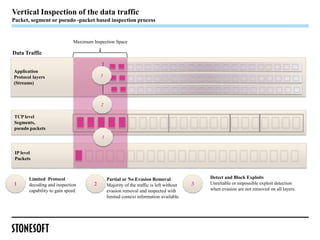
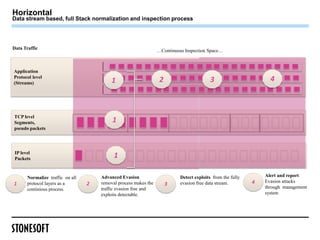
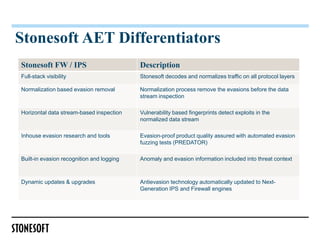
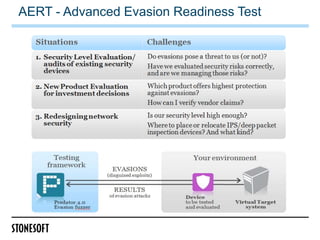
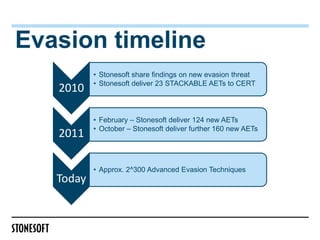
The document outlines a webinar presented by Steven Turner and Alan Cottom, focusing on identifying, preventing, and securing against advanced evasion techniques (AETs) in cyber attacks. It details the nature of AETs, which allow attackers to evade detection by security systems, and emphasizes the need for comprehensive security solutions that can address these threats. The presentation includes a demonstration of Stonesoft's security solutions, showcasing their efficacy in detecting and mitigating AETs.



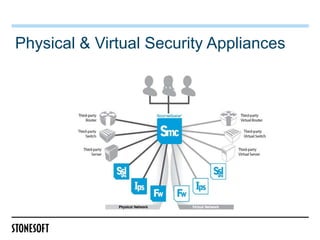



![AETs in action
AET Test Environment
Untrusted Network Security Device(s) Protected Network
[Exploit with AETs]
Predator Target
[AET Attack] [Vulnerable]
Tool Host
Gartner Magic
Quadrant
IPS/IDS/NGFW
Solutions](https://image.slidesharecdn.com/stonesoftandintergencewebinar-120813073325-phpapp01/85/Webinar-on-identifying-preventing-and-securing-against-the-unidentifiable-attacks-11-320.jpg)