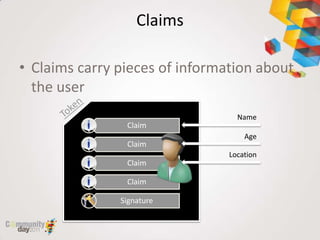
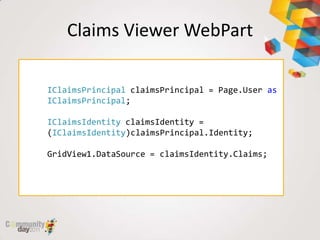
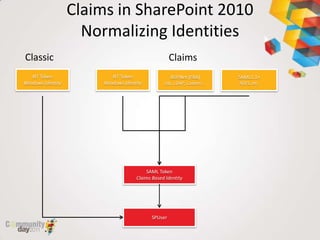
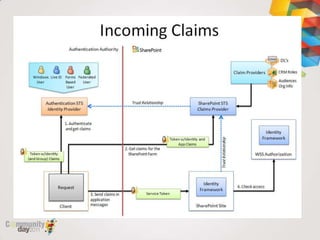
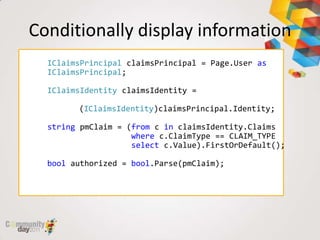
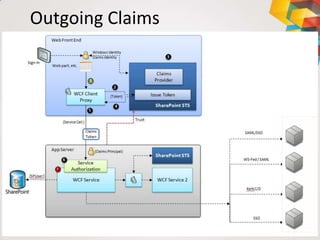
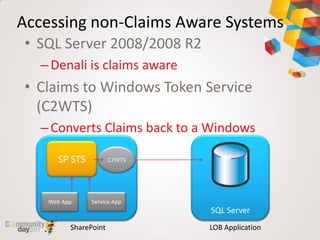
This document provides an overview of claim based authentication in SharePoint 2010 from a developer's perspective. It discusses key claim based terminology, how claims work in SharePoint 2010 including normalizing identities and configuring claims providers. It also covers development tasks with claims such as augmenting claims and resolving claims in the people picker. Finally, it discusses trusted identity providers such as Active Directory Federation Services, Windows Live ID, and OpenID.