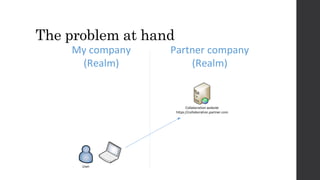
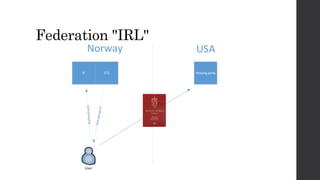
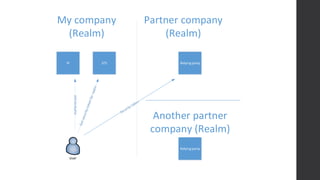
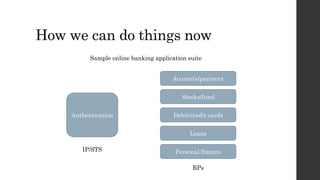
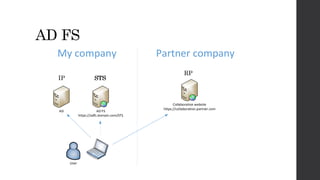
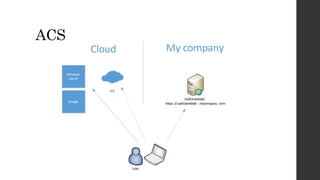
This document discusses federated identity and how it allows different companies to provide access to resources based on a user's identity asserted by another company. It describes how WS-Federation is an industry standard that defines mechanisms for security realms to federate. Key components of federated identity systems are discussed, including identity providers, security token services, relying parties, and security tokens that contain claims about a user. Architectural advantages of federated identity like single sign-on and flexibility in building applications are highlighted. Windows Identity Foundation and Active Directory Federation Services are presented as frameworks for building federated identity applications.