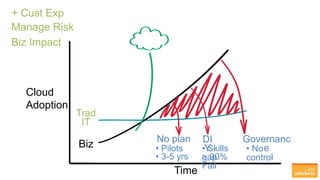
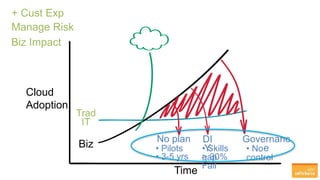
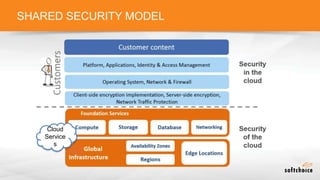
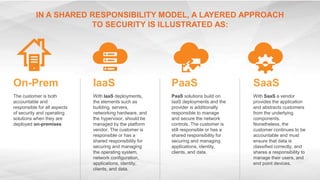
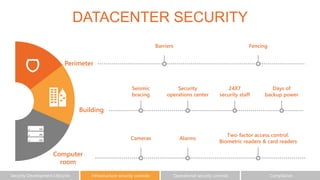
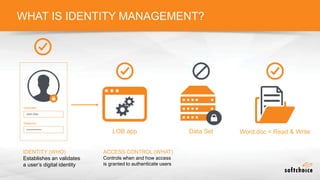
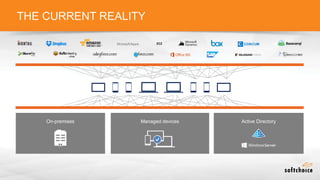
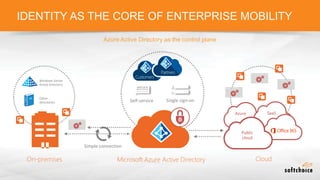
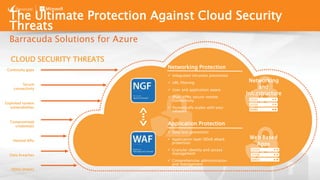
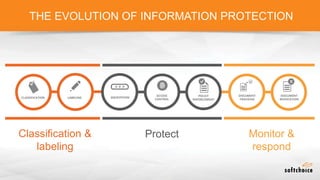
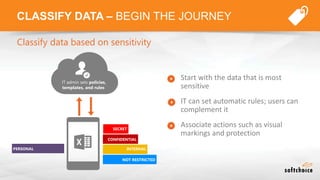
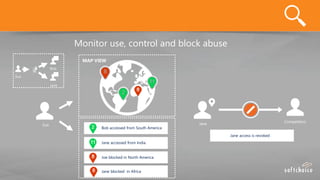
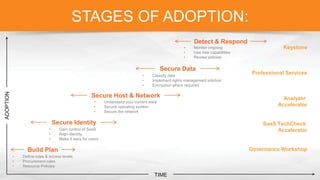
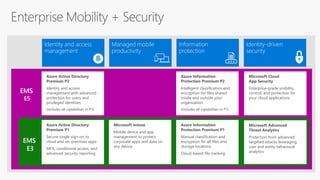
The document outlines the importance of understanding cloud security responsibilities, emphasizing the shared security model between cloud providers and customers. It details the elements of data center security, identity management, and network infrastructure security, highlighting how each party is accountable for certain aspects of security. The presentation aims to clarify what cloud providers secure and what responsibilities customers must manage to ensure effective cloud security.