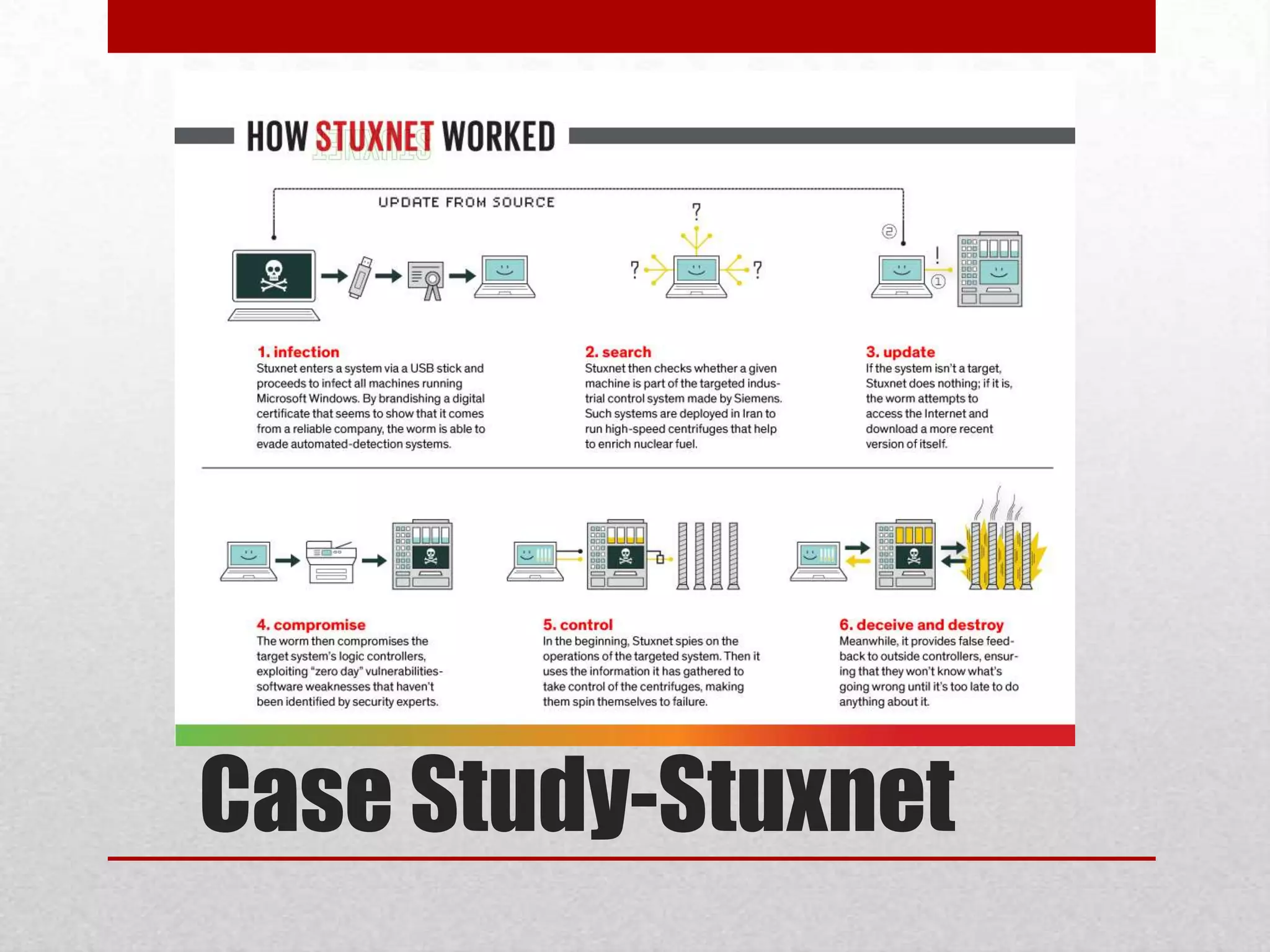
