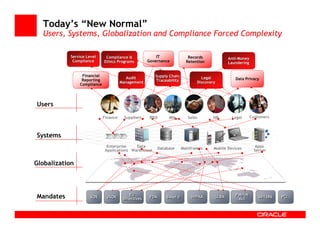
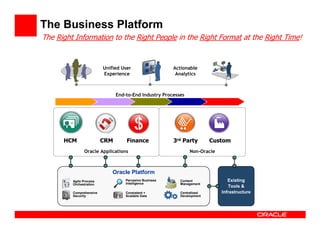
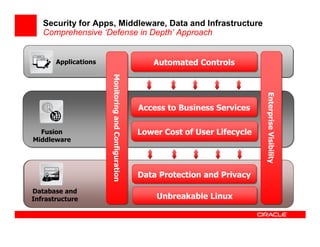
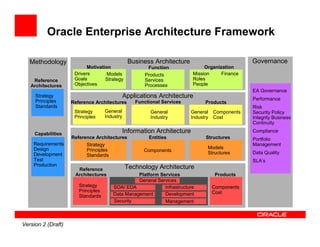
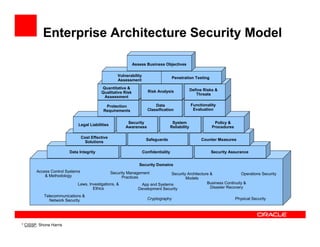
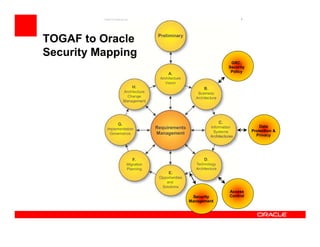
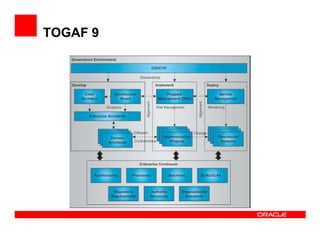
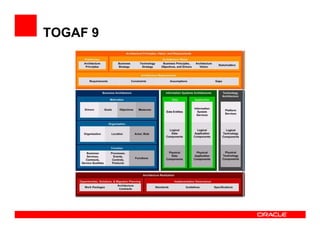
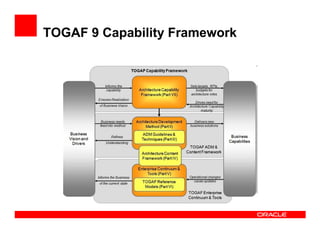
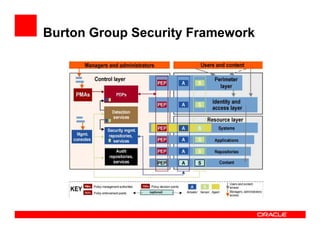
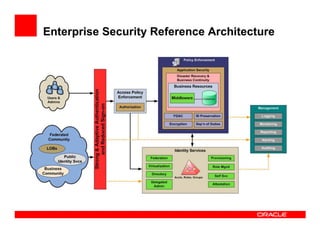
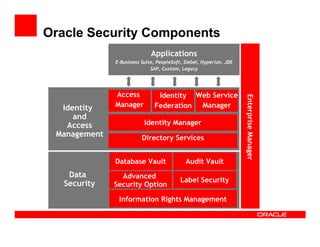
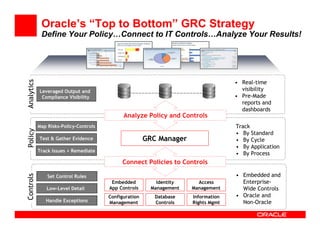
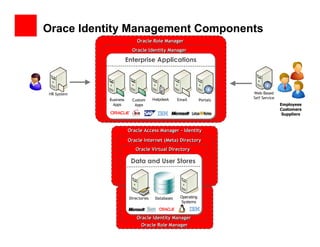
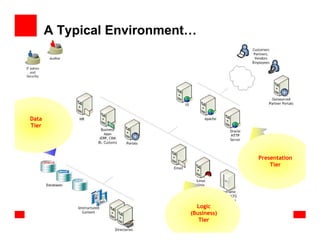
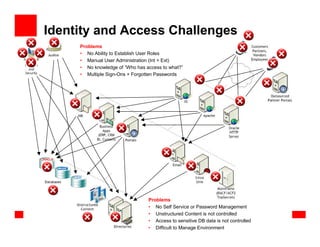
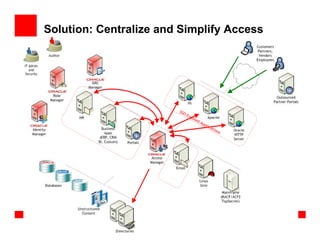
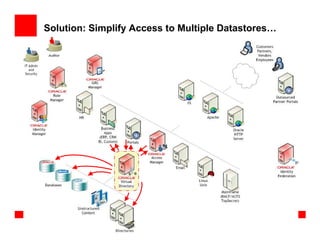
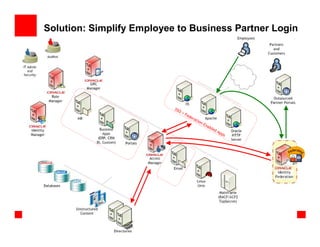
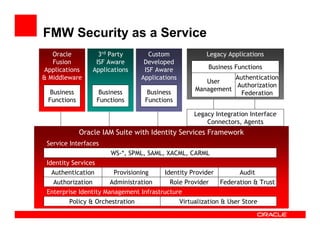
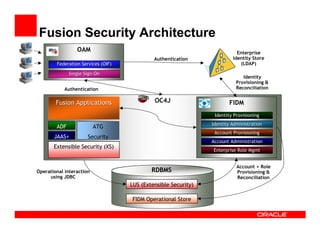
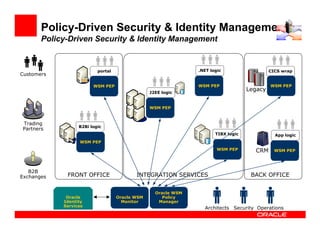
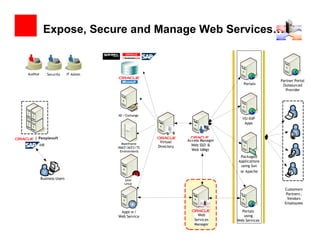
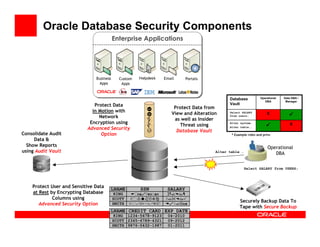
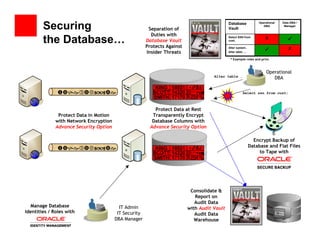
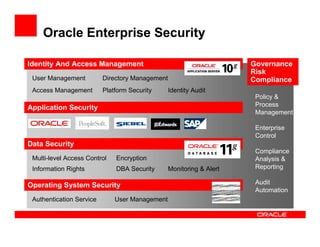
The document outlines the essential components of enterprise security architecture, emphasizing the need for effective access control, compliance with regulations, and protection of data as businesses navigate a turbulent environment. It discusses the importance of a comprehensive security approach, including governance, risk management, and continuous monitoring across various systems and user identities. Additionally, it highlights Oracle's solutions for managing security and compliance across applications and infrastructure.