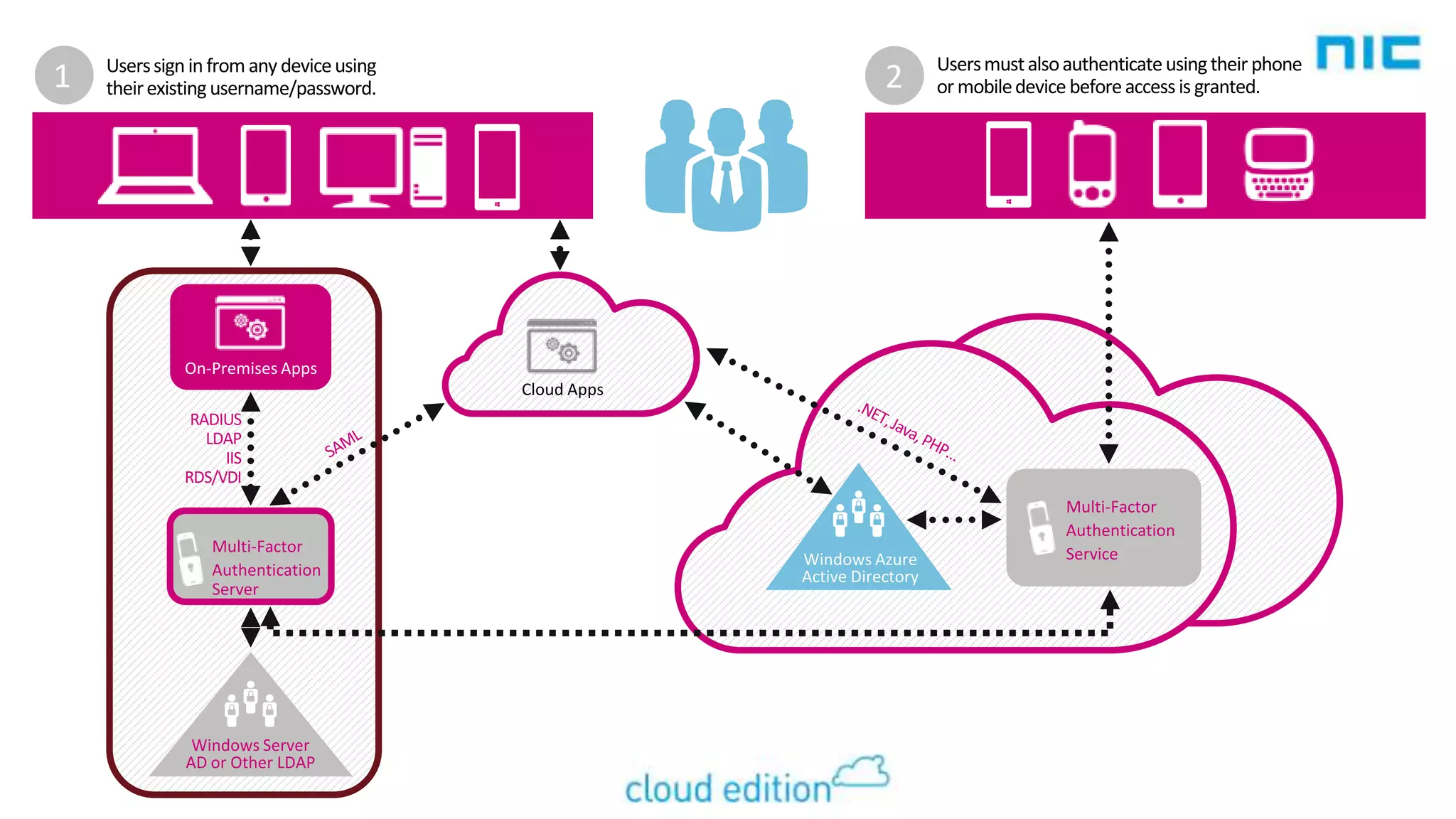
Windows Azure Multi-Factor Authentication provides an additional layer of security beyond passwords for accessing applications. It works by requiring two or more authentication factors, such as something you know (a password) and something you have (a registered mobile phone). The solution can integrate with on-premises applications and services using an on-premises server, and with cloud applications using Azure Active Directory. Users register their phones through a portal for authentication via calls, texts, or mobile app notifications. The solution is affordable and easy to use compared to hardware tokens since it leverages existing mobile phones.