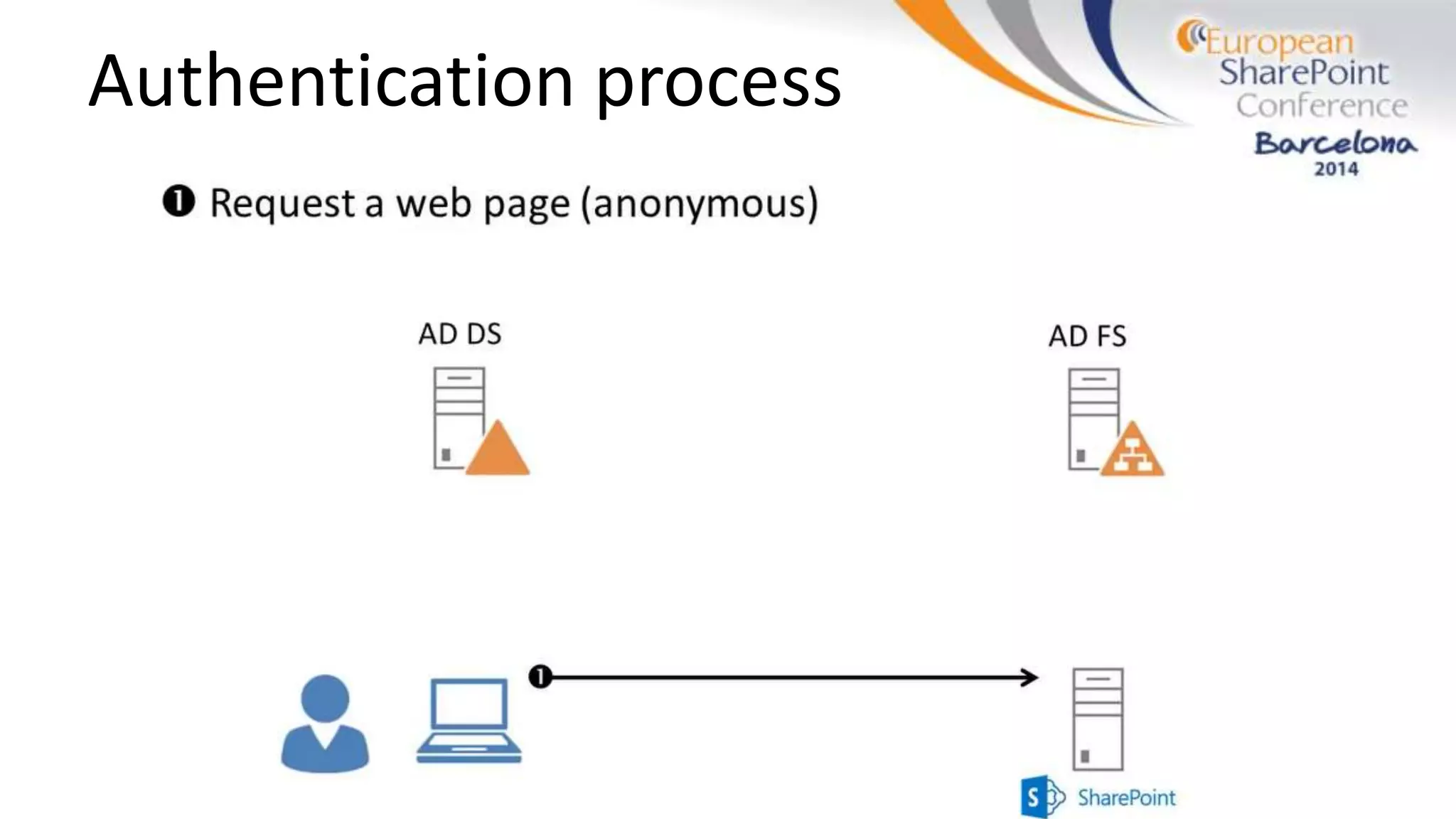
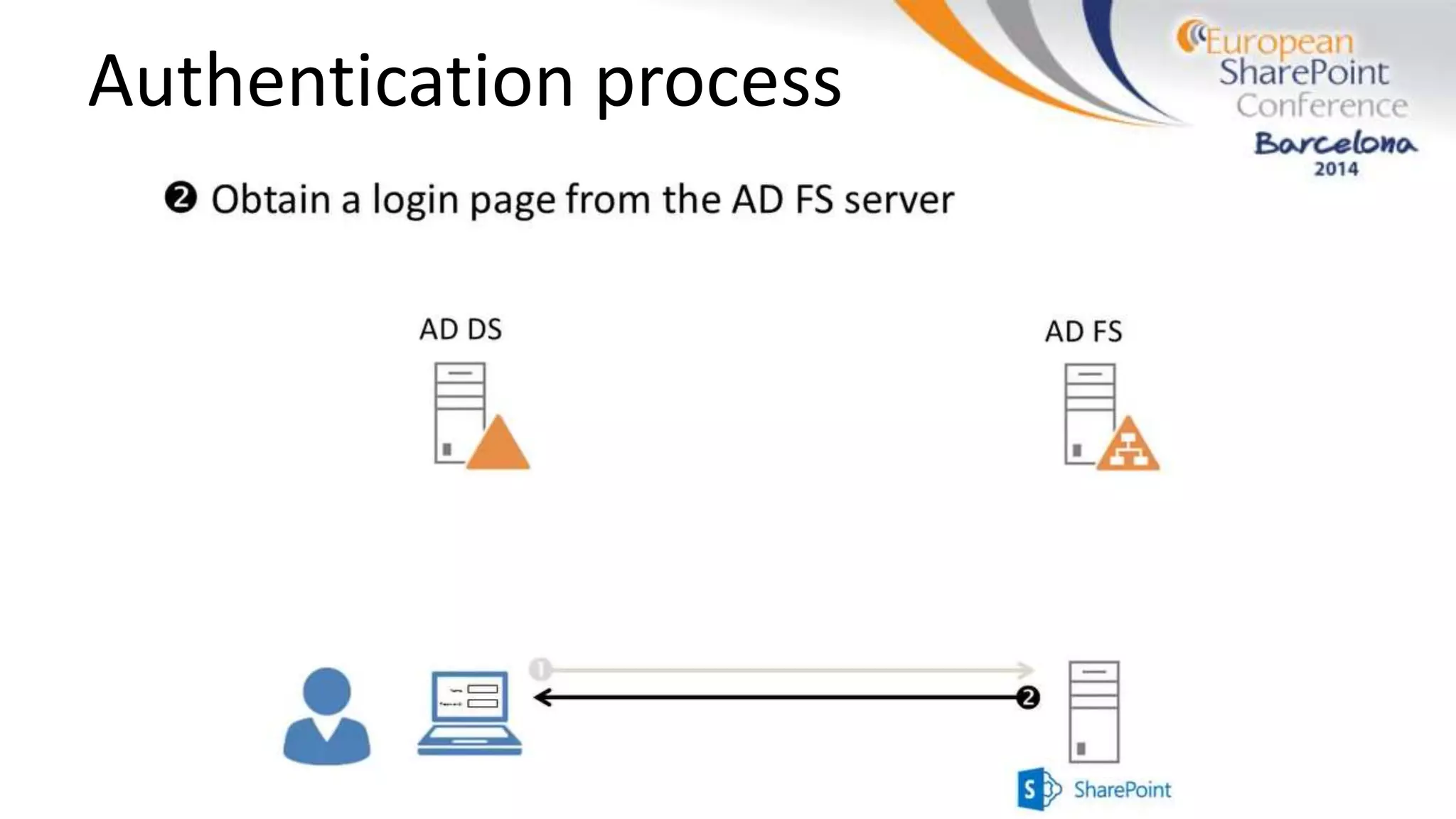
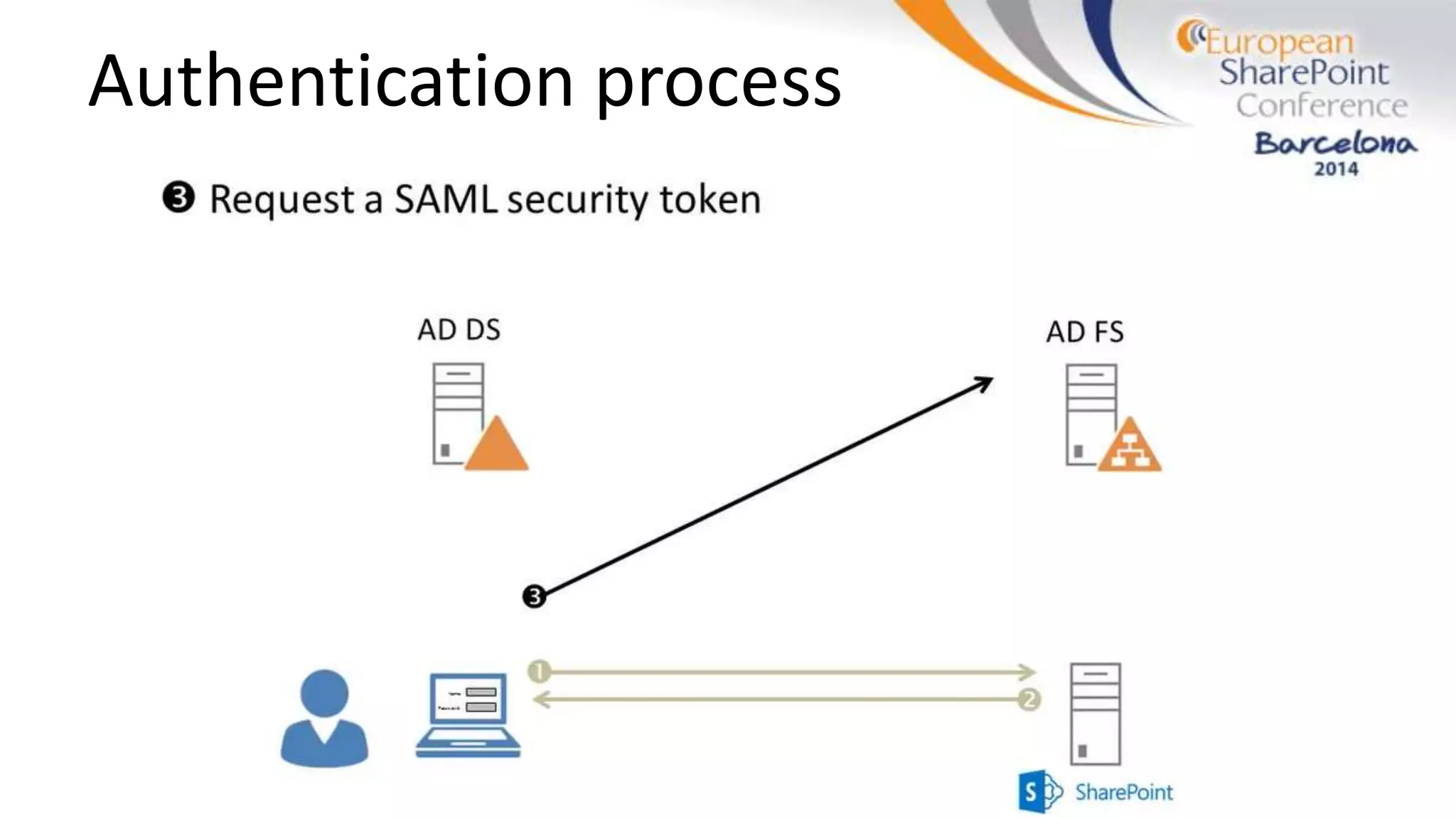
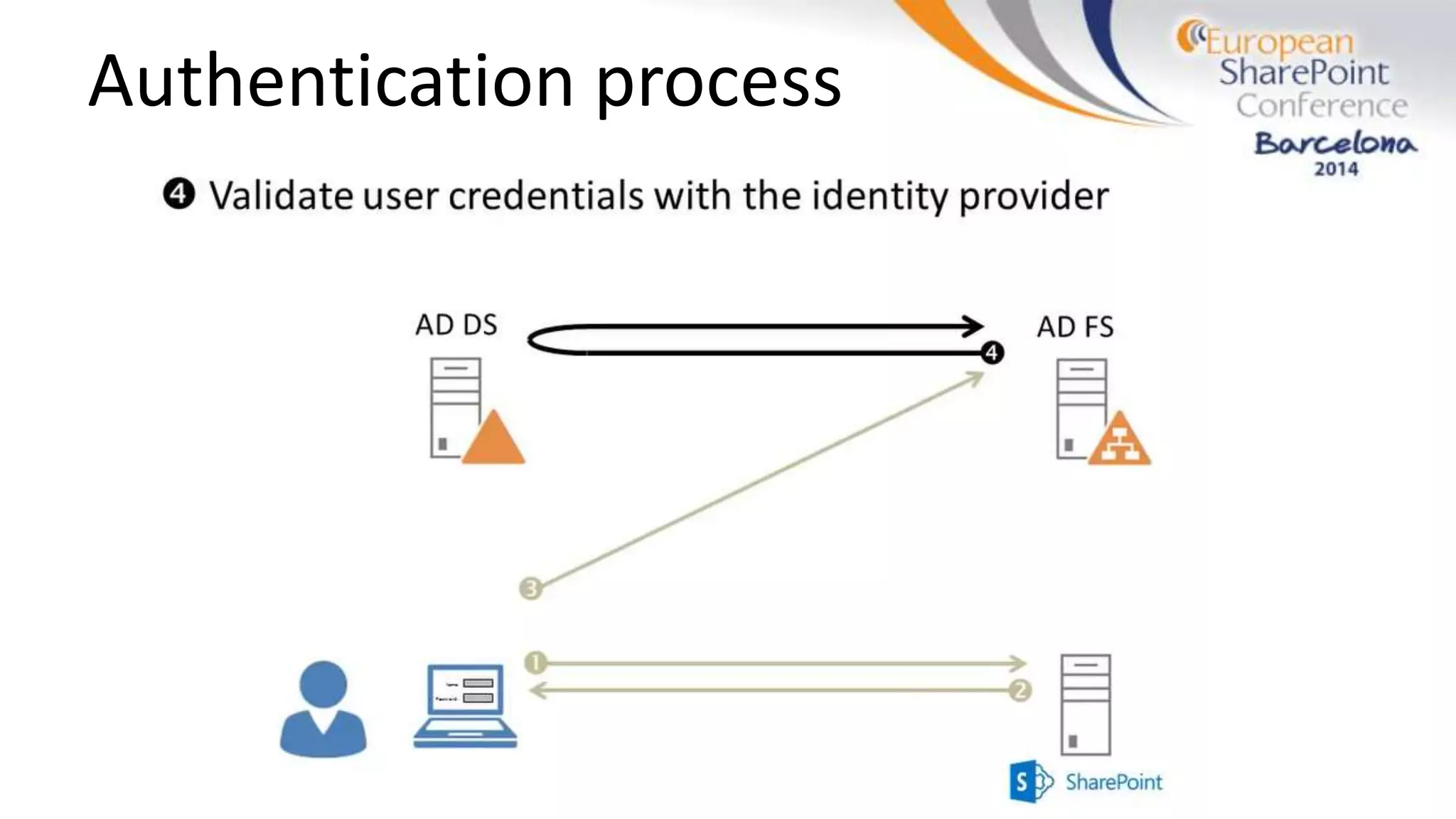
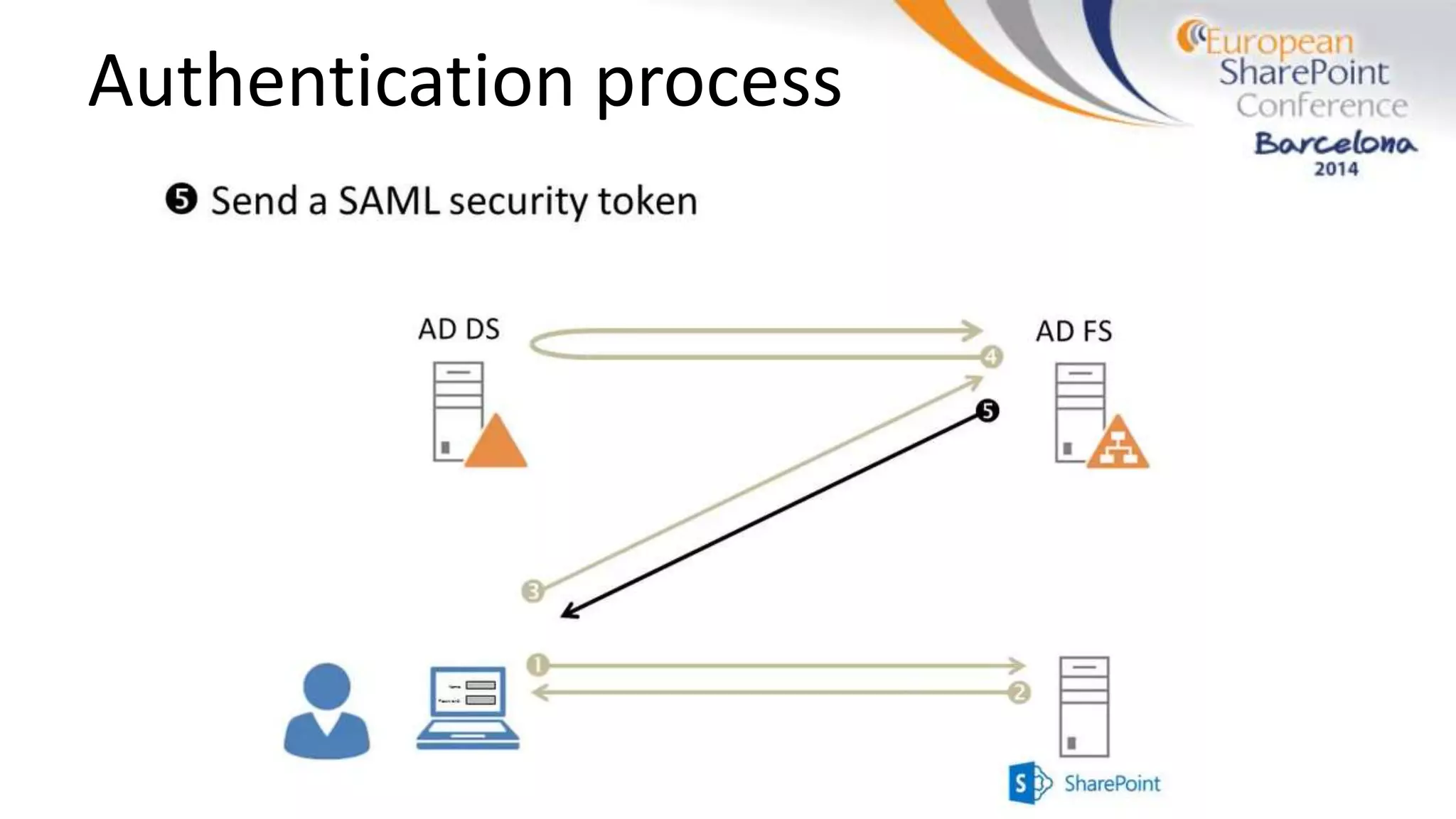
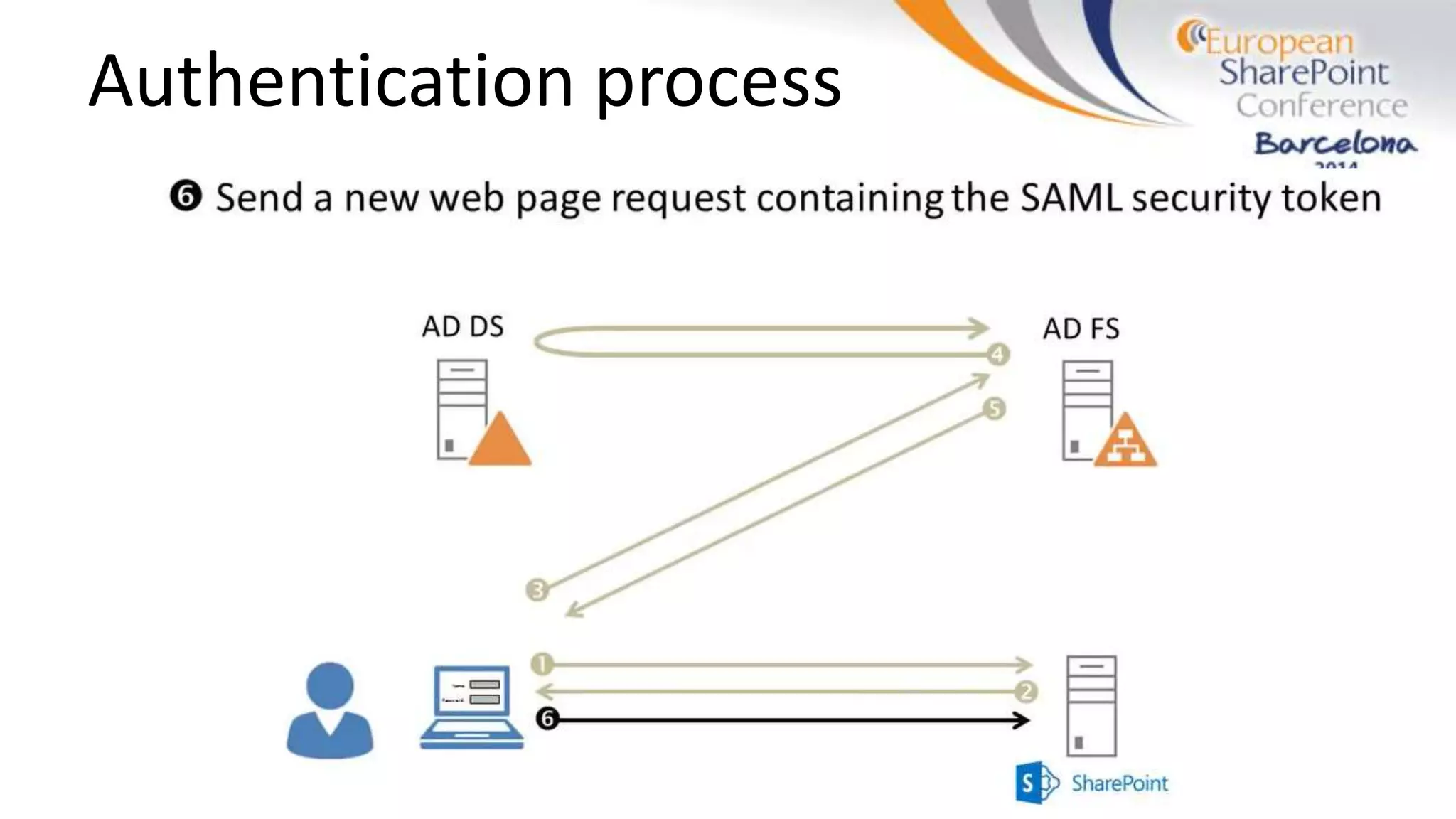
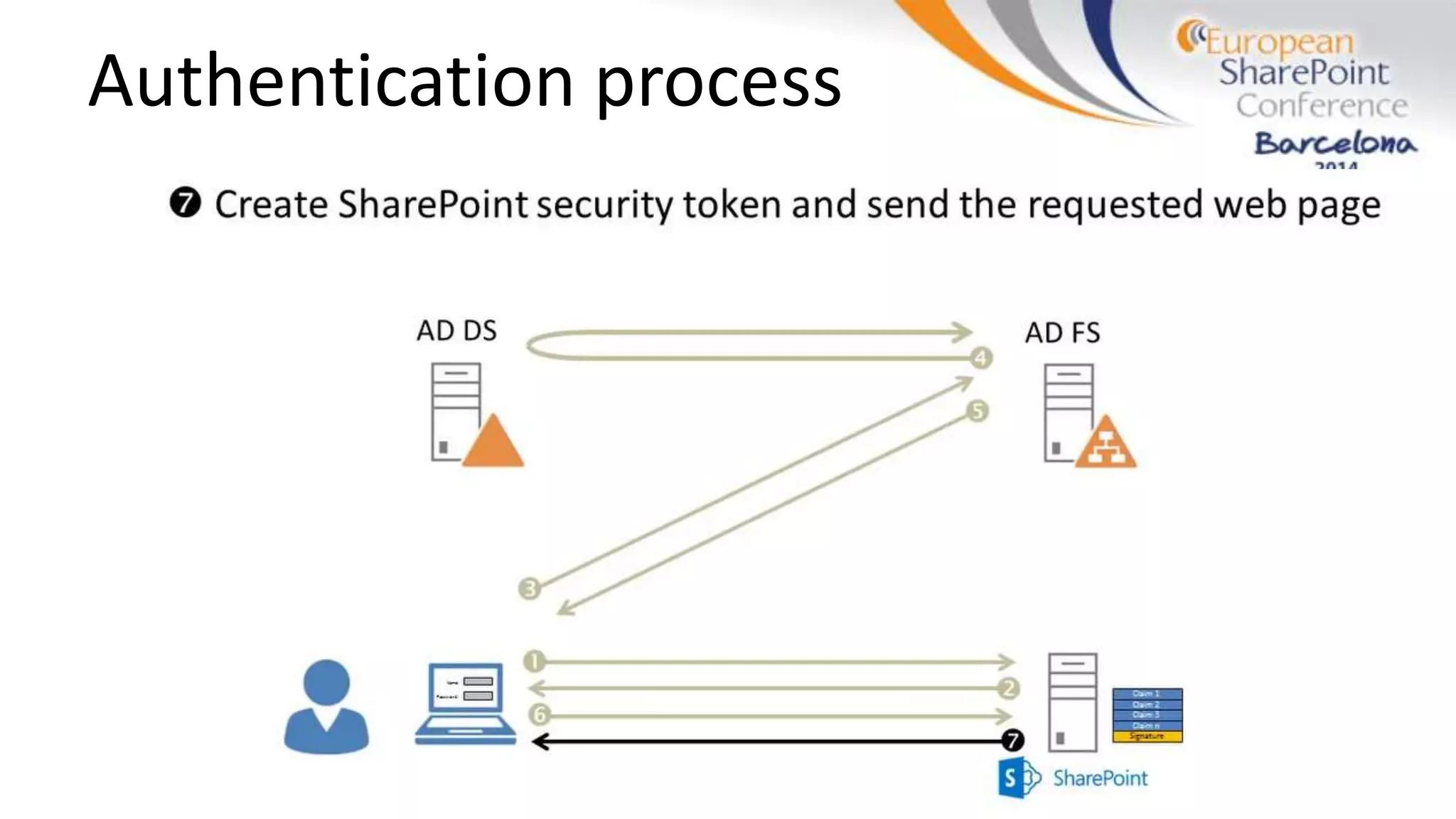
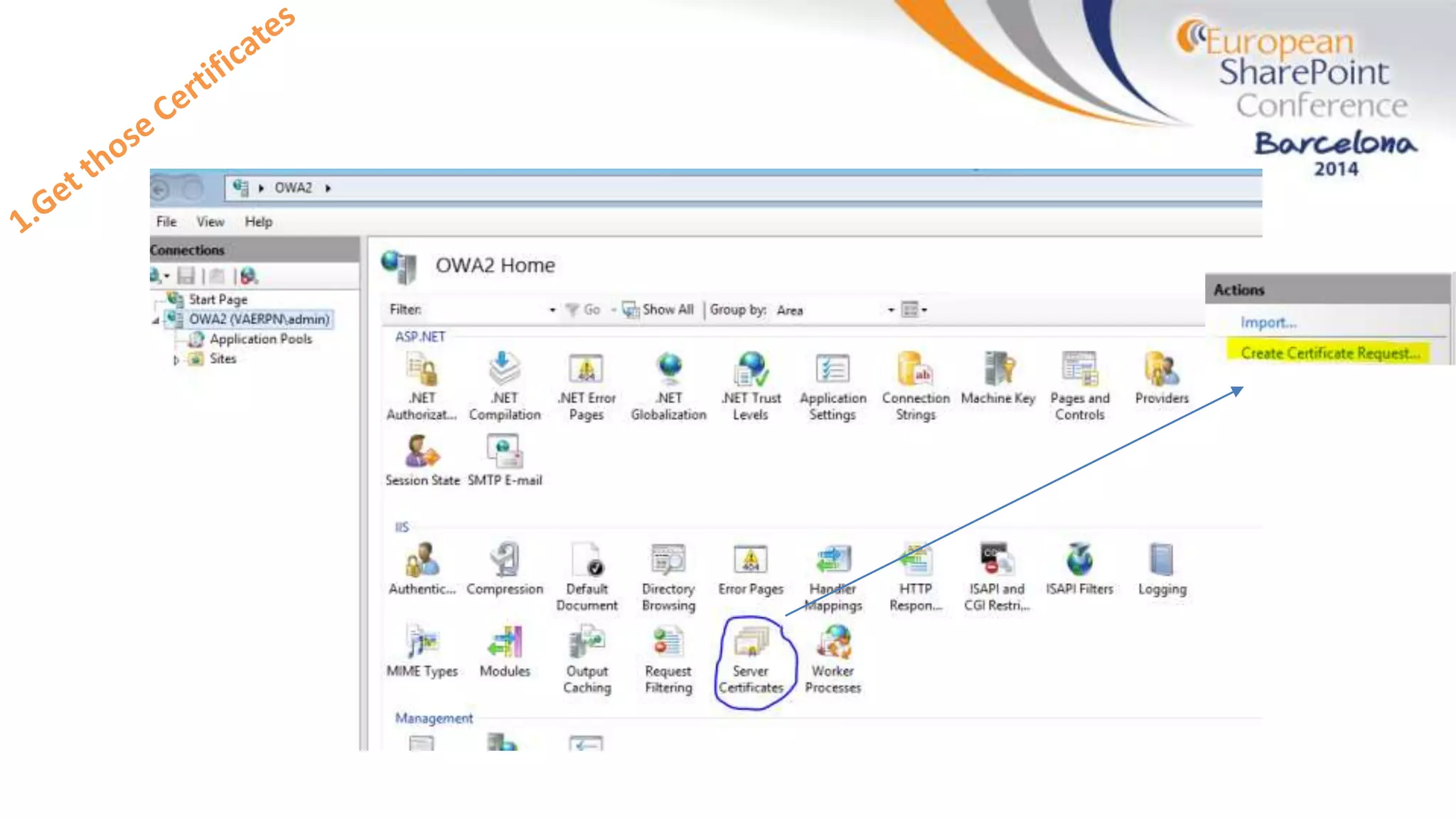
