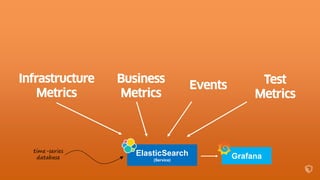
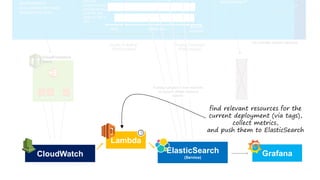
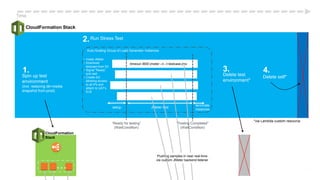
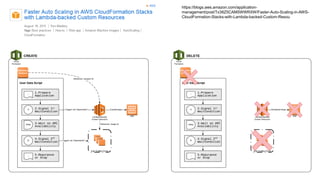
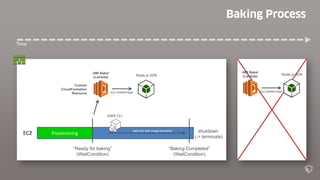
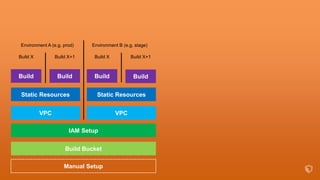
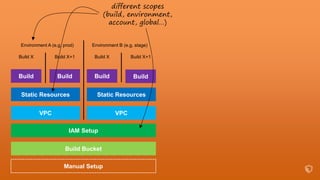
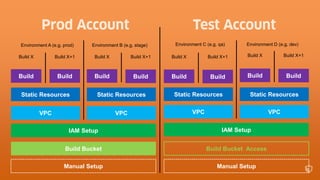
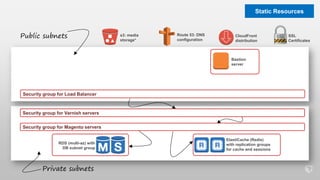
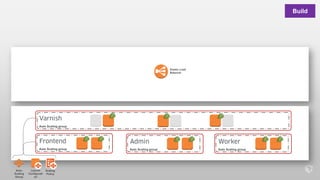
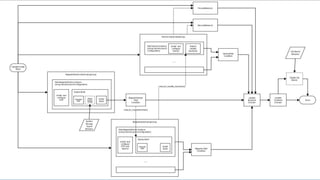
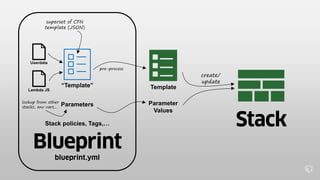
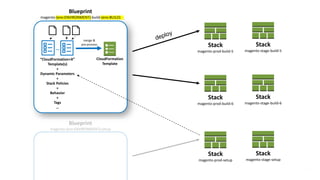
This document describes an immutable infrastructure approach using AWS Lambda and CloudFormation. Key points:
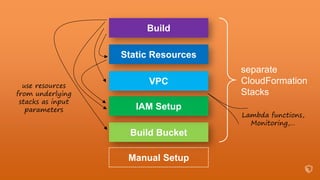
- Infrastructure is defined as code using CloudFormation templates for reproducibility and versioning.
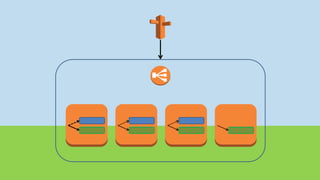
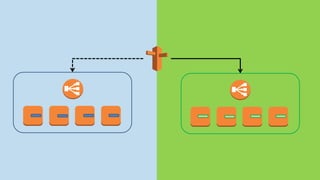
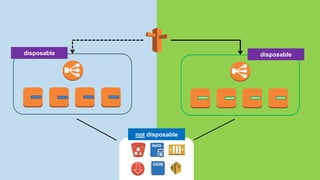
- Lambda functions are used to provision resources, configure settings, run tests, and clean up resources to enforce immutability.
- A pipeline handles building AMIs, deploying stacks, testing, updating DNS, and deleting old stacks in an automated and repeatable way.














![var r = require('cfn-response');
exports.handler = function (event, context) {
[…]
var res = {};
if (event.RequestType == 'Create') {
res.Password = randomPassword(20);
}
r.send(event, context, r.SUCCESS, res);
};](https://image.slidesharecdn.com/2016-03-17advancedawsmeetup-immutabledeployments-160318055040/85/Immutable-Deployments-with-AWS-CloudFormation-and-AWS-Lambda-29-320.jpg)
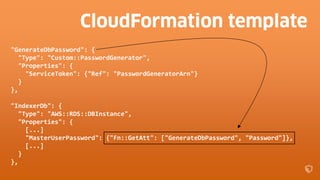
!["IndexerDb": {
"Type": "AWS::RDS::DBInstance",
"Properties": {
[...]
"MasterUserPassword": {"Fn::GetAtt": ["GenerateDbPassword", "Password"]},
[...]
}
},
"GenerateDbPassword": {
"Type": "Custom::PasswordGenerator",
"Properties": {
"ServiceToken": {"Ref": "PasswordGeneratorArn"}
}
},](https://image.slidesharecdn.com/2016-03-17advancedawsmeetup-immutabledeployments-160318055040/85/Immutable-Deployments-with-AWS-CloudFormation-and-AWS-Lambda-30-320.jpg)



