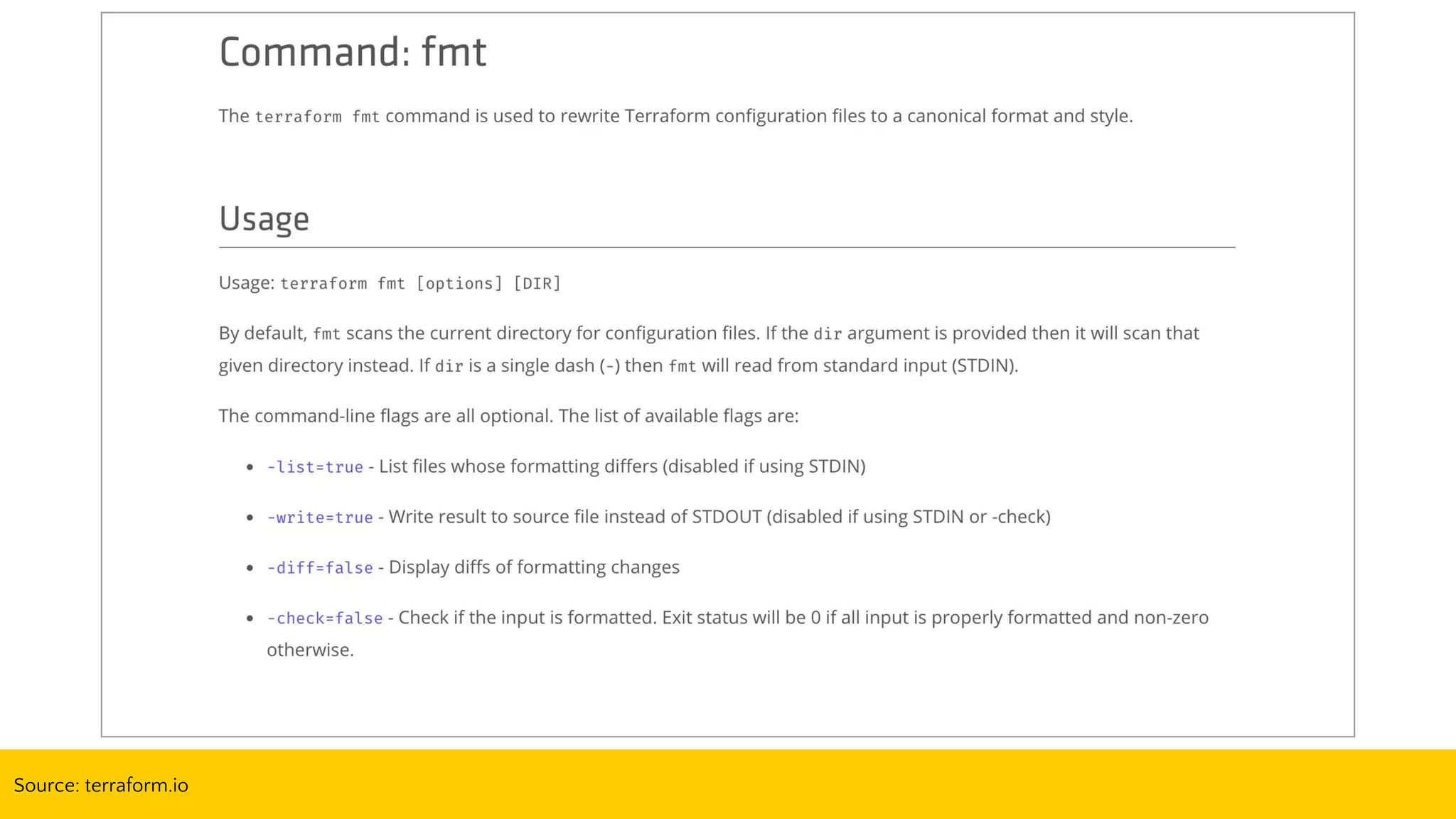





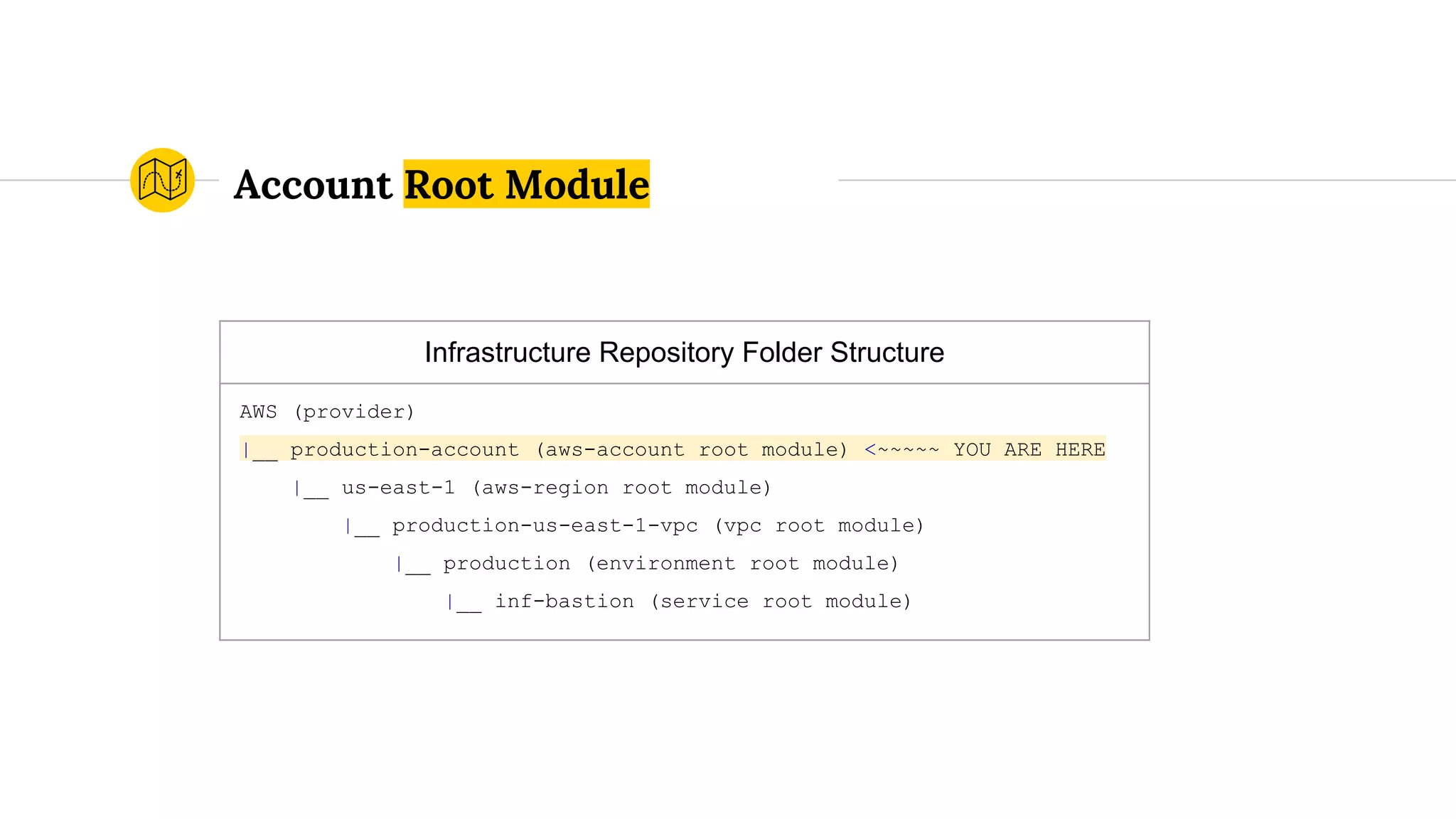
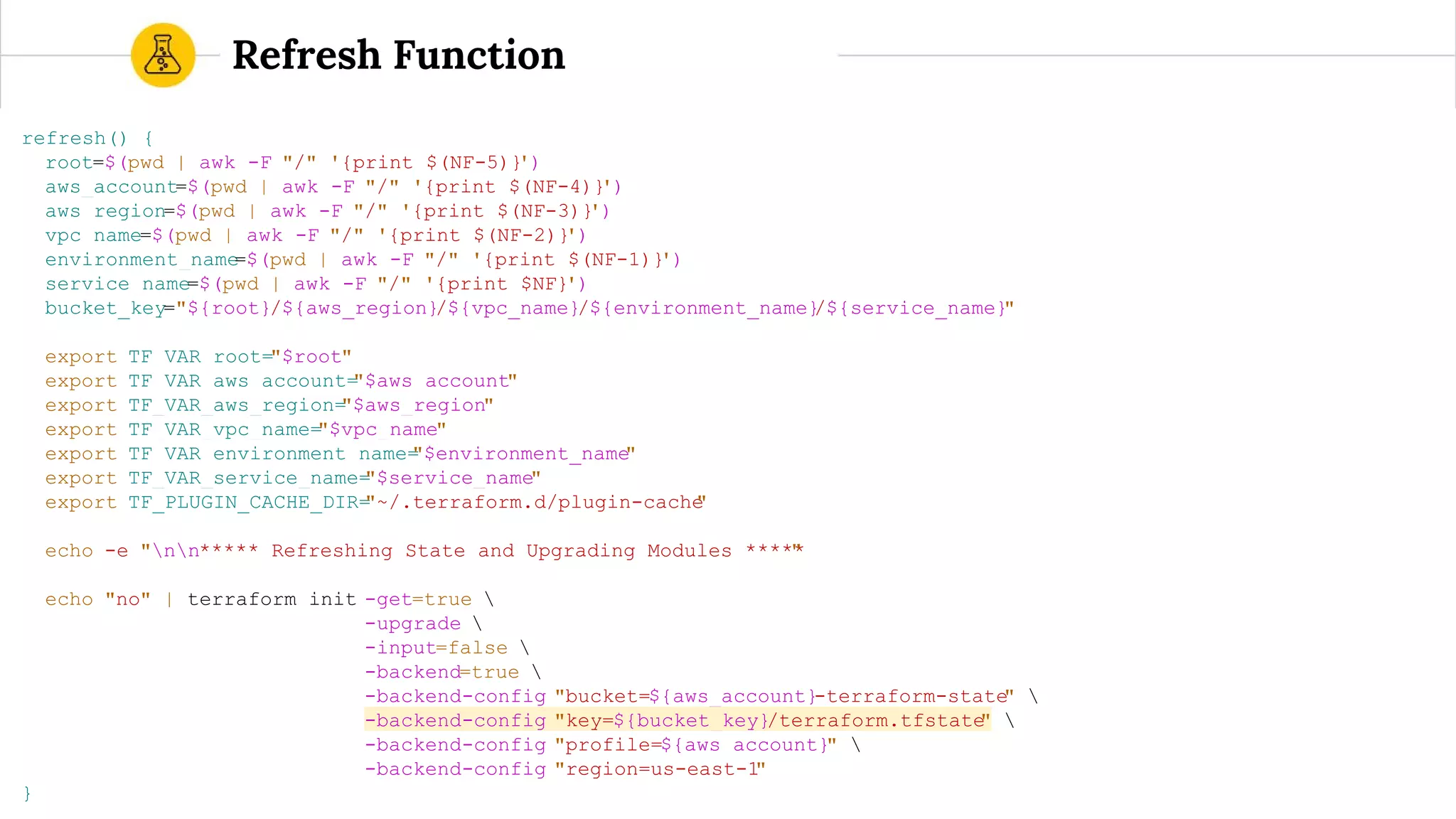
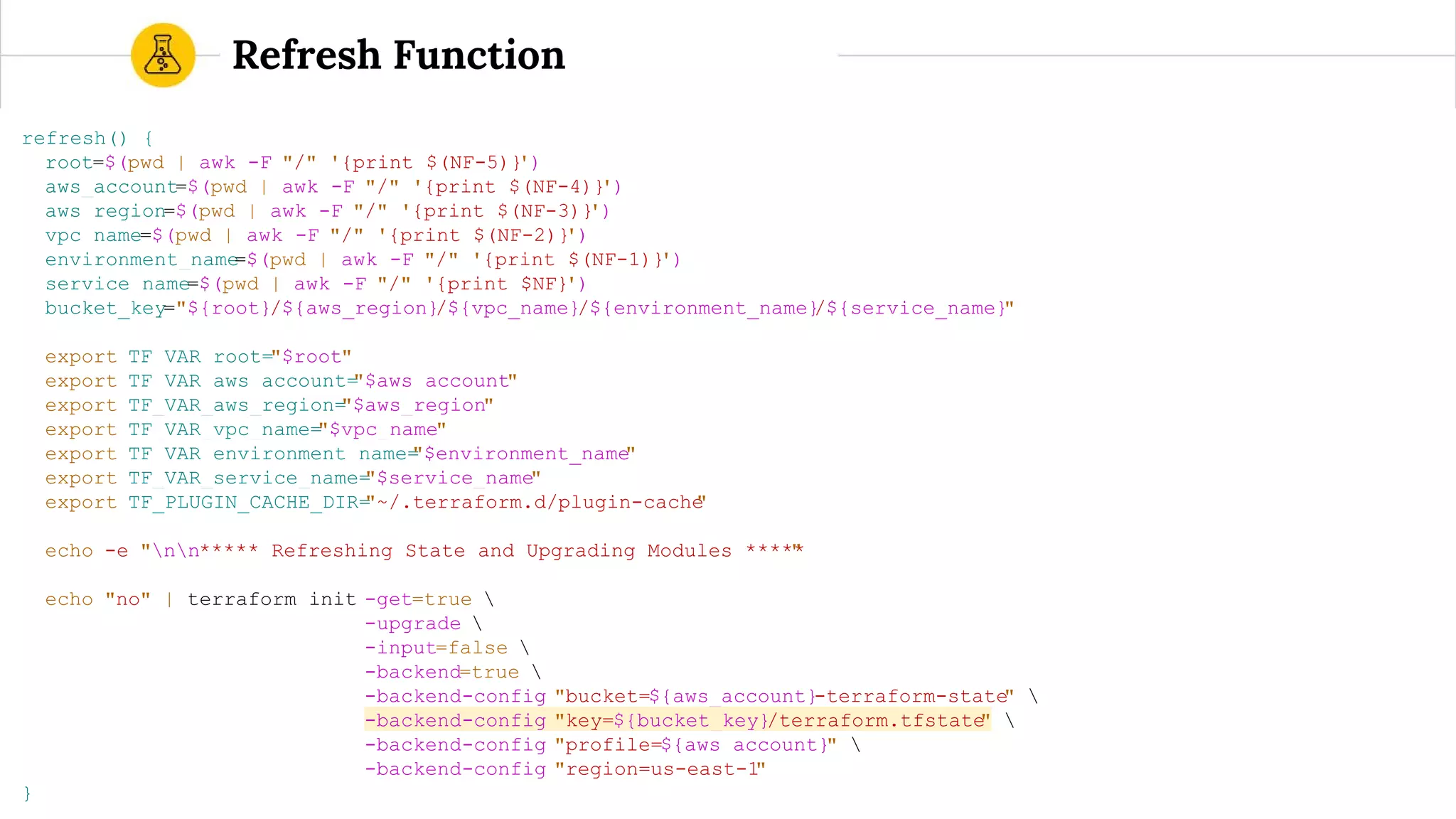
![terraform.sh (bash wrapper)
Usage: ./templates/account-terraform.sh [apply|destroy|plan|refresh|show]
The following arguments are supported:
apply Refresh the Terraform remote state, "terraform get -update", and "terraform apply"
destroy Refresh the Terraform remote state and destroy the Terraform stack
plan Refresh the Terraform remote state, "terraform get -update", and "terraform plan"
refresh Refresh the Terraform remote state
show Refresh and show the Terraform remote state](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-62-2048.jpg)




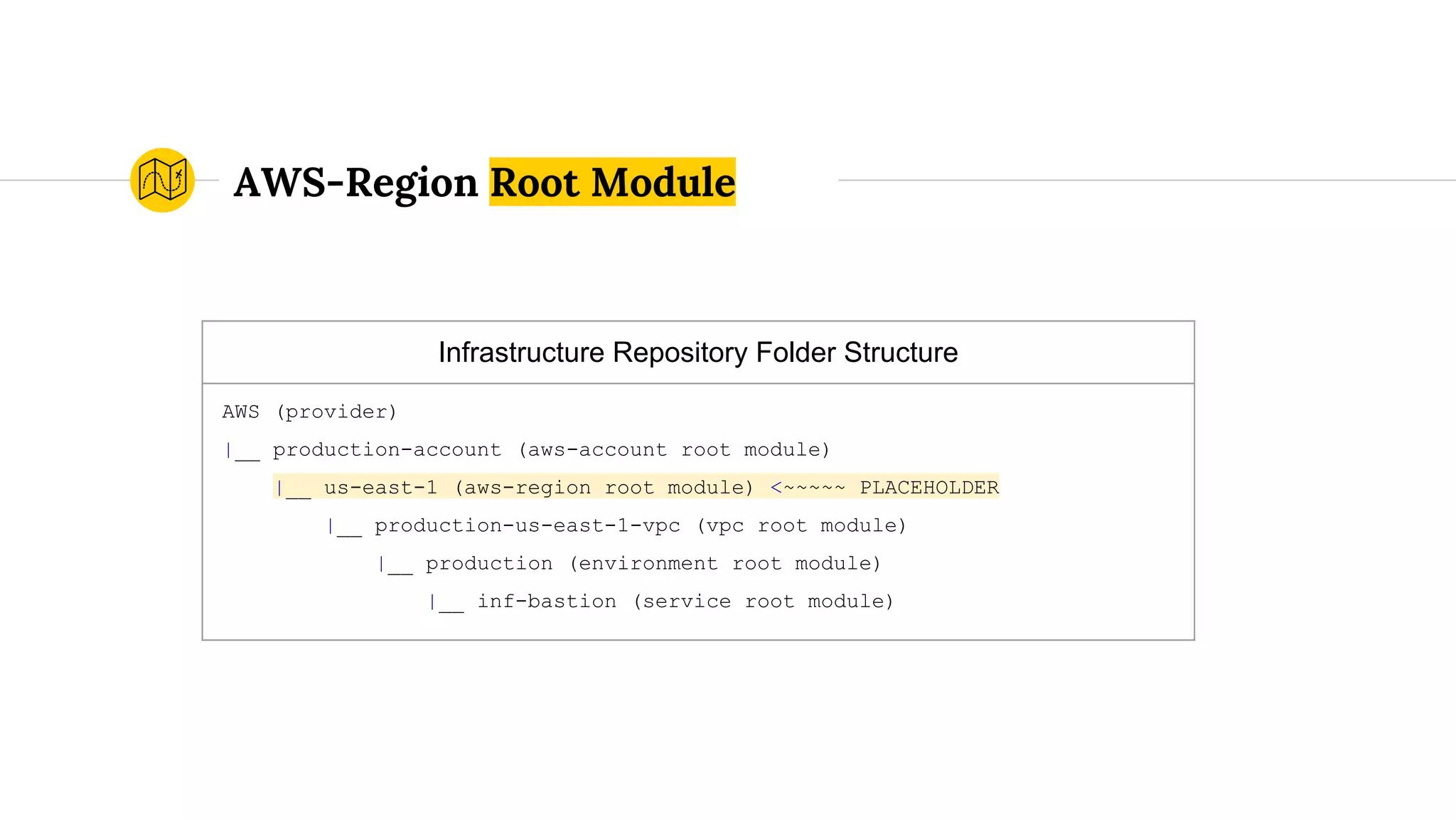
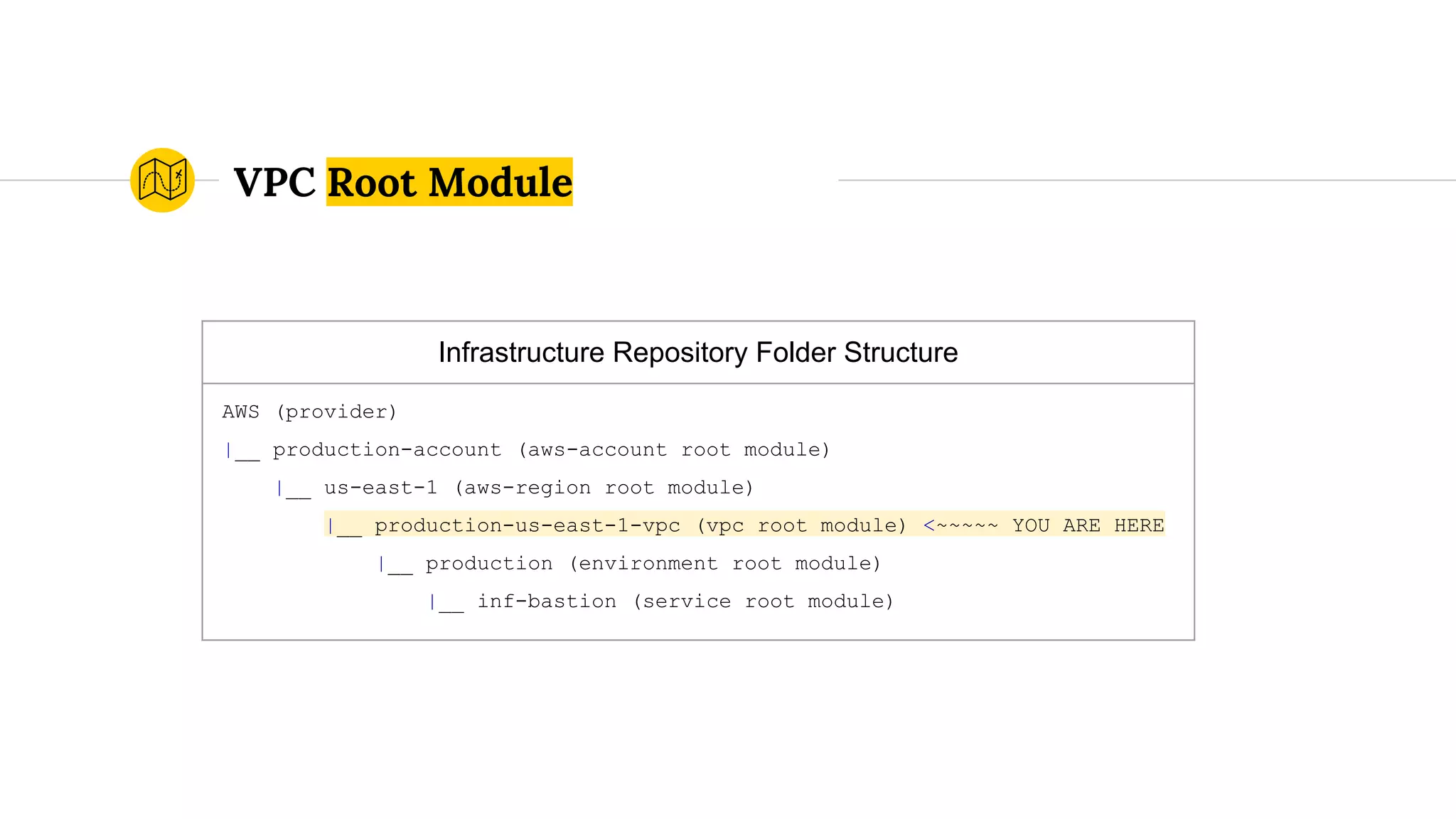
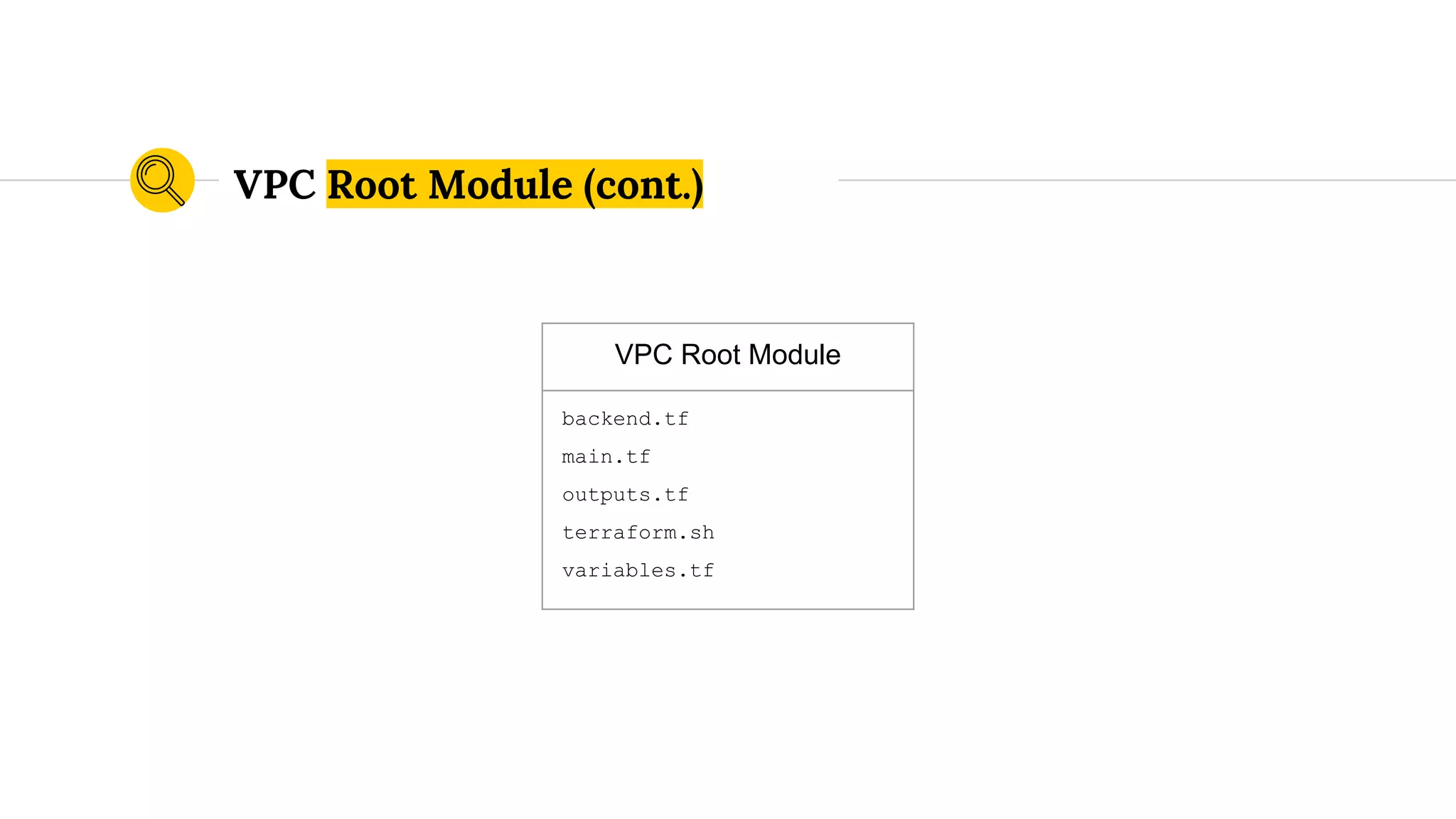
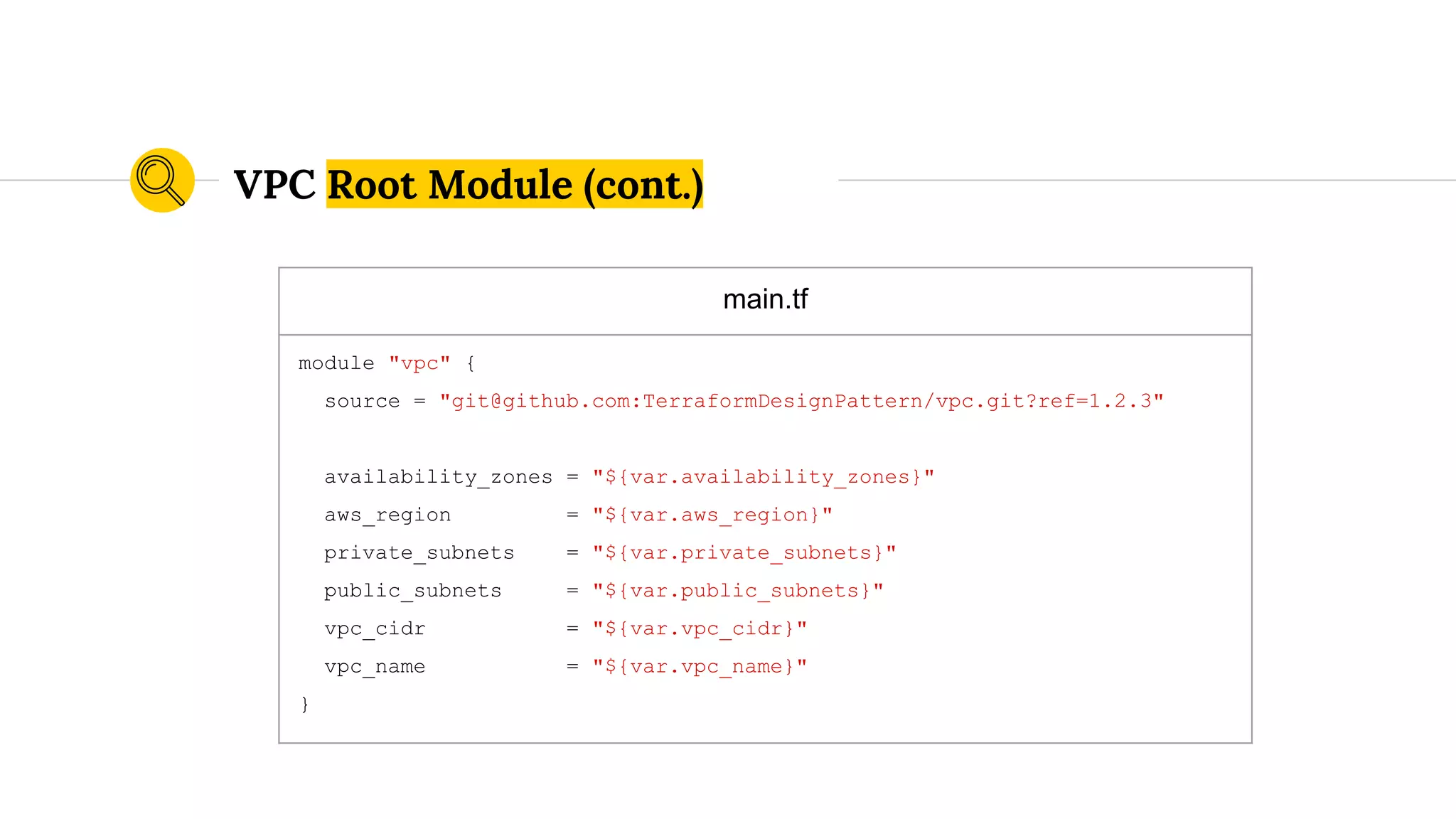
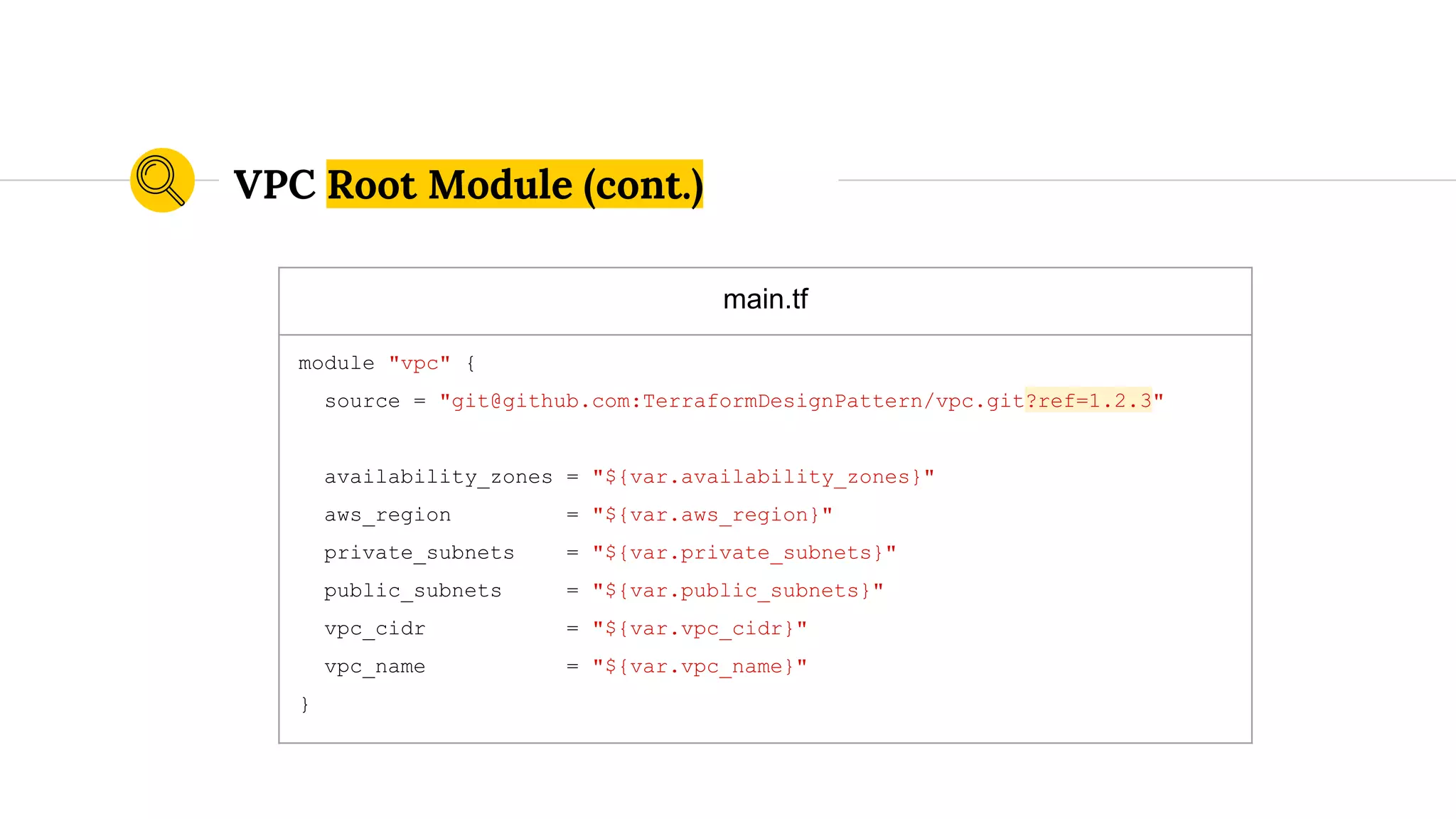