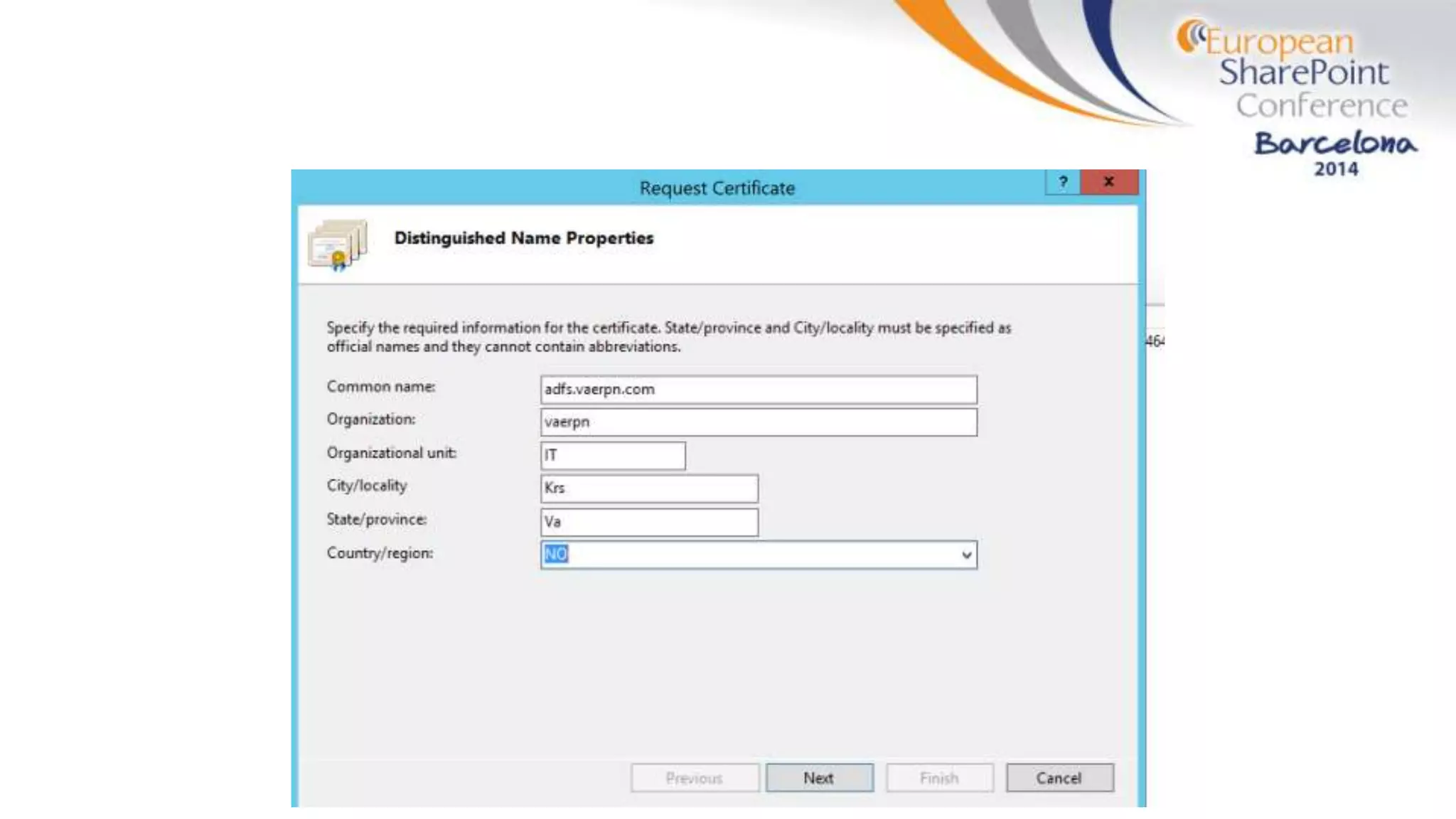
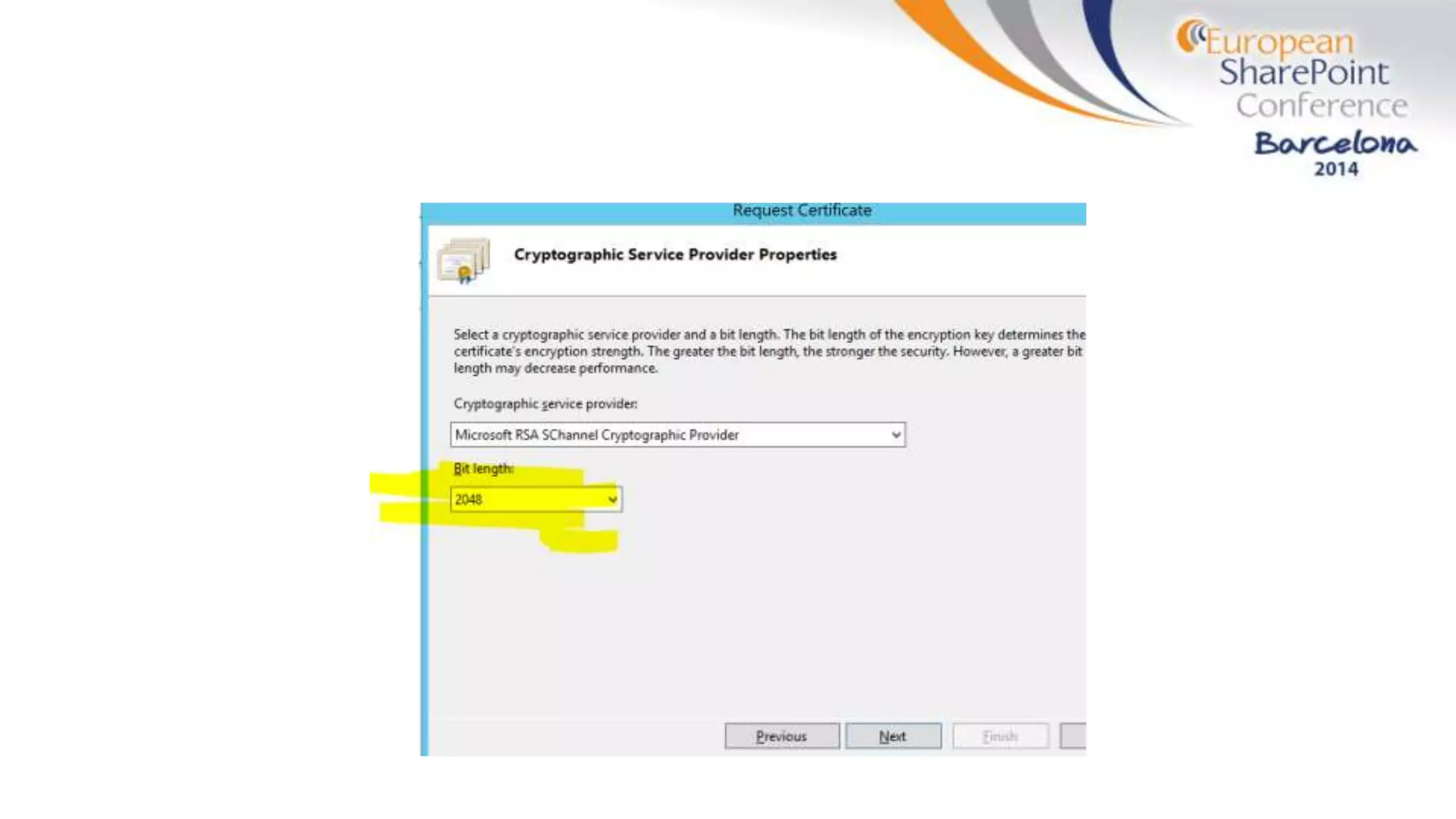
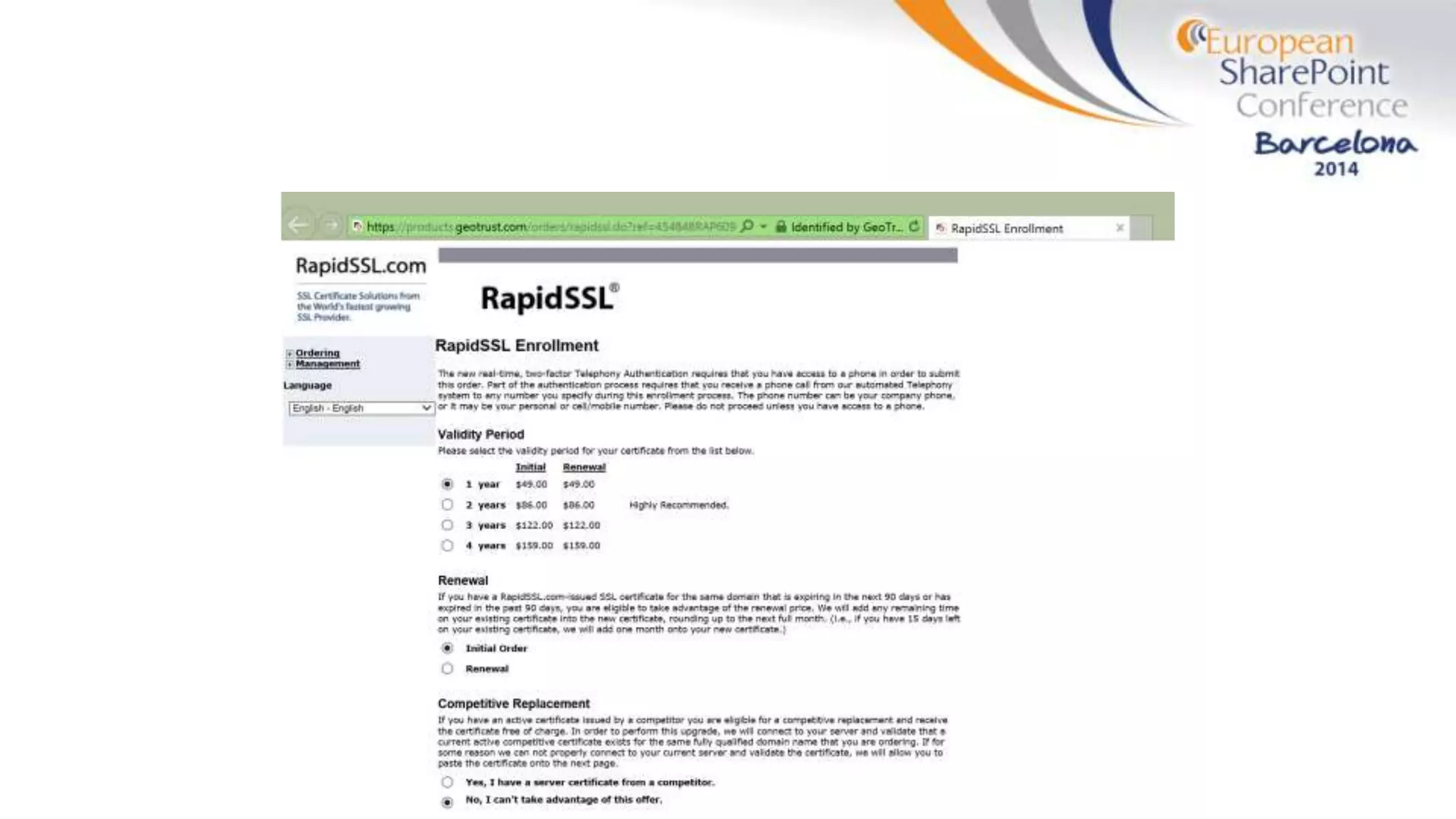
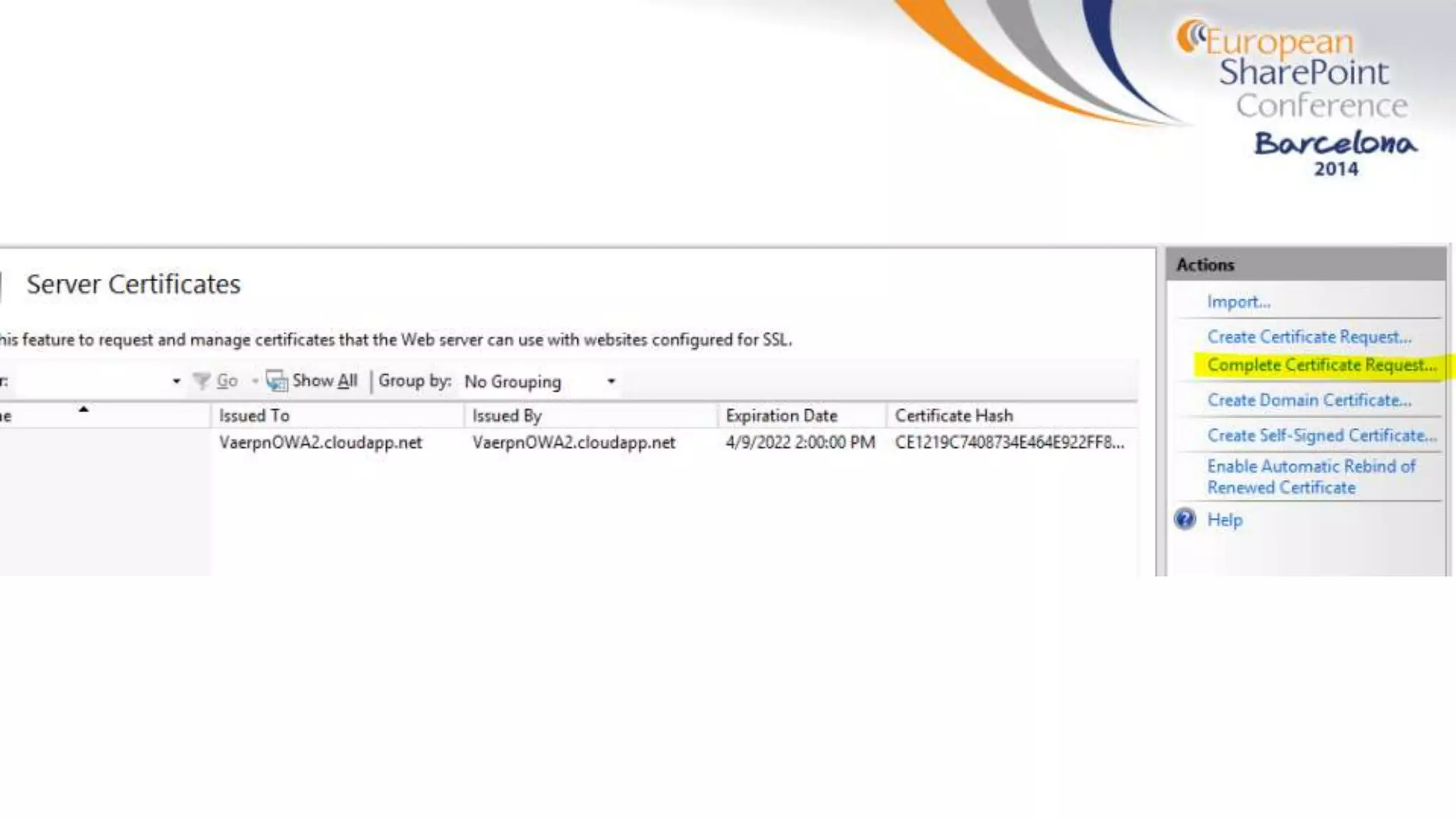
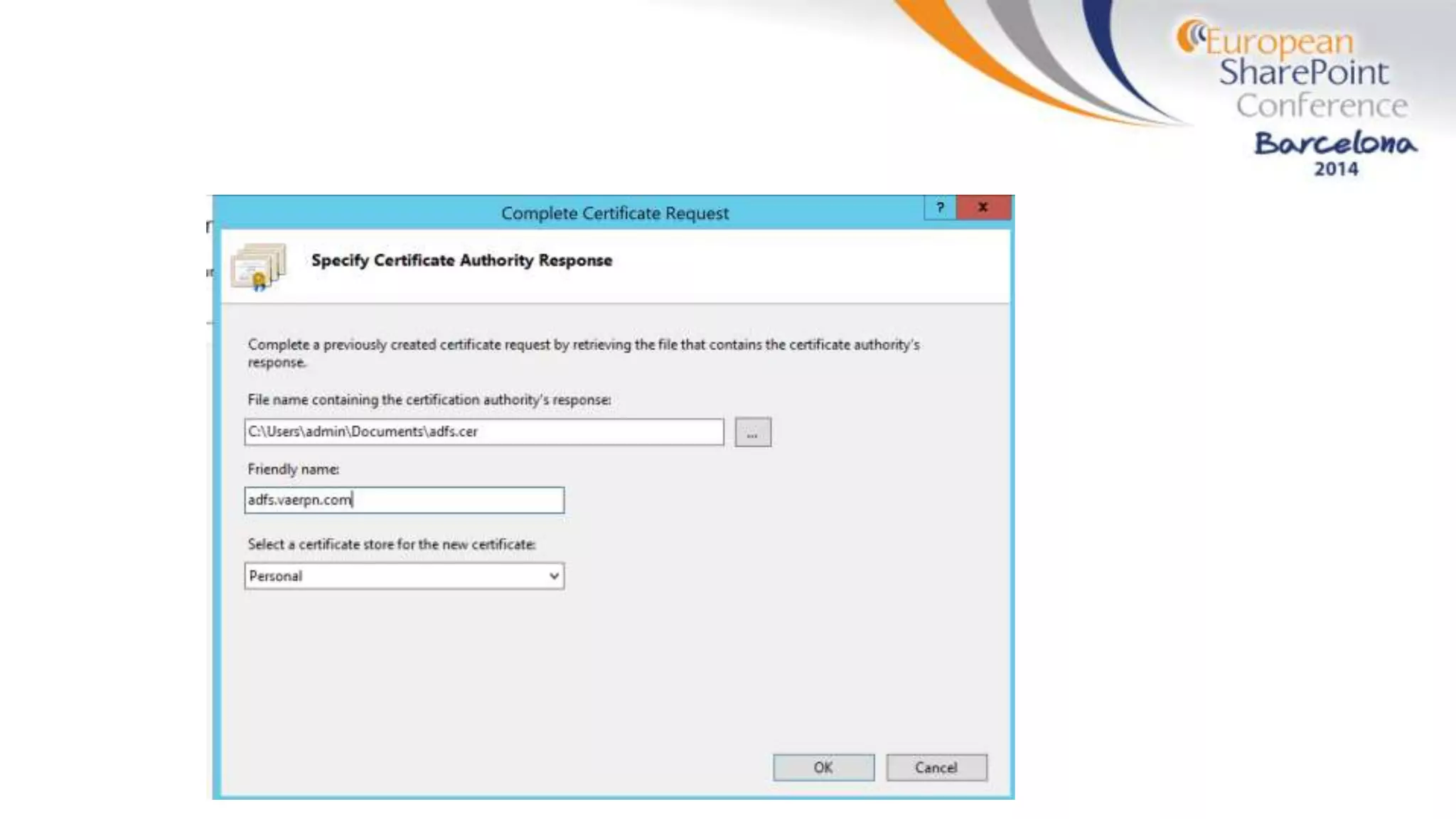
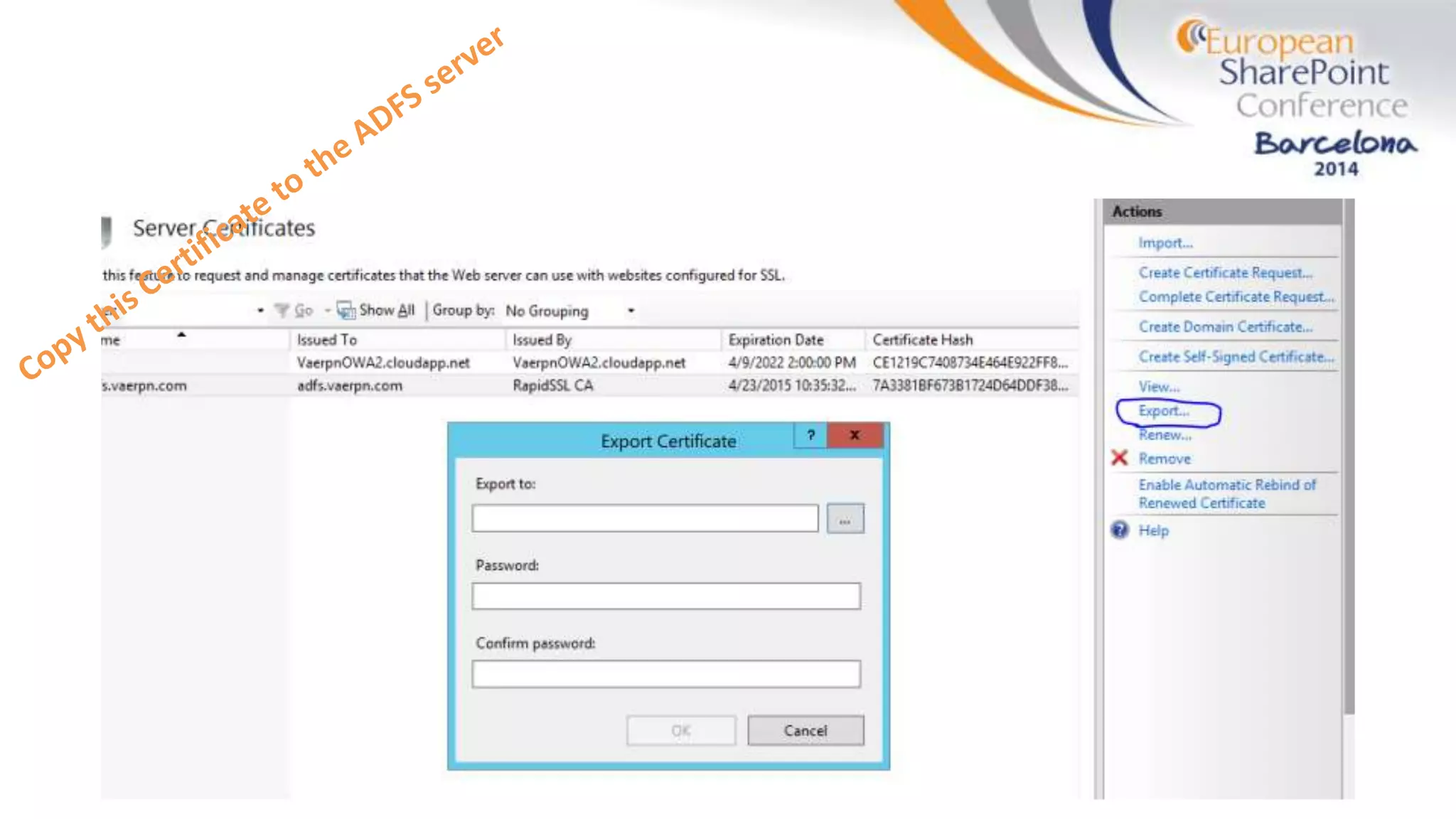
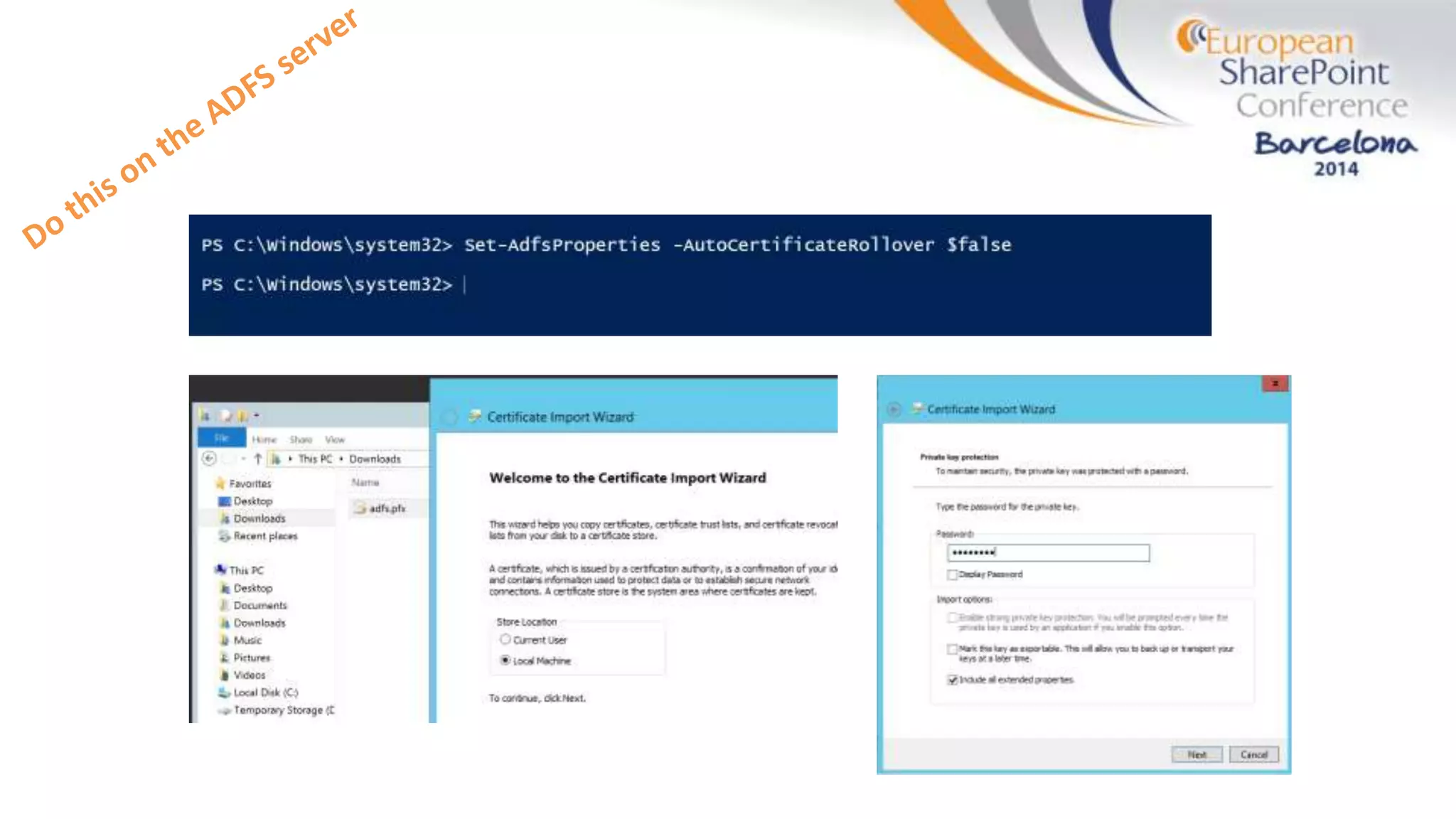
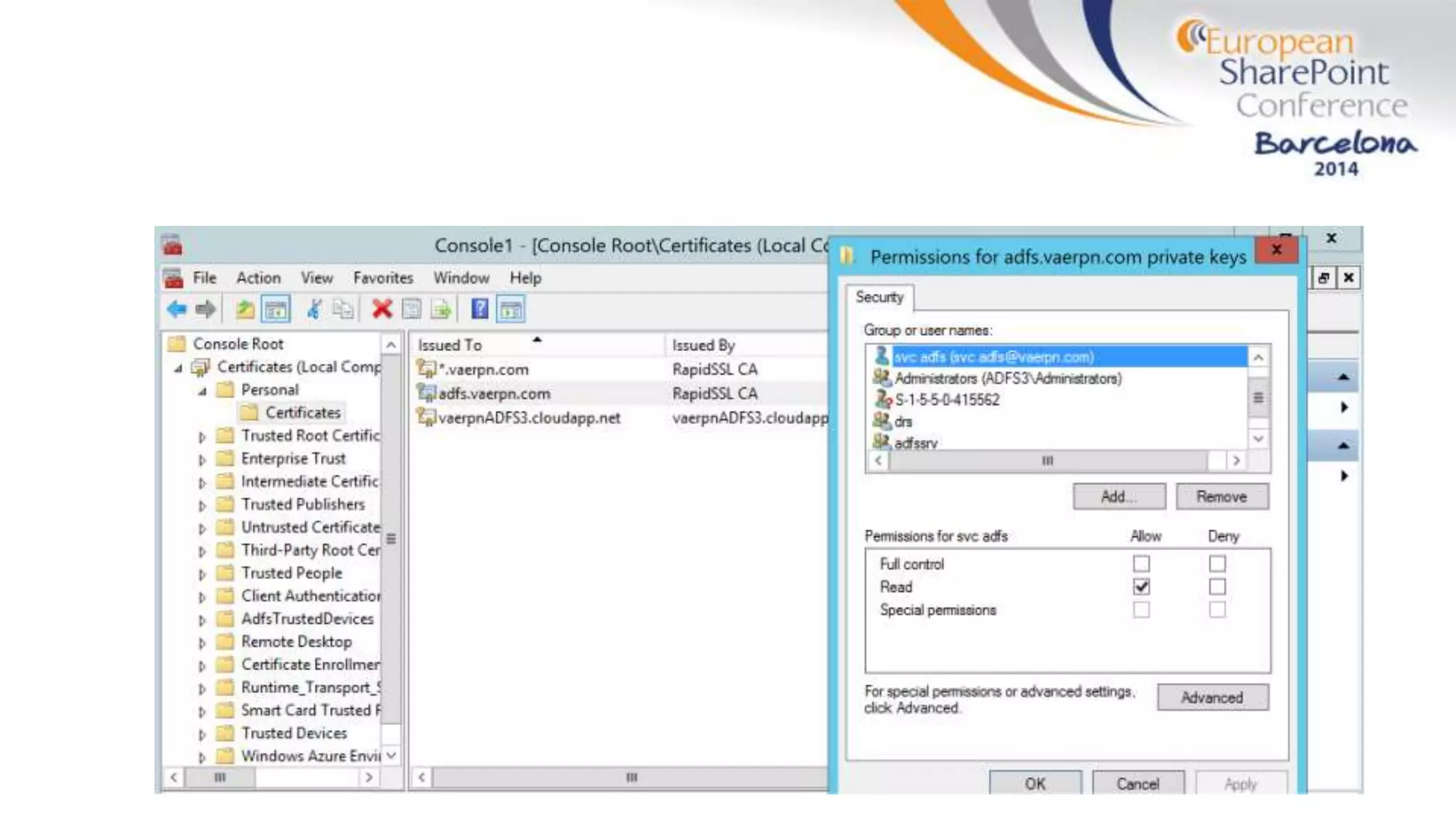