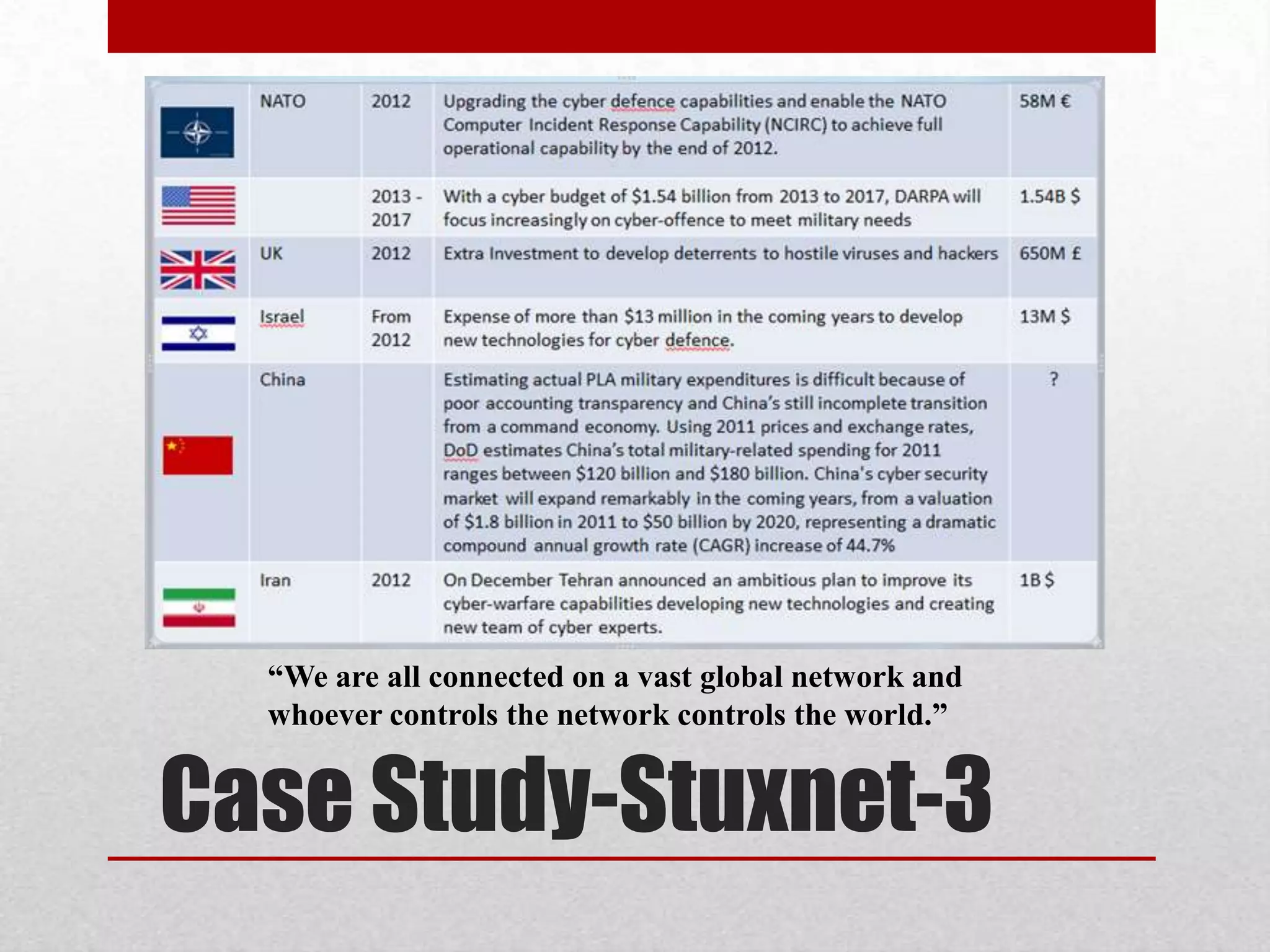
