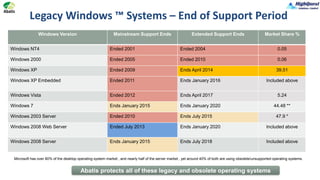
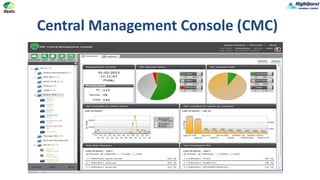
Abatis HDF is a proactive security tool designed to protect systems from advanced cyber threats, including zero-day malware and unauthorized software modifications. It maintains system integrity across legacy and current Windows platforms without requiring constant updates, effectively stopping 99% of viruses. The central management console allows for easy deployment, logging, and policy enforcement across an organization, enhancing security while minimizing performance impact.