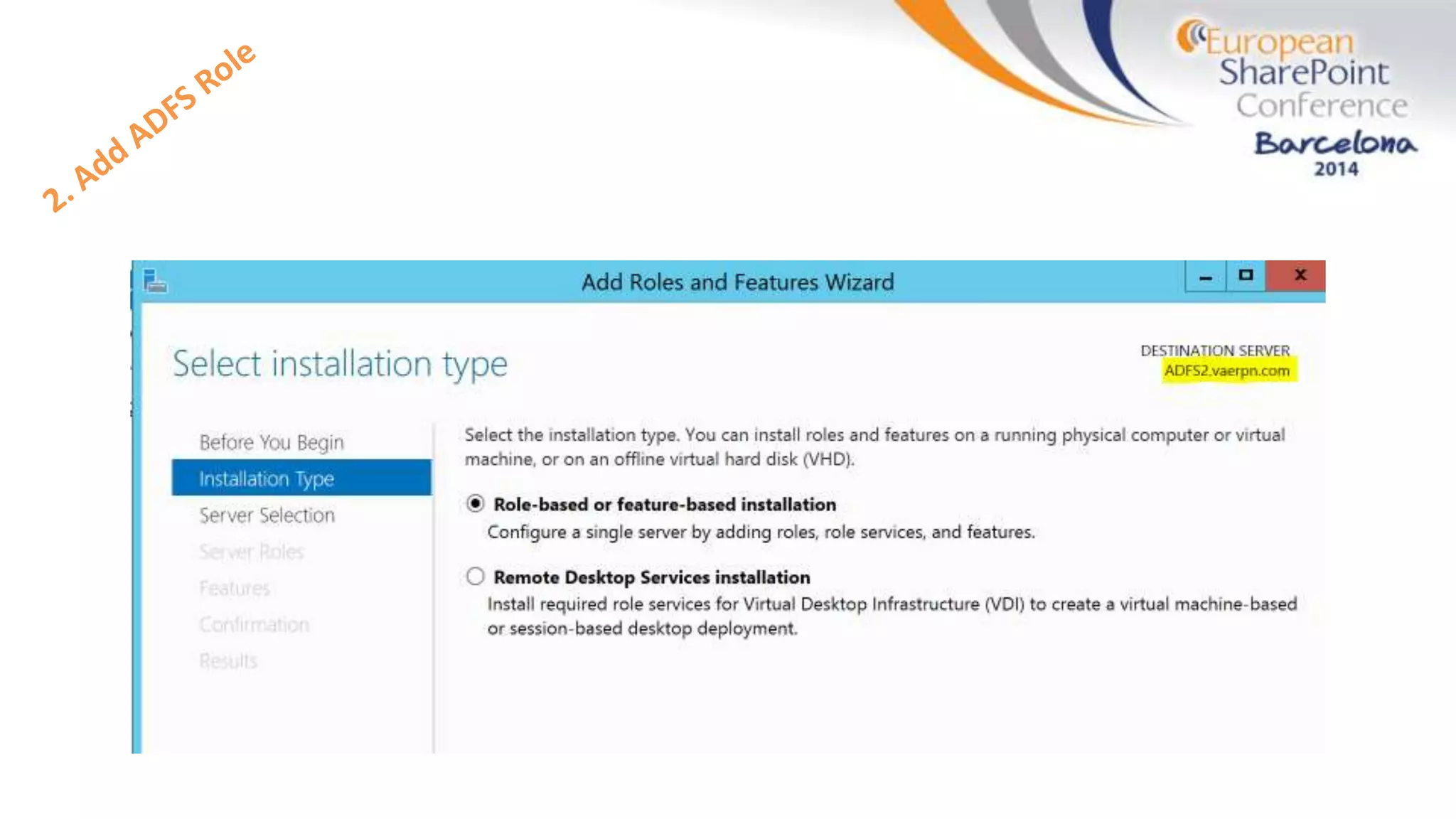
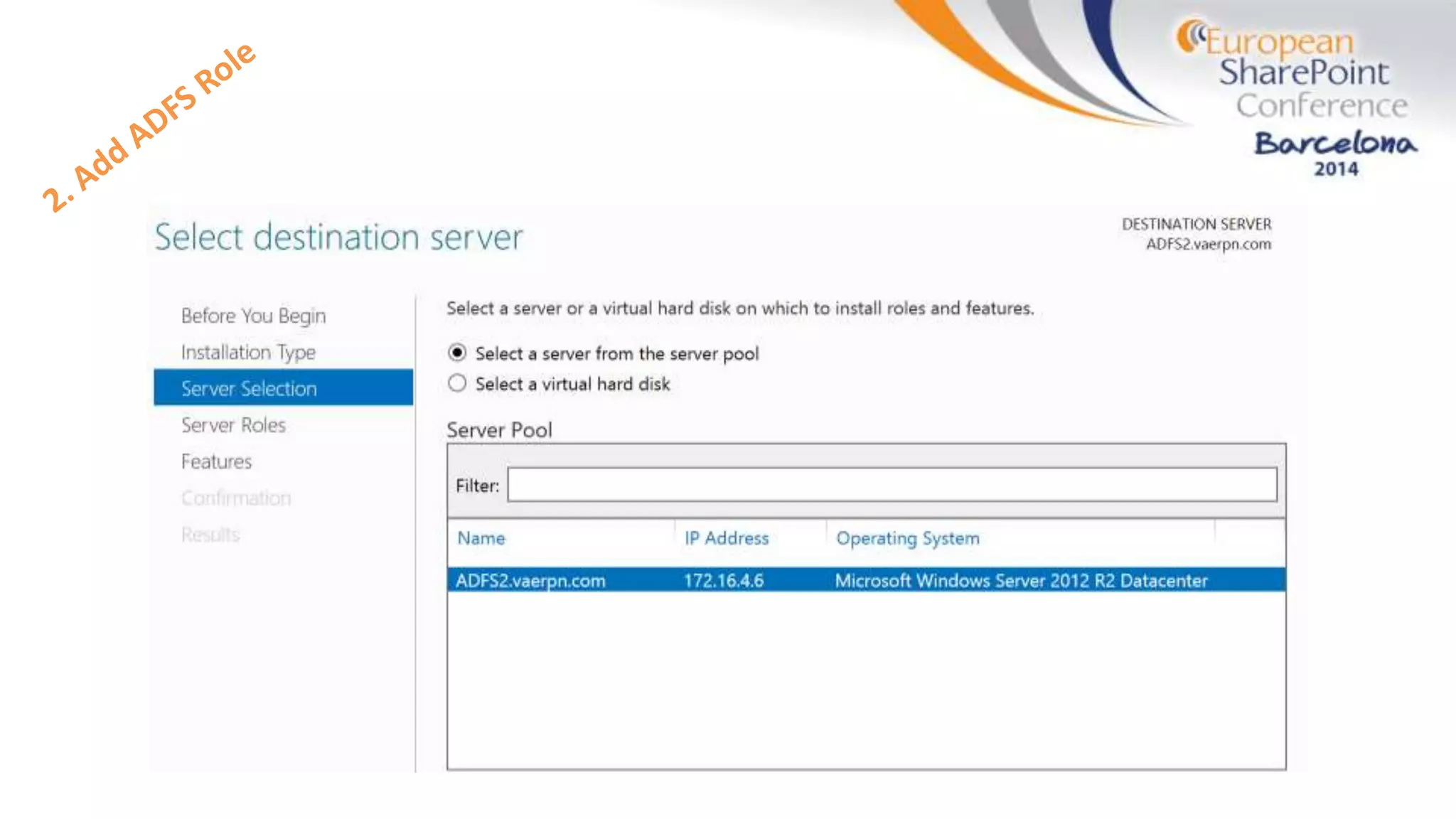
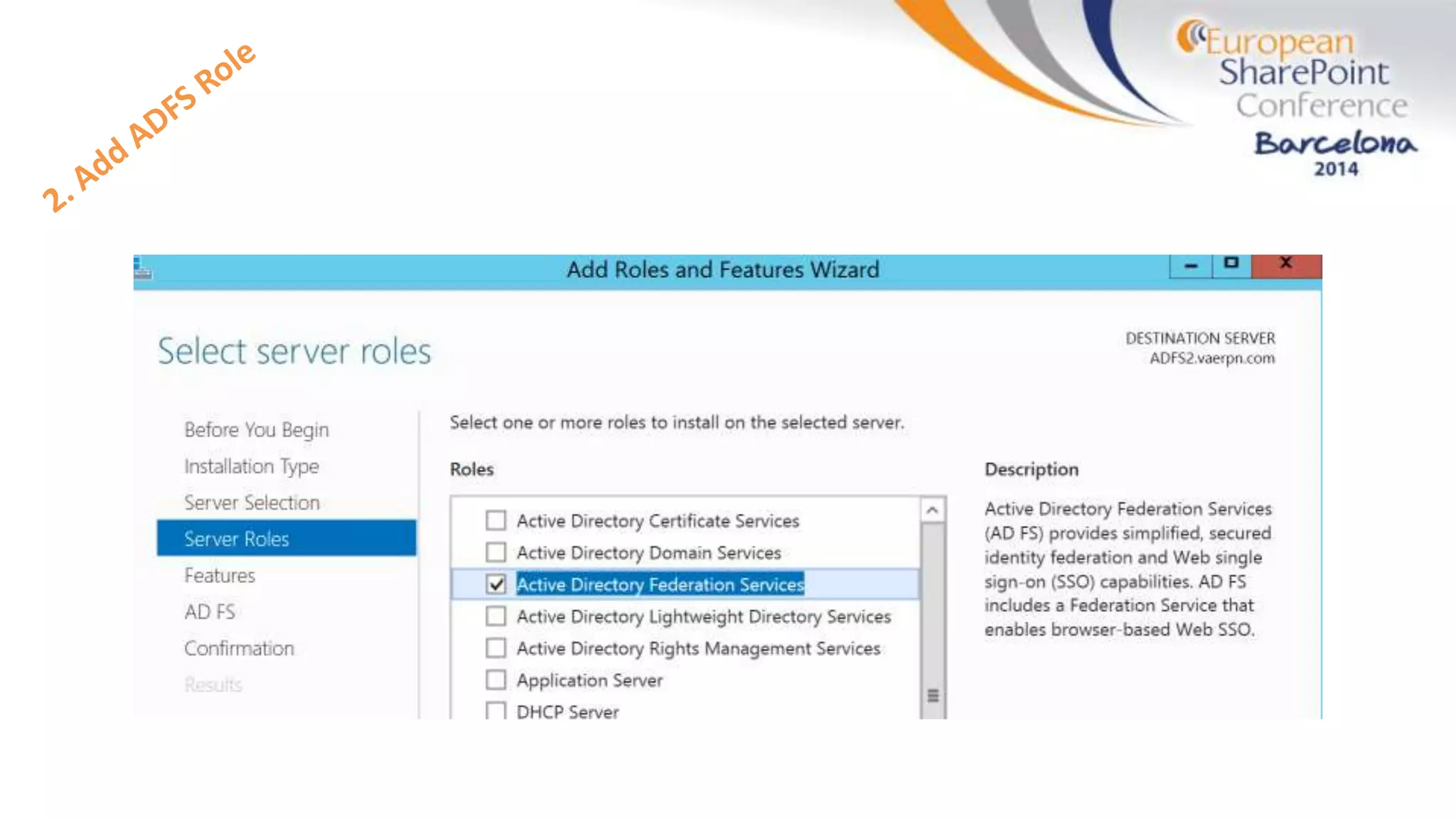
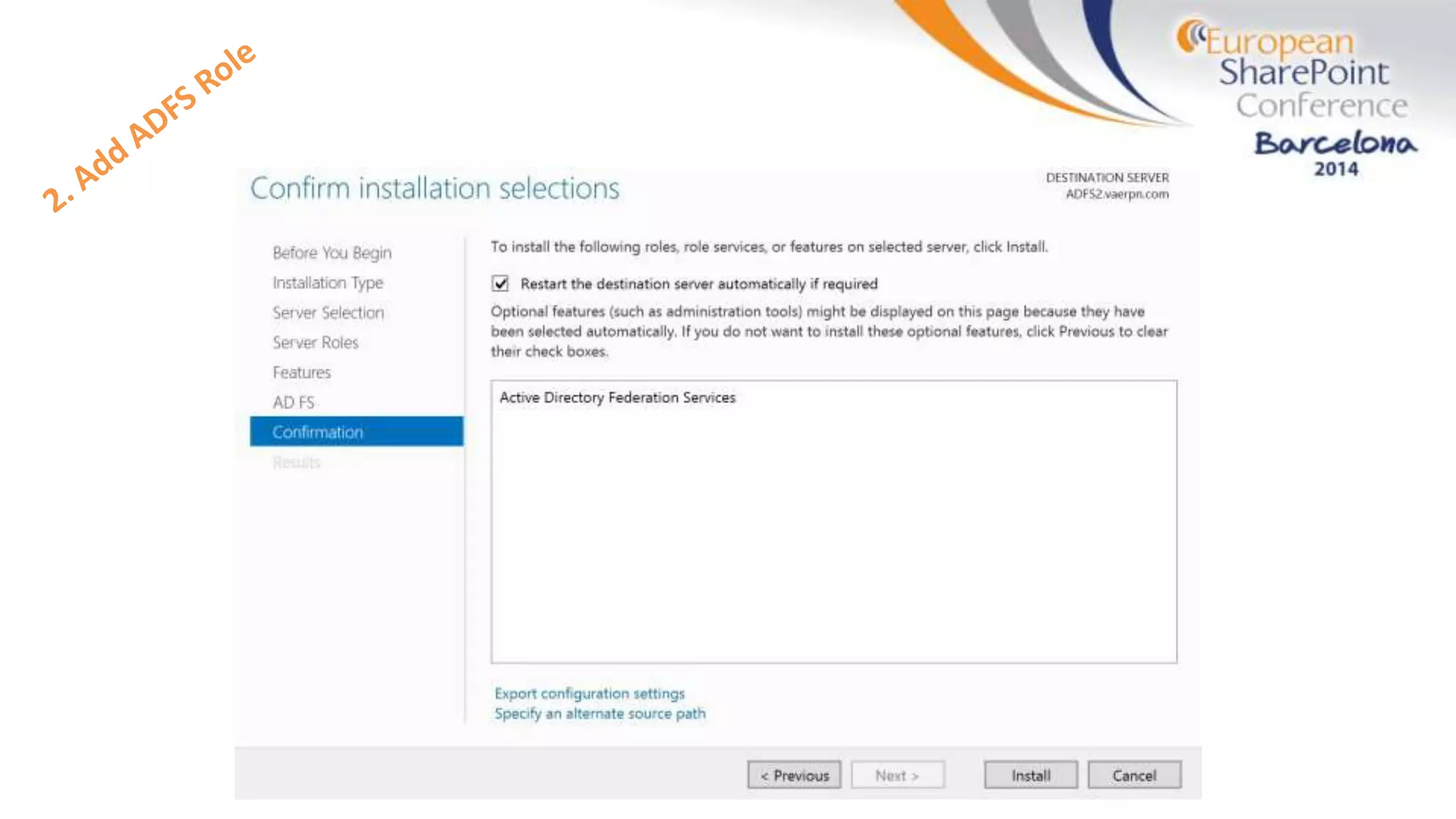
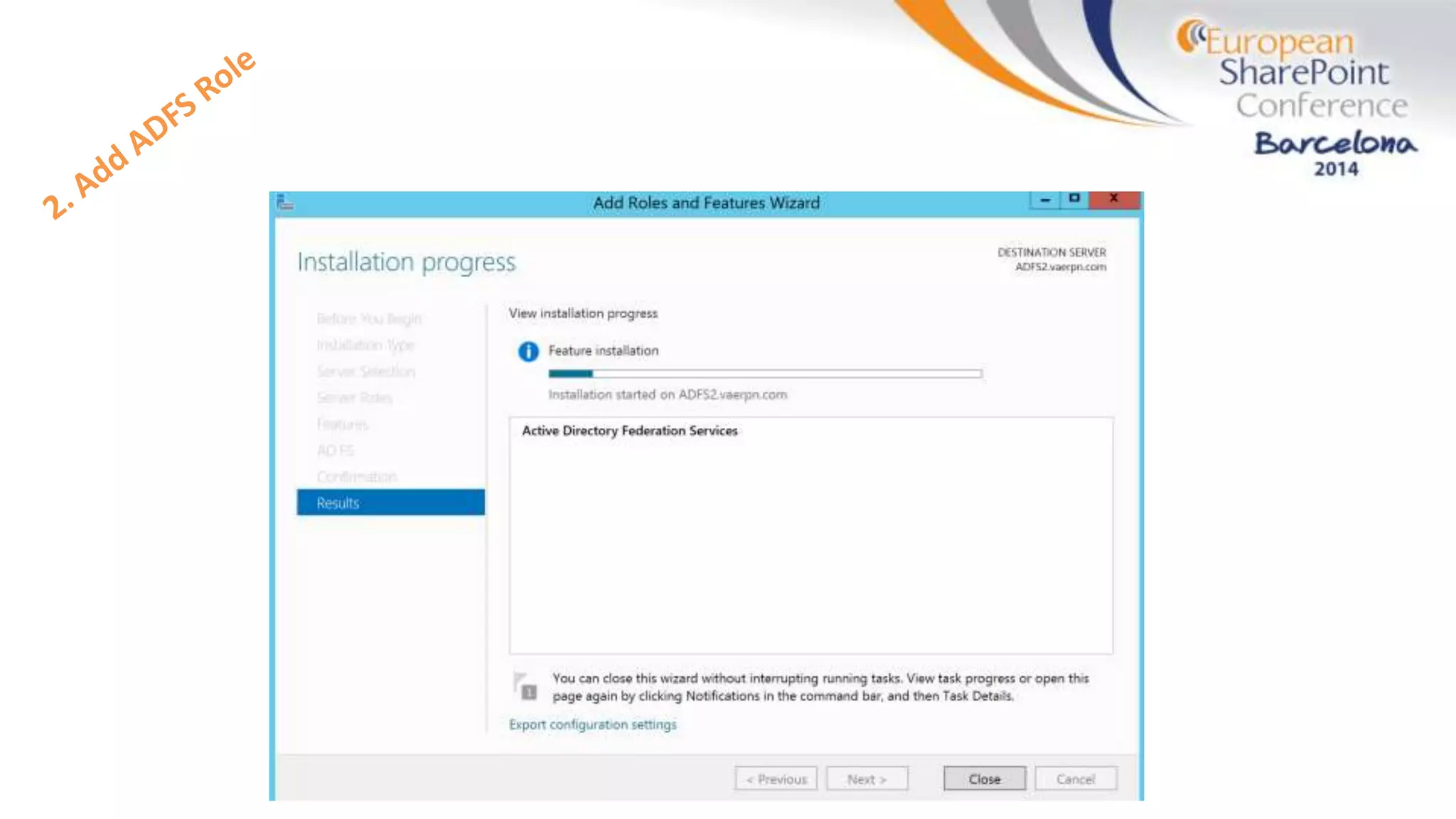
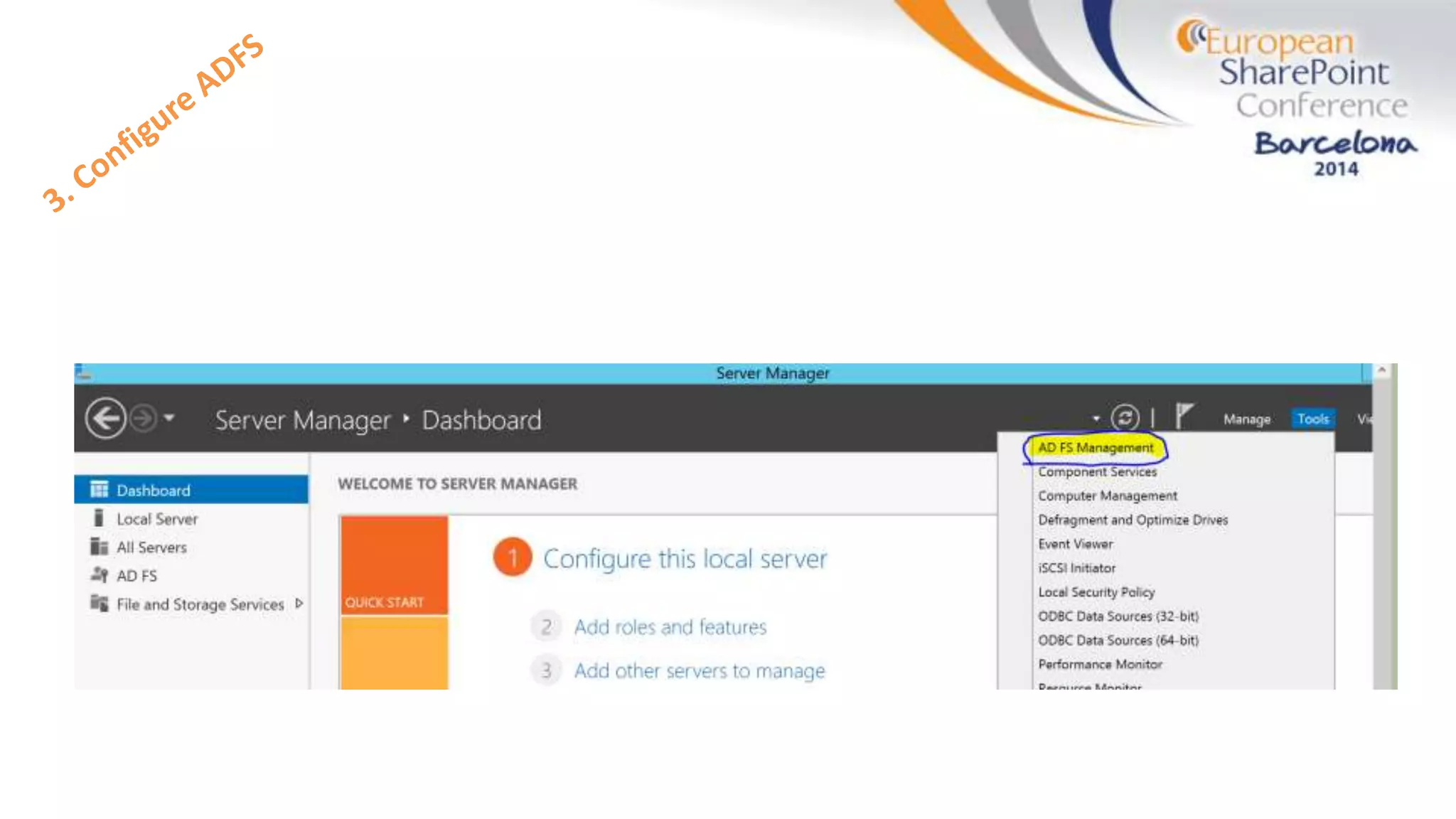
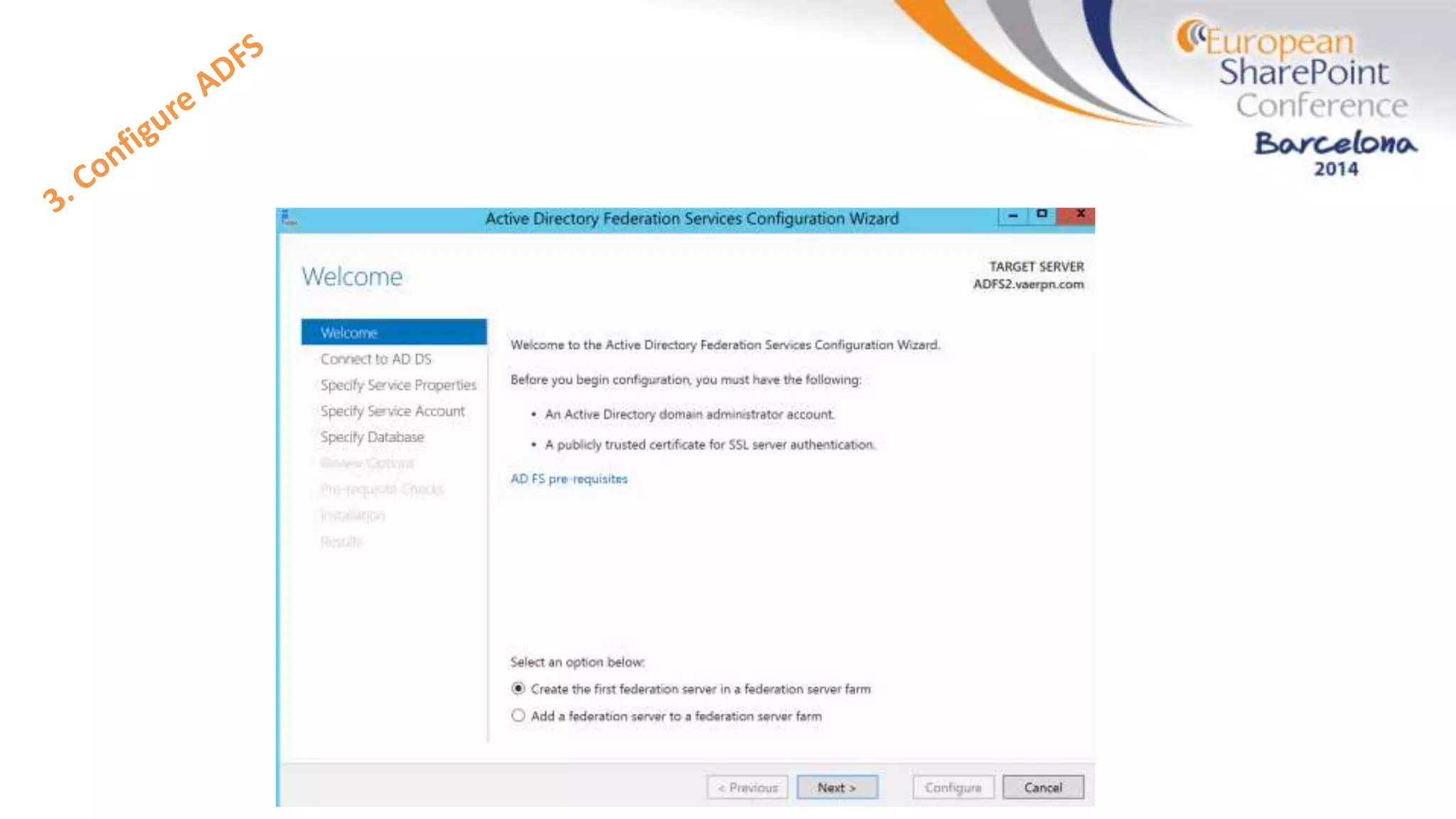
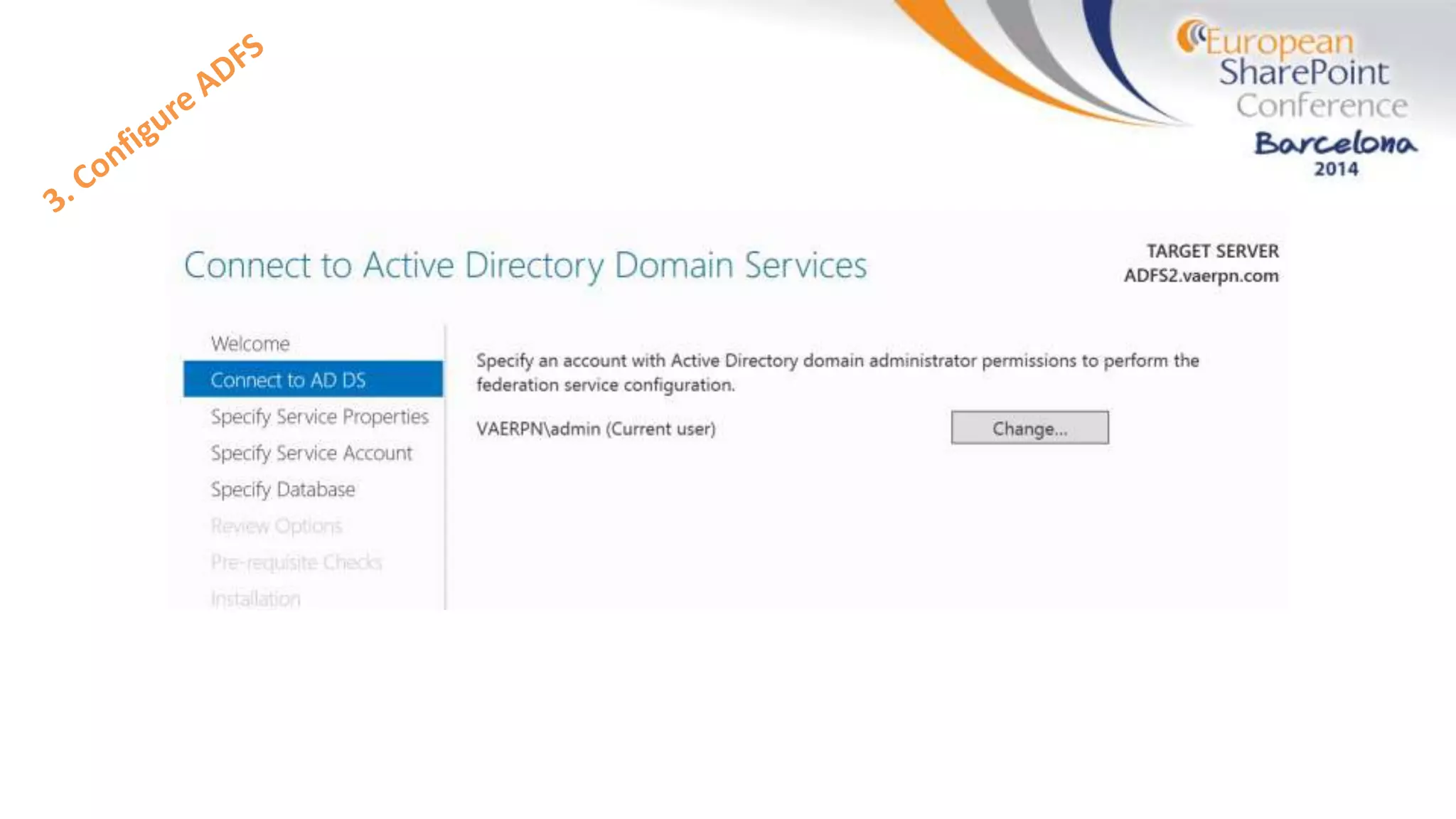