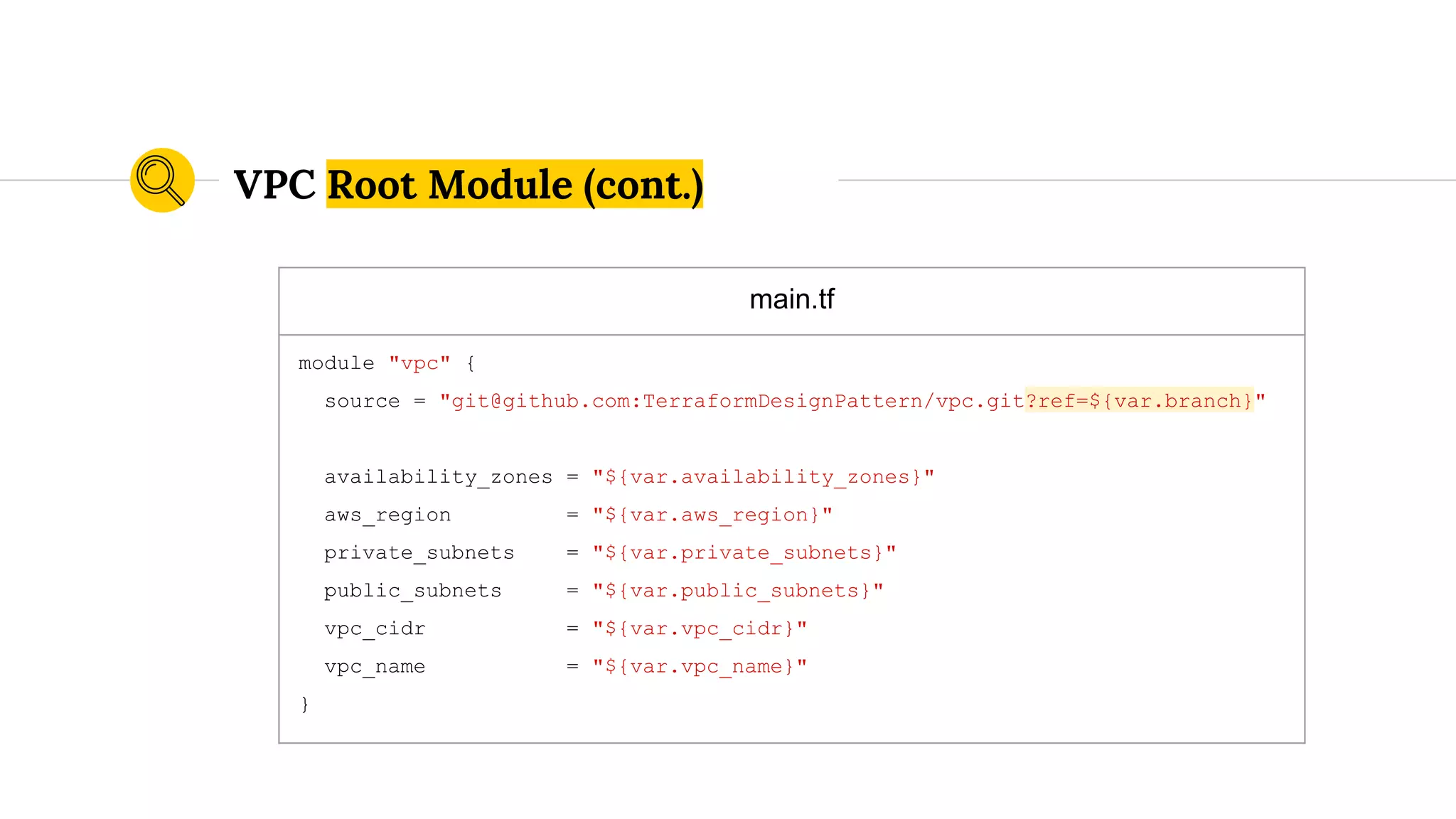

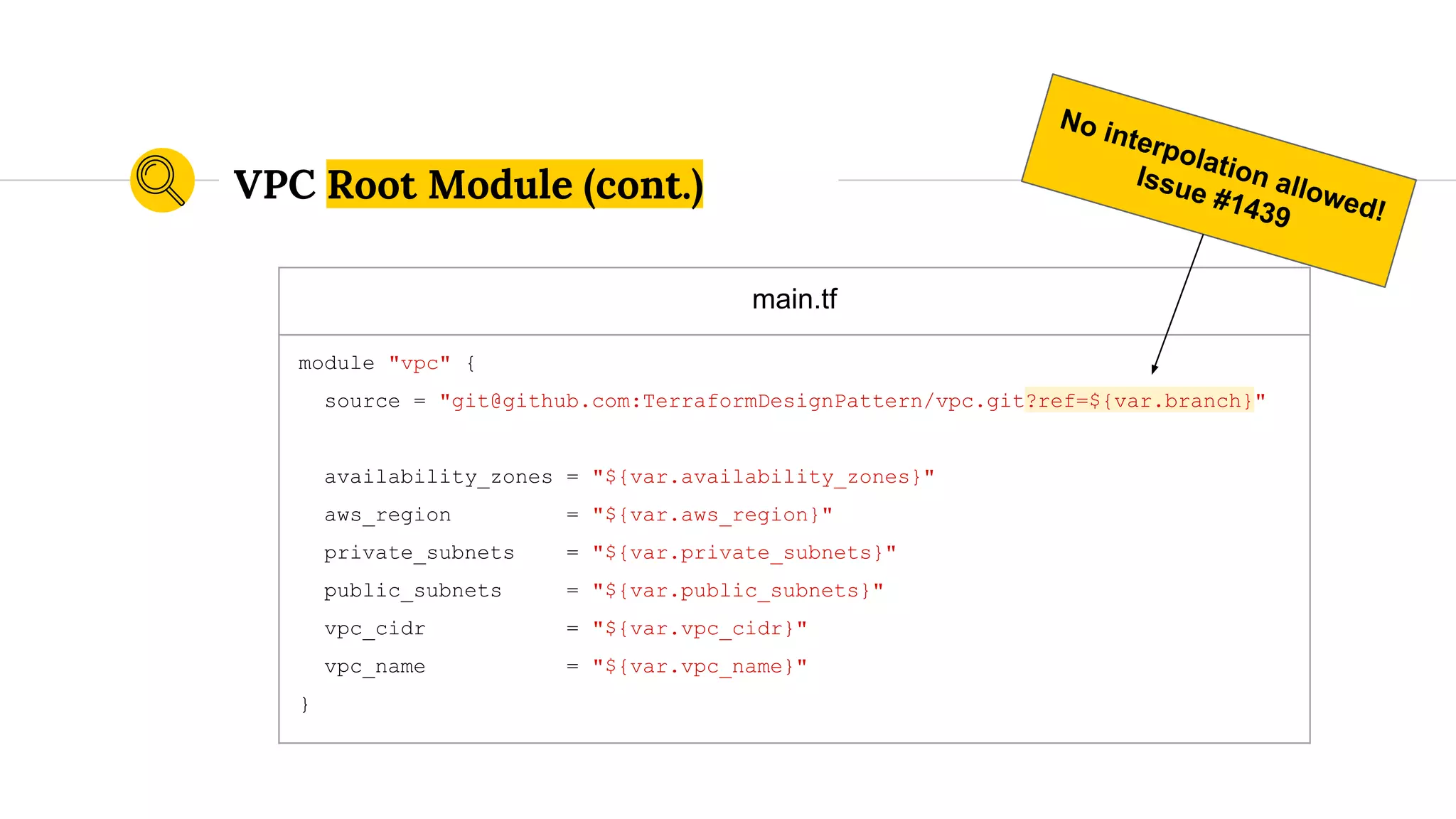
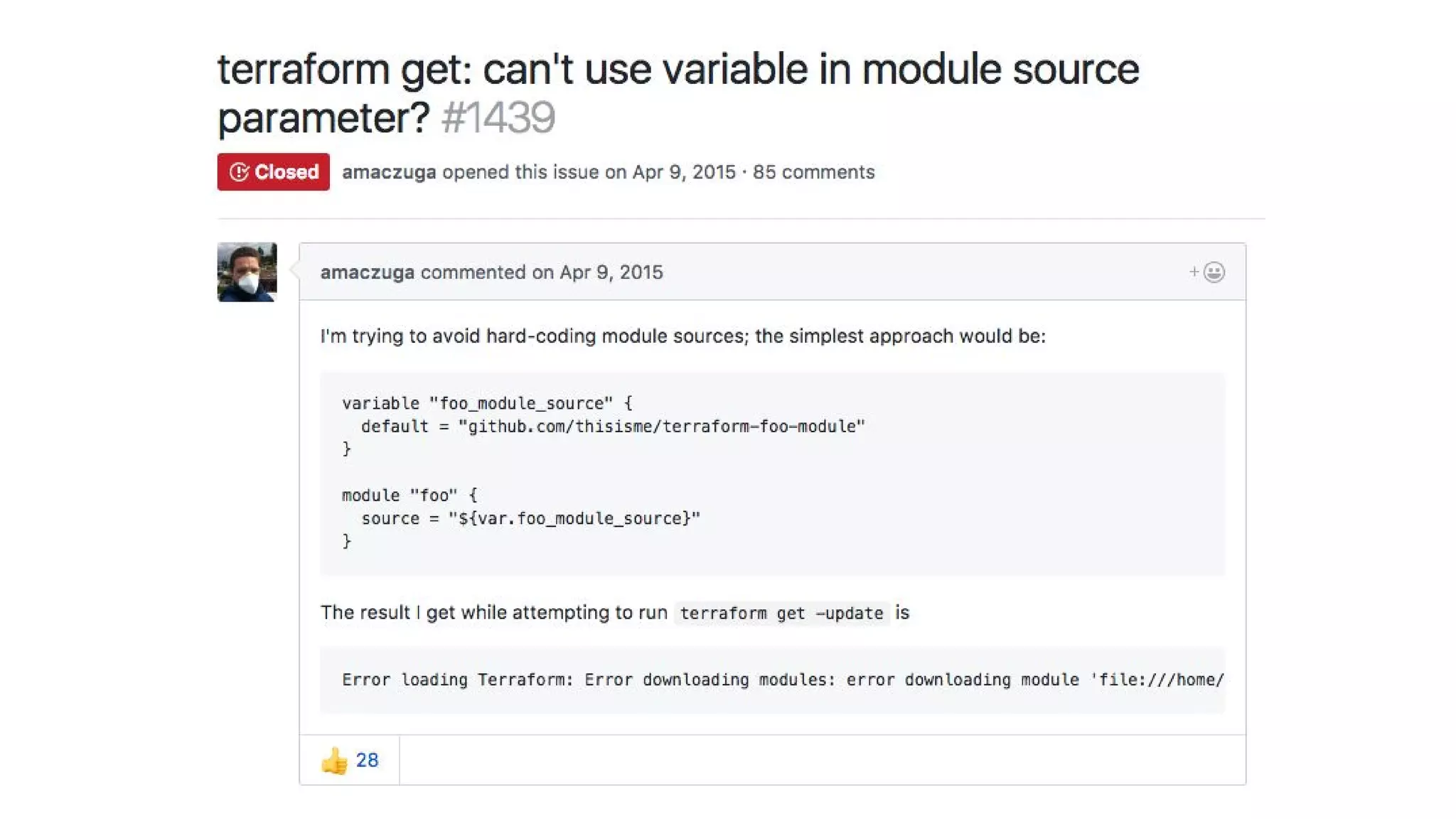
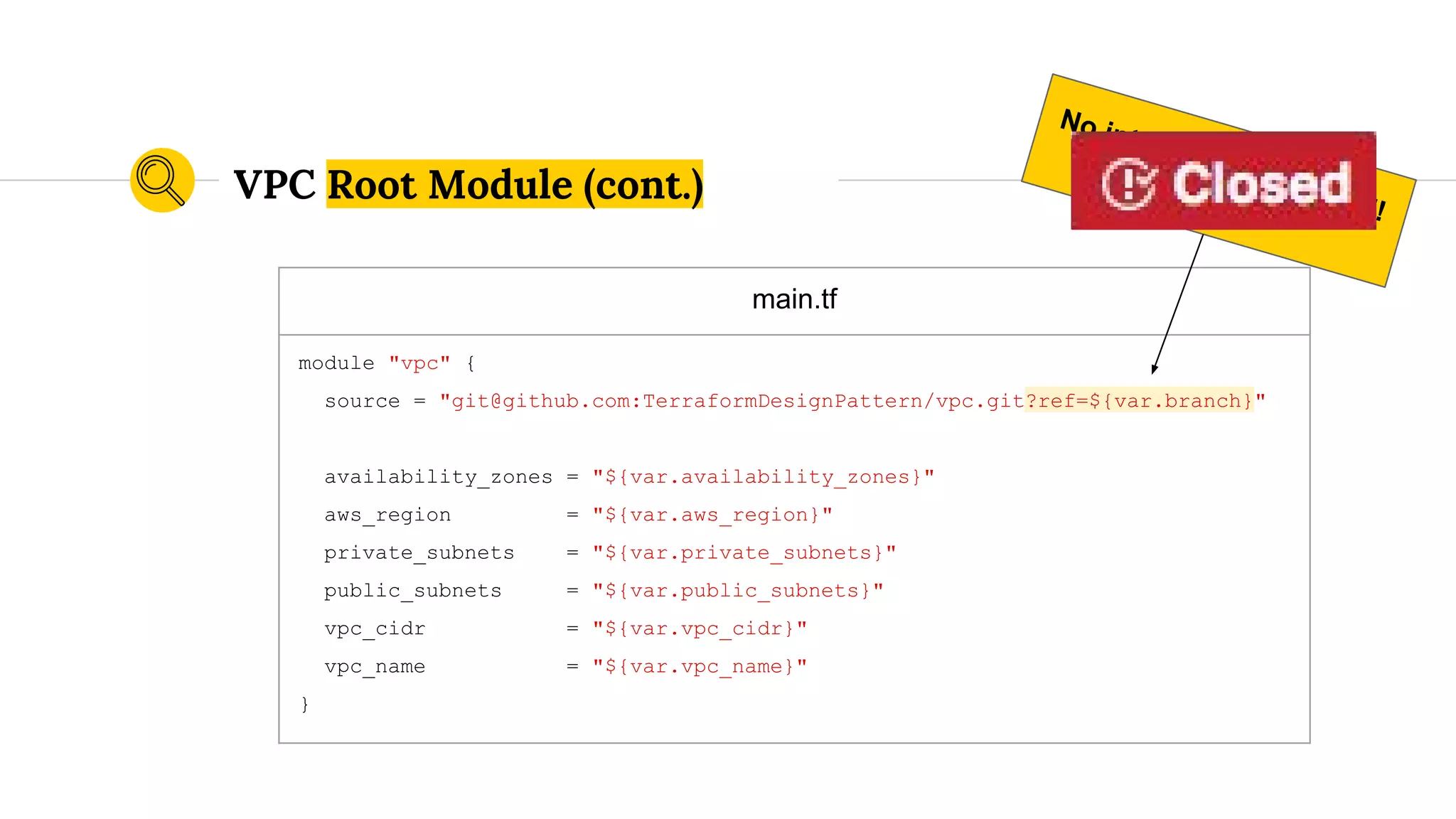

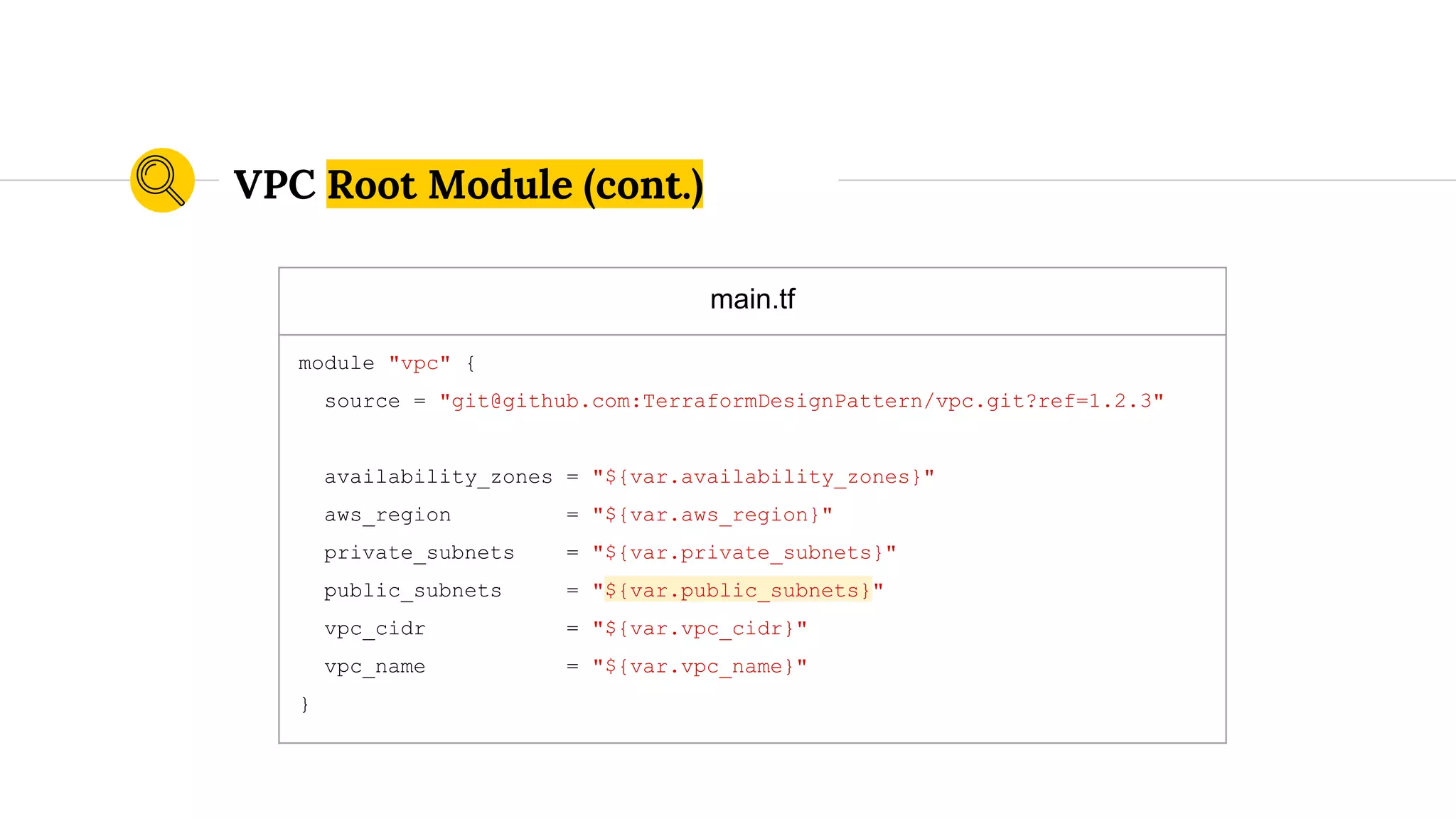

![variables.tf
...
variable "public_subnets" {
default = [
"172.19.101.0/24",
"172.19.102.0/24",
"172.19.103.0/24",
]
}
...
