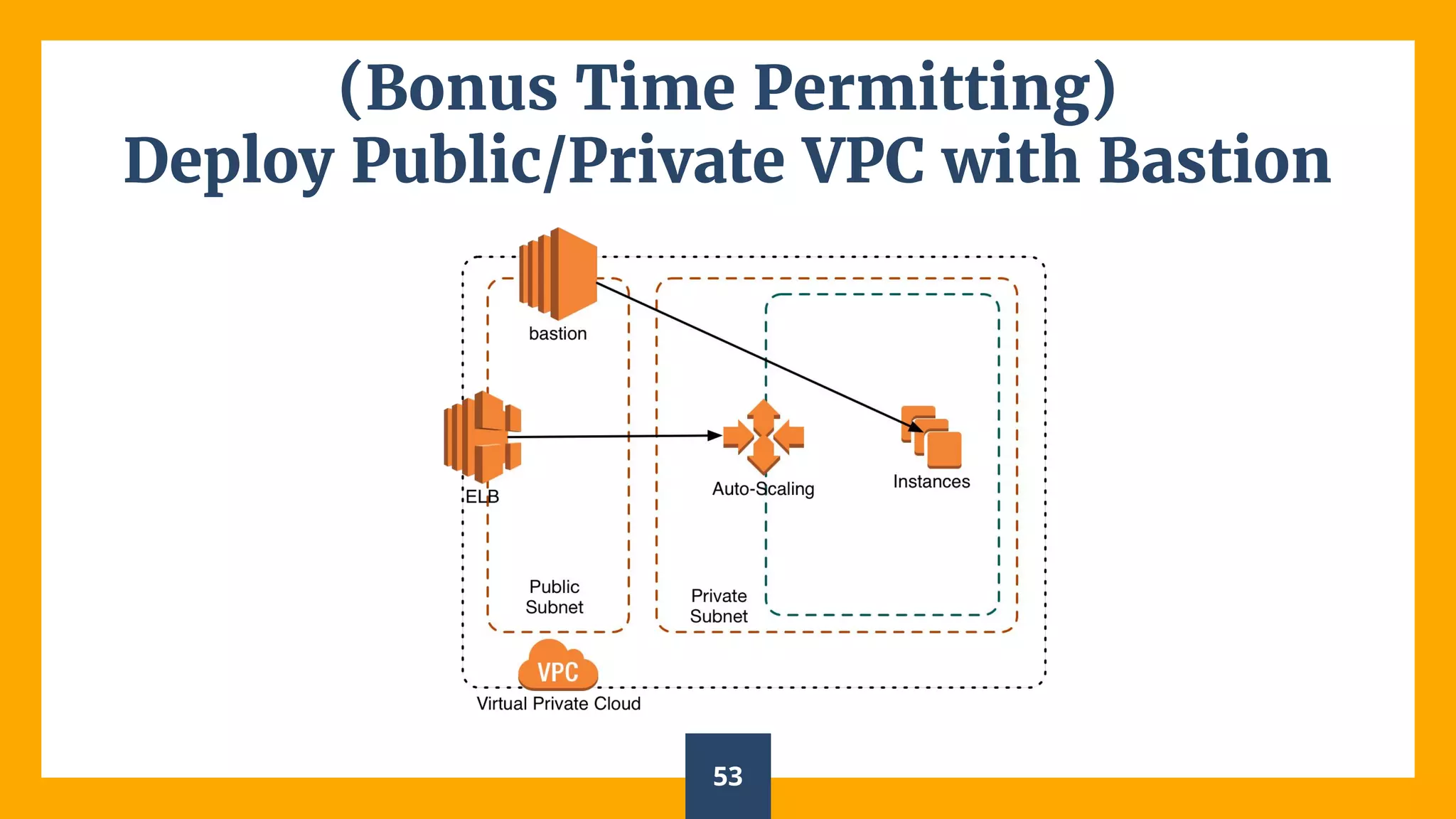
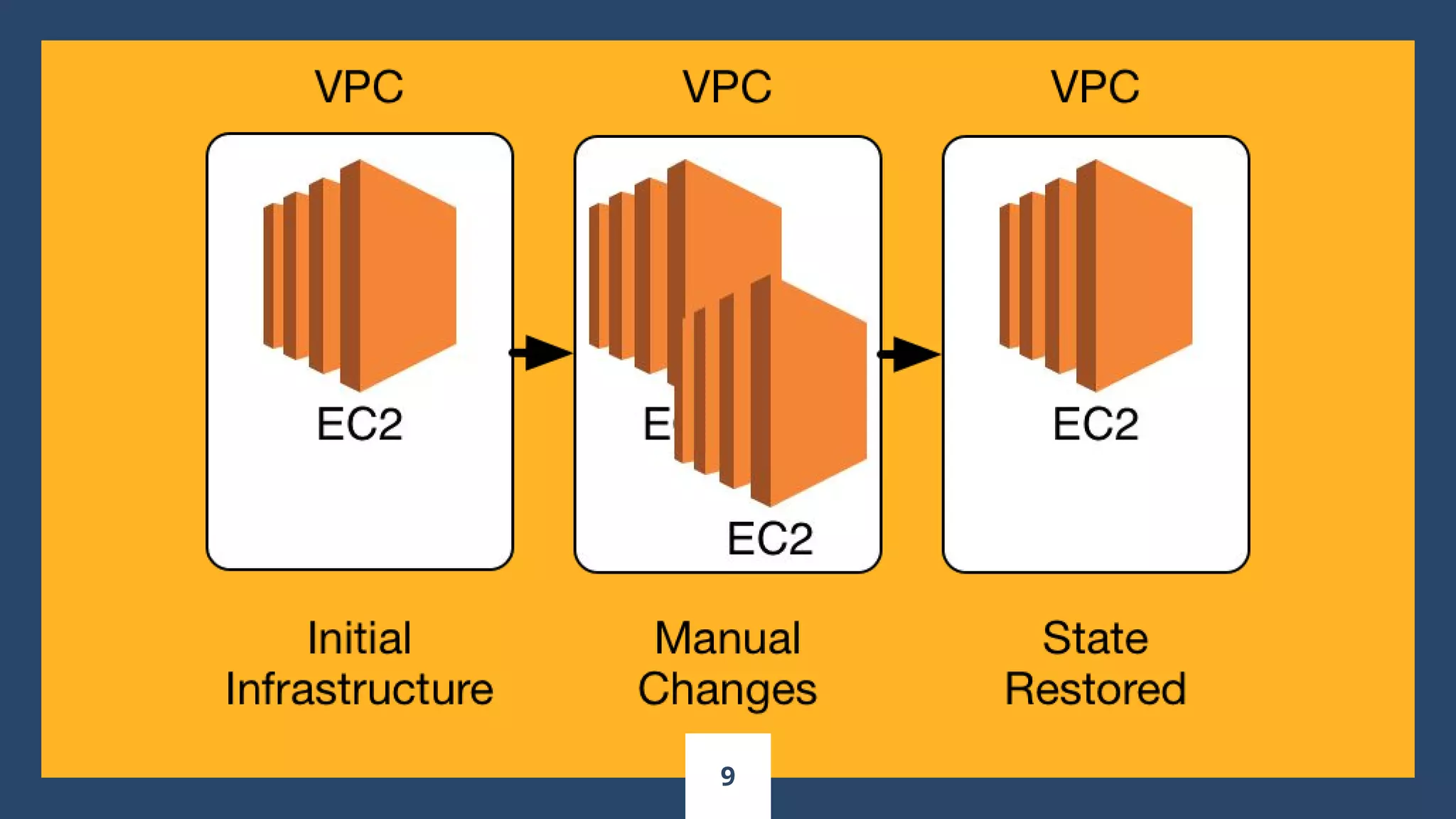
This document introduces infrastructure as code (IaC) using Terraform and provides examples of deploying infrastructure on AWS including:
- A single EC2 instance
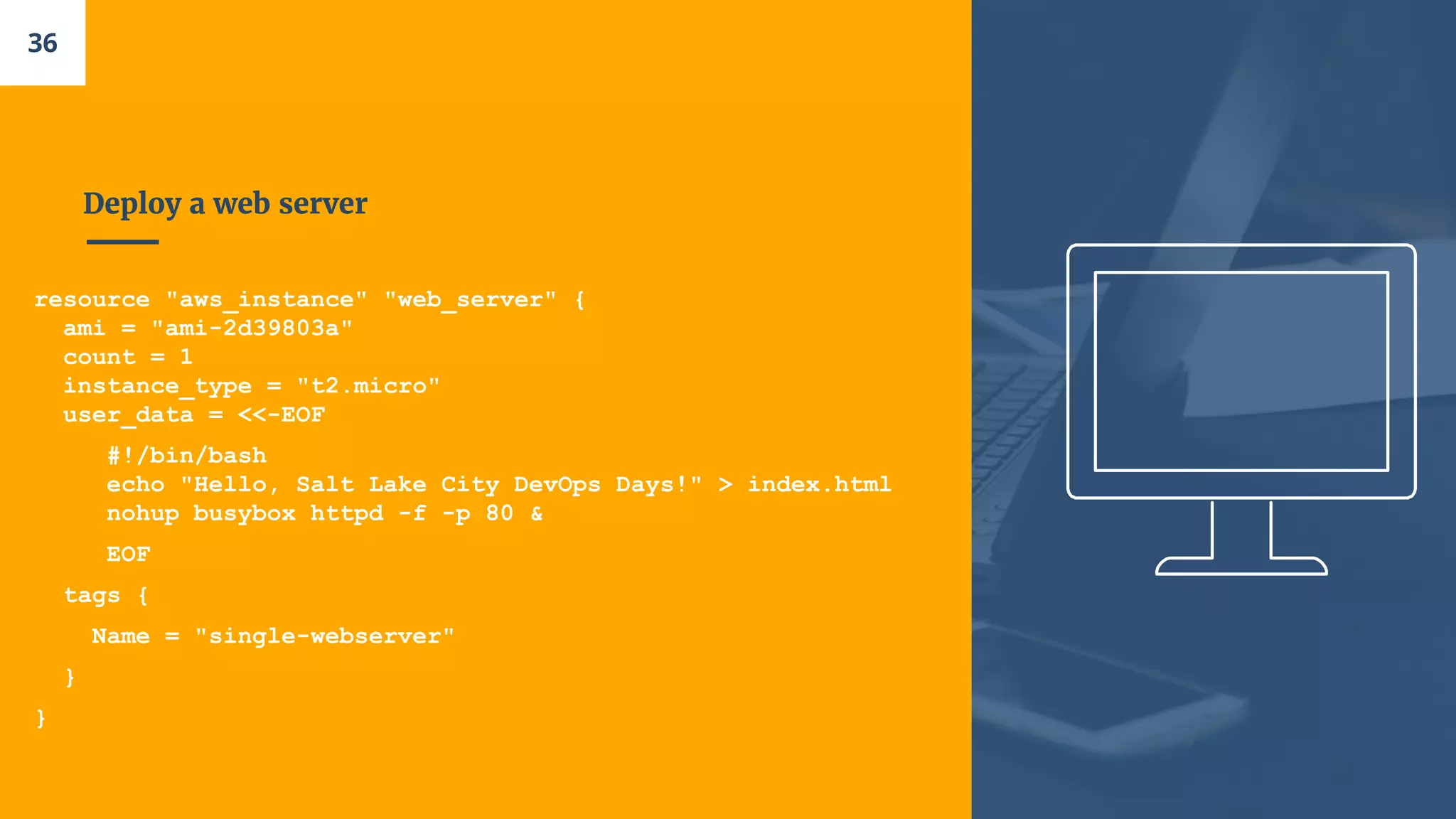
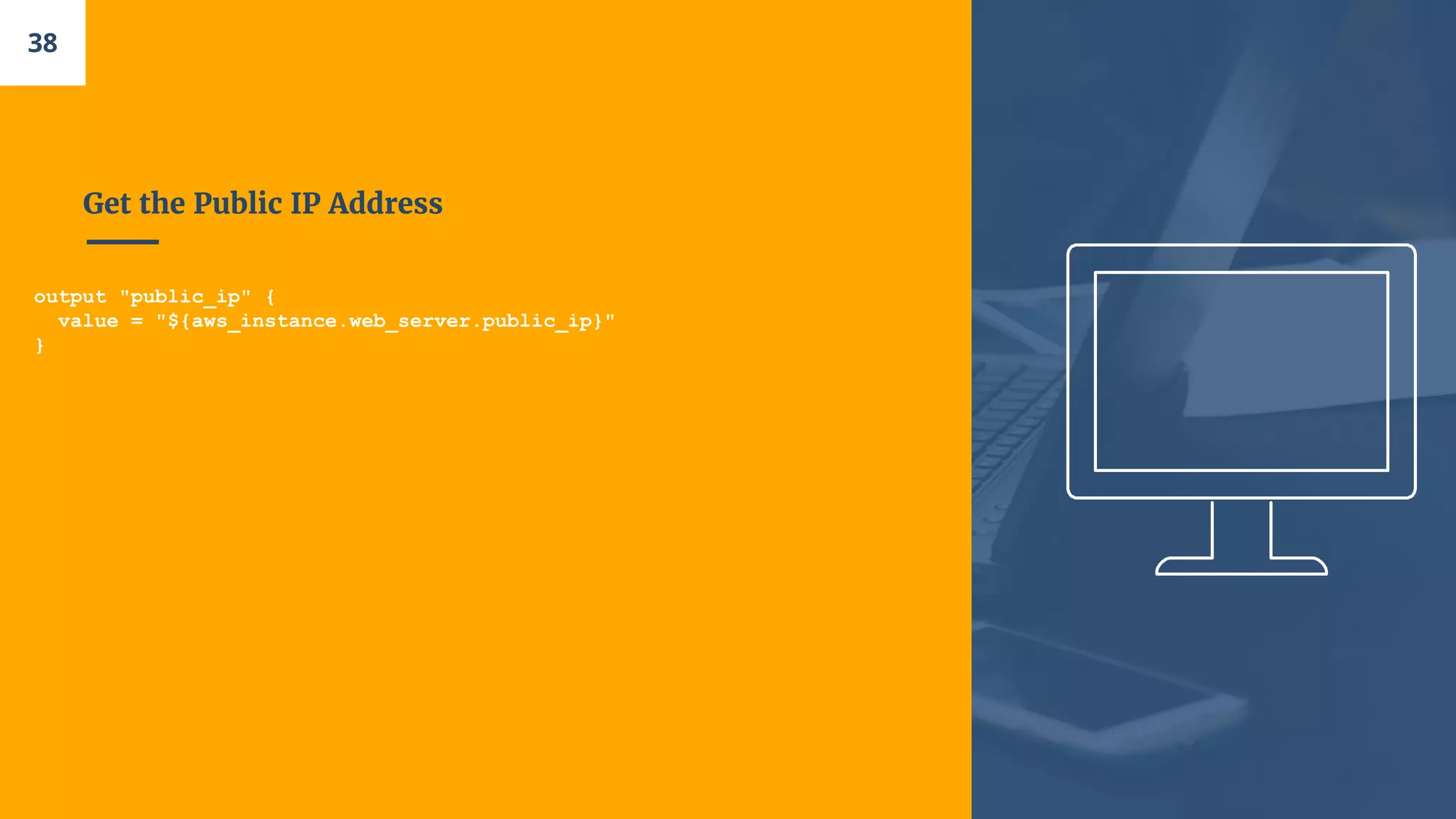
- A single web server
- A cluster of web servers using an Auto Scaling Group
- Adding a load balancer using an Elastic Load Balancer