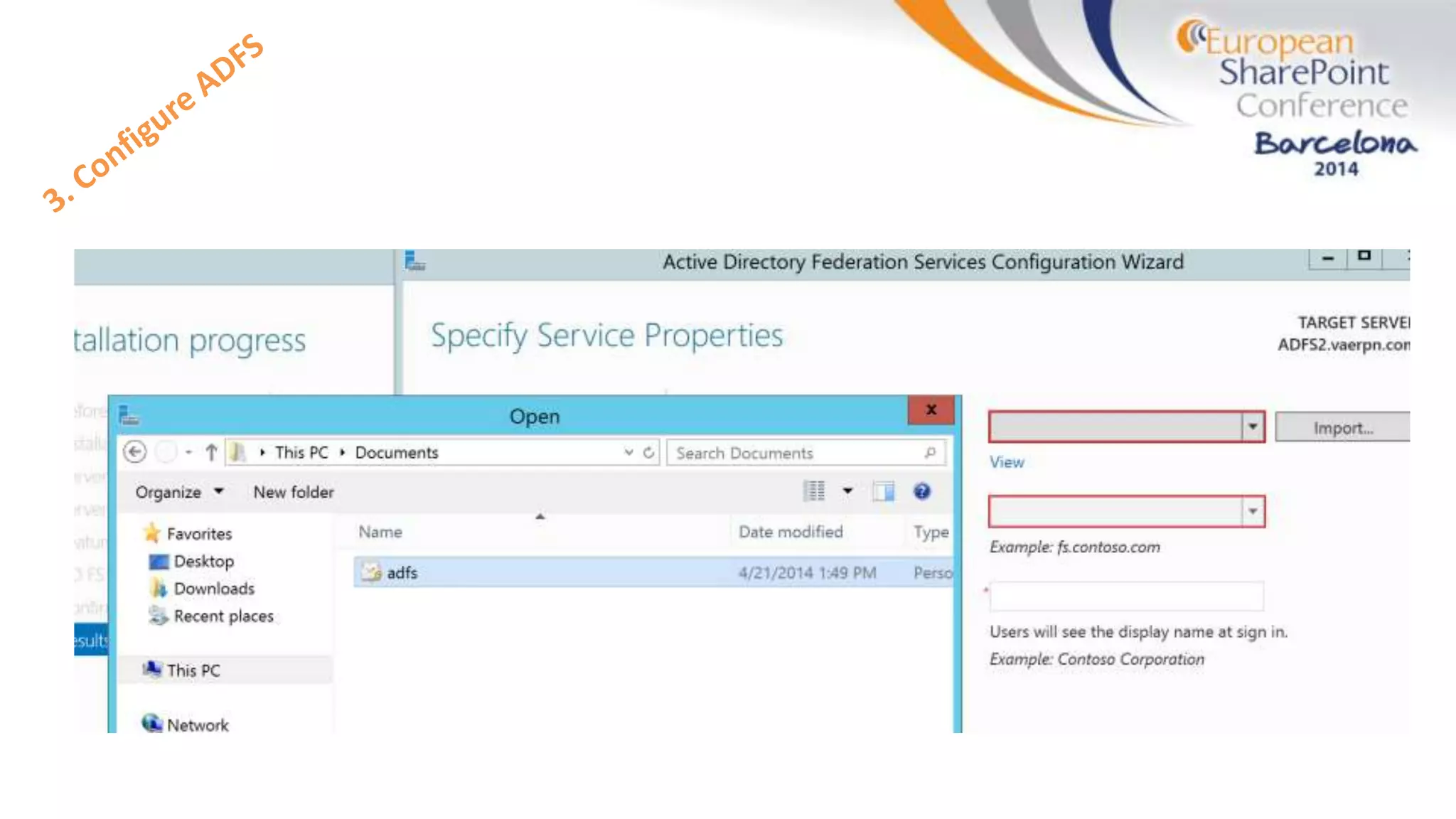
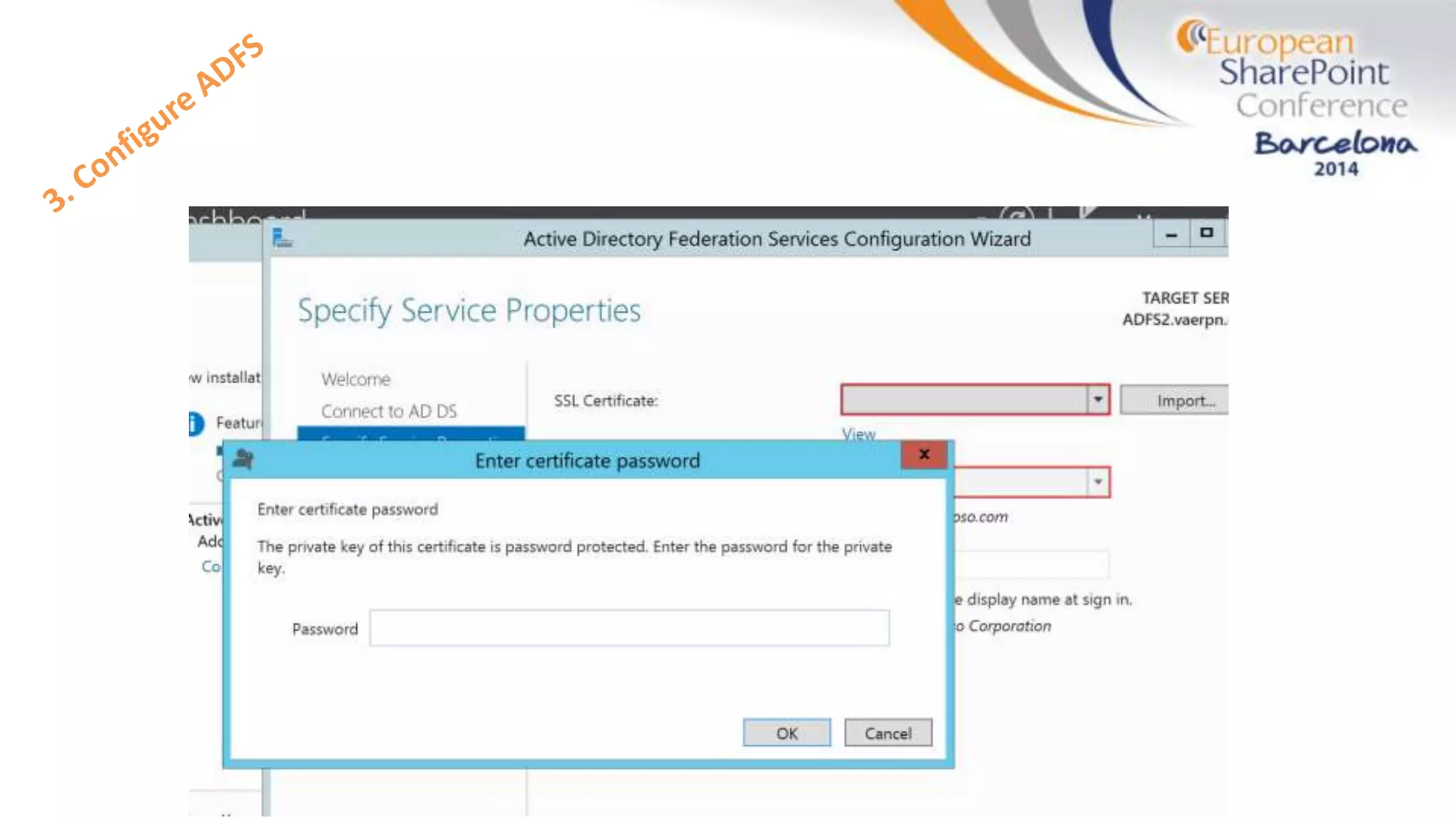
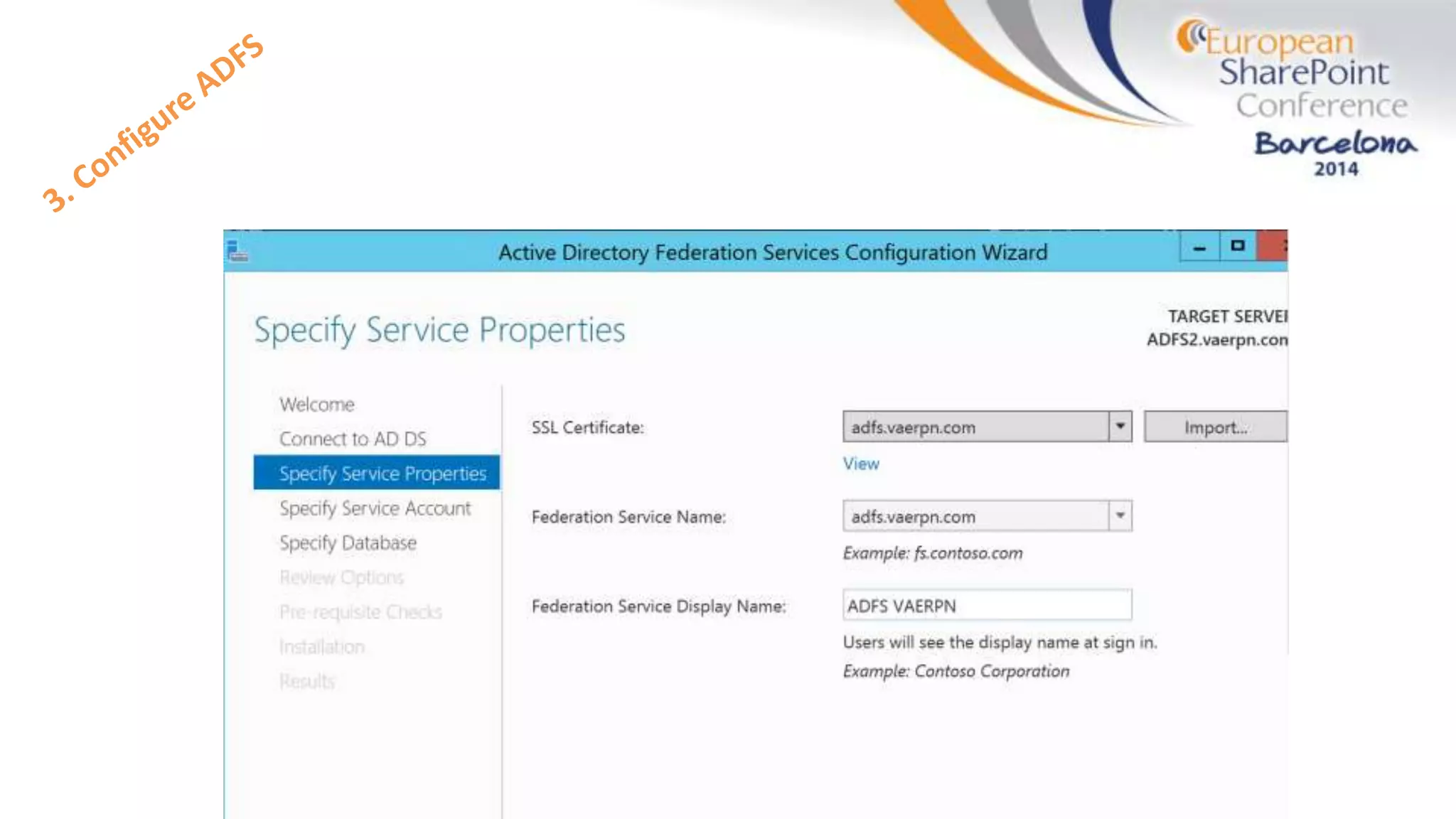
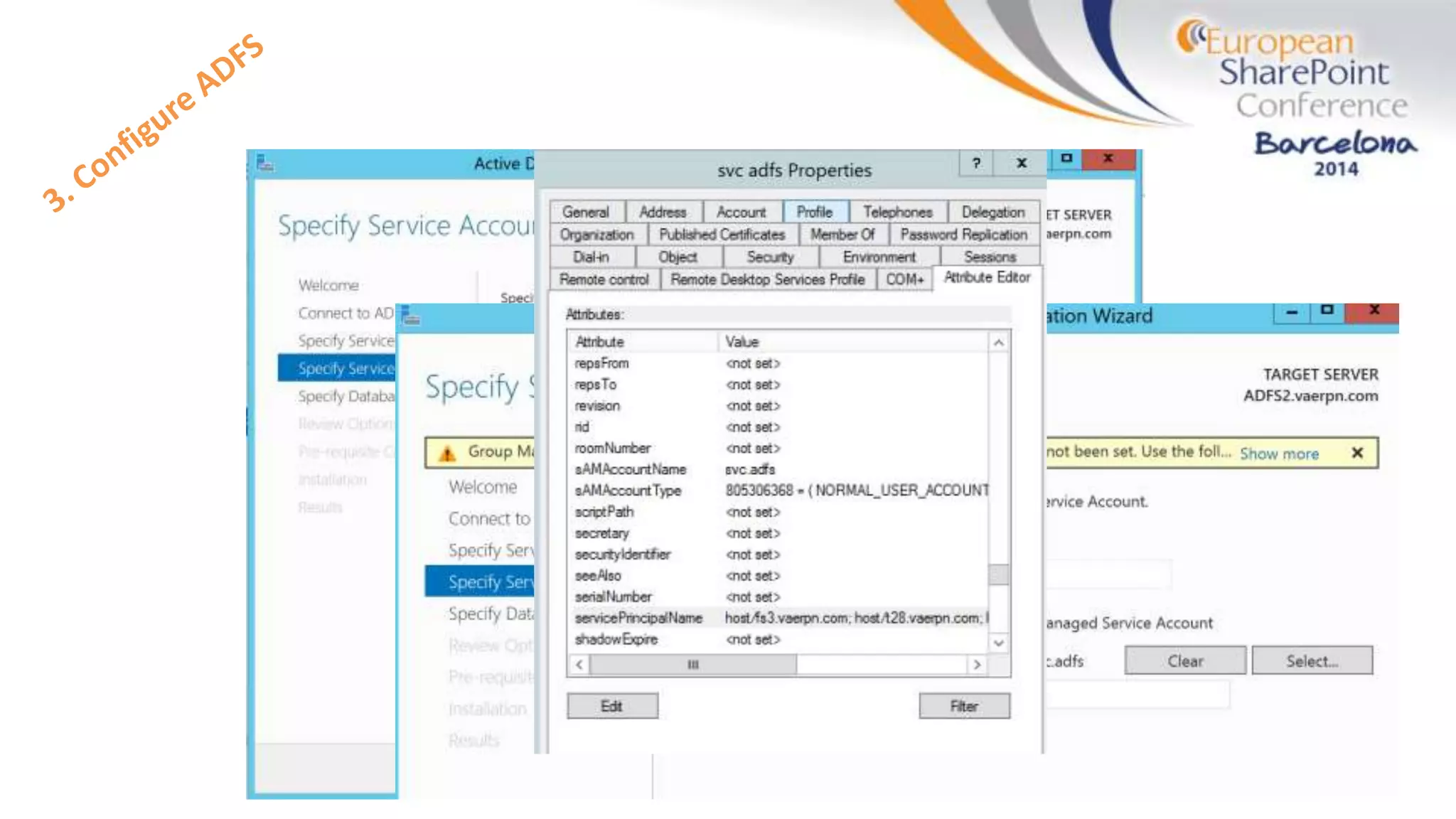
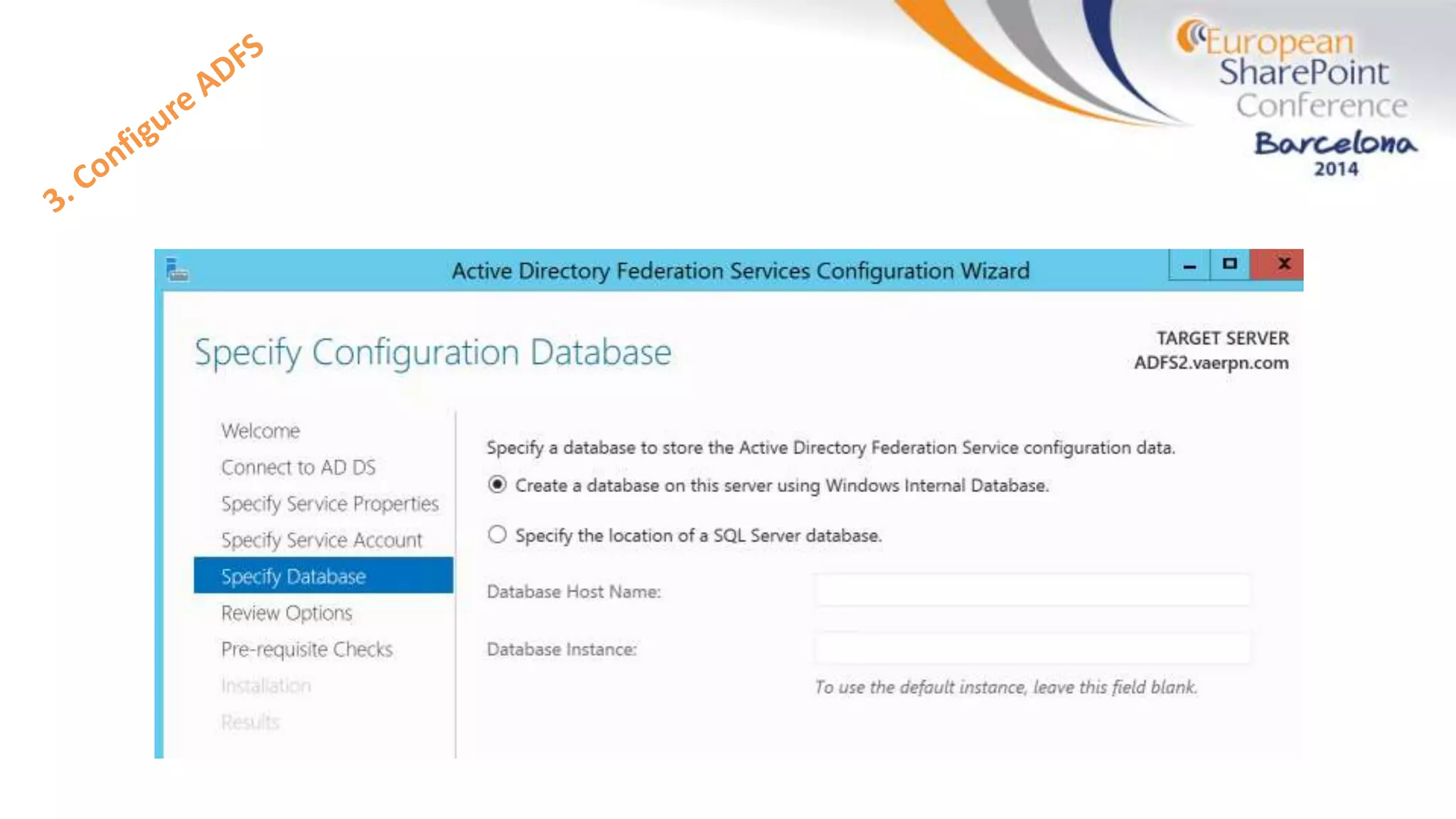
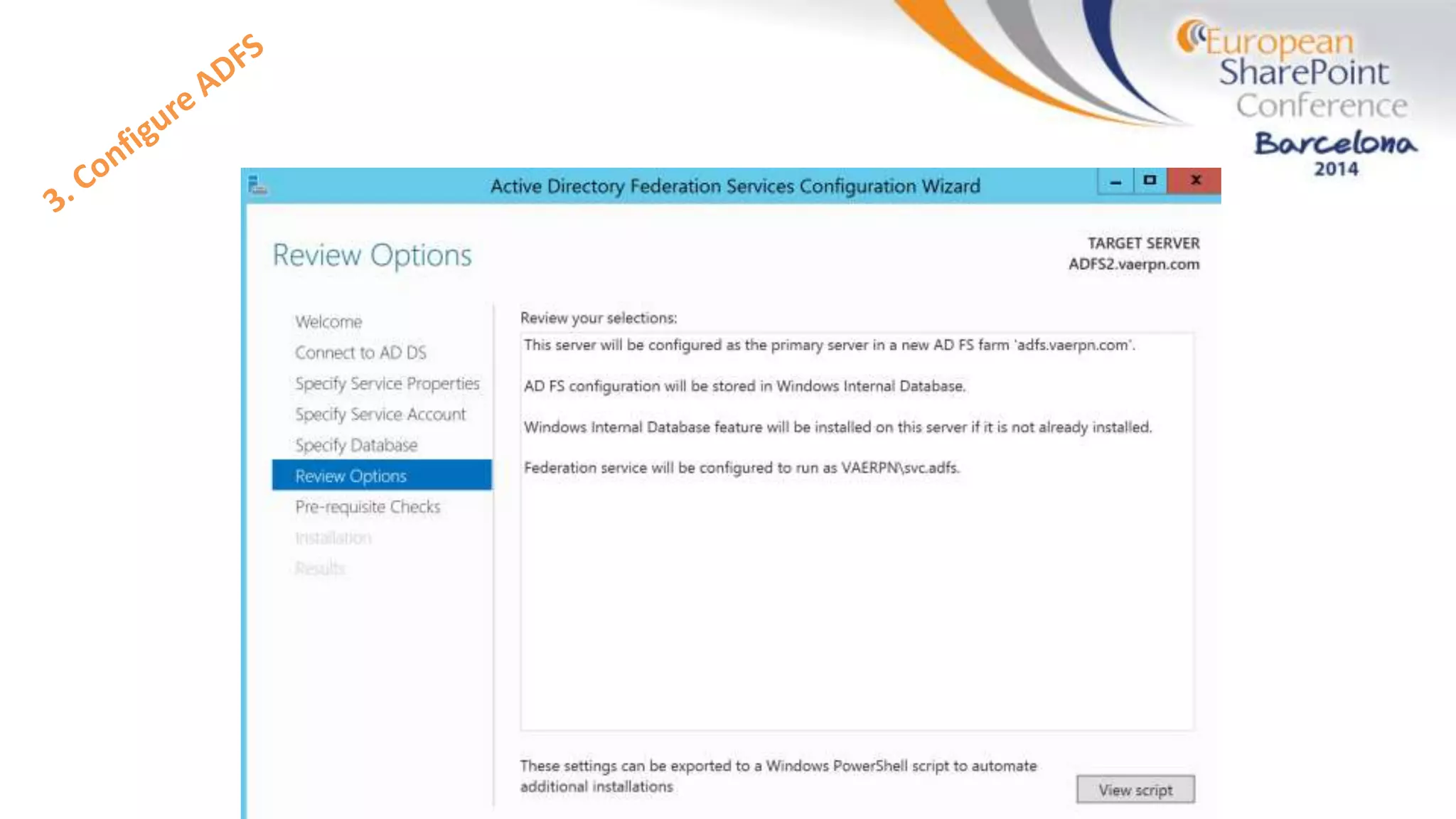
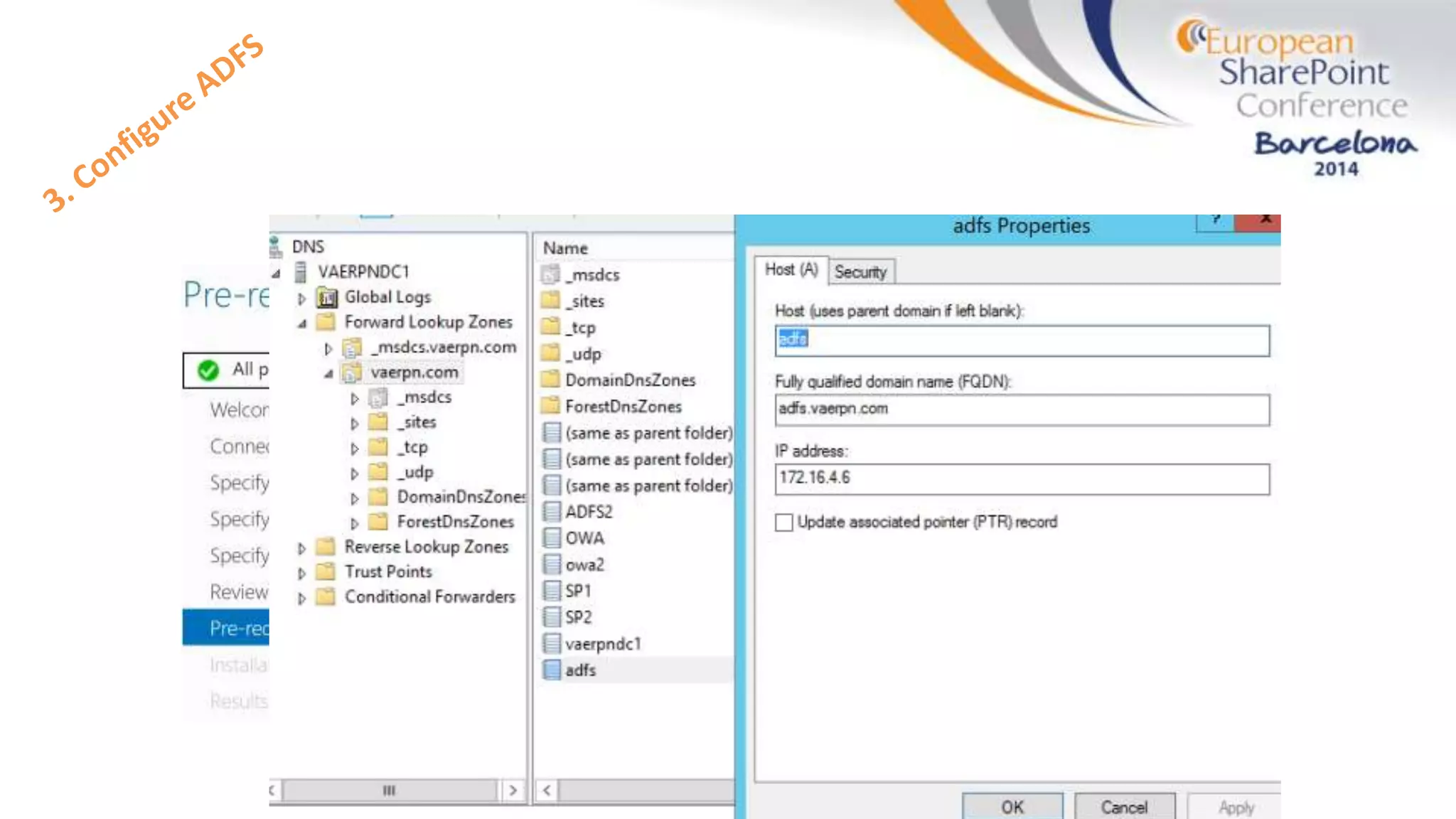
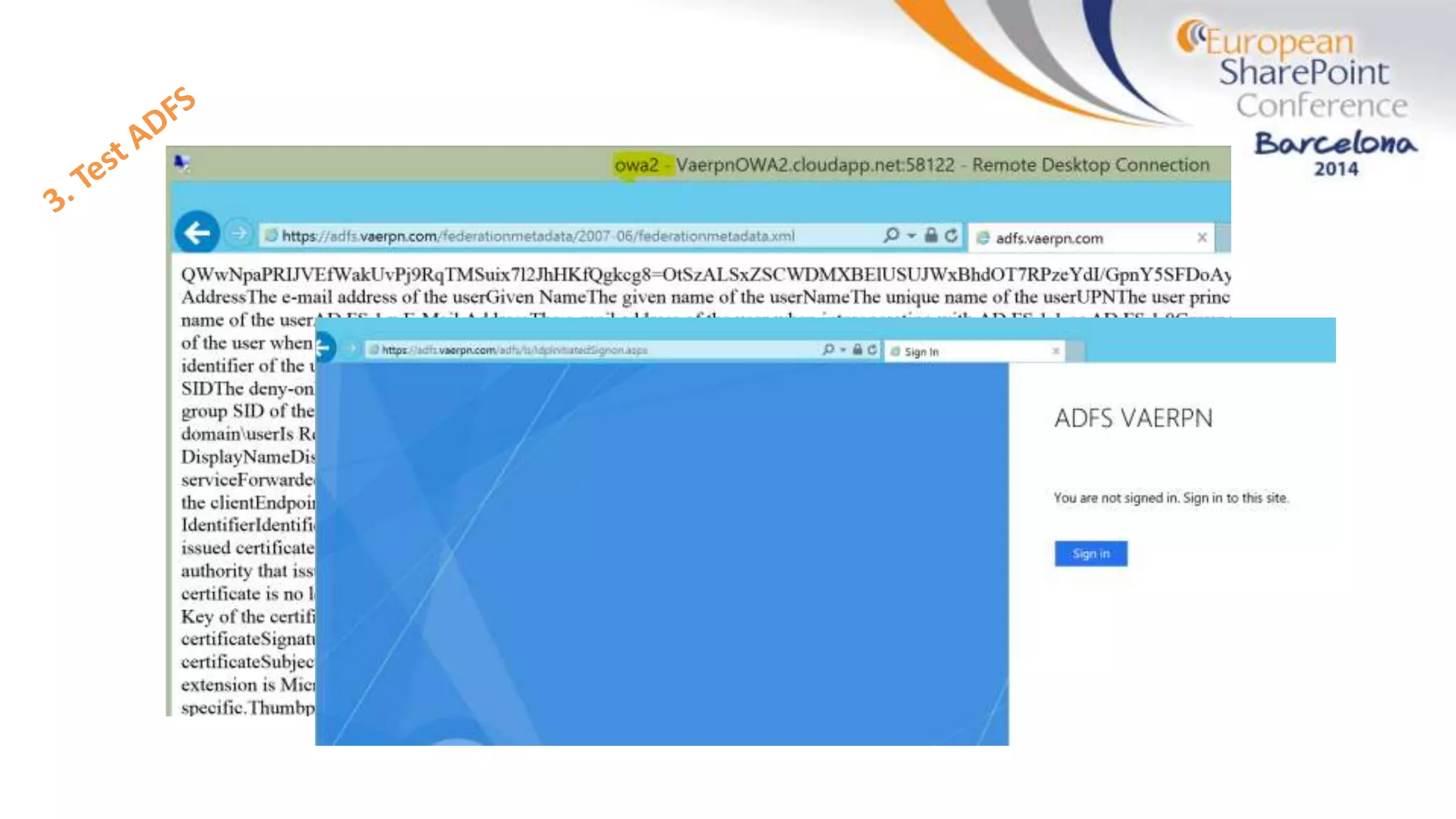
