Varun Sharma from Microsoft India identifies 5 common authentication and authorization flaws in web applications:
1. Custom authentication is implemented instead of using proven system methods.
2. Rule-based authorization is not considered, with authorization relying only on disabling UI elements.
3. Input validation only checks for blacklisted characters instead of whitelisting allowed values.
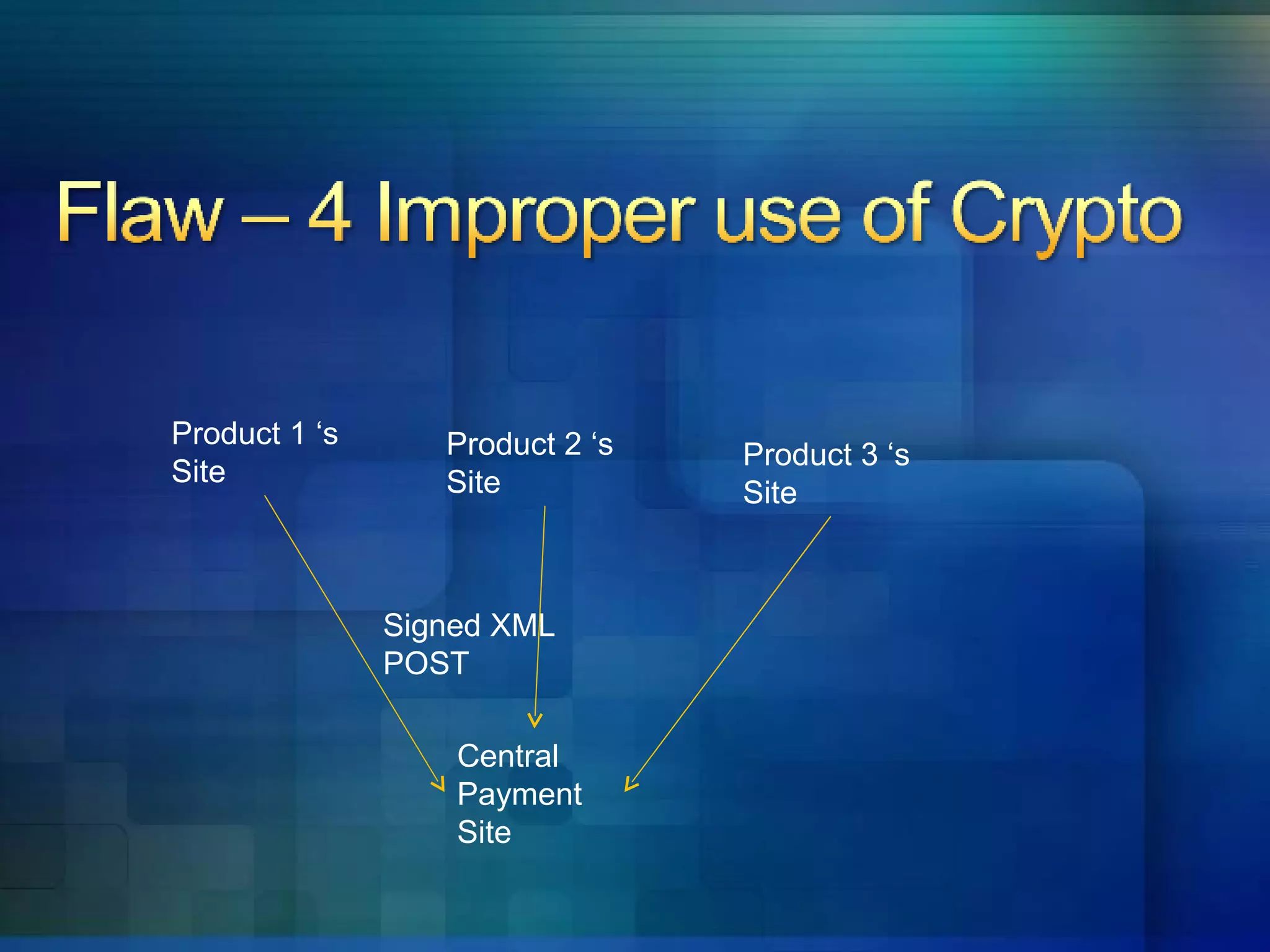
4. Cryptography is improperly implemented without understanding what security mechanisms provide.