It also discusses Terraform concepts and syntax like variables, resources, outputs, and interpolation. The target audience is people who deploy infrastructure on AWS or other clouds.




















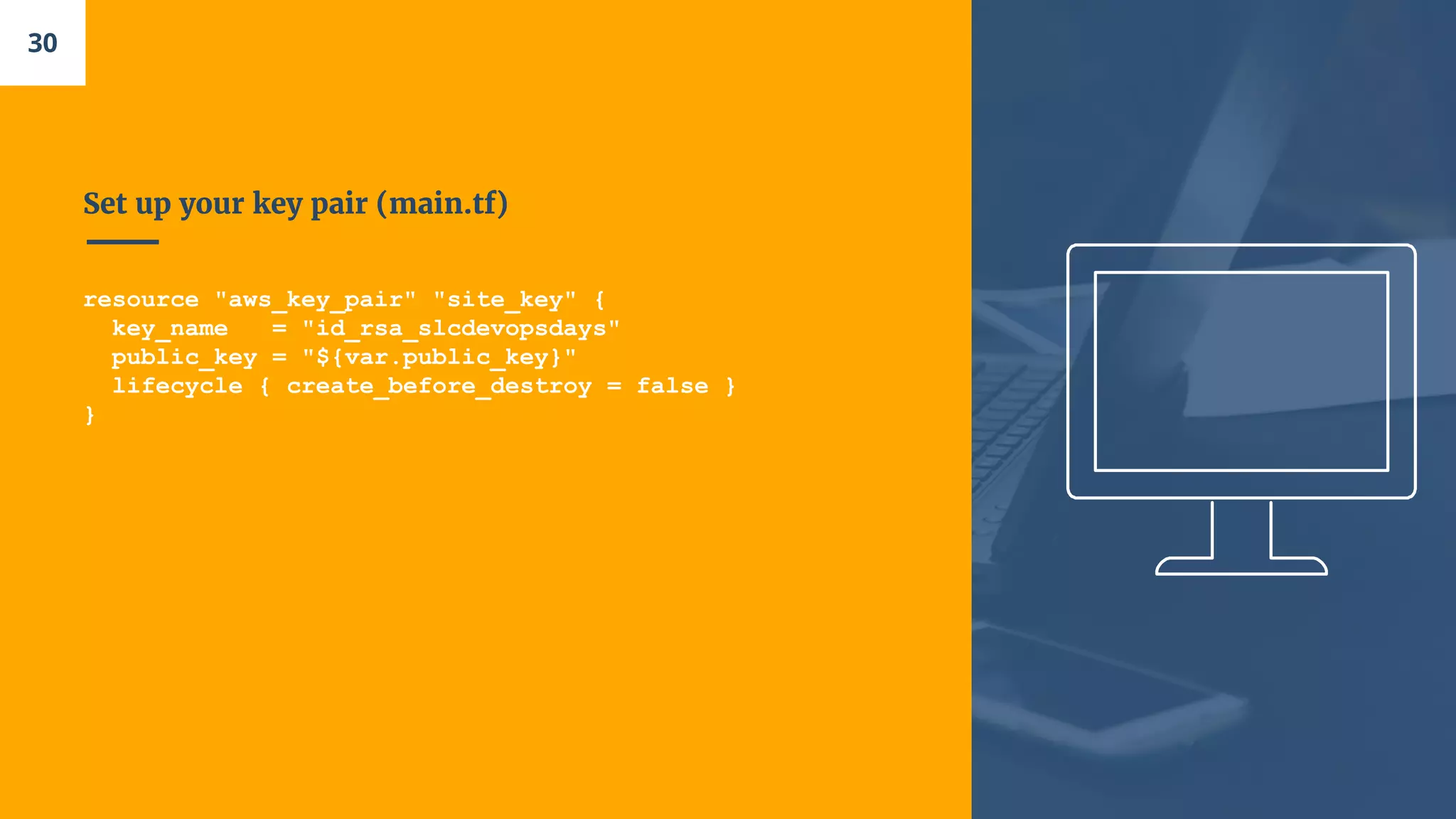
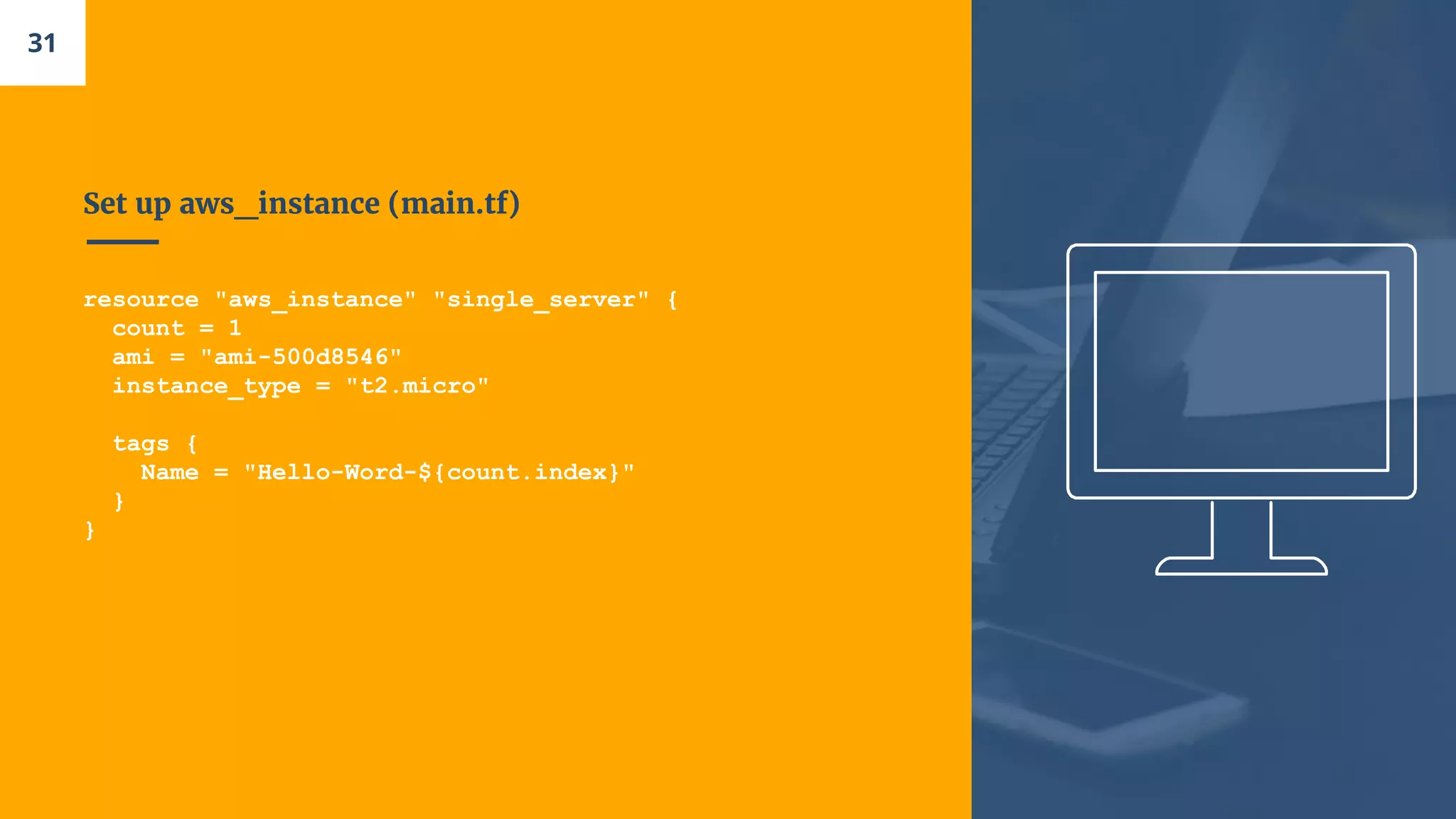
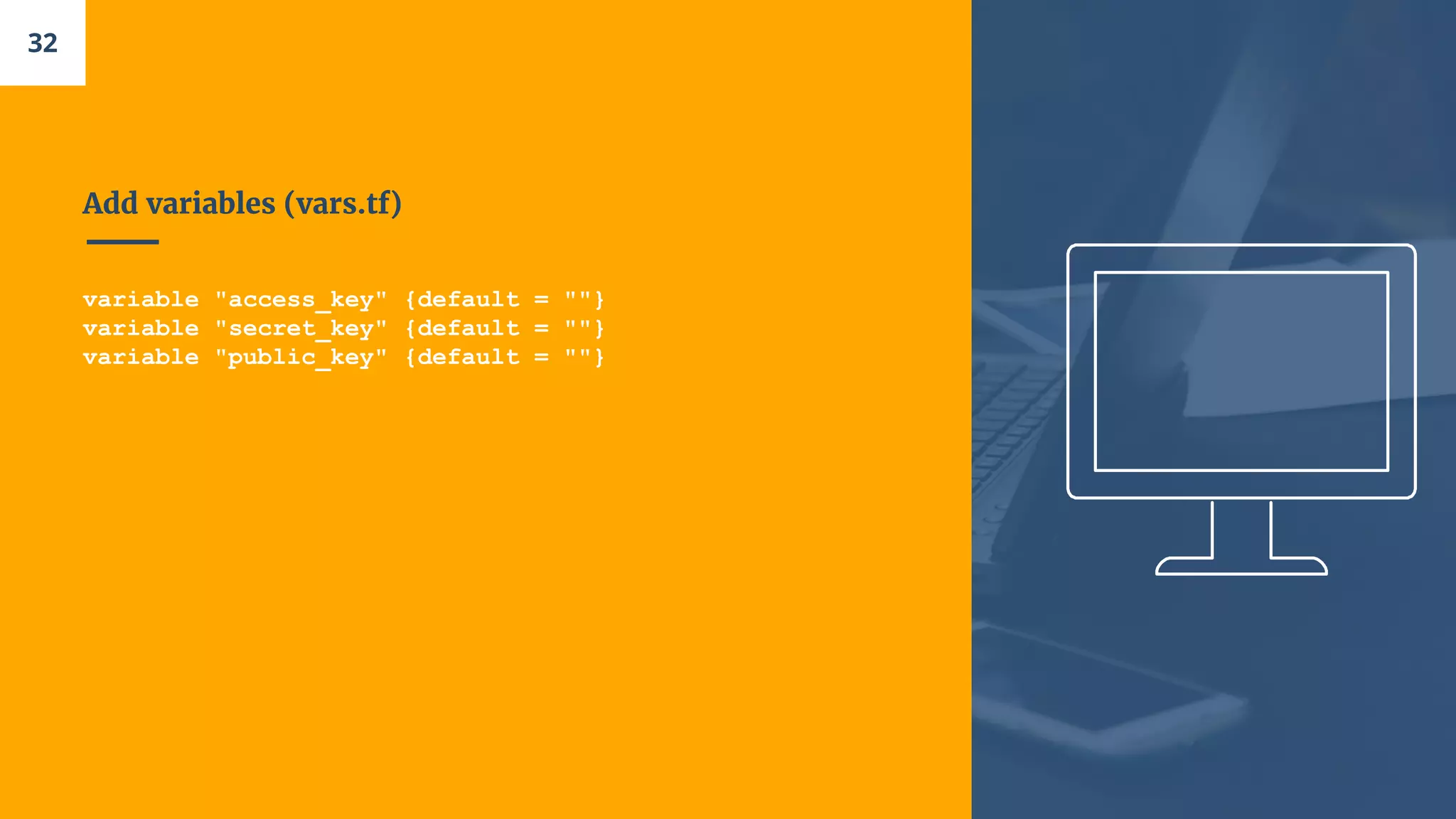


![Let’s open a Security Group
resource "aws_security_group" "web_server_sg" {
name = "web_server_sg"