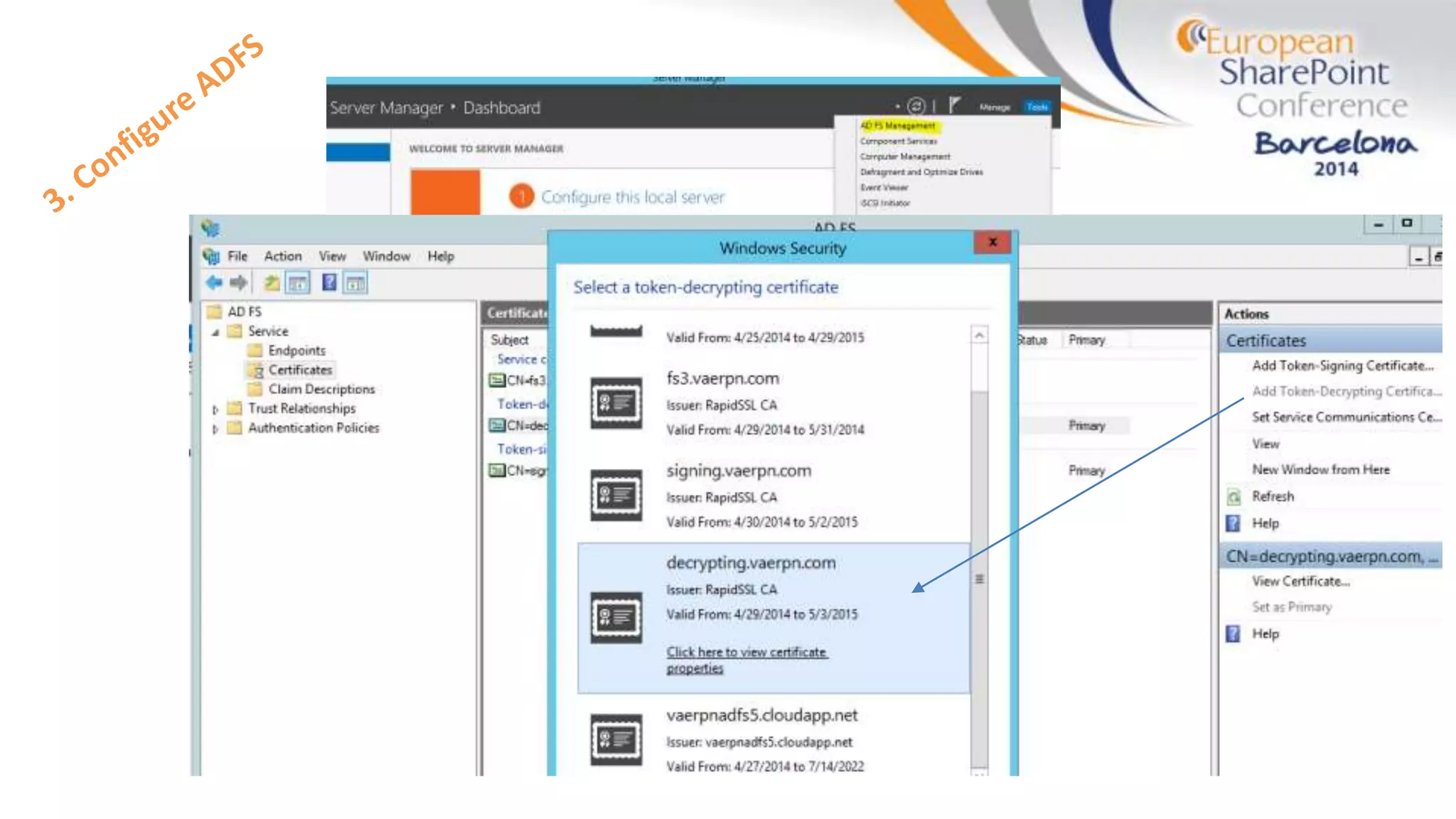
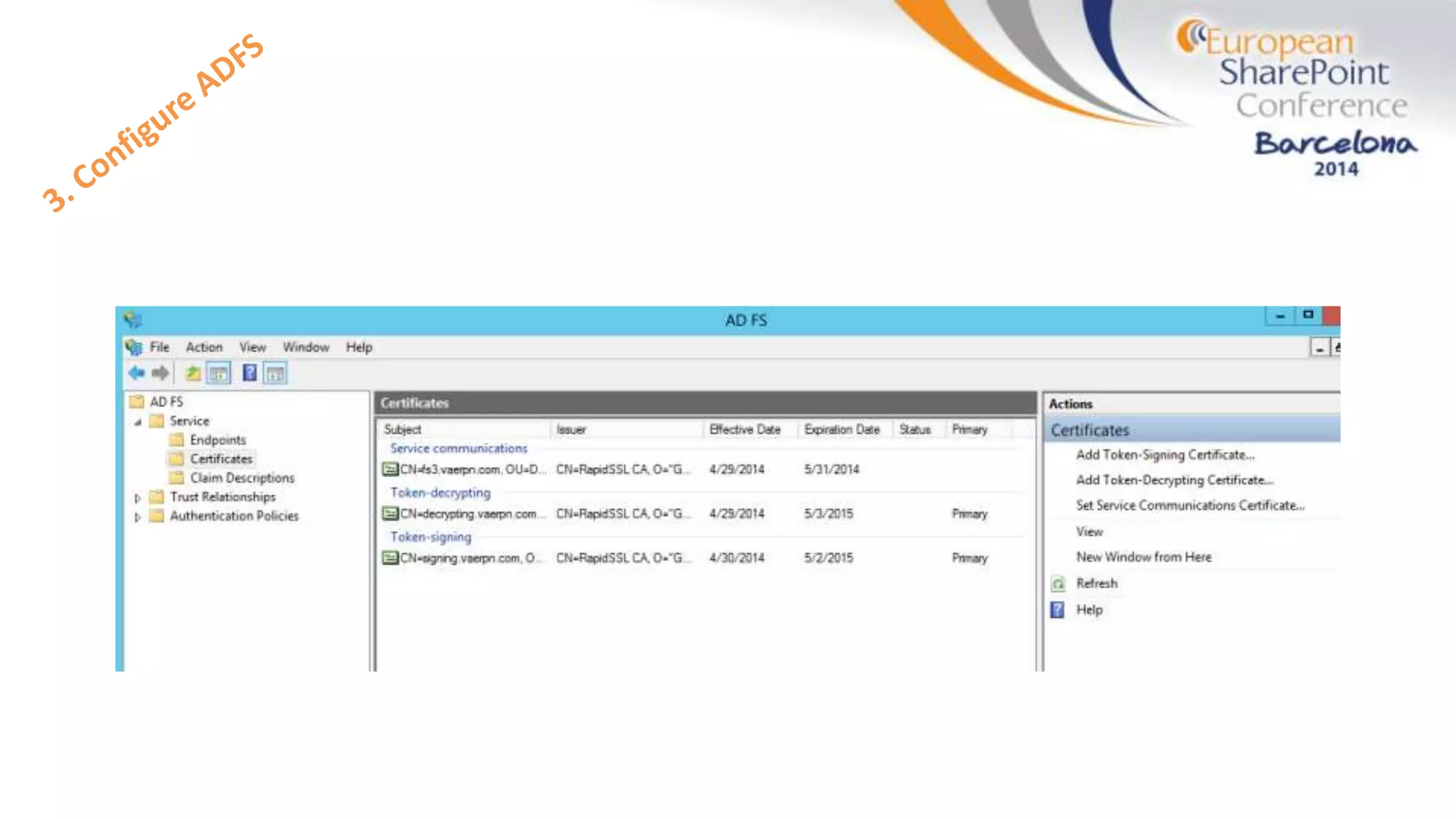
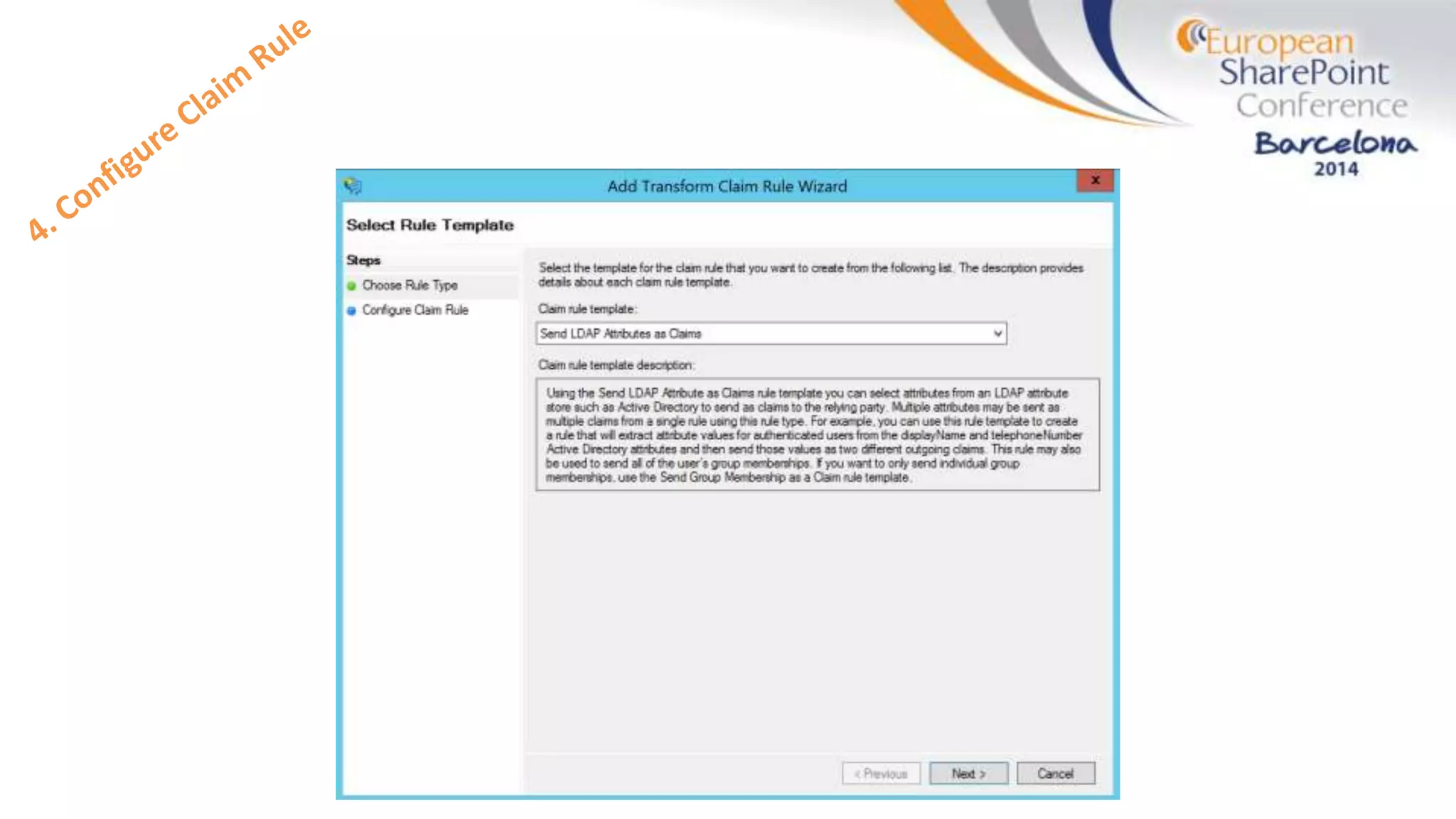
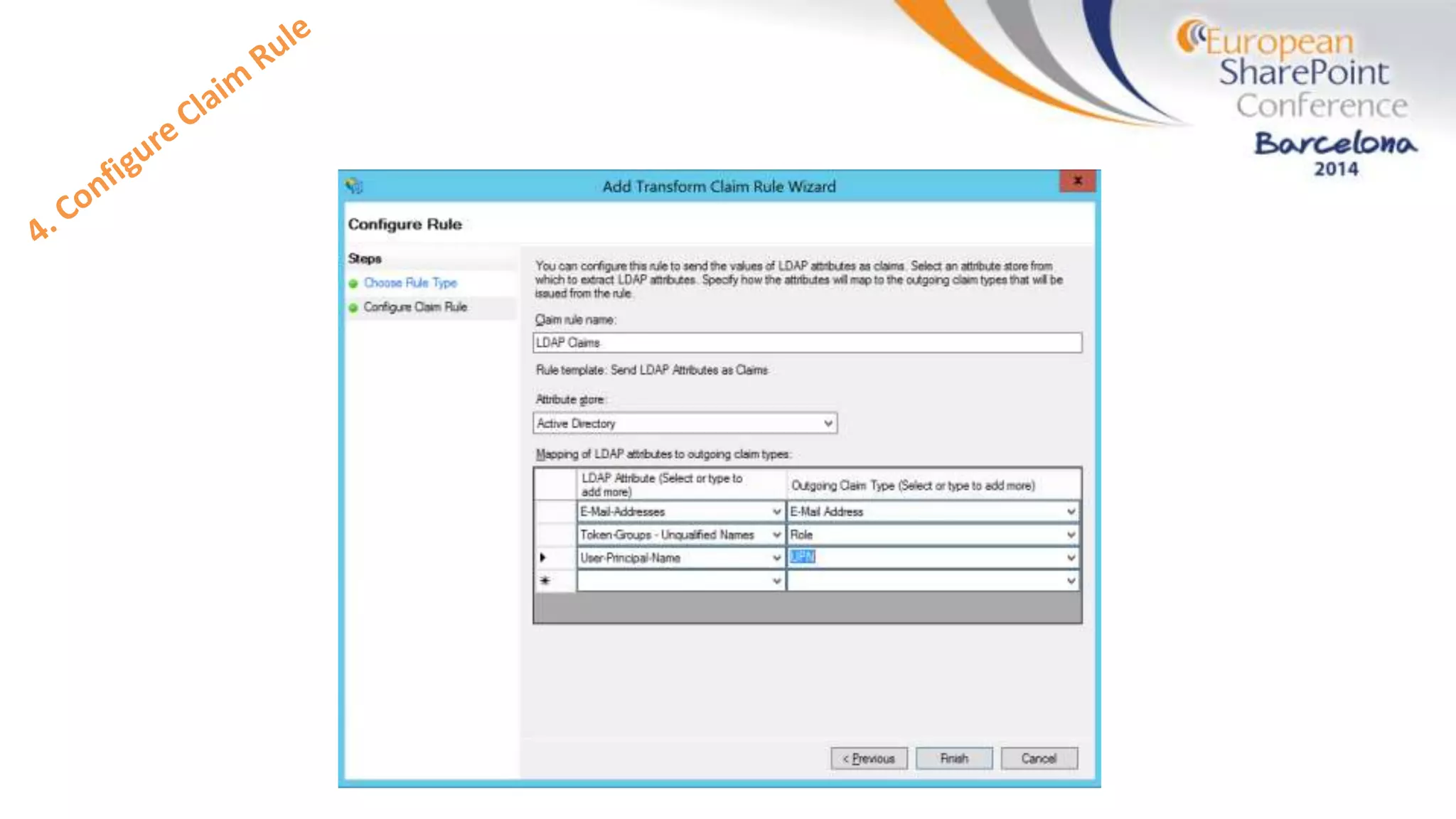
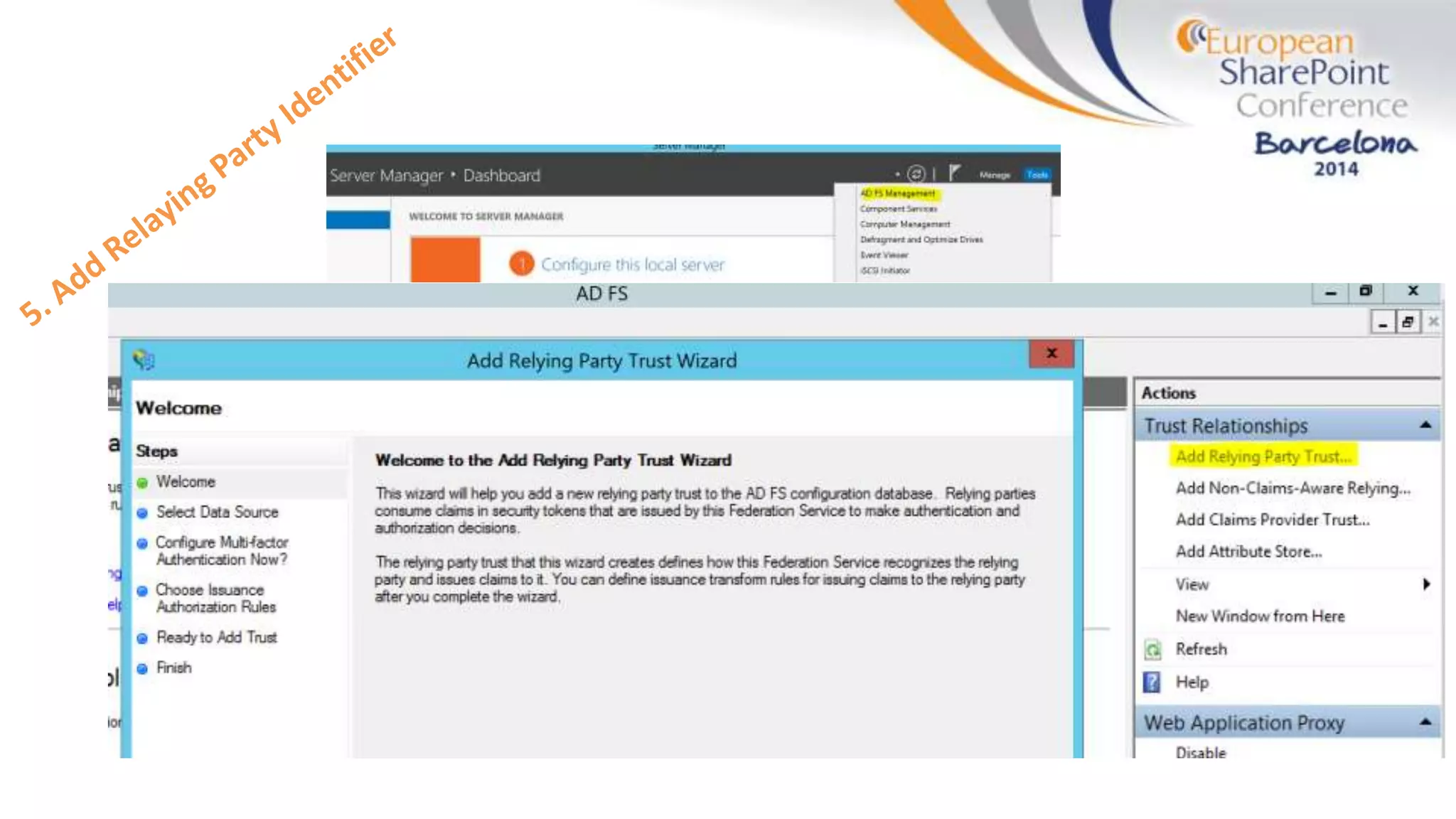
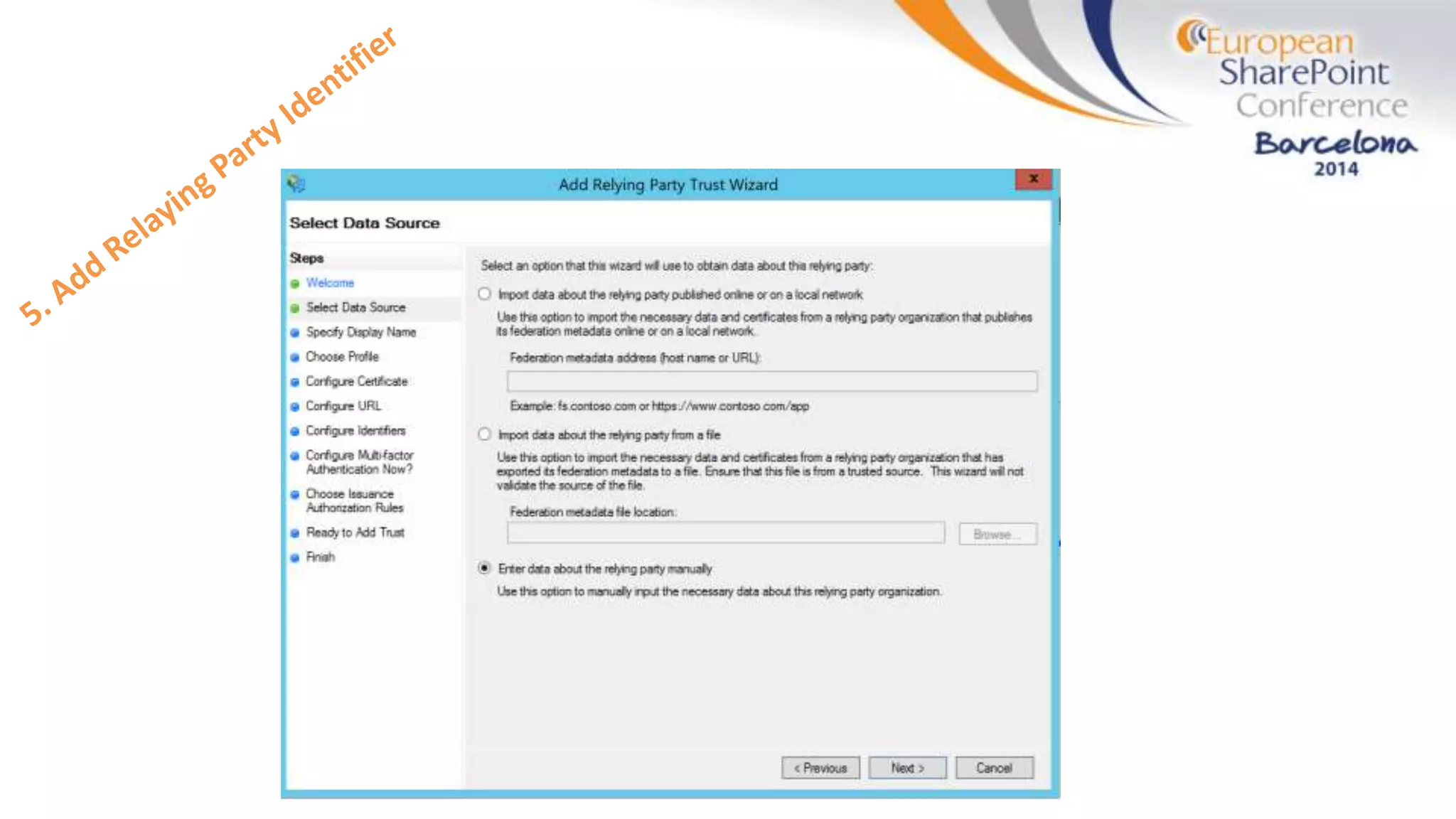
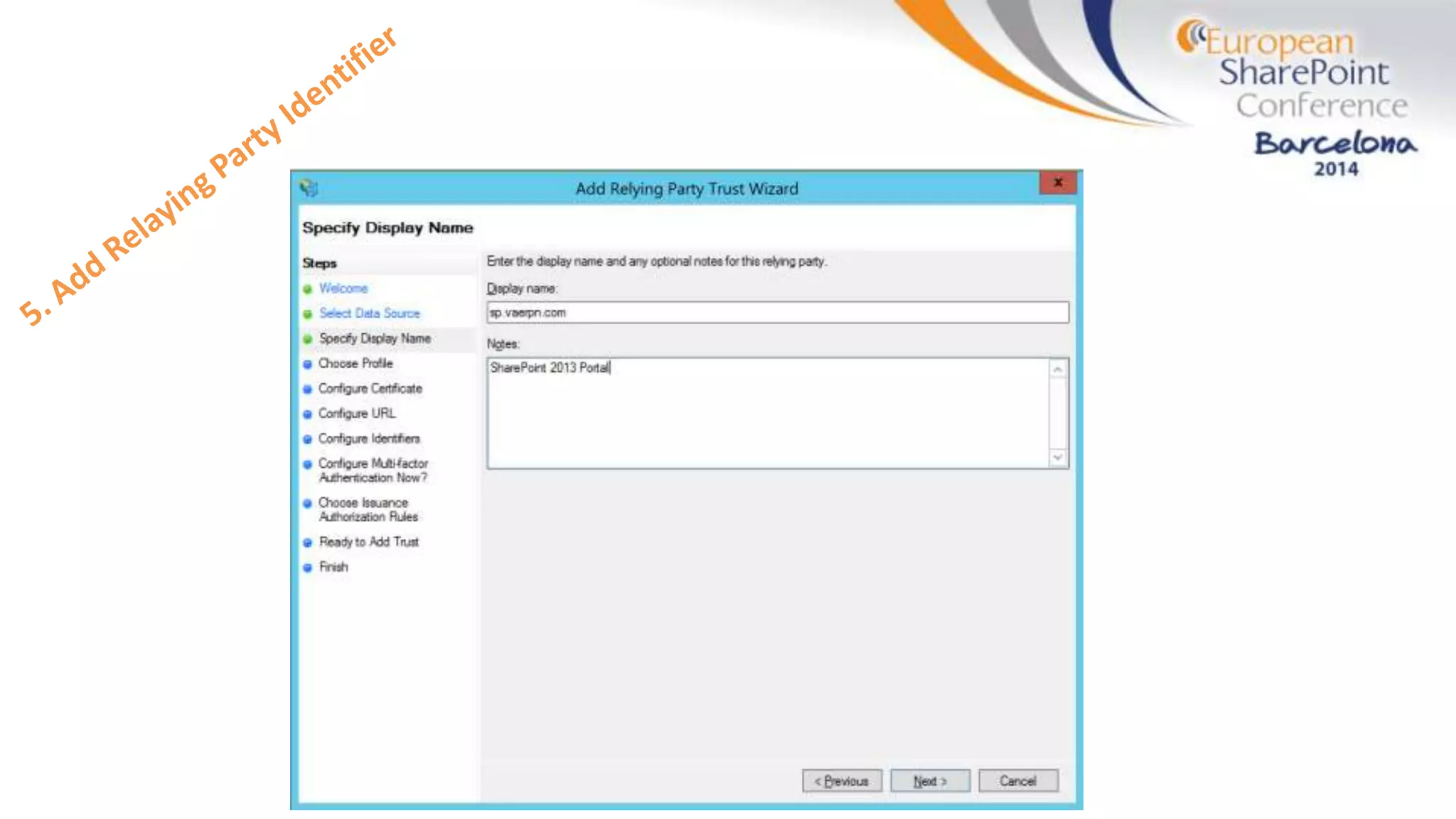
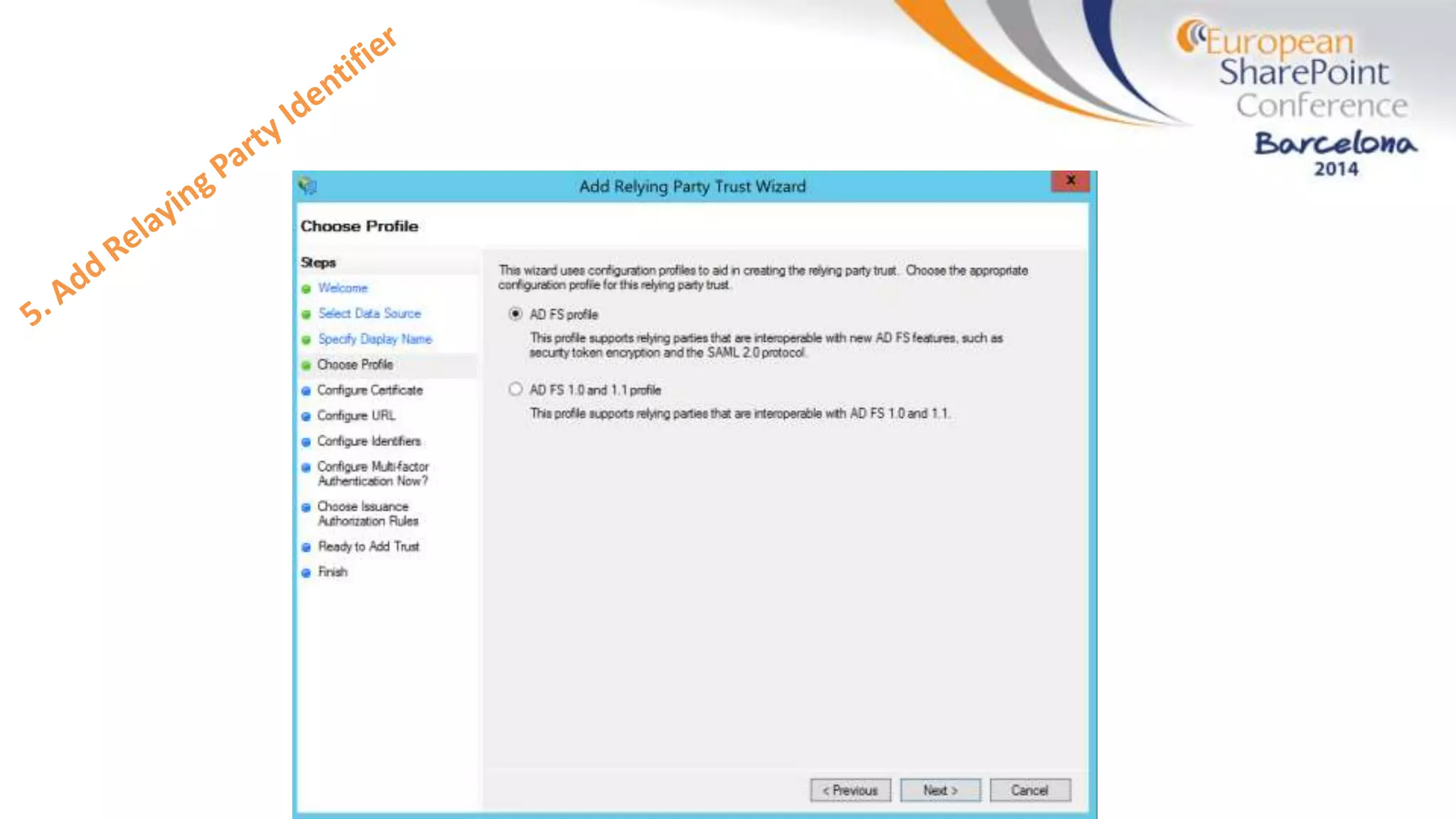