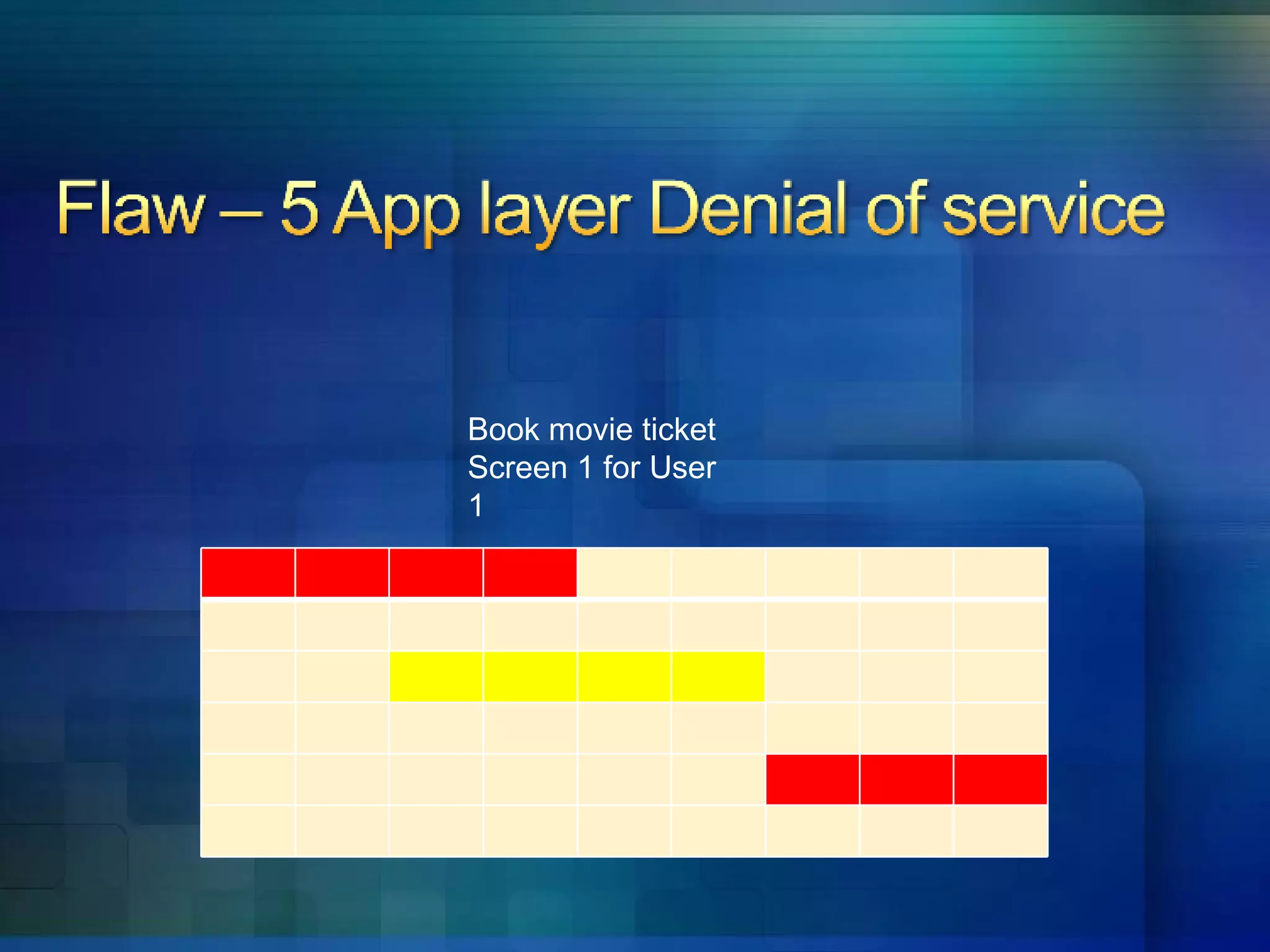
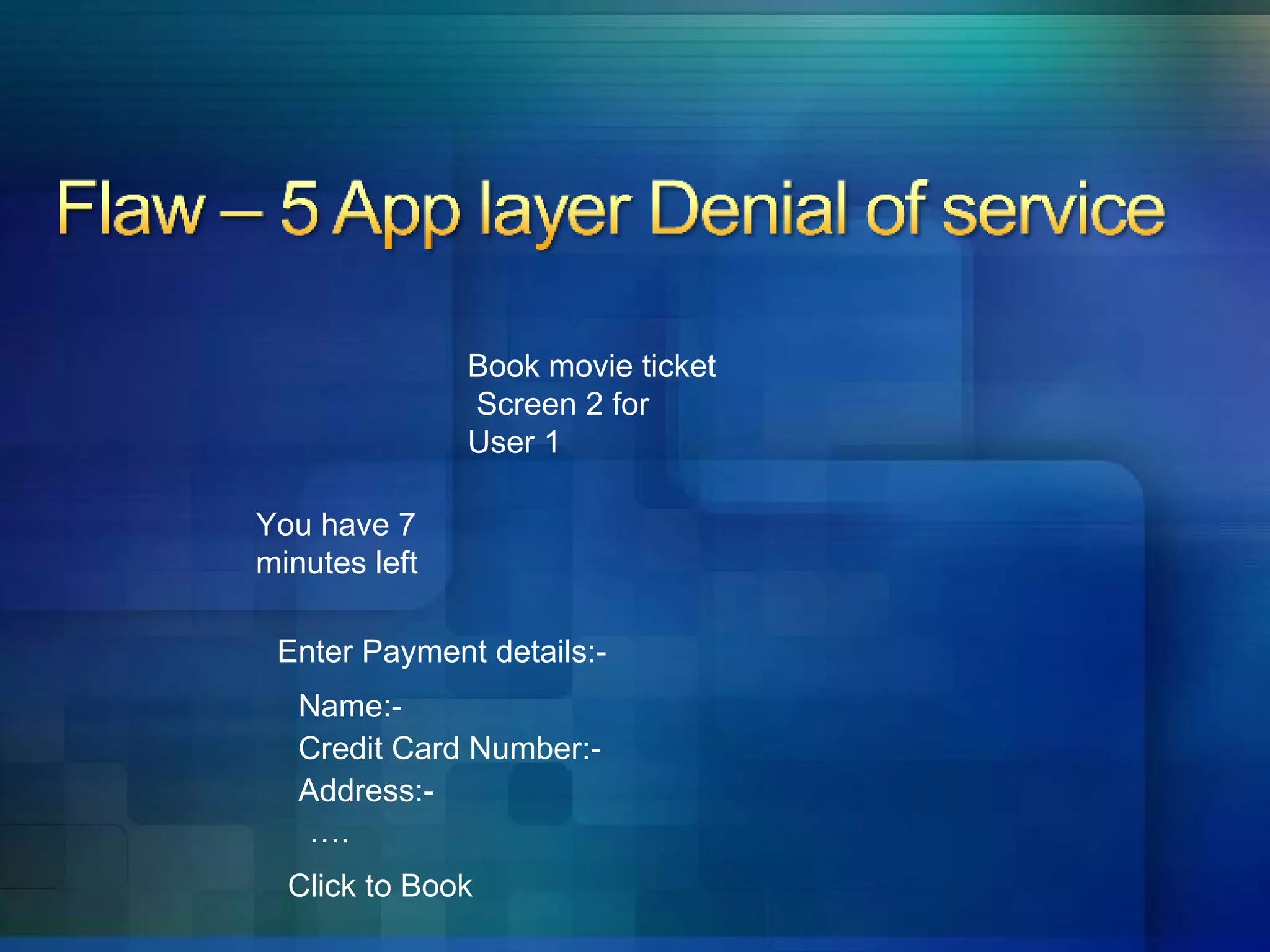
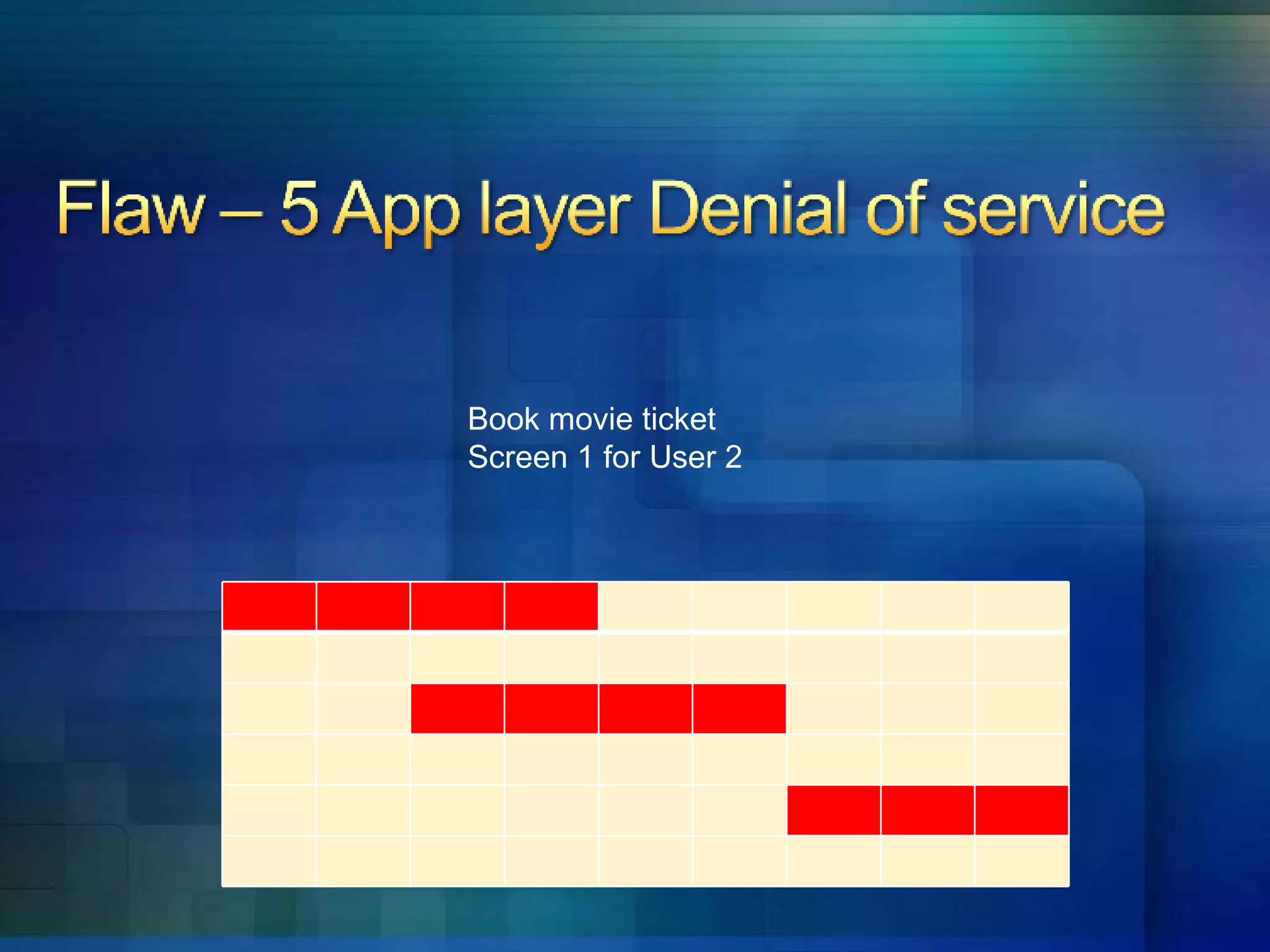
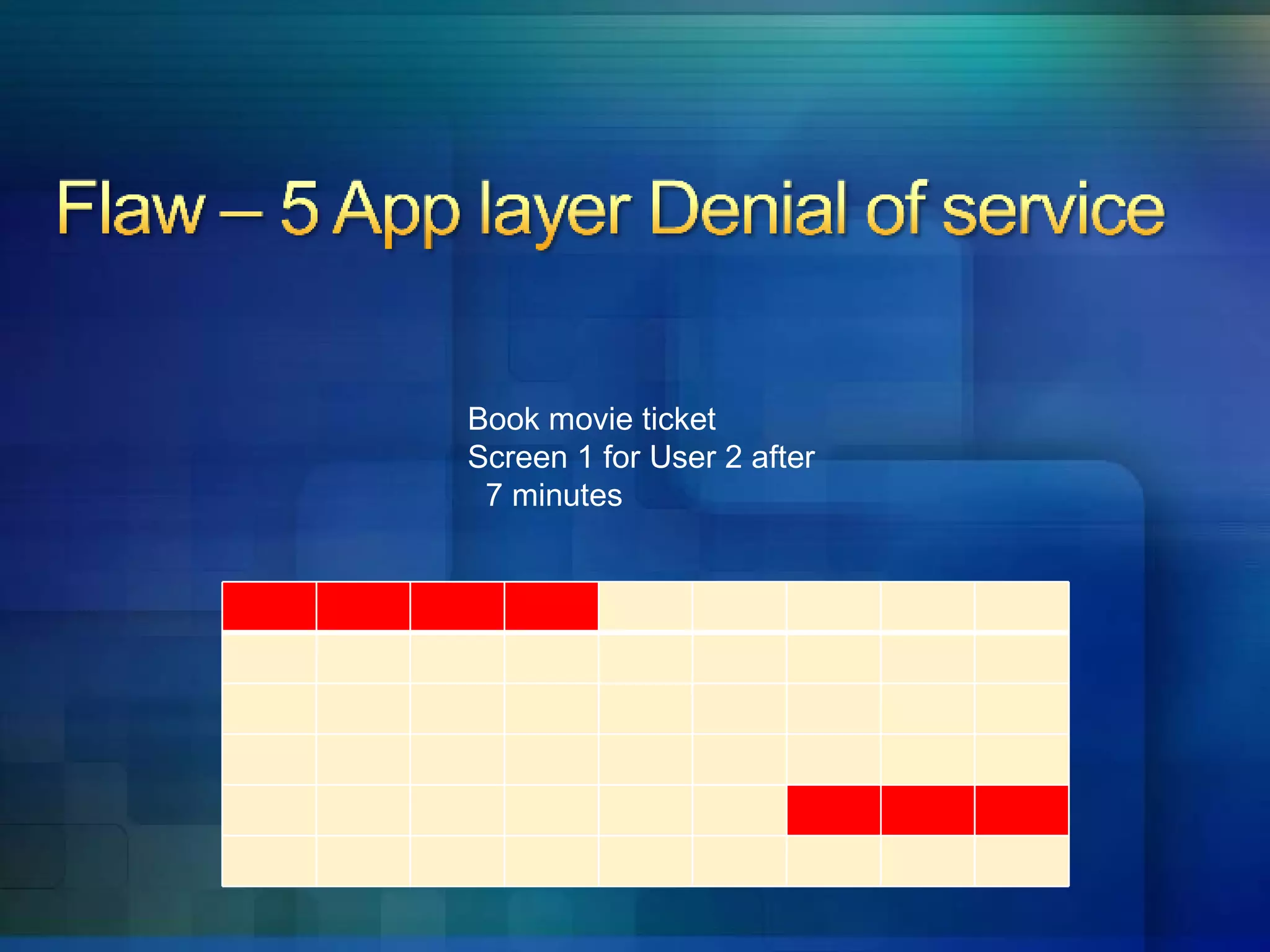
