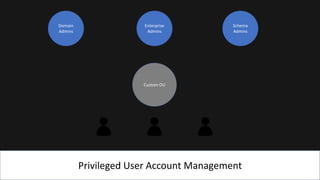
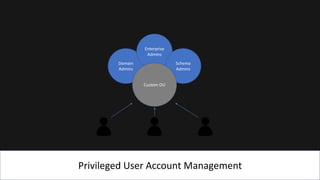
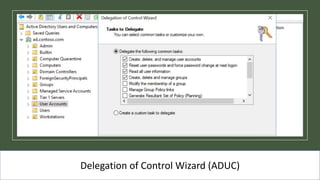
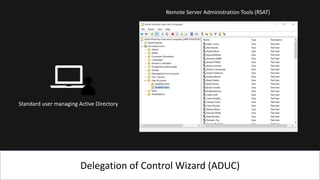
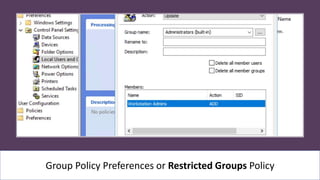
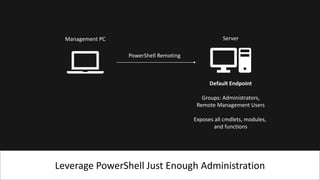
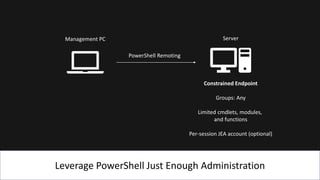
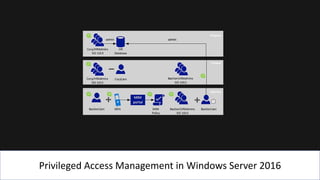
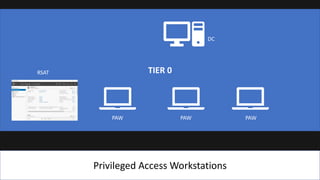
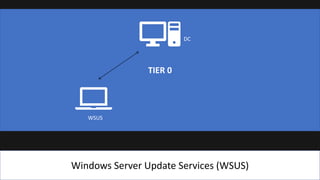
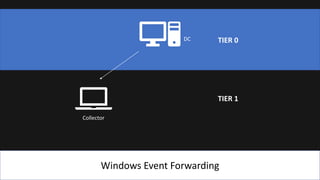
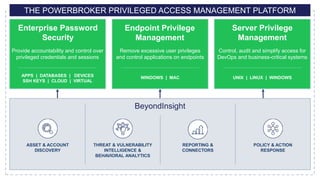
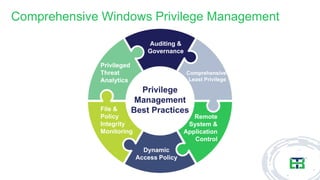
The document presents an 8-step guide for administering Windows systems without requiring domain admin privileges, highlighting the risks of privileged account usage and best practices to mitigate those risks. Key steps include enforcing role separation, limiting privileged group memberships, and using tools like PowerShell and privileged access management solutions. The importance of managing administrative access and monitoring is emphasized to prevent privilege abuse and enhance security.