VPC Root Module (cont.)](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-84-2048.jpg)
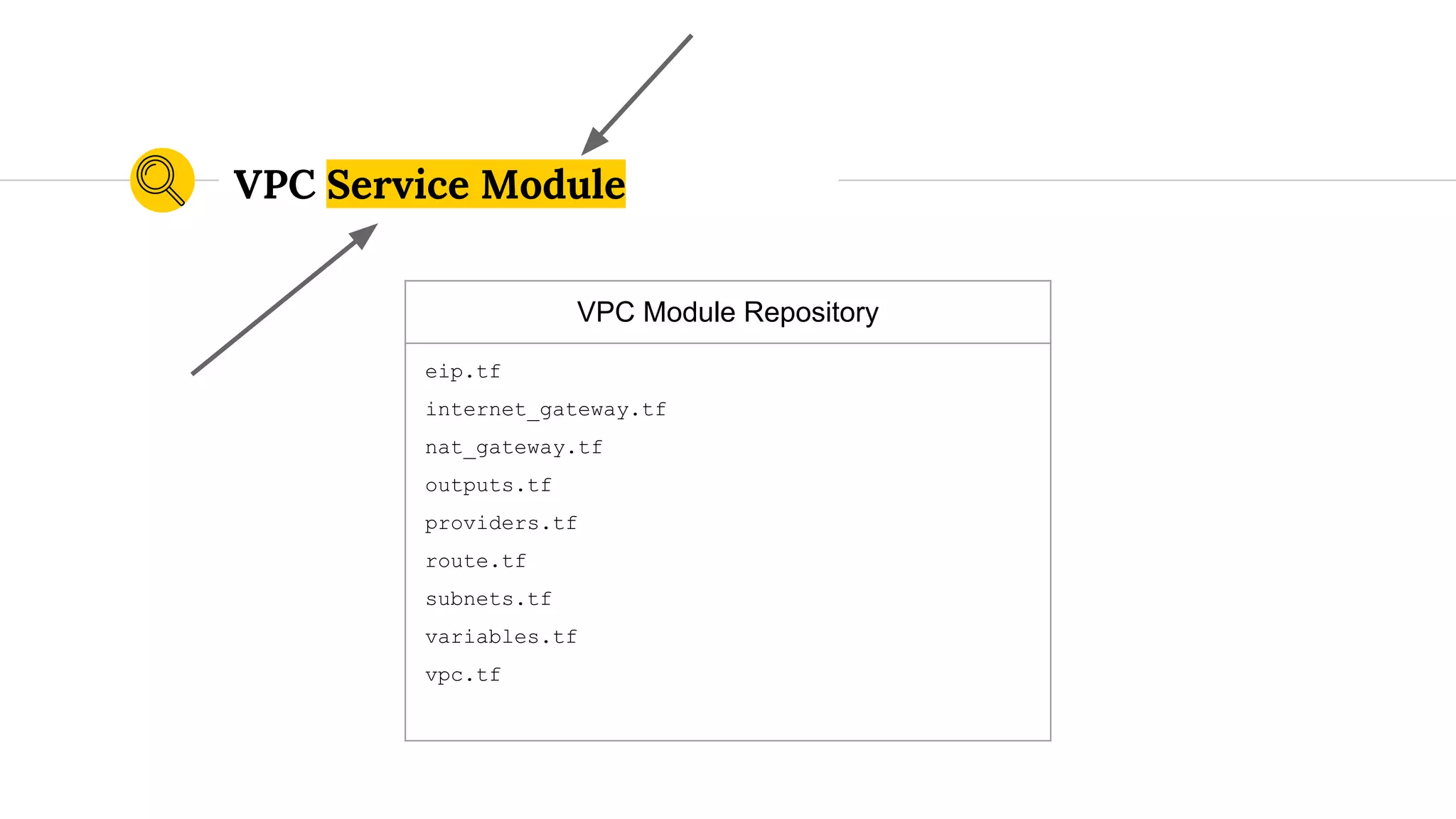
![outputs.tf
...
output "public_subnet_ids" {
value = ["${aws_subnet.public_subnet.*.id}"]
}
...
VPC Service Module Outputs](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-86-2048.jpg)
![outputs.tf
...
output "public_subnet_ids" {
value = ["${module.vpc.public_subnet_ids}"]
}
...
VPC Root Module Outputs](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-87-2048.jpg)

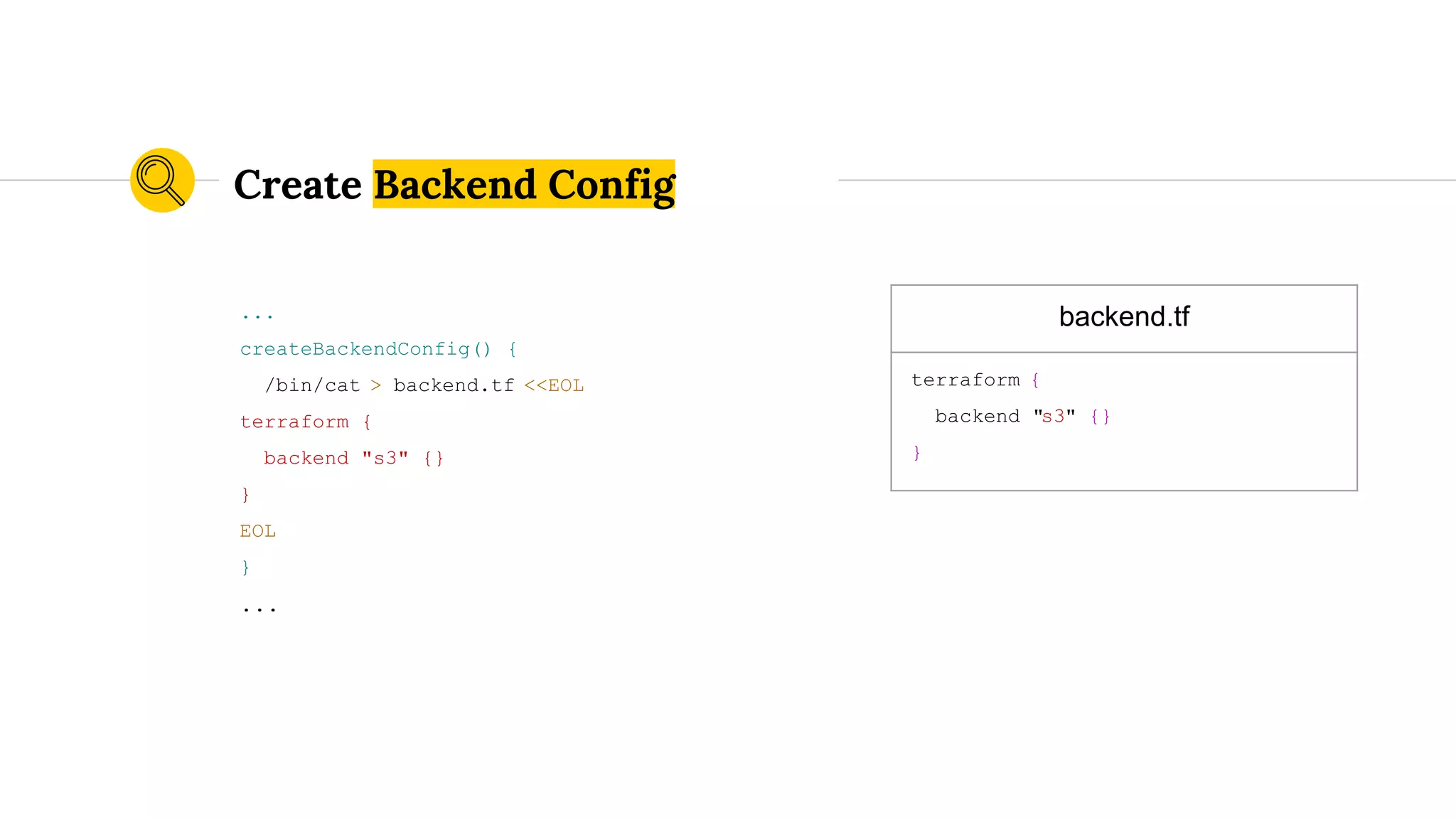
![s3.tf
resource "aws_s3_bucket_object" "outputs_object" {
bucket = "${var.aws_account}-terraform-state"
key =
"aws/${var.aws_region}/${var.vpc_name}/dummy_object_outputs"
source = "outputs.tf"
etag = "${md5(file("outputs.tf"))}"
}
resource "aws_s3_bucket_object" "variables_object" {
bucket = "${var.aws_account}-terraform-state"
key =
"aws/${var.aws_region}/${var.vpc_name}/dummy_object_variables"
source = "variables.tf"
etag = "${md5(file("variables.tf"))}"
}
Root Module State Seeding
outputs.tf
output "public_subnet_ids" {
value = ["${var.public_subnets}"]
}
...