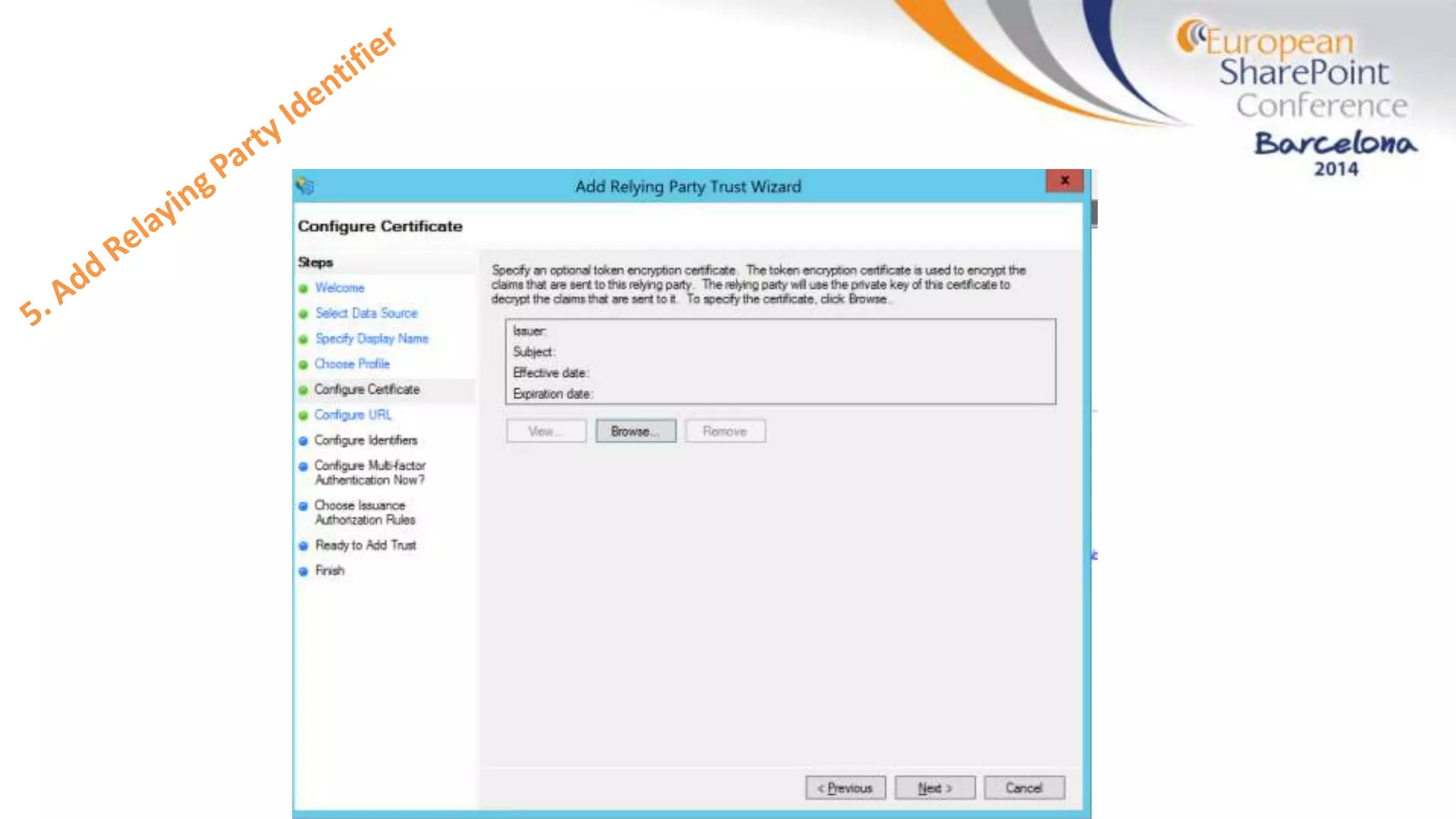
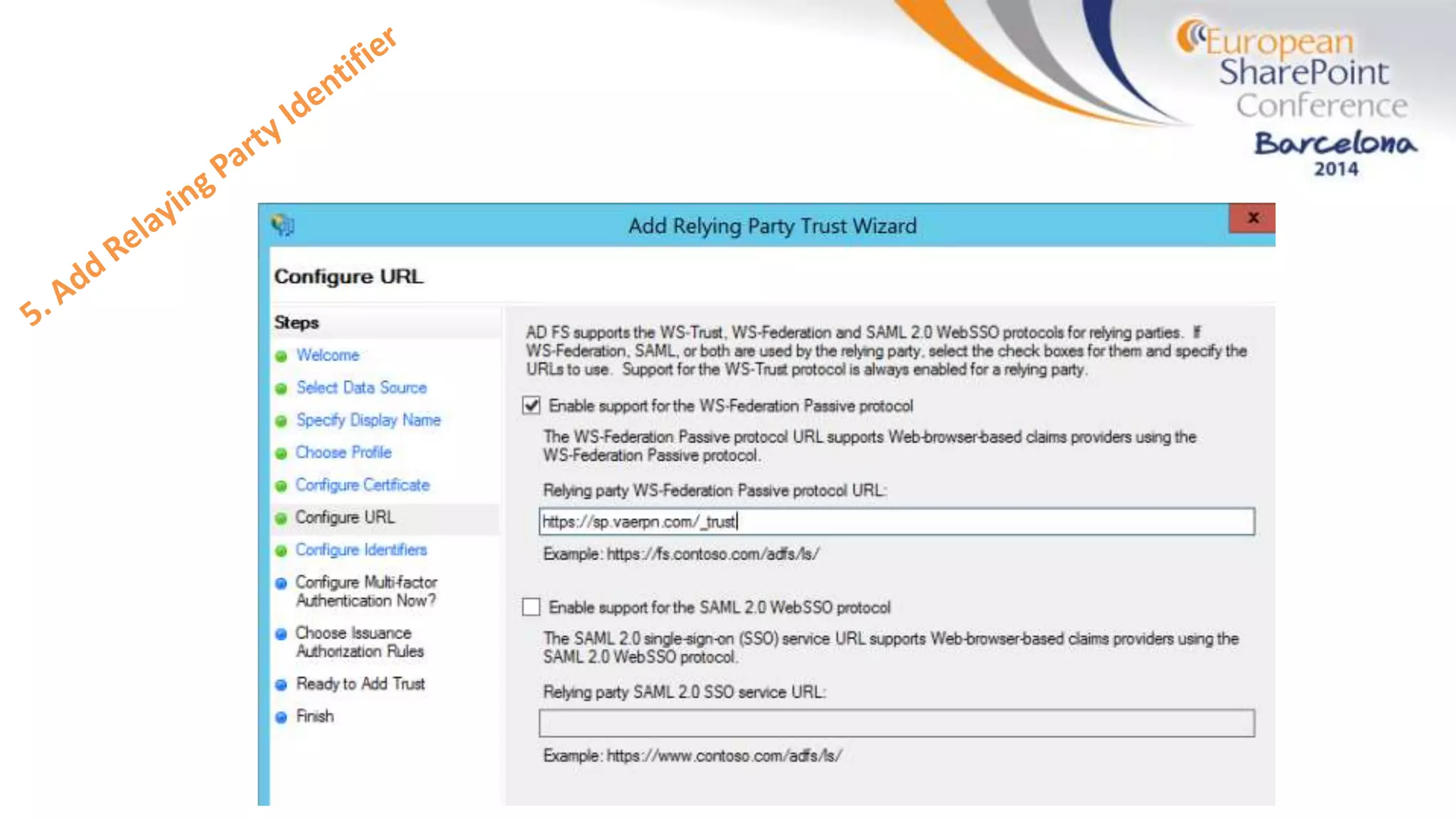
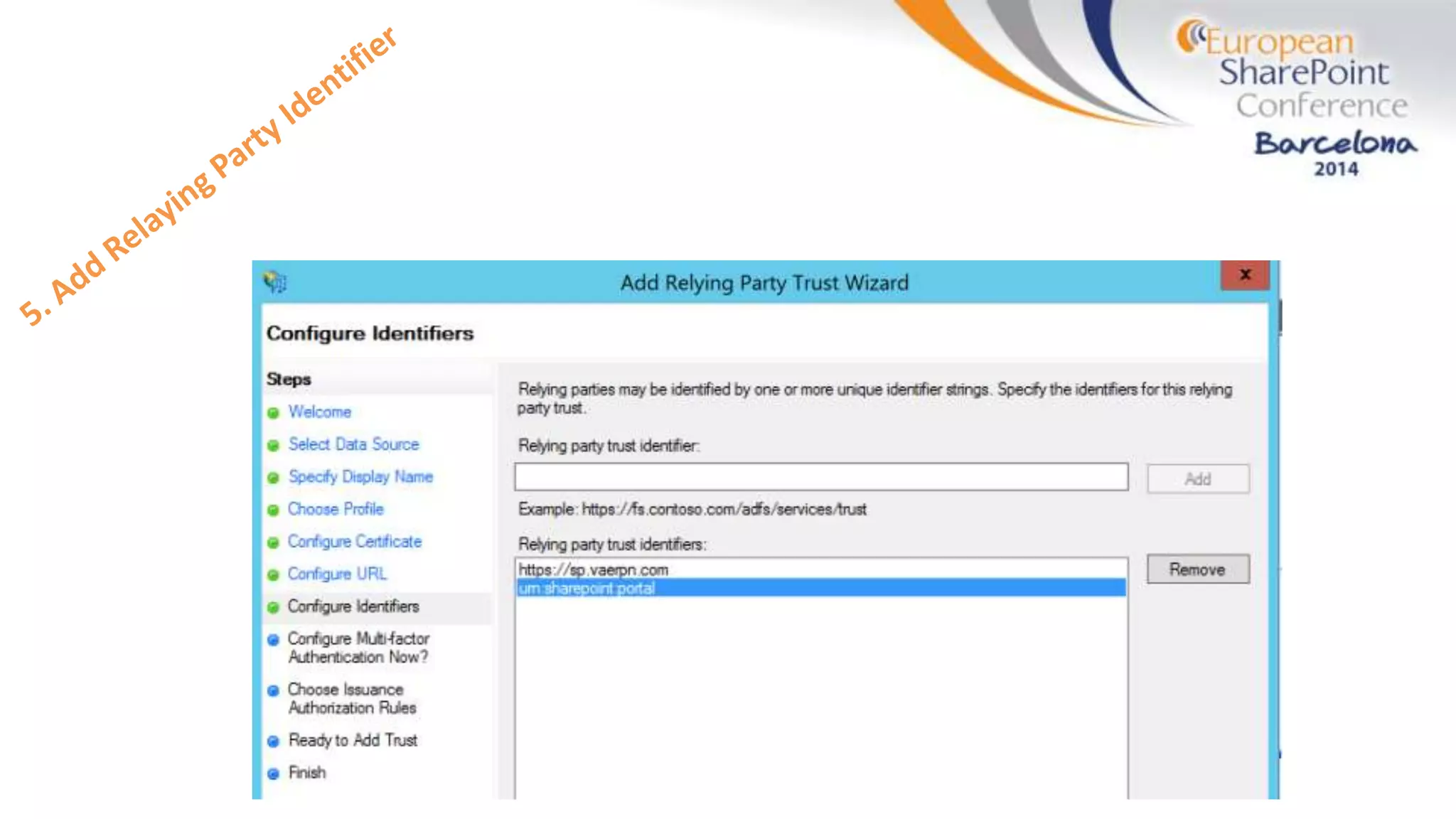
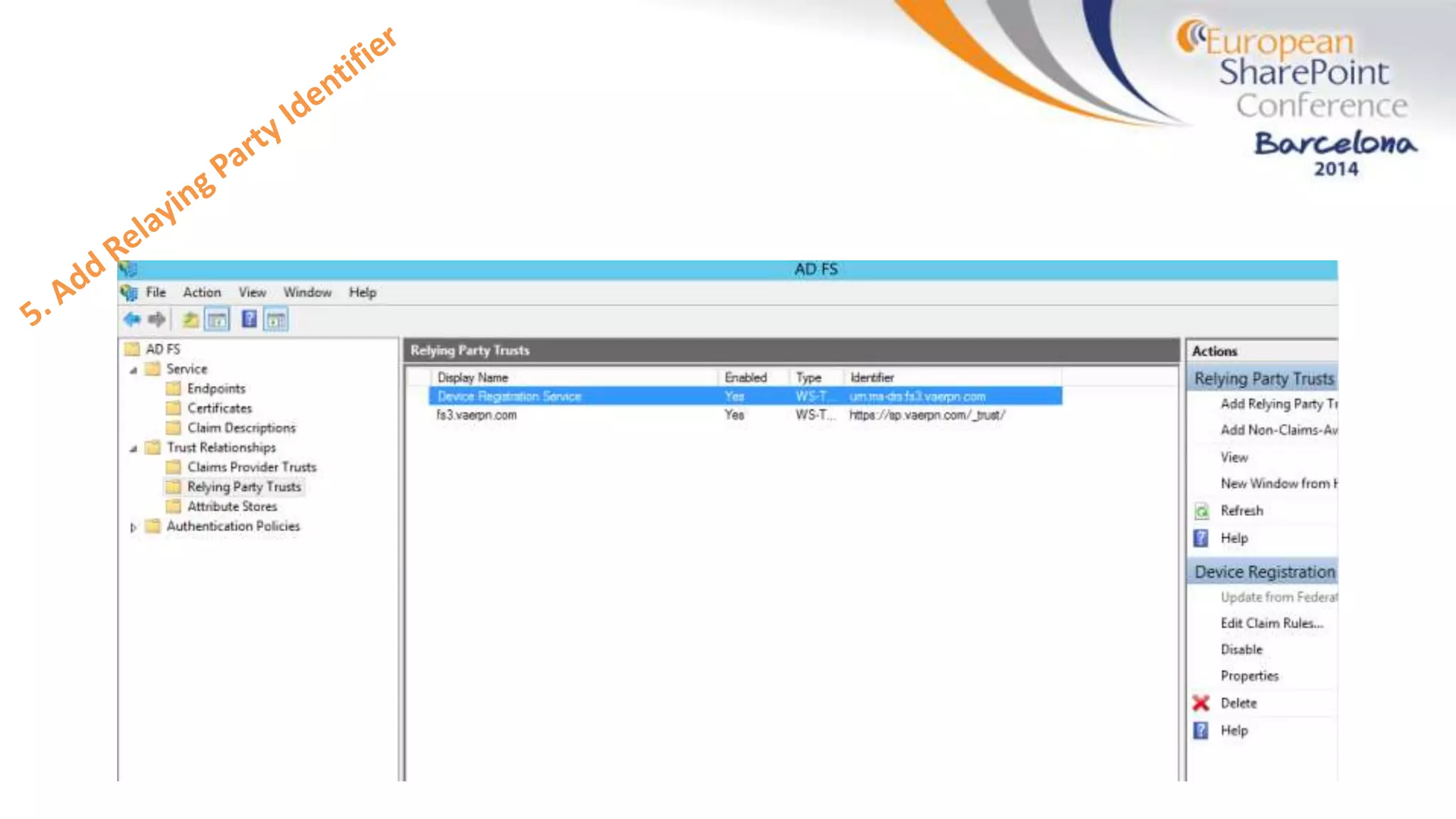
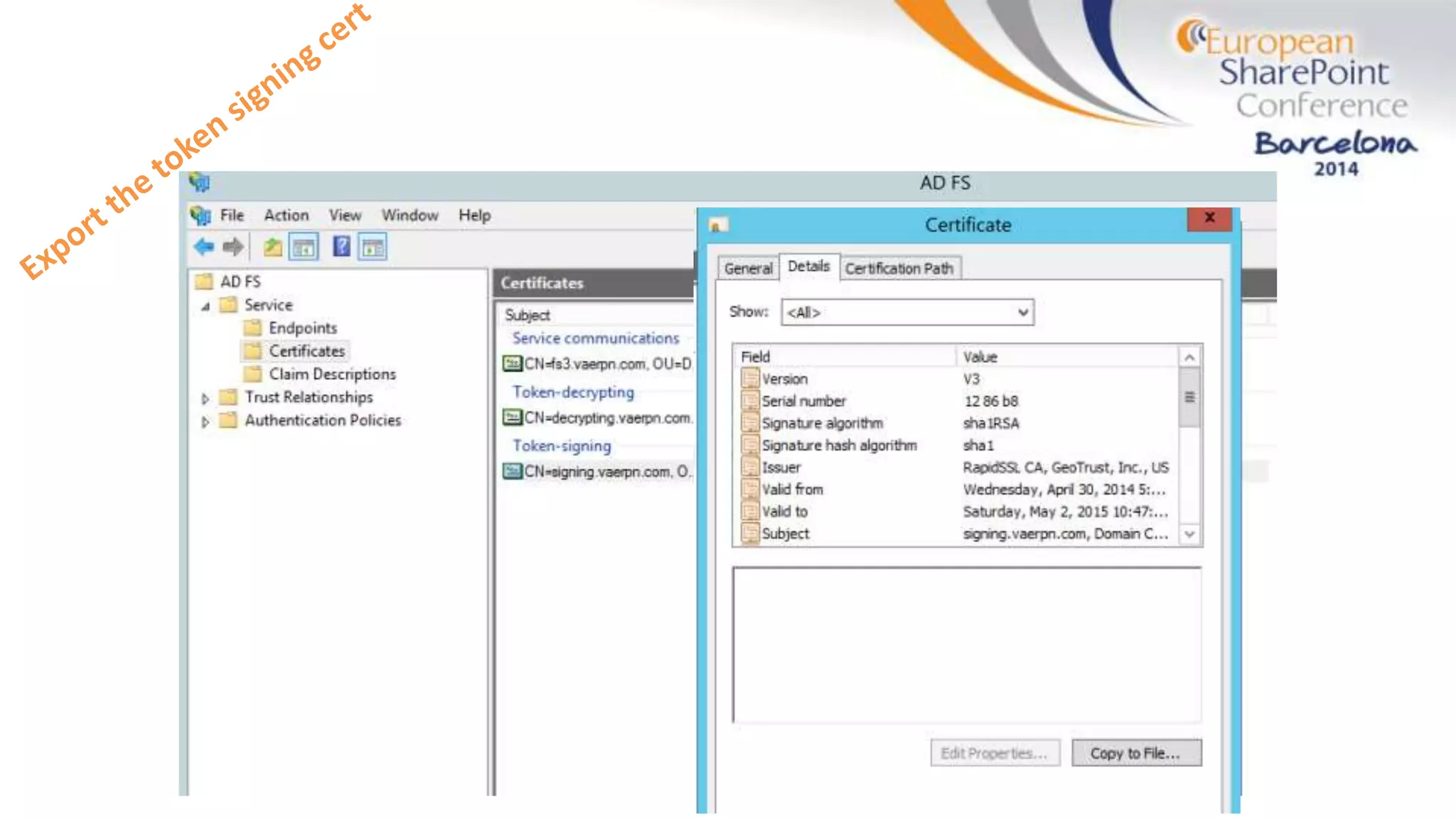
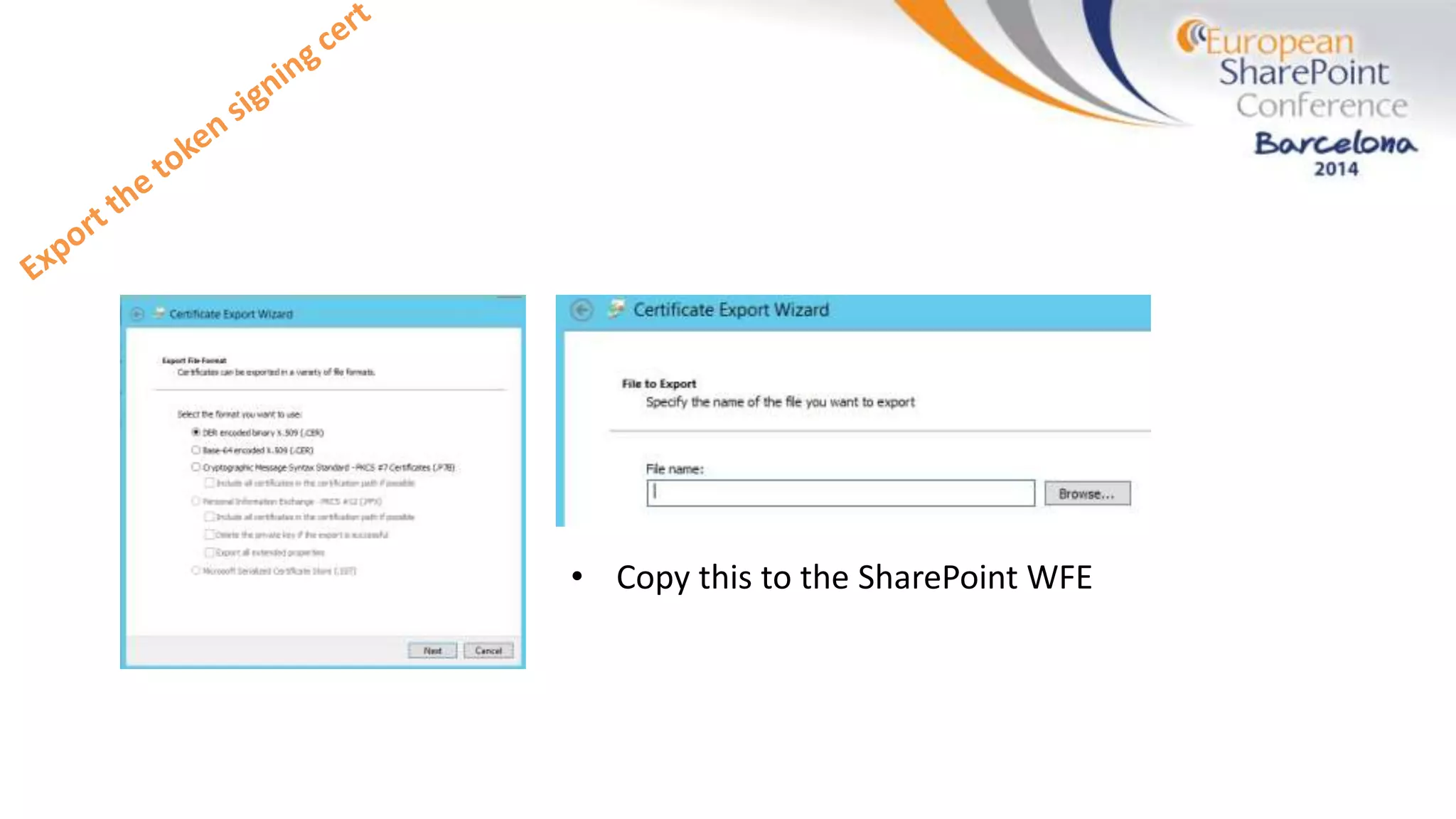
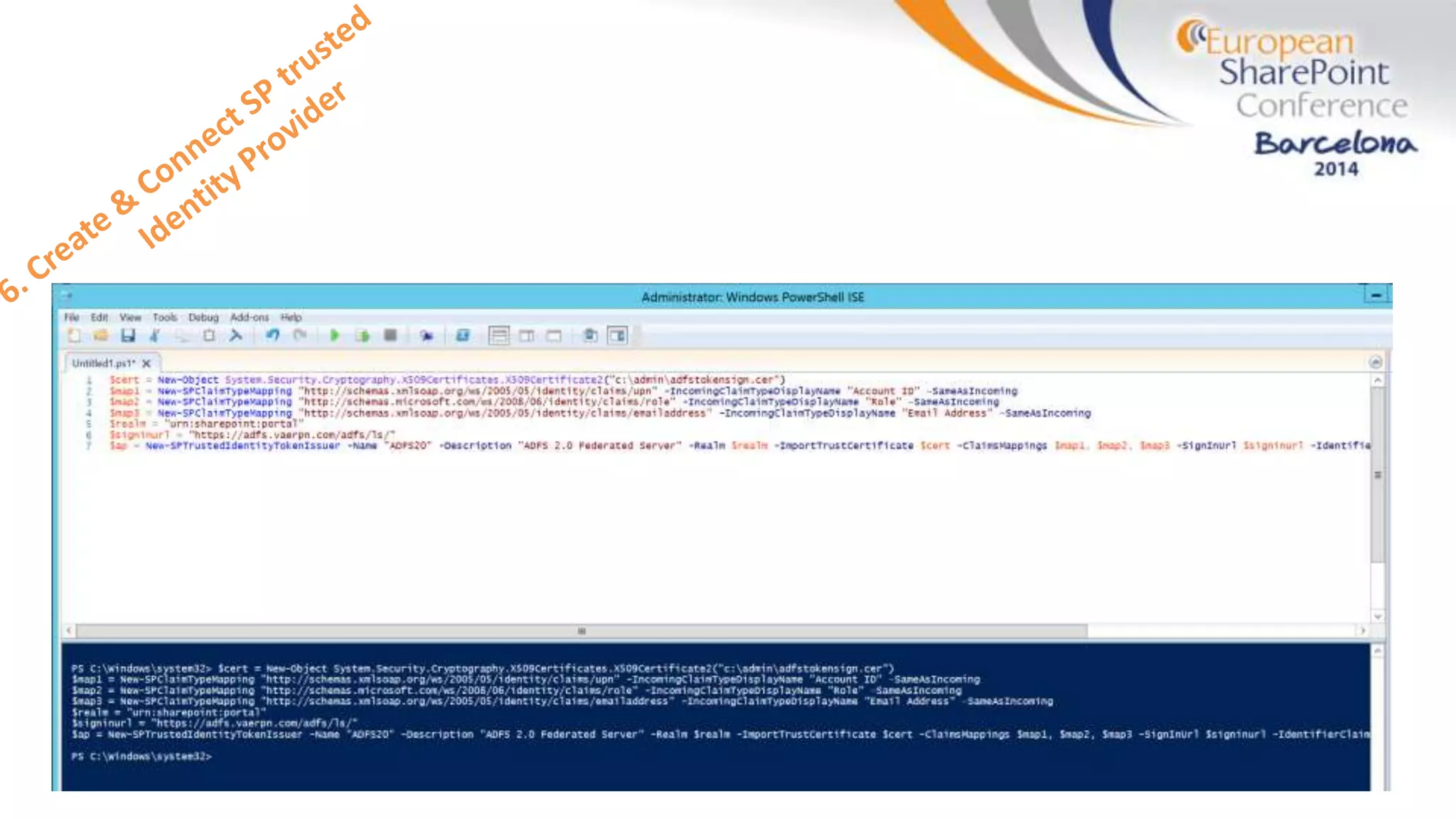
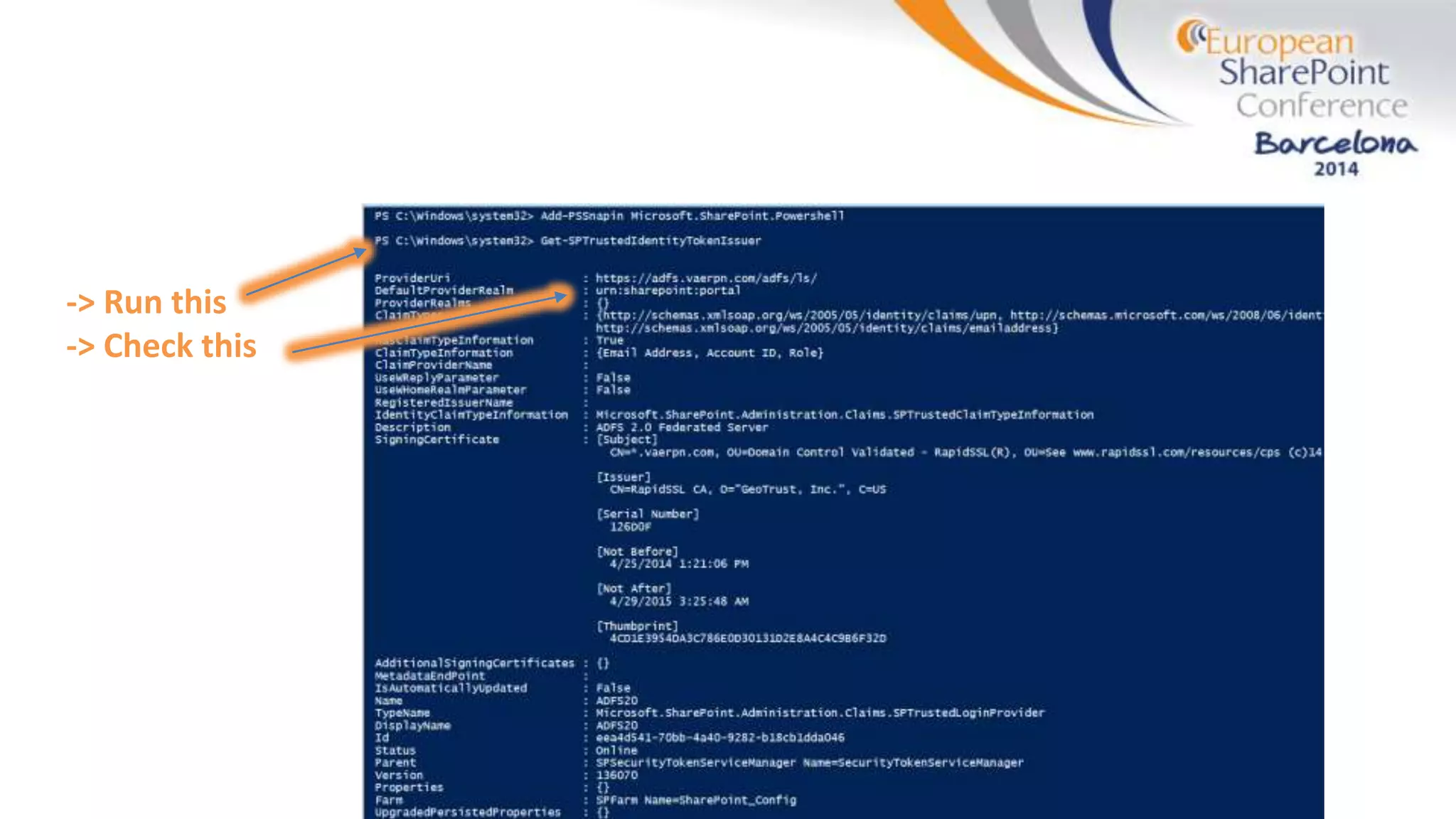