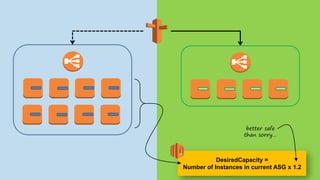
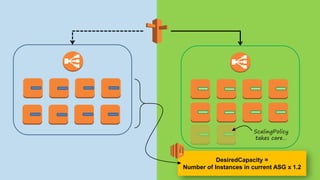
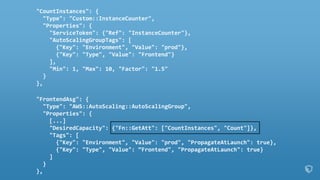
!["CountInstances": {
"Type": "Custom::InstanceCounter",
"Properties": {
"ServiceToken": {"Ref": "InstanceCounter"},
"AutoScalingGroupTags": [
{"Key": "Environment", "Value": "prod"},
{"Key": "Type", "Value": "Frontend"}
],
"Min": 1, "Max": 10, "Factor": "1.5"
}
},
"FrontendAsg": {
"Type": "AWS::AutoScaling::AutoScalingGroup",
"Properties": {
[...]
"DesiredCapacity": {"Fn::GetAtt": ["CountInstances", "Count"]},
"Tags": [
{"Key": "Environment", "Value": "prod", "PropagateAtLaunch": true},
{"Key": "Type", "Value": “Frontend", "PropagateAtLaunch": true}
]
}
},](https://image.slidesharecdn.com/2016-03-17advancedawsmeetup-immutabledeployments-160318055040/85/Immutable-Deployments-with-AWS-CloudFormation-and-AWS-Lambda-37-320.jpg)
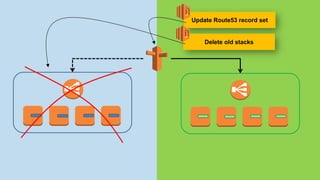
!["UpdateR53": {
"DependsOn": [ "MagentoWaitCondition", "MagentoWorkerWaitCondition", "Elb"],
"Type": "Custom::Route53Update",
"Properties": {
"ServiceToken": {"Ref": "R53Updater"},
"Name": {"Fn::Join": ["", [ "www-", {"Ref": "EnvironmentName"} ]]},
"HostedZoneId": {"Ref": "HostedZoneId"},
"AliasTargetDNSName": {"Fn::GetAtt": ["Elb", "DNSName"]},
"AliasTargetHostedZoneId": {"Fn::GetAtt": ["Elb", "CanonicalHostedZoneNameID"]},
"Comment": "Updated via CloudFormation/Lambda"
}
},
"DeleteStacks": {
"Condition": "DeleteOldStacks",
"DependsOn": ["UpdateR53"],
"Type": "Custom::StackDeleter",
"Properties": {
"ServiceToken": {"Ref": "StackDeleter"},
"TagFilter": { "Environment": {"Ref": "EnvironmentName"}, "Type": "Deployment"},
"ExceptStackName": {"Ref": "AWS::StackName"}
}
}](https://image.slidesharecdn.com/2016-03-17advancedawsmeetup-immutabledeployments-160318055040/85/Immutable-Deployments-with-AWS-CloudFormation-and-AWS-Lambda-40-320.jpg)




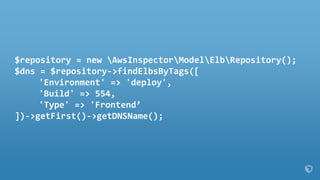
![$repository = new AwsInspectorModelElbRepository();
$dns = $repository->findElbsByTags([
'Environment' => 'deploy',
'Build' => 554,
'Type' => 'Frontend’
])->getFirst()->getDNSName();](https://image.slidesharecdn.com/2016-03-17advancedawsmeetup-immutabledeployments-160318055040/85/Immutable-Deployments-with-AWS-CloudFormation-and-AWS-Lambda-53-320.jpg)
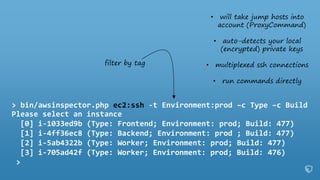
![> bin/awsinspector.php ec2:ssh -t Environment:prod –c Type –c Build
filter by tag
Please select an instance
[0] i-1033ed9b (Type: Frontend; Environment: prod; Build: 477)
[1] i-4ff36ec8 (Type: Backend; Environment: prod ; Build: 477)
[2] i-5ab4322b (Type: Worker; Environment: prod; Build: 477)
[3] i-705ad42f (Type: Worker; Environment: prod; Build: 476)
>
• will take jump hosts into
account (ProxyCommand)
• auto-detects your local
(encrypted) private keys
• multiplexed ssh connections
• run commands directly](https://image.slidesharecdn.com/2016-03-17advancedawsmeetup-immutabledeployments-160318055040/85/Immutable-Deployments-with-AWS-CloudFormation-and-AWS-Lambda-54-320.jpg)