variables.tf
variable "public_subnets" {
default = [
"172.19.101.0/24",
"172.19.102.0/24",
"172.19.103.0/24",
]
}
...](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-90-2048.jpg)
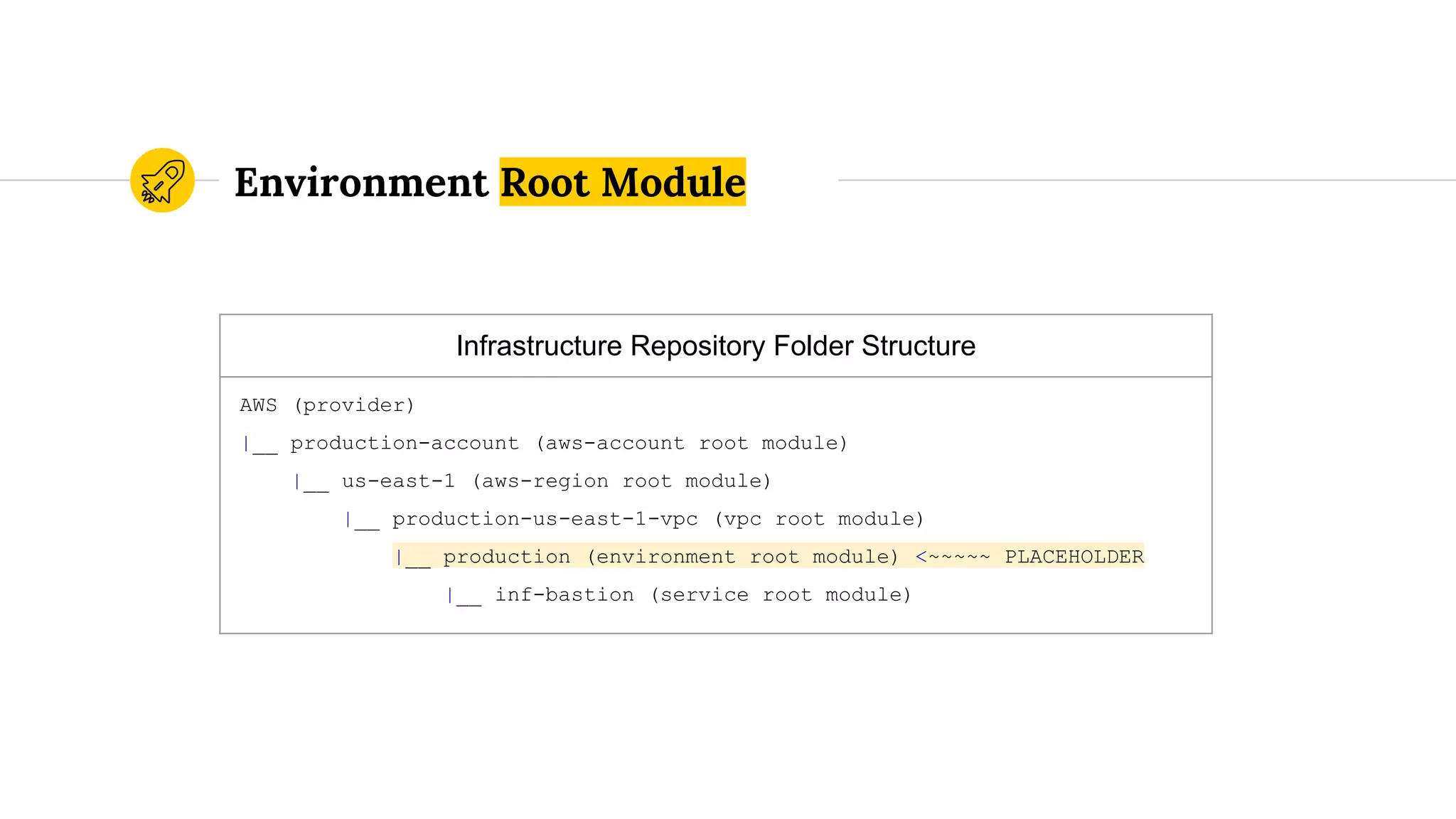

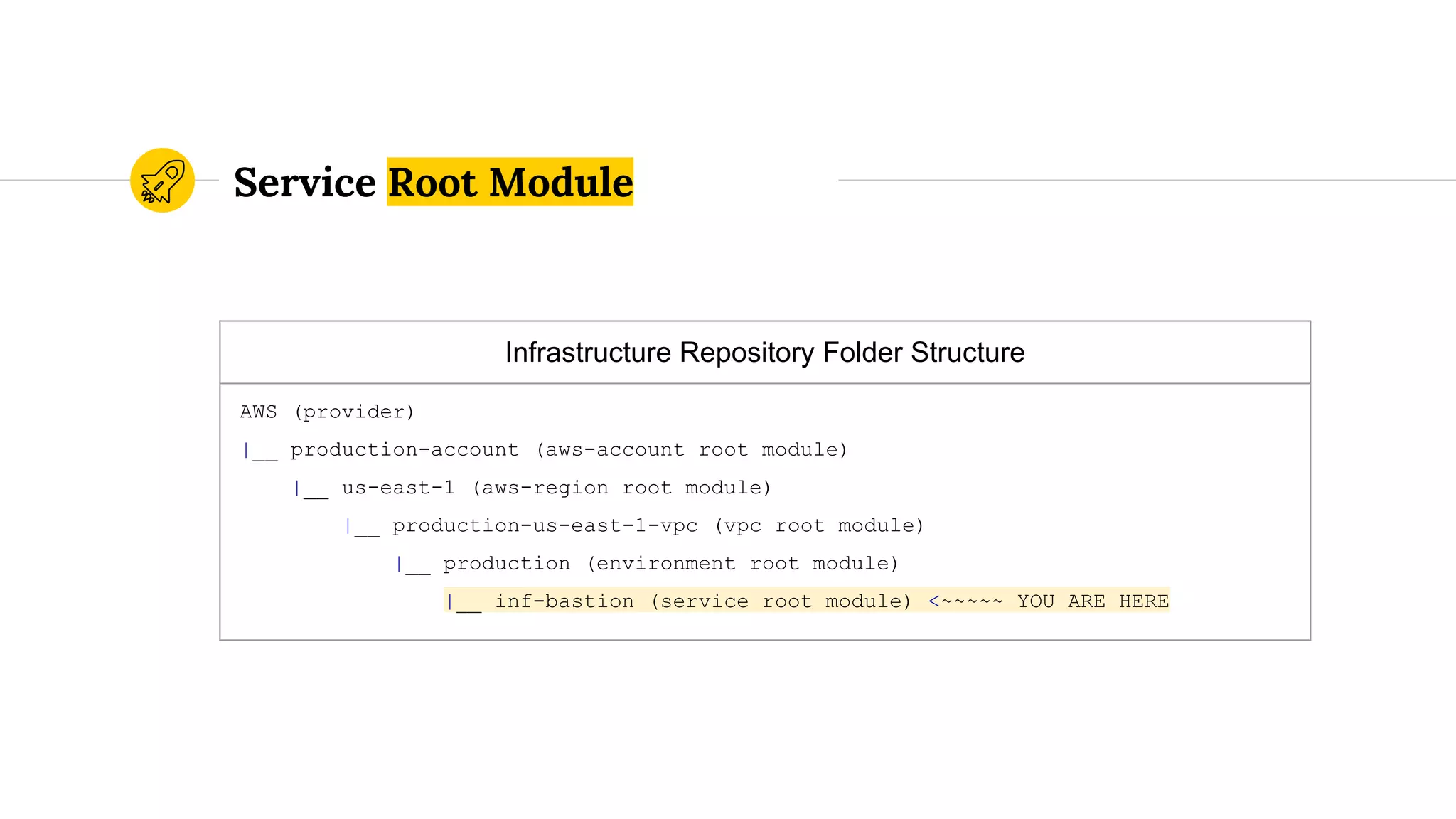

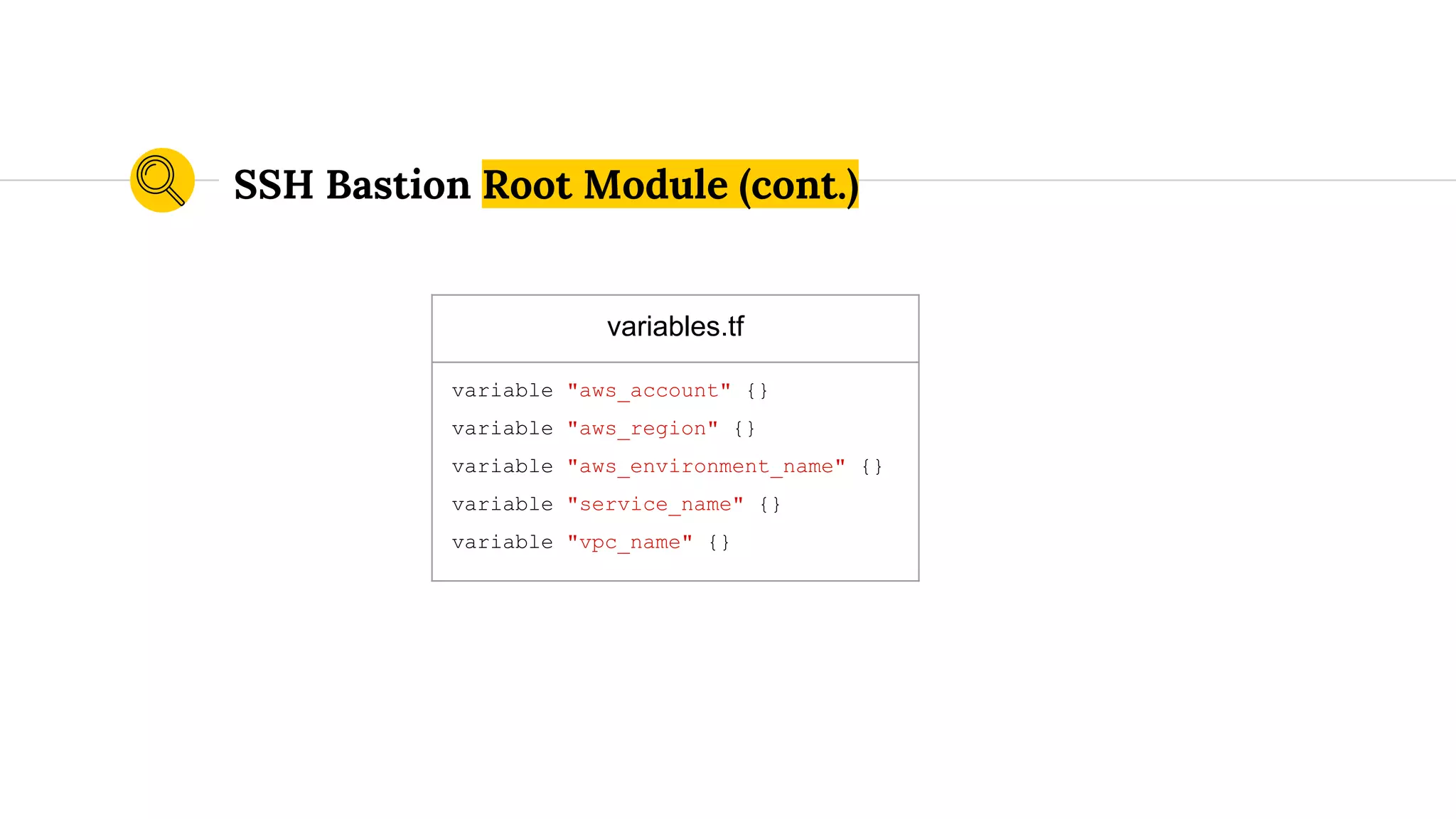
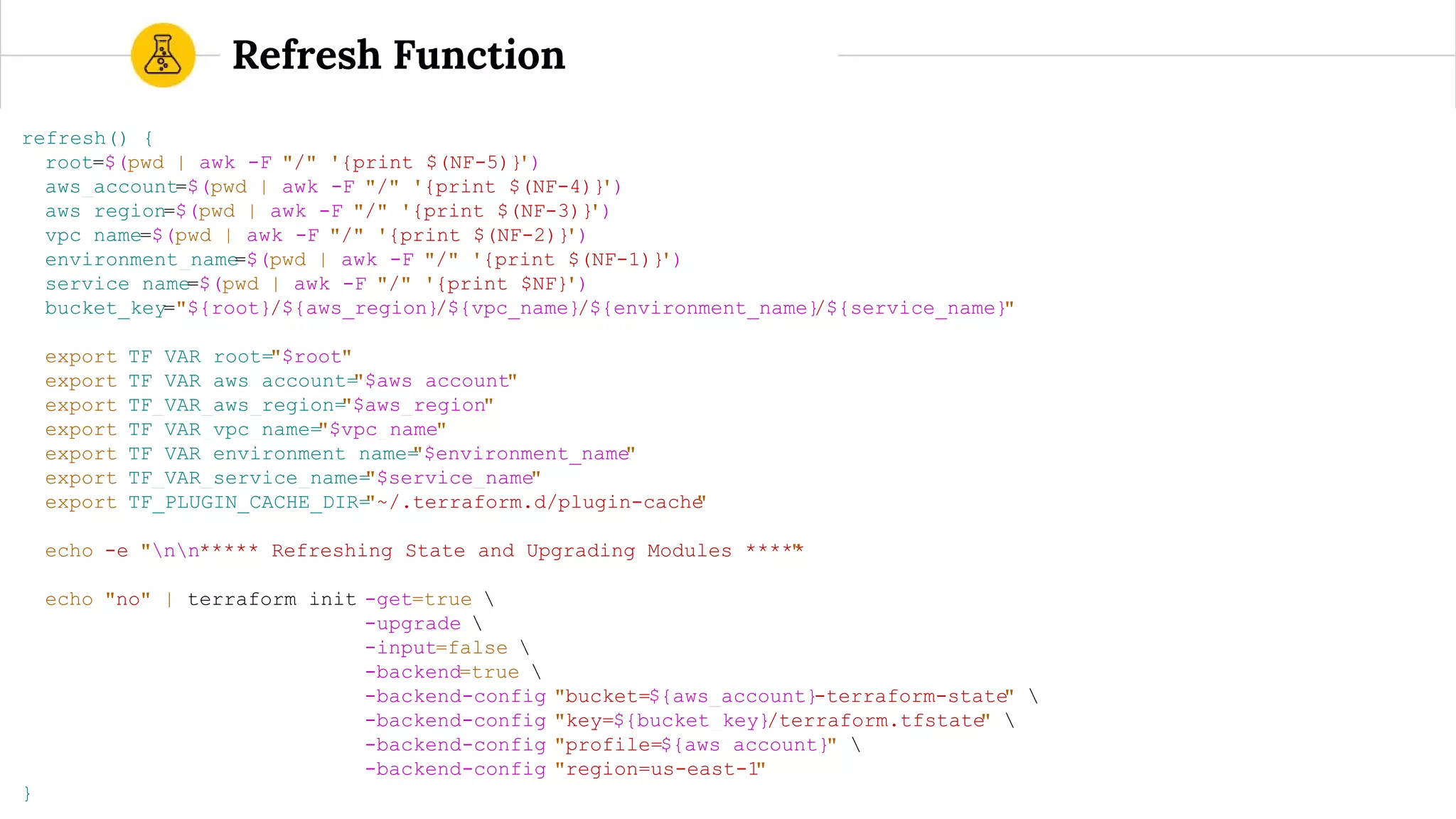
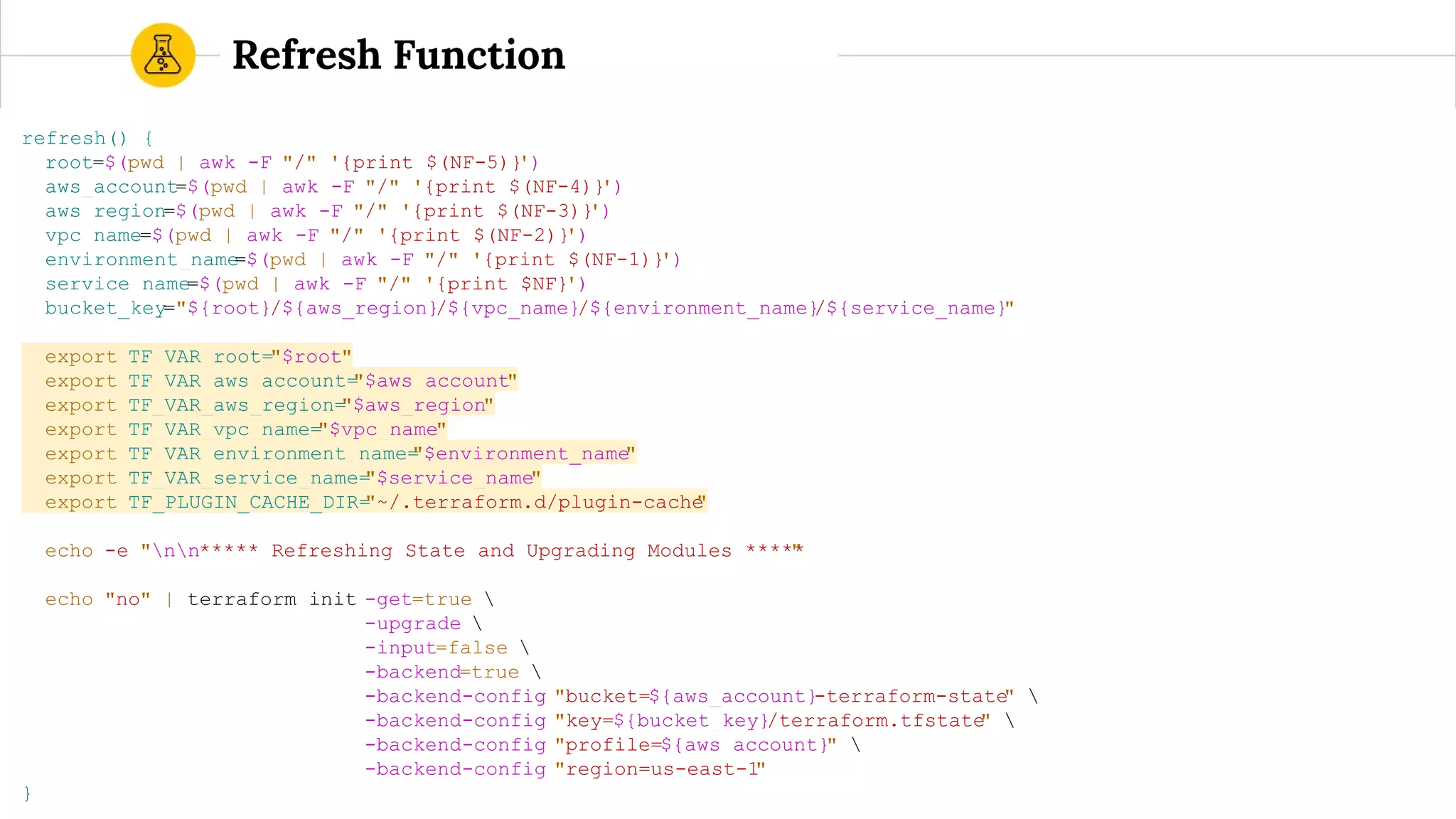
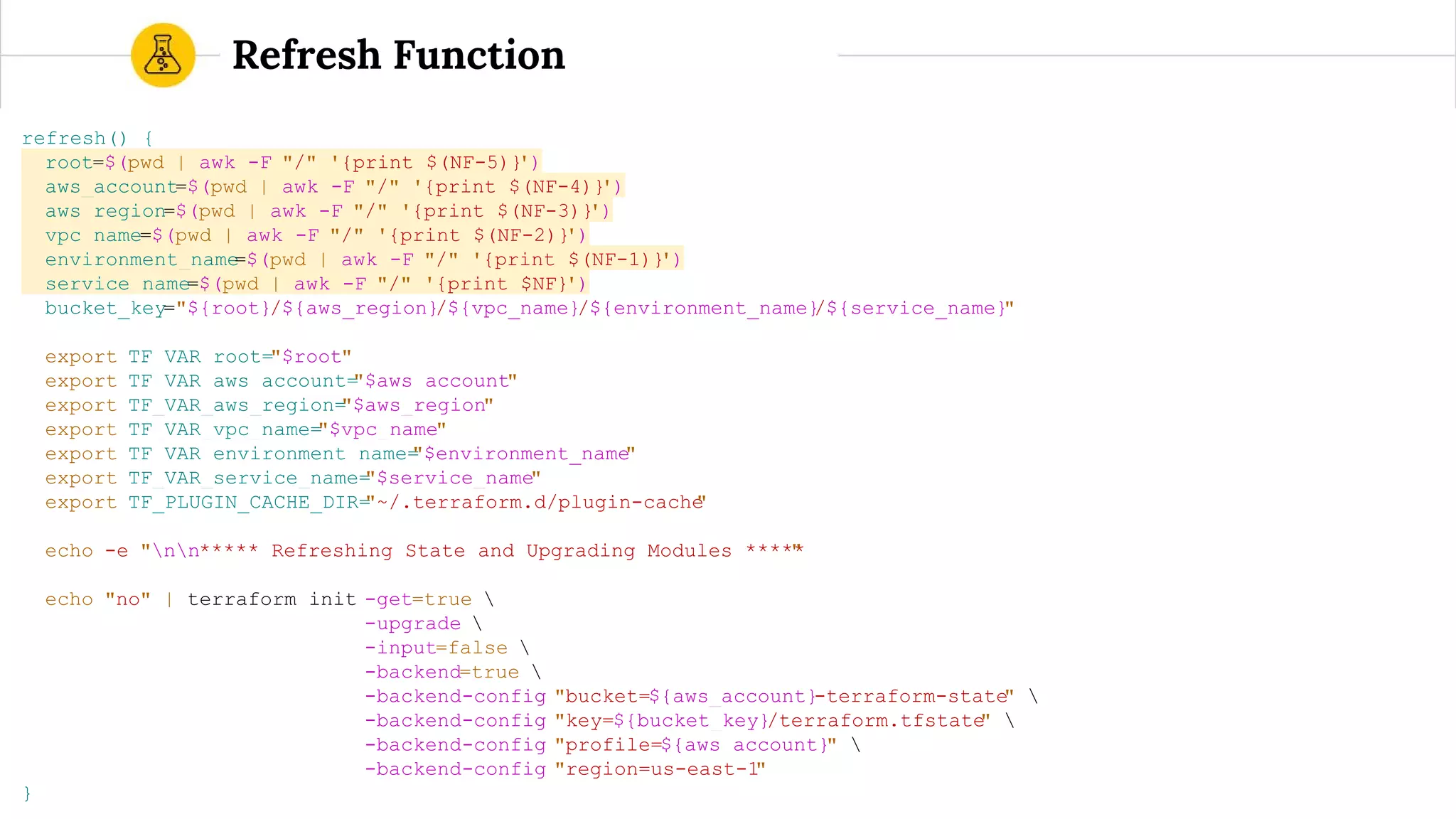
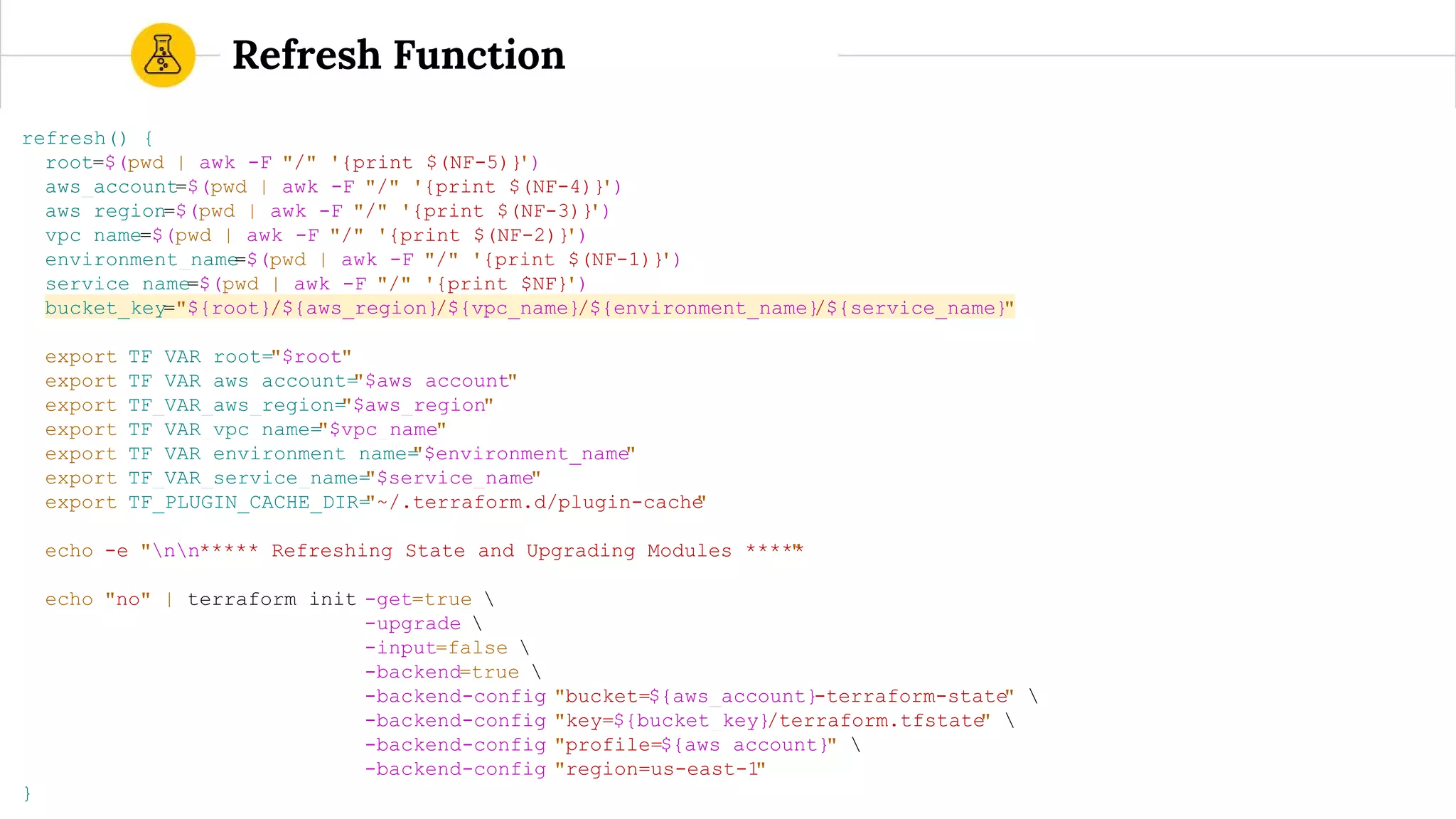
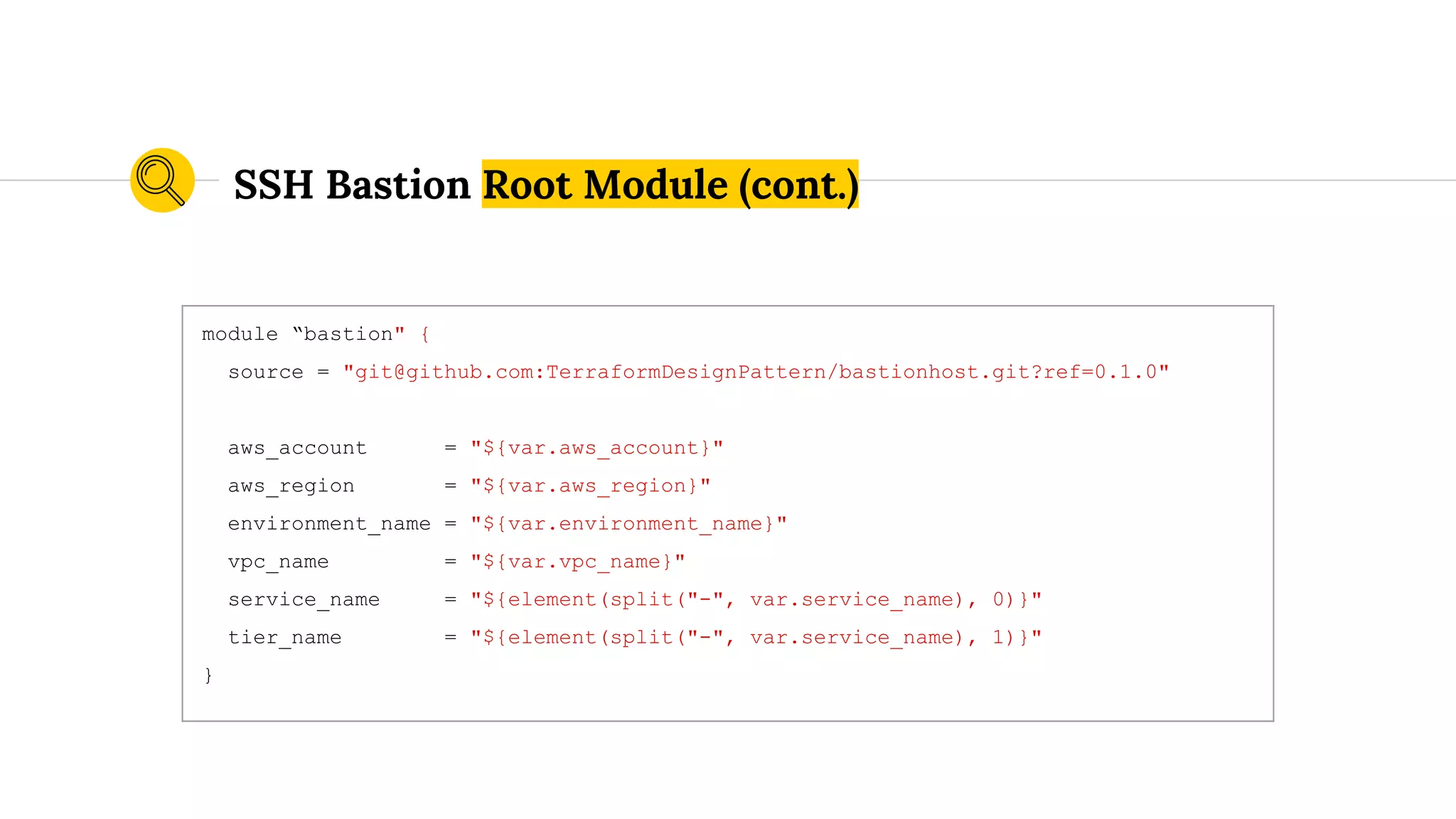
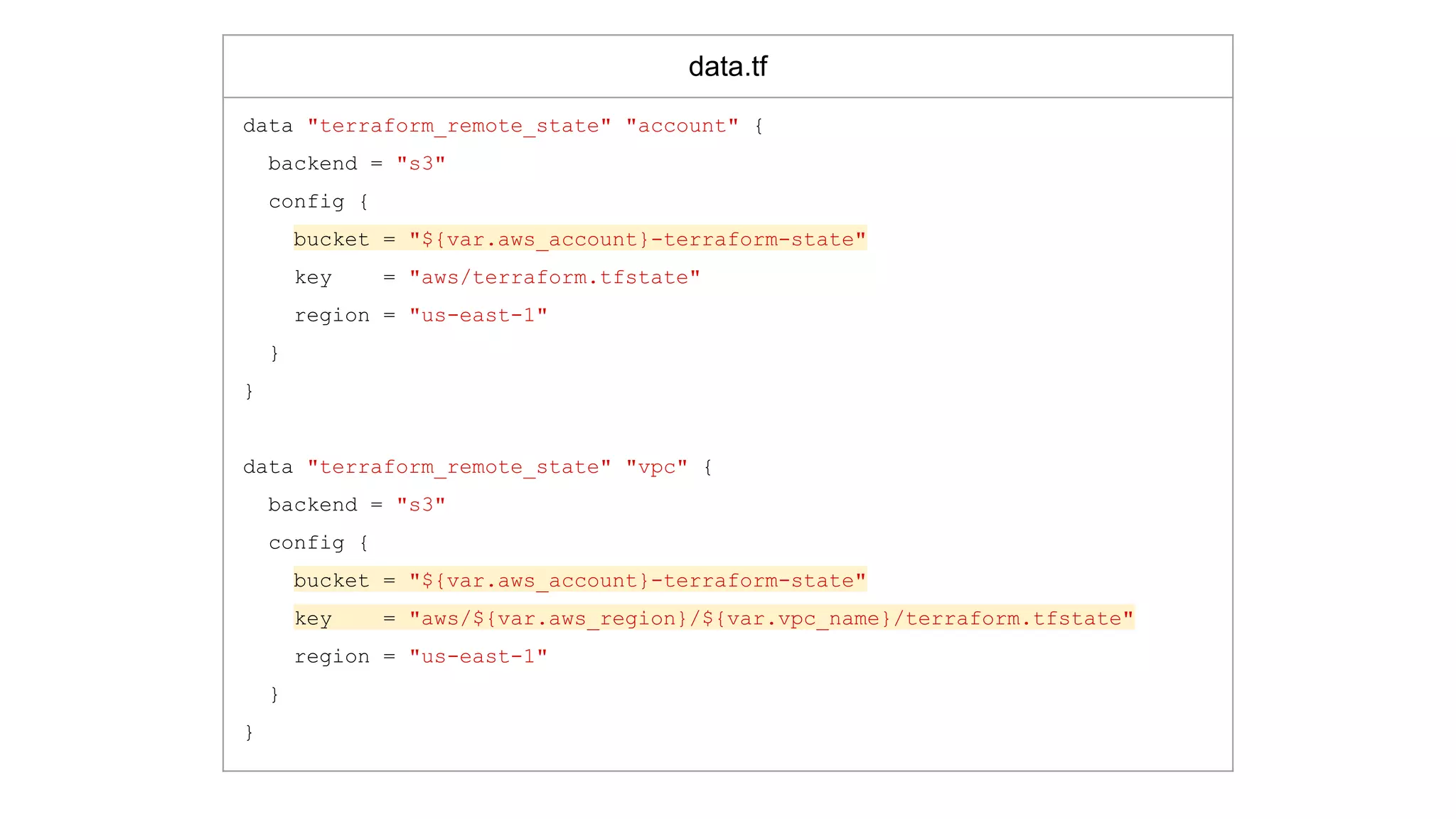
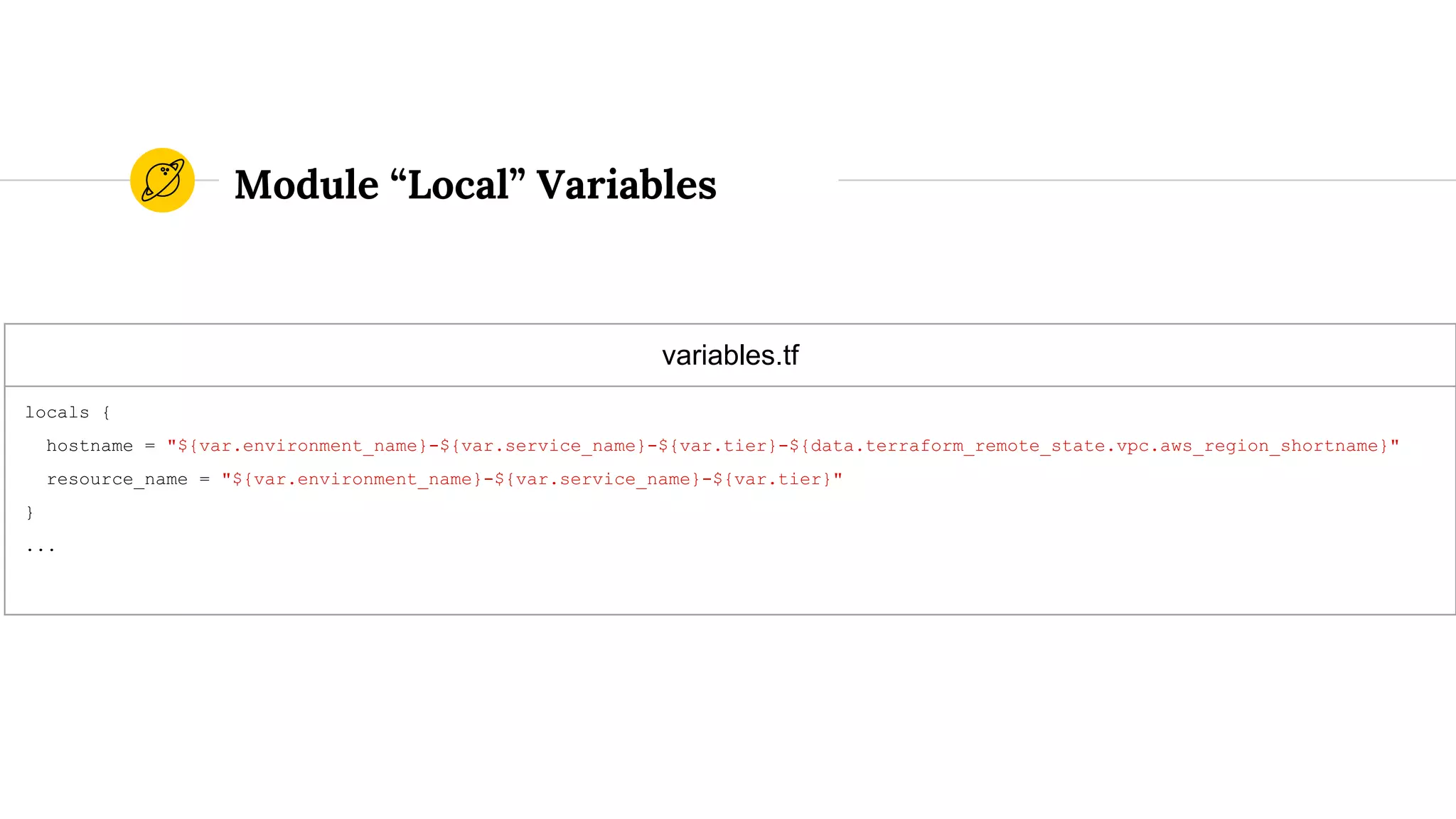