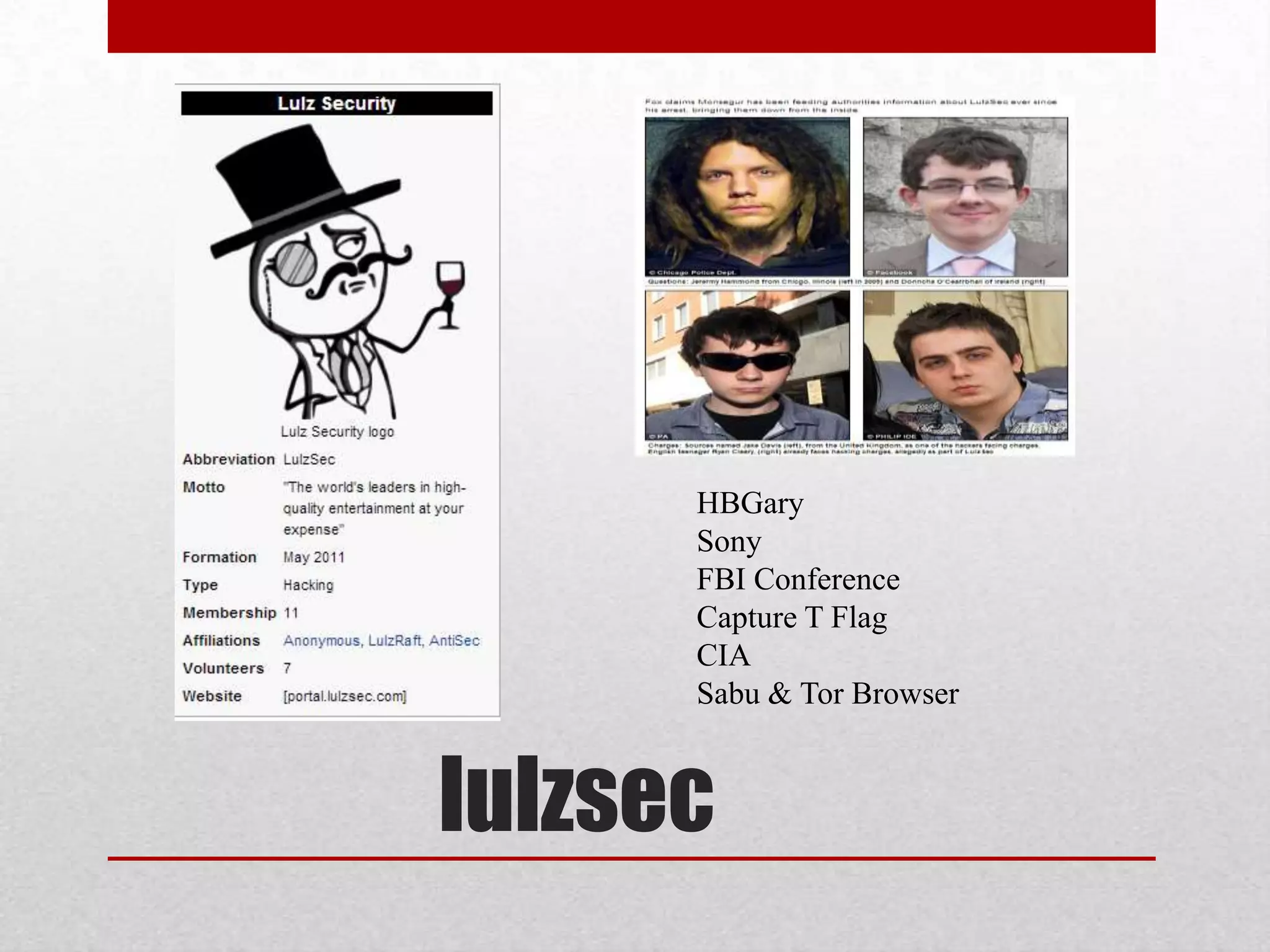