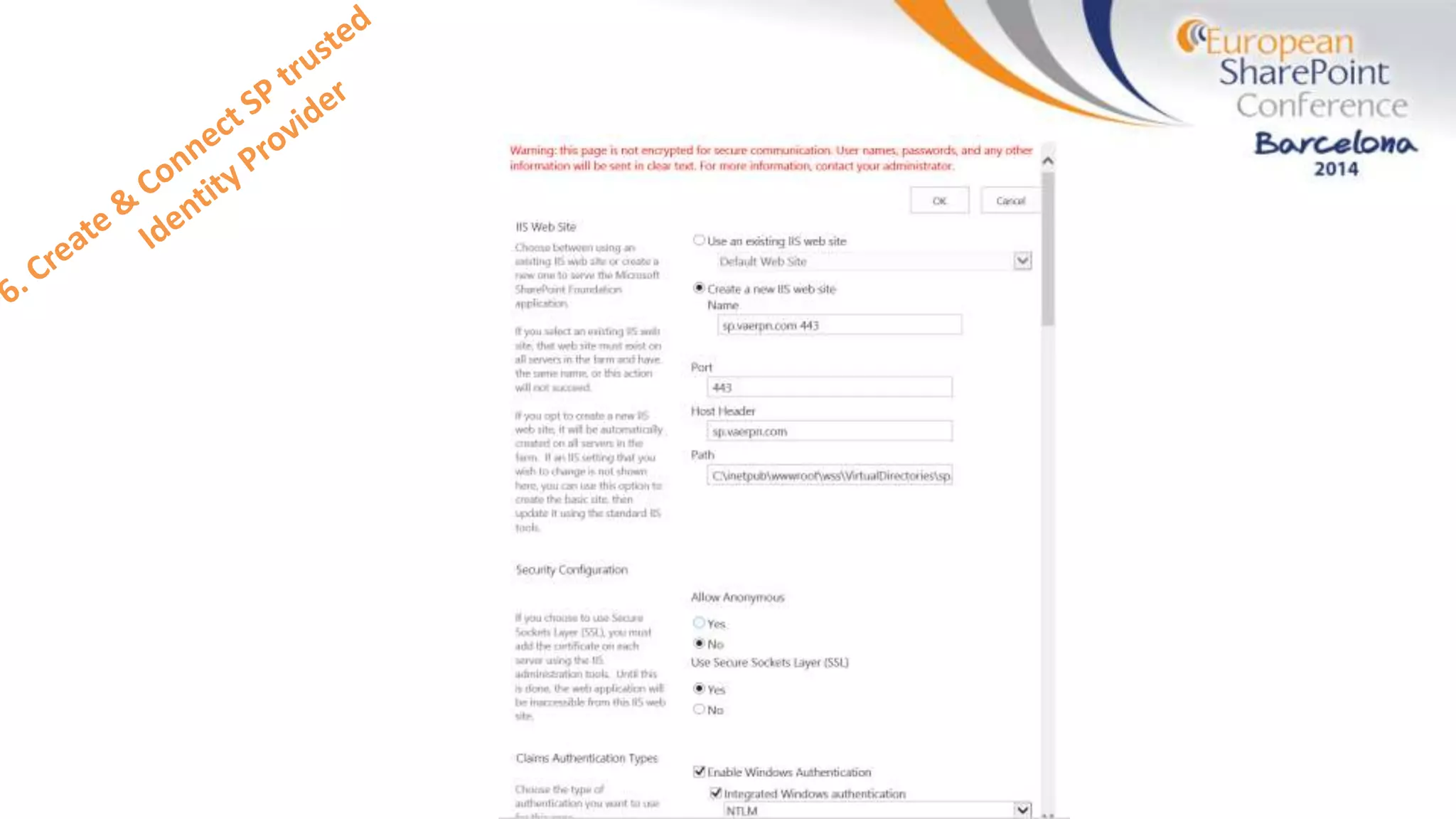
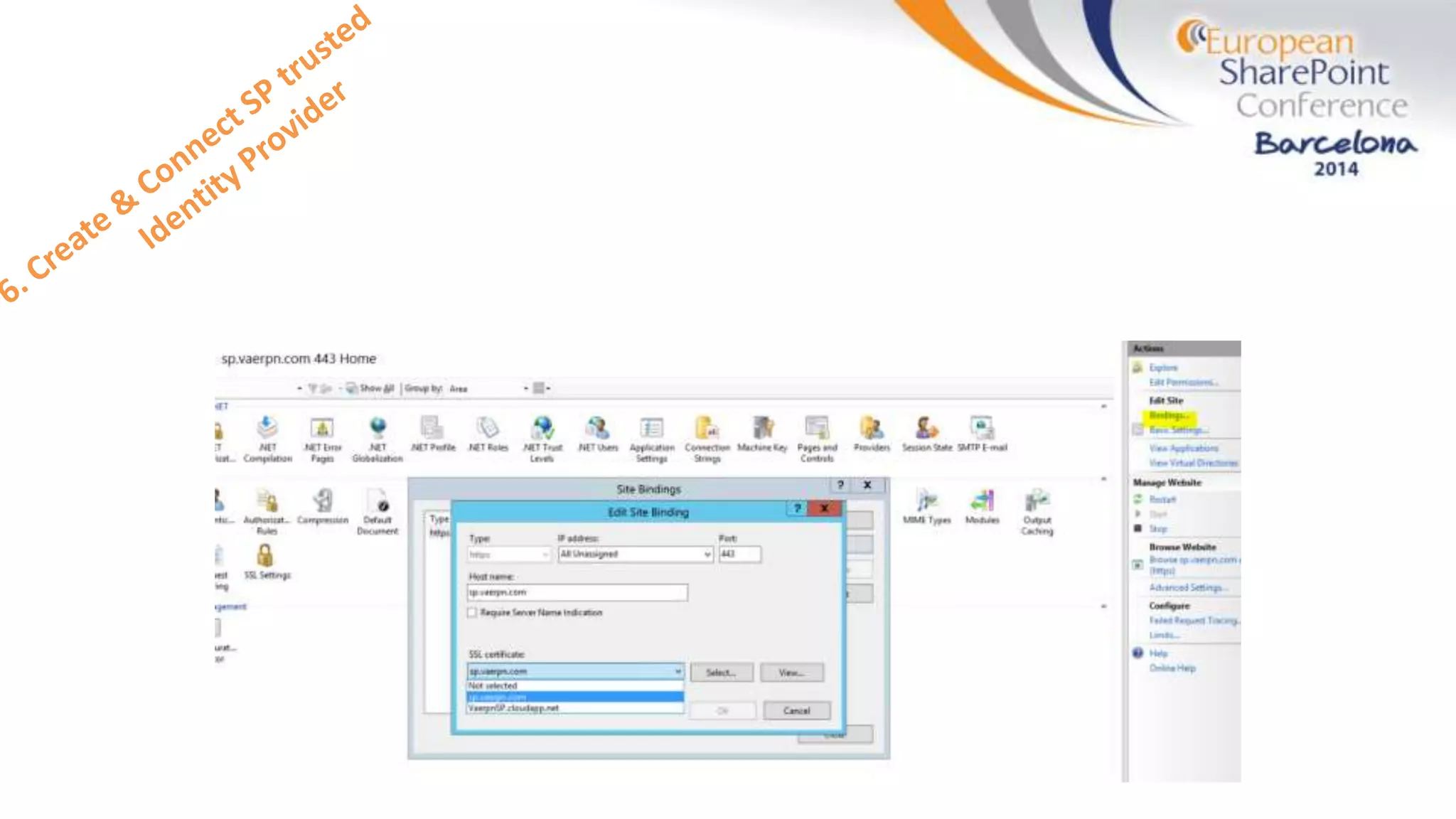
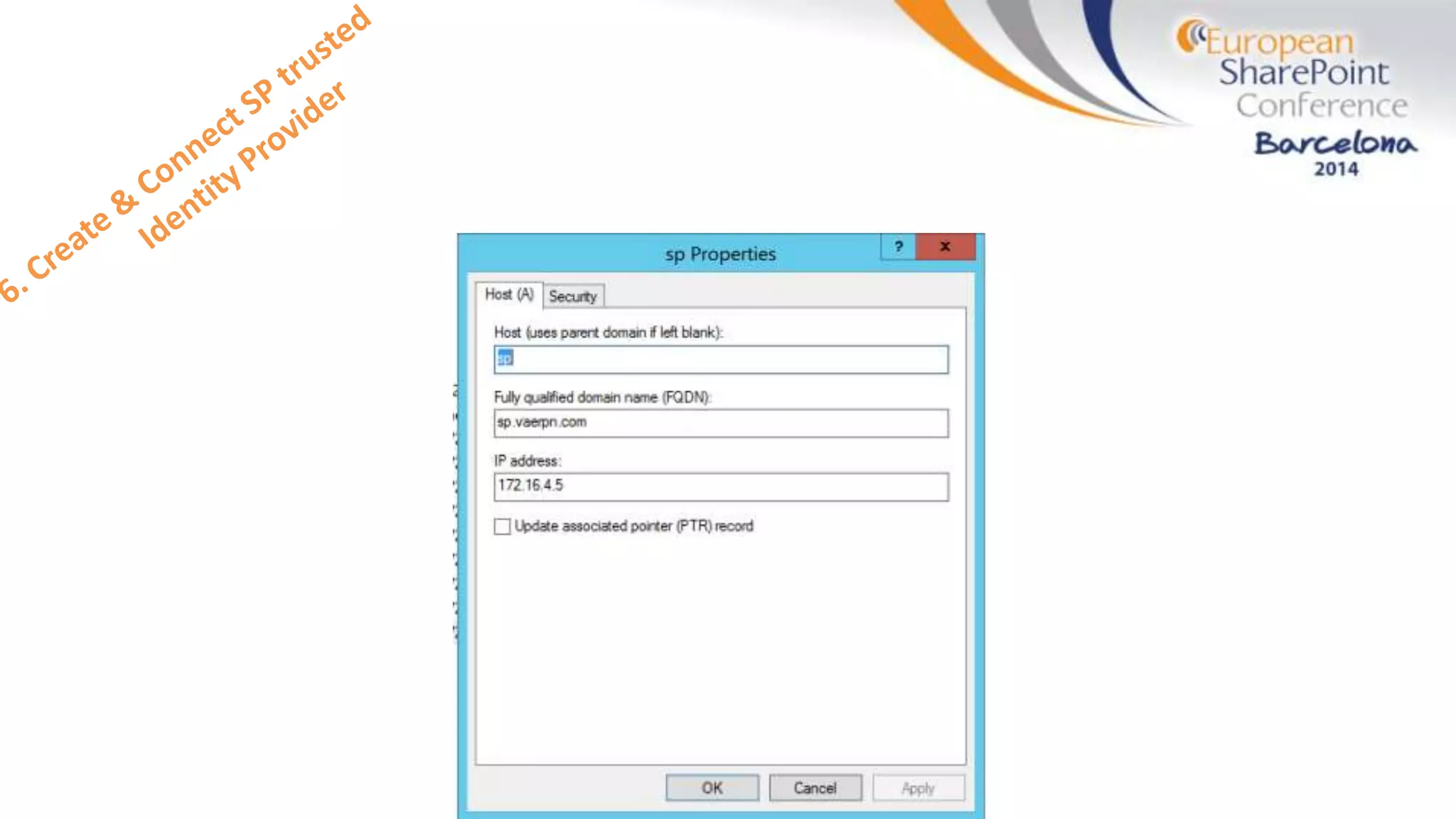
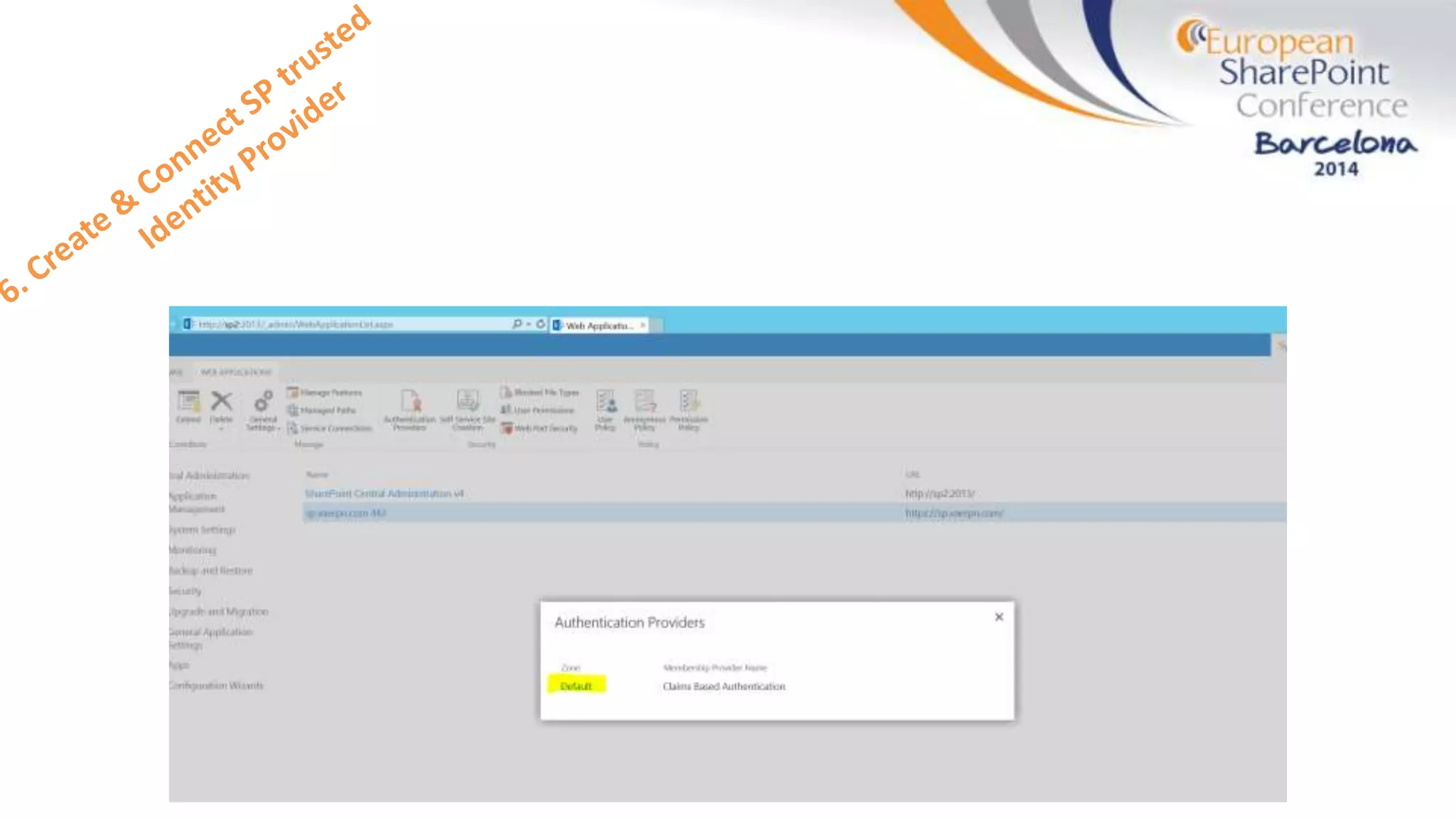
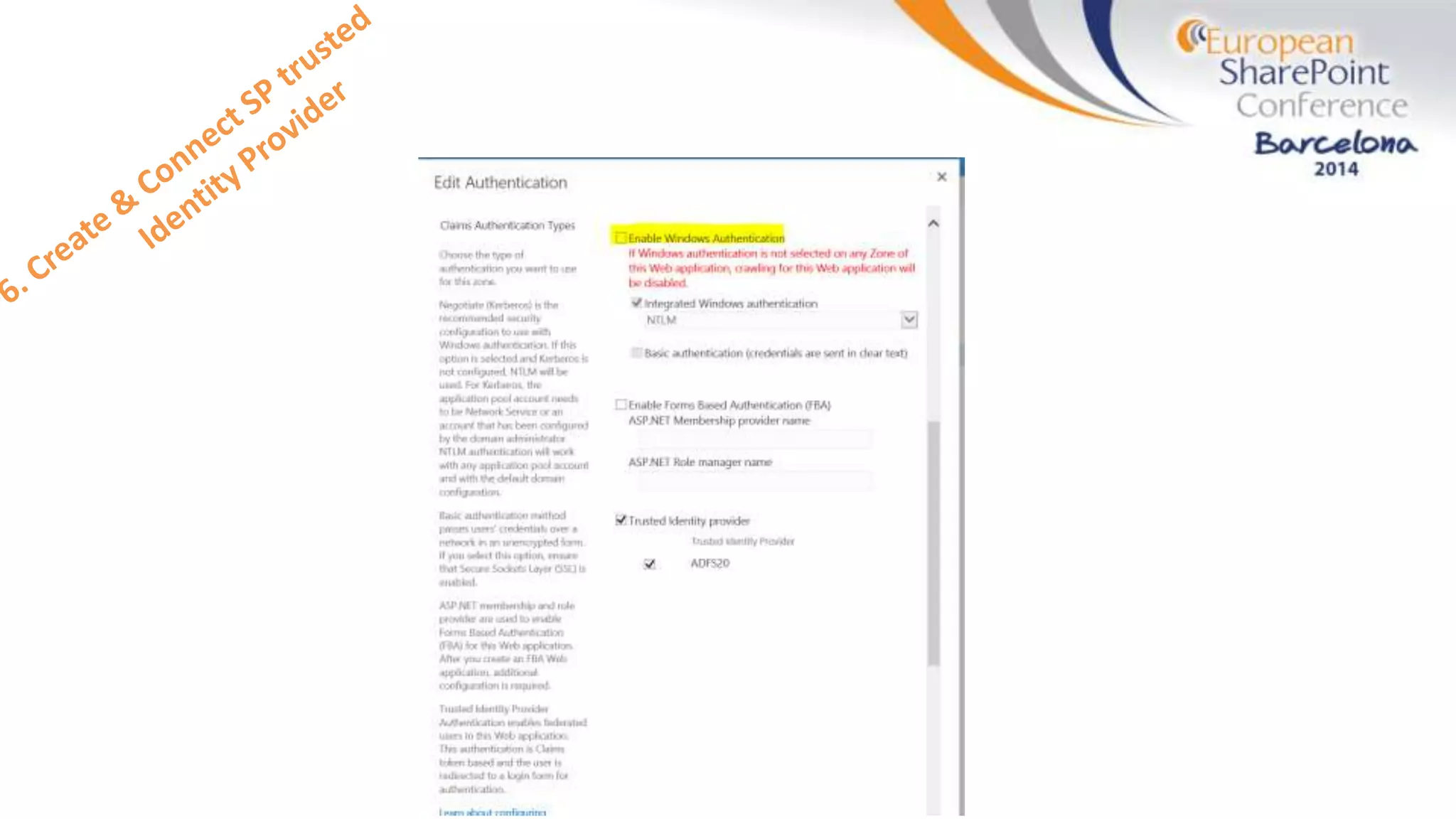
The document discusses the implementation of ADFS and claims-based authentication in SharePoint 2013, highlighting the limitations of traditional authentication mechanisms. It explains claims-based identity as an abstraction layer with claims being authoritative statements stored in security tokens, and outlines the ADFS setup process for SharePoint. The author emphasizes the need for public certificates and proper configuration to ensure a functional environment.