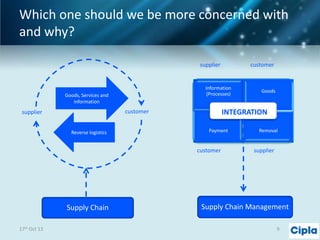
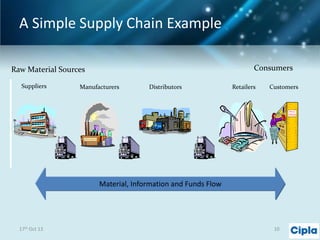
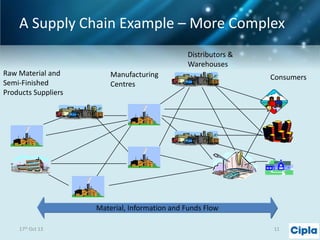
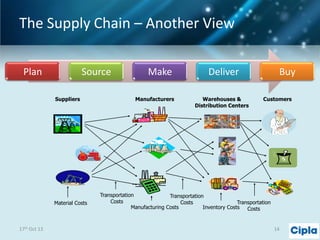
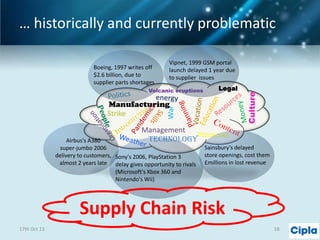
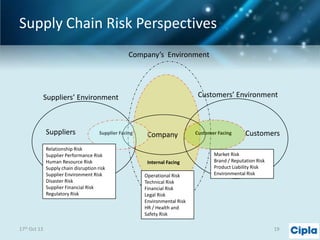
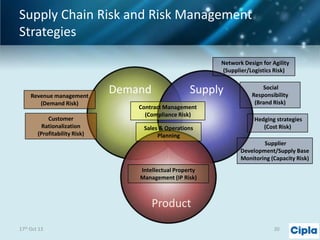
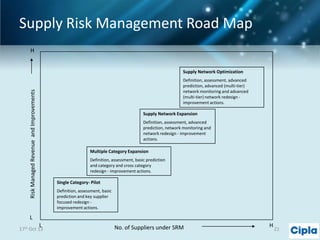
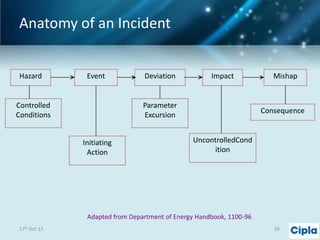
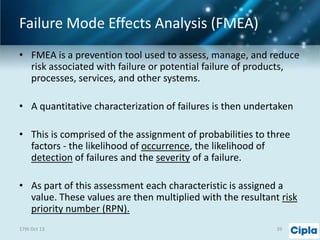
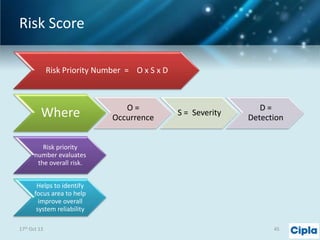
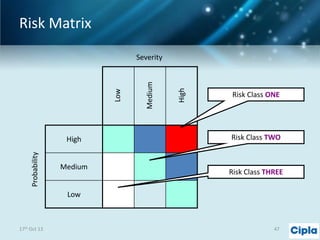
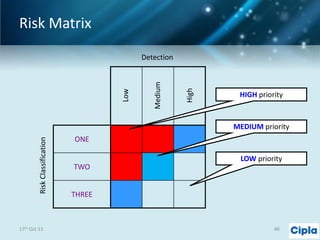
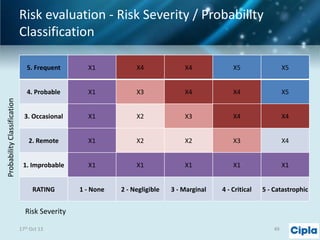
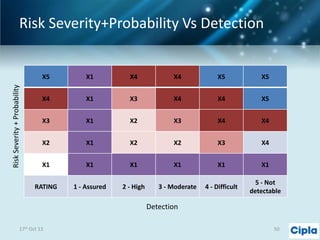
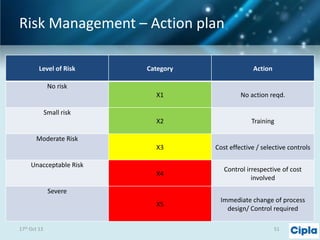
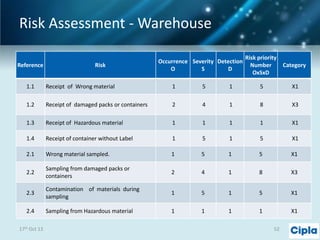
The document provides a comprehensive overview of supply chain risk management, emphasizing its complexity and the urgent need for effective strategies across various industries. It discusses the fundamental concepts of supply chain management, common risks encountered, and the importance of assessing and managing those risks through structured frameworks and methodologies, including risk assessments and mitigation strategies. The presentation concludes with call-to-action items for developing robust risk management processes critical for maintaining supply chain integrity.