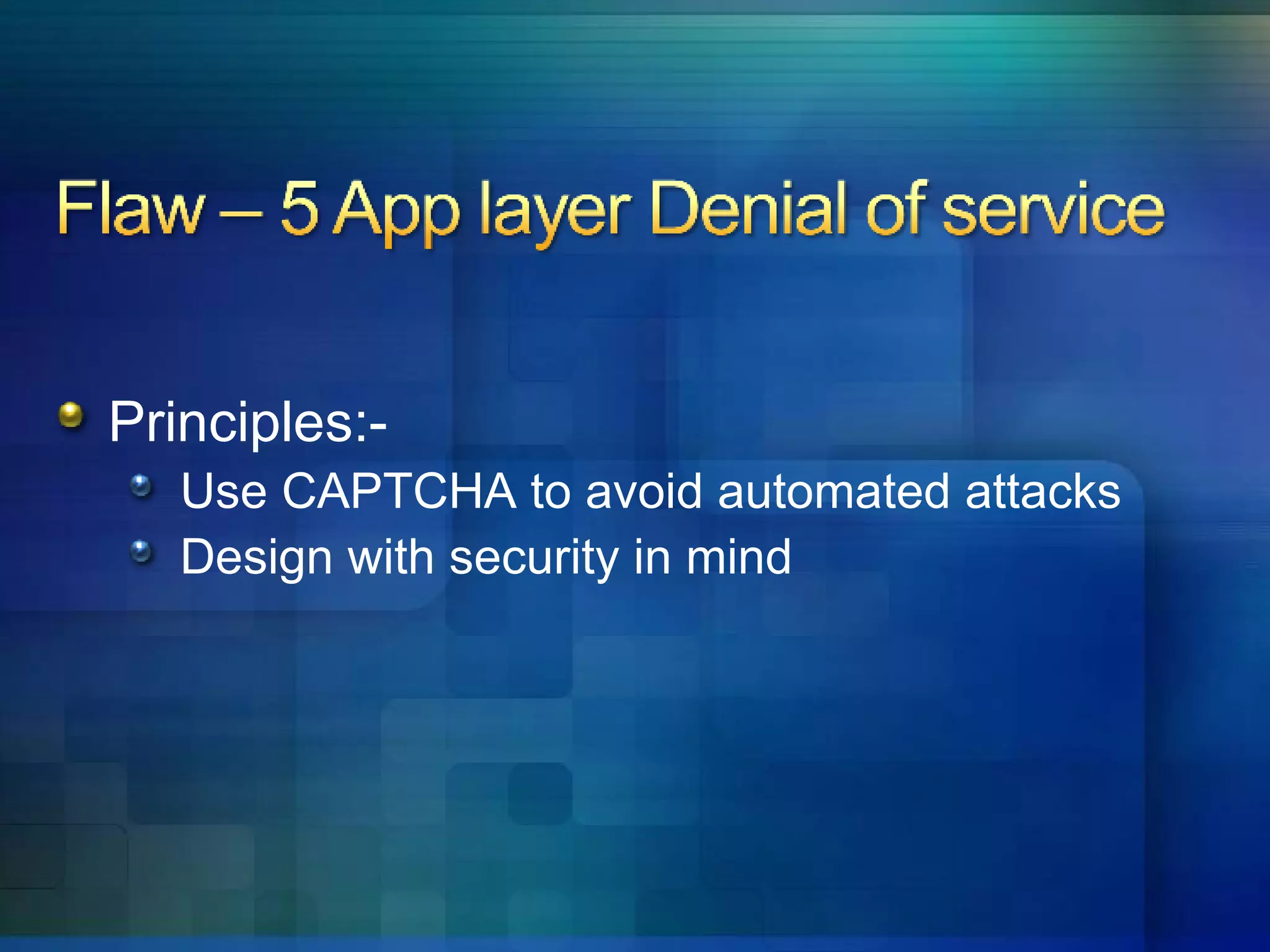
5. Applications are vulnerable to denial of service attacks from excessive automated requests.