ingress {
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
protocol = -1
from_port = 0
to_port = 0
cidr_blocks = ["0.0.0.0/0"]
}
}
37](https://image.slidesharecdn.com/terraformintroduction-170518142523/75/Terraform-introduction-37-2048.jpg)



![Create a Launch Configuration
resource "aws_launch_configuration" "web_server_lc" {
image_id = "ami-2d39803a"
instance_type = "t2.micro"
security_groups = ["${aws_security_group.web_server_sg.name}"]
user_data = <<-EOF
#!/bin/bash
echo "Hello, Salt Lake City DevOps Days!" > index.html
nohup busybox httpd -f -p 80 &
EOF
lifecycle {
create_before_destroy = true
}
}
42](https://image.slidesharecdn.com/terraformintroduction-170518142523/75/Terraform-introduction-42-2048.jpg)
![Add create_before_destry to the Security Group
resource "aws_security_group" "web_server_sg" {
name = "web_server_sg"
ingress {
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
protocol = -1
from_port = 0
to_port = 0
cidr_blocks = ["0.0.0.0/0"]
}
lifecycle {
create_before_destroy = true
}
}
43](https://image.slidesharecdn.com/terraformintroduction-170518142523/75/Terraform-introduction-43-2048.jpg)
![Create the Auto Scaling Group
resource "aws_autoscaling_group" "web_server_asg" {
launch_configuration = "${aws_launch_configuration.web_server_lc.id}"
availability_zones = ["${data.aws_availability_zones.all.names}"]
