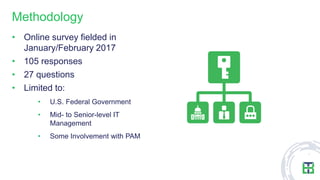
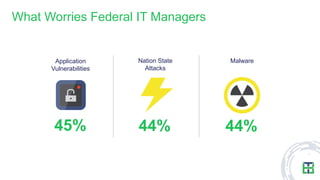
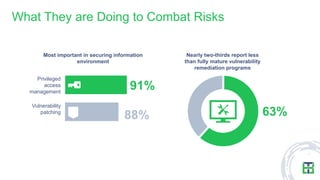
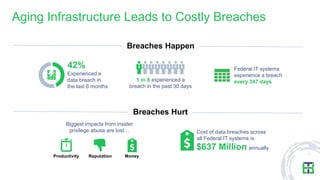
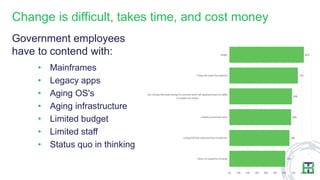
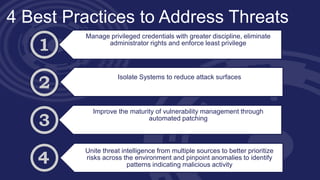
The document discusses strategies for mitigating risks in aging federal IT systems, highlighting the results of a survey conducted among mid- to senior-level IT managers in the U.S. federal government. Key findings indicate that malware, state-sponsored attacks, and application vulnerabilities are significant concerns, with aging infrastructure leading to costly data breaches. Recommendations for improvement include managing privileged credentials, enhancing vulnerability management practices, and isolating legacy systems to reduce attack surfaces.