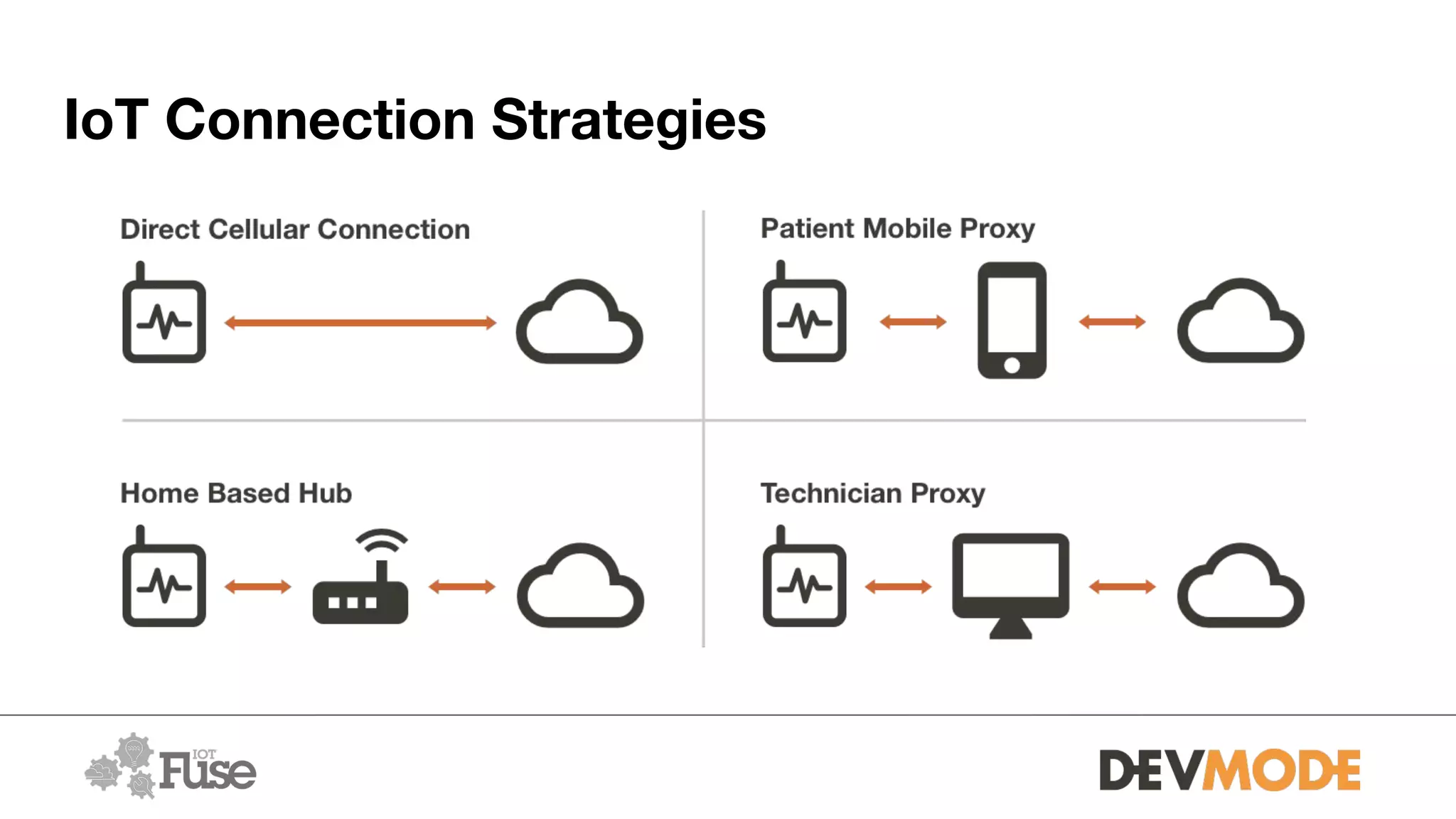
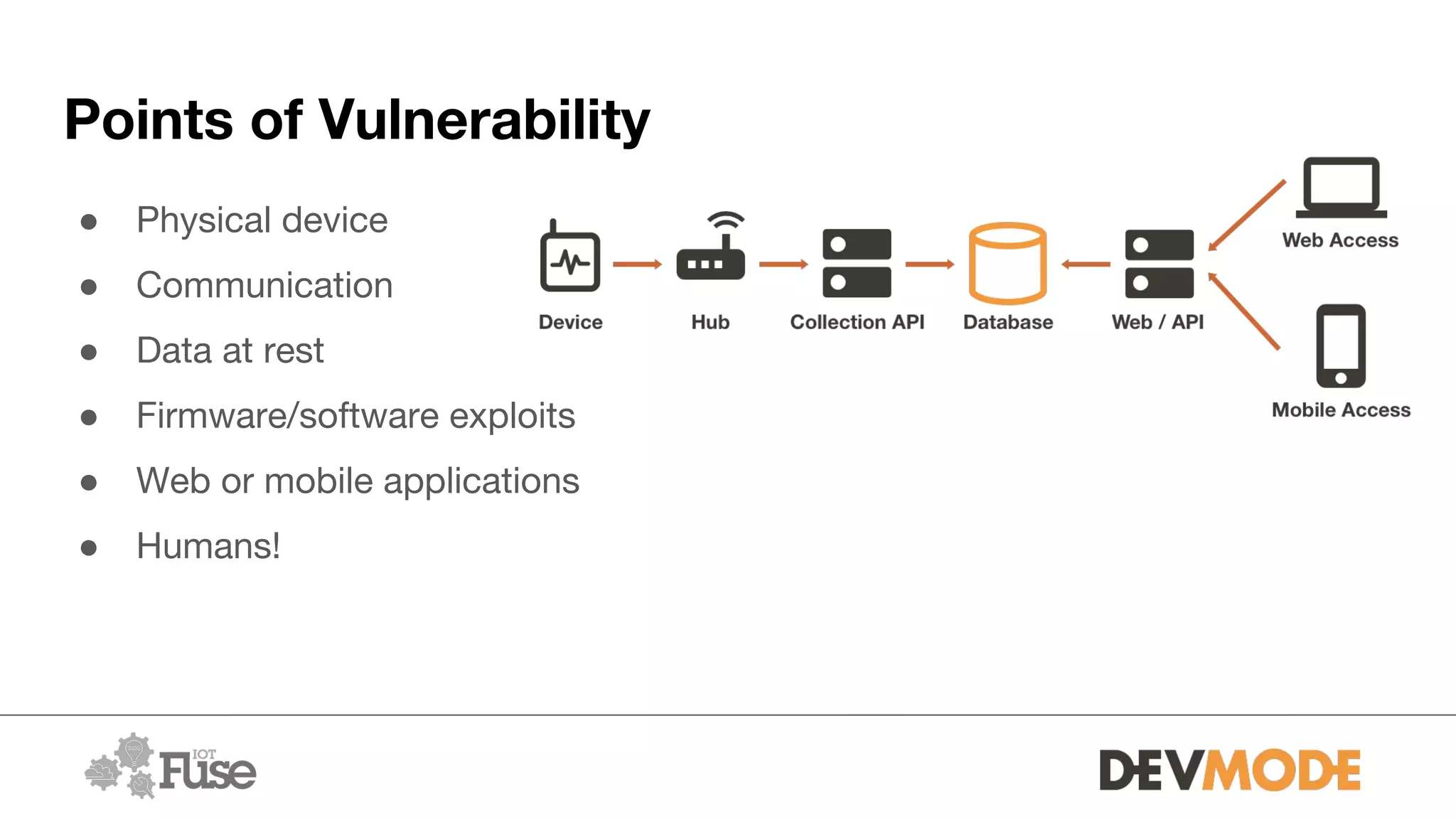
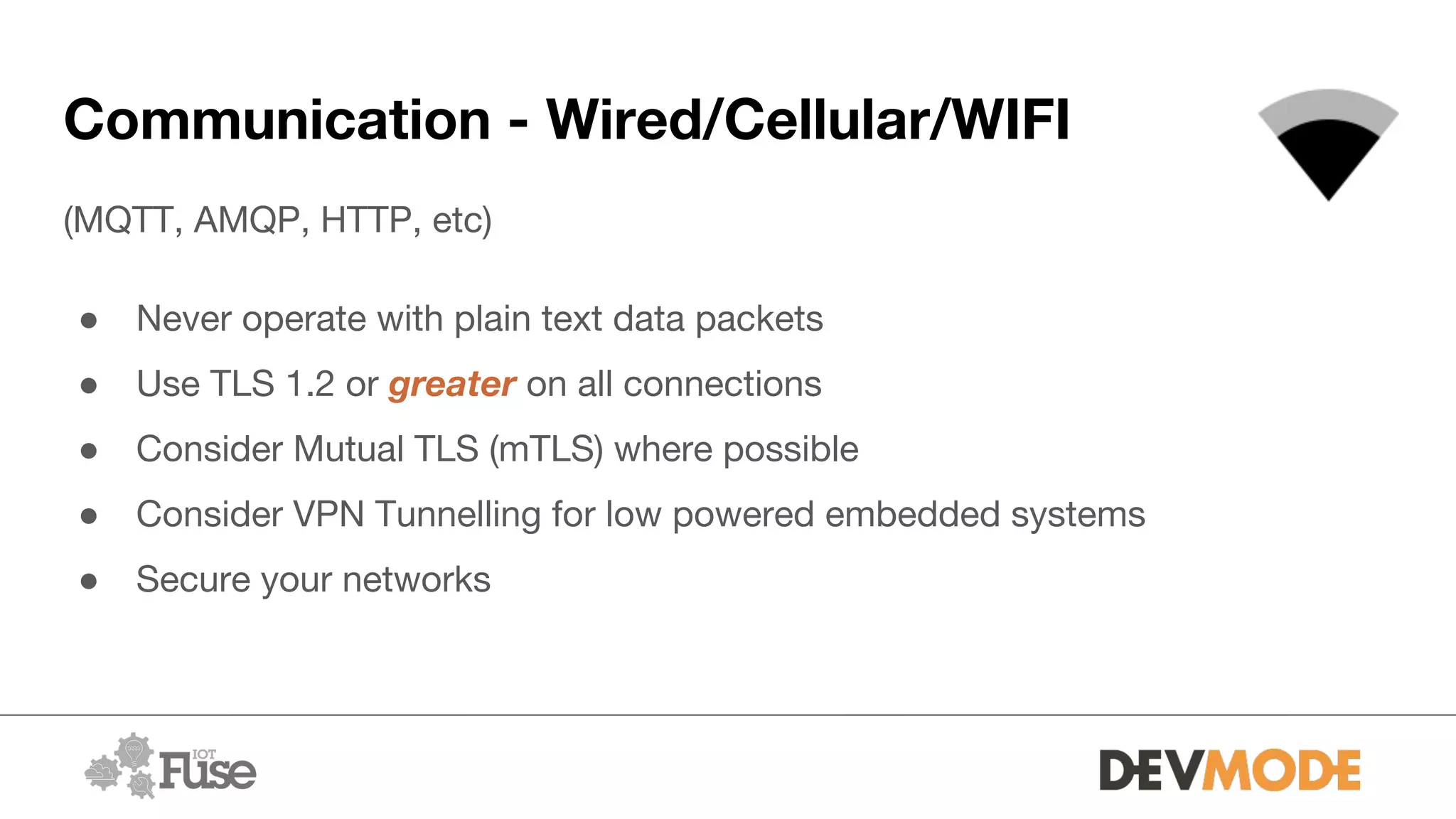
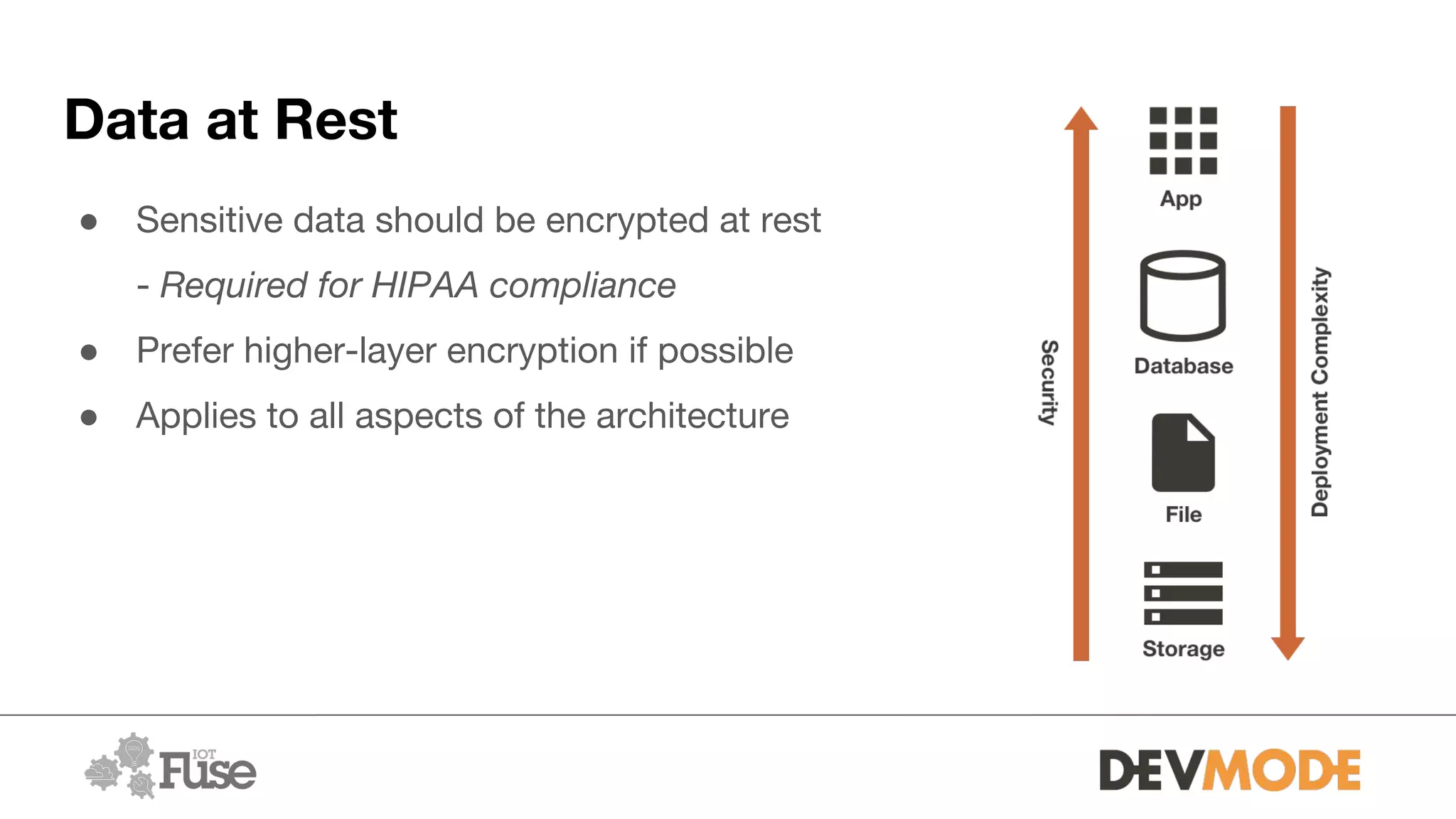
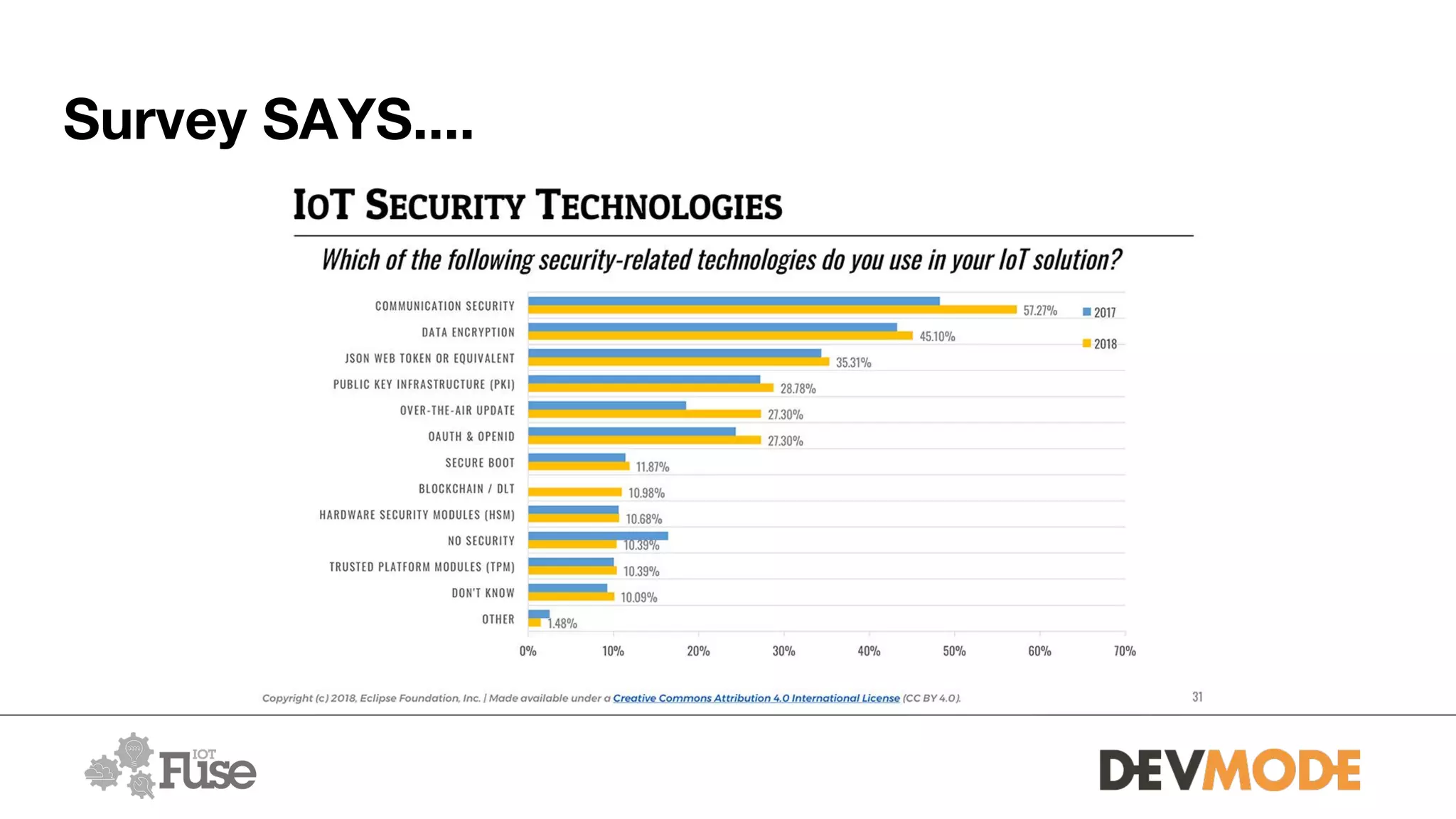
The document provides an overview of securing medical devices. It begins by outlining the objectives of understanding current device security, vulnerabilities, and considerations for securing systems. It then discusses what constitutes a medical device and why connectivity is important but introduces risks. Several risk scenarios are described, such as device hacking, data breaches, and DIY modifications. Specific examples of insulin pump and pacemaker hacks are given. The document then provides strategies for improving security, including identifying risks, using strong identities and cryptography, monitoring for issues, and securing various aspects of systems from the hardware to communications to applications. It acknowledges barriers to security but emphasizes doing as much as possible and understanding what is at stake.