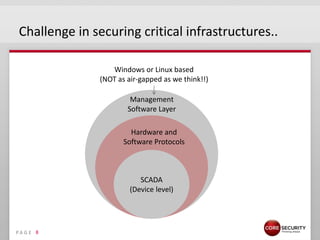
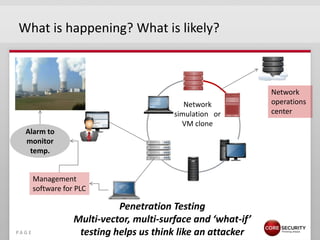
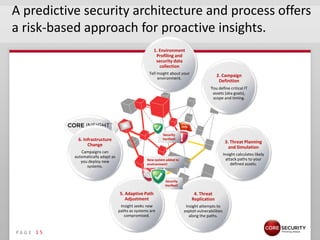
This document discusses proactive security intelligence for smart utilities. It covers the threat landscape including sophisticated malware like Stuxnet, targeted attacks using zero-days and social engineering, and high-volume attacks. It notes challenges in securing critical infrastructures due to their use of common operating systems and protocols. The document advocates taking a performance and analytics-driven approach to proactive security using network simulation, penetration testing, and predictive modeling to identify exposures before they can be exploited.