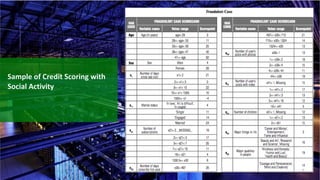
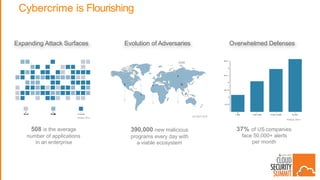
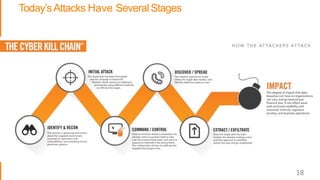
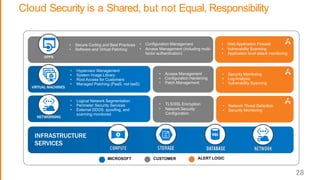
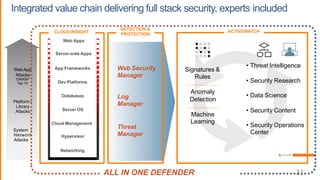
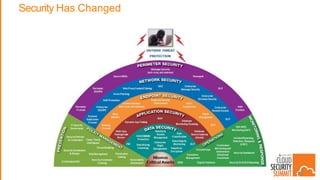
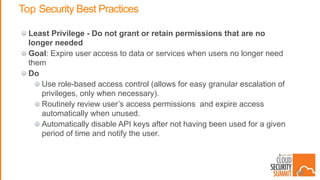
This document summarizes security best practices for cloud computing. It discusses how security in the cloud requires a shared responsibility model between the cloud provider and customer. It recommends implementing least privilege access, defense in depth strategies like isolating environments and regular patching, and knowing your system through strong authentication and authorization. Specific best practices covered include using multi-factor authentication, limiting exposed services, expiring unnecessary permissions, and preventing lateral movement between hosts. The document promotes keeping systems simple and securing the full technology stack.