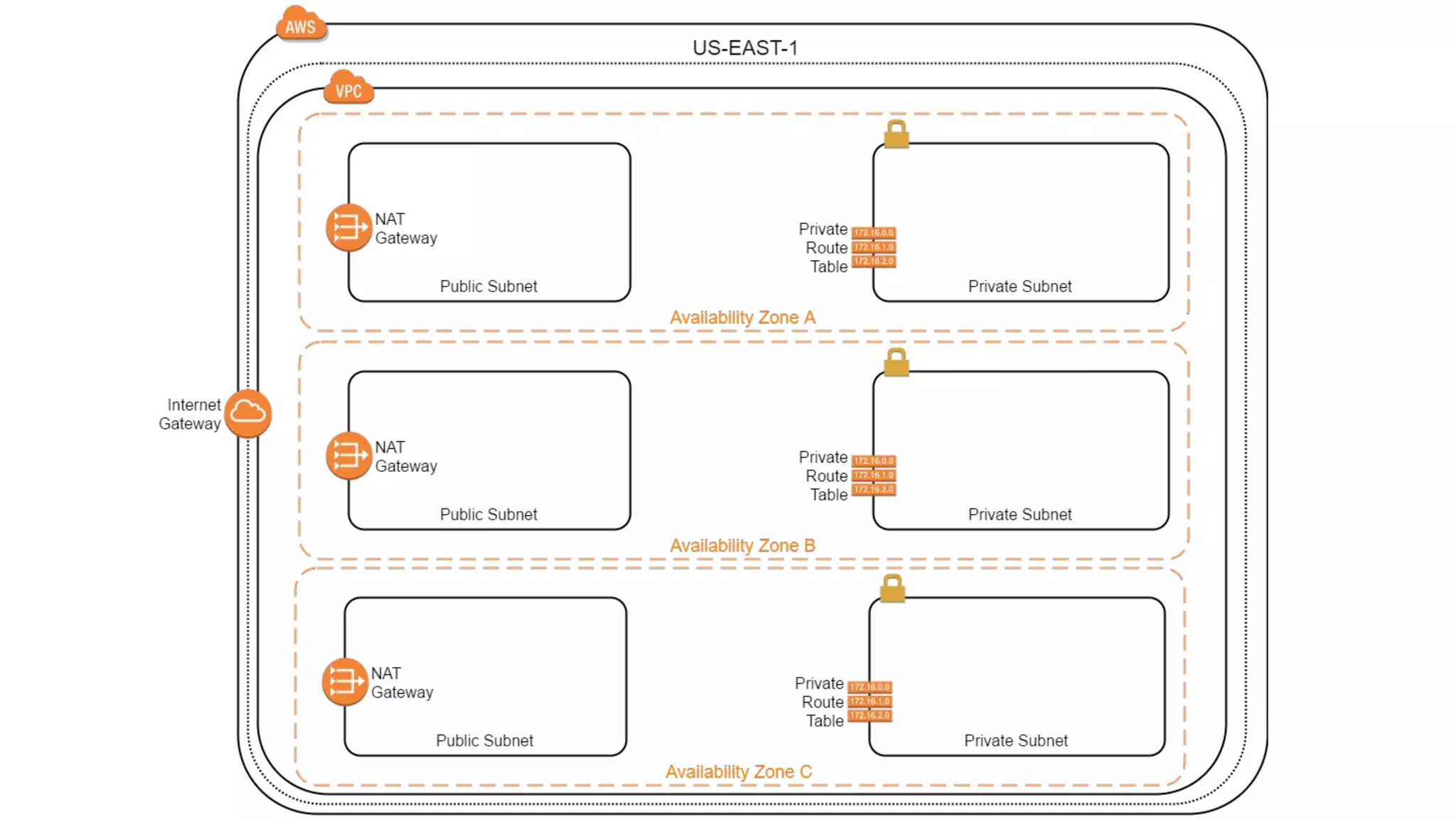
![route53.tf
resource "aws_route53_record" "route53_record" {
zone_id = "${data.terraform_remote_state.account.zone_id}"
name = "${local.hostname}.${data.terraform_remote_state.account.domain_name}"
type = "A"
ttl = "300"
records = ["${aws_instance.instance.public_ip}"]
}
...
security_groups.tf
resource "aws_security_group" "elb_security_group" {
name = "${local.resource_name}-elb-sg-${data.terraform_remote_state.vpc.aws_region_shortname}"
vpc_id = "${data.terraform_remote_state.vpc.vpc_id}"
...](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-105-2048.jpg)
![route53.tf
resource "aws_route53_record" "route53_record" {
zone_id = "${data.terraform_remote_state.account.zone_id}"
name = "${local.hostname}.${data.terraform_remote_state.account.domain_name}"
type = "A"
ttl = "300"
records = ["${aws_instance.instance.public_ip}"]
}
...
security_groups.tf
resource "aws_security_group" "elb_security_group" {
name = "${local.resource_name}-elb-sg-${data.terraform_remote_state.vpc.aws_region_shortname}"
vpc_id = "${data.terraform_remote_state.vpc.vpc_id}"
...](https://image.slidesharecdn.com/terraformatscale-171024153028/75/Terraform-at-Scale-All-Day-DevOps-2017-106-2048.jpg)