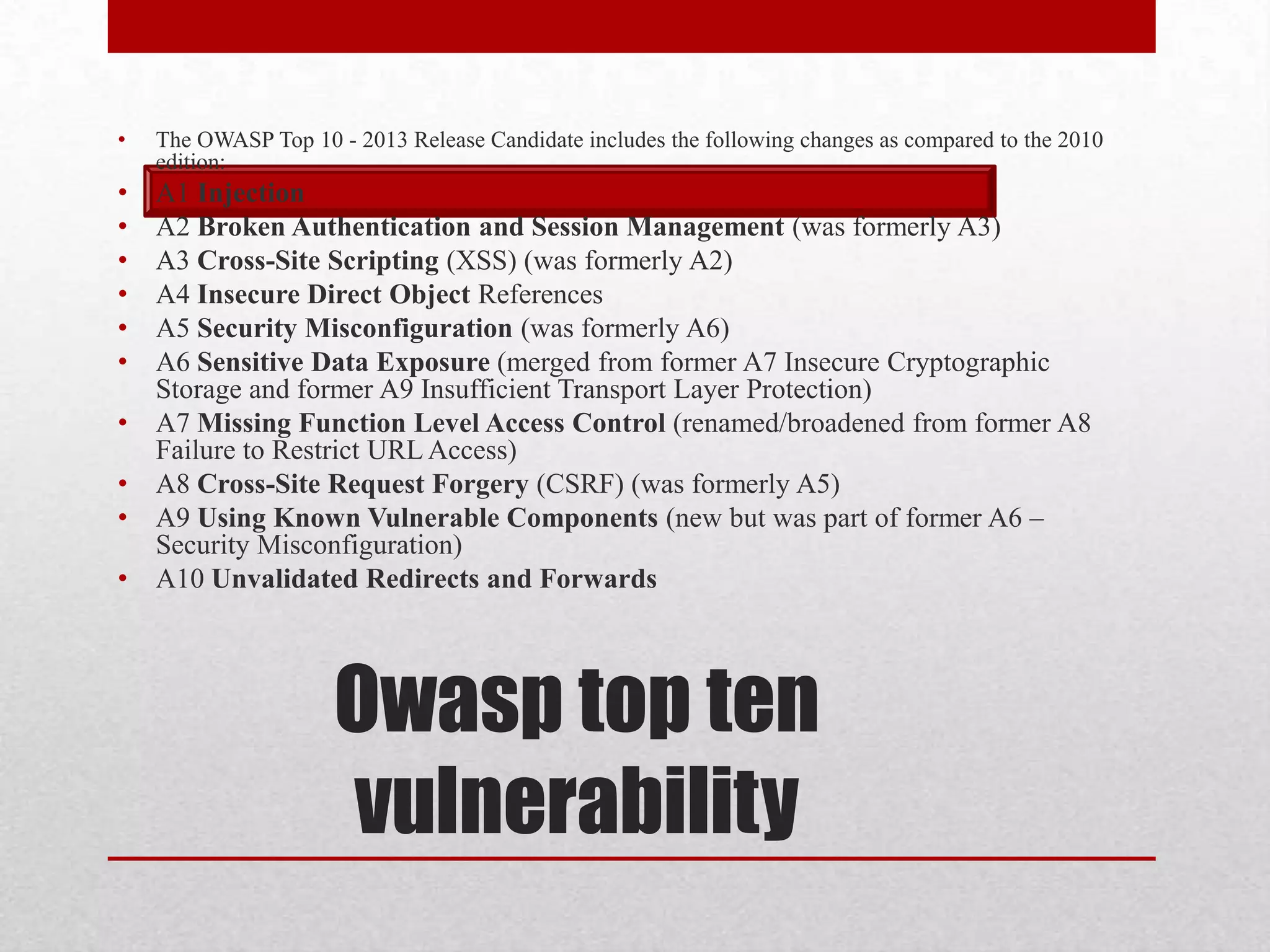