min_size = 2
max_size = 10
tag {
key = "Name"
value = "terraform-asg-example"
propagate_at_launch = true
}
}
data "aws_availability_zones" "all" {}
44](https://image.slidesharecdn.com/terraformintroduction-170518142523/75/Terraform-introduction-44-2048.jpg)



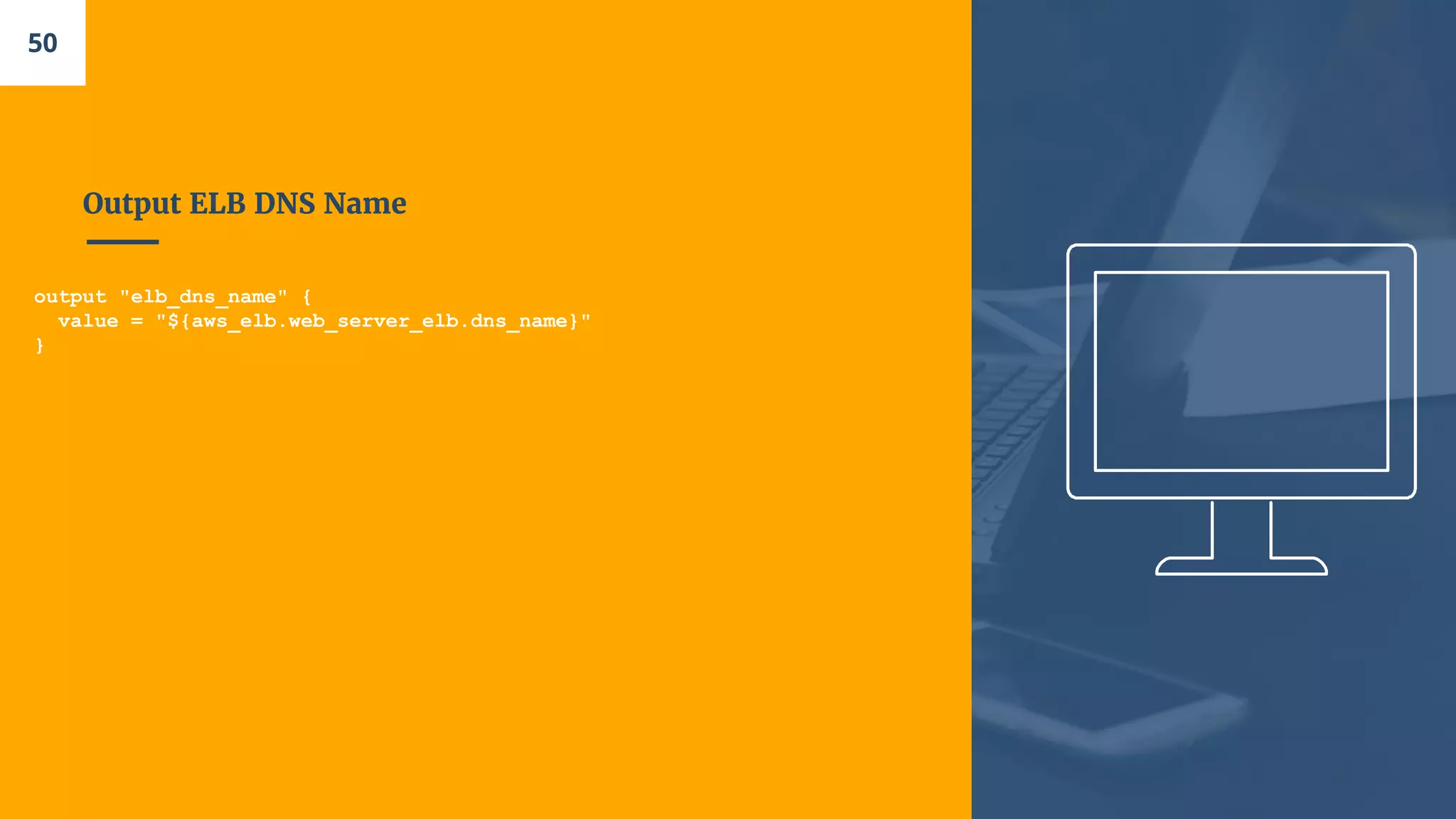
![Add an ELB
resource "aws_elb" "web_server_elb" {
name = "terraform-elb-example"
security_groups = ["${aws_security_group.web_server_sg.id}"]
availability_zones = ["${data.aws_availability_zones.all.names}"]
health_check {
healthy_threshold = 2
unhealthy_threshold = 2
timeout = 3
interval = 30
target = "HTTP:80/"
}
listener {
lb_port = 80
lb_protocol = "http"
instance_port = "80"
instance_protocol = "http"
}
}
48](https://image.slidesharecdn.com/terraformintroduction-170518142523/75/Terraform-introduction-48-2048.jpg)
![Update ASG
resource "aws_autoscaling_group" "web_server_asg" {
launch_configuration = "${aws_launch_configuration.web_server_lc.id}"
availability_zones = ["${data.aws_availability_zones.all.names}"]
load_balancers = ["${aws_elb.web_server_elb.name}"]
health_check_type = "ELB"
min_size = 2
max_size = 10
tag {
key = "Name"
value = "terraform-asg-example"
propagate_at_launch = true
}
}
49](https://image.slidesharecdn.com/terraformintroduction-170518142523/75/Terraform-introduction-49-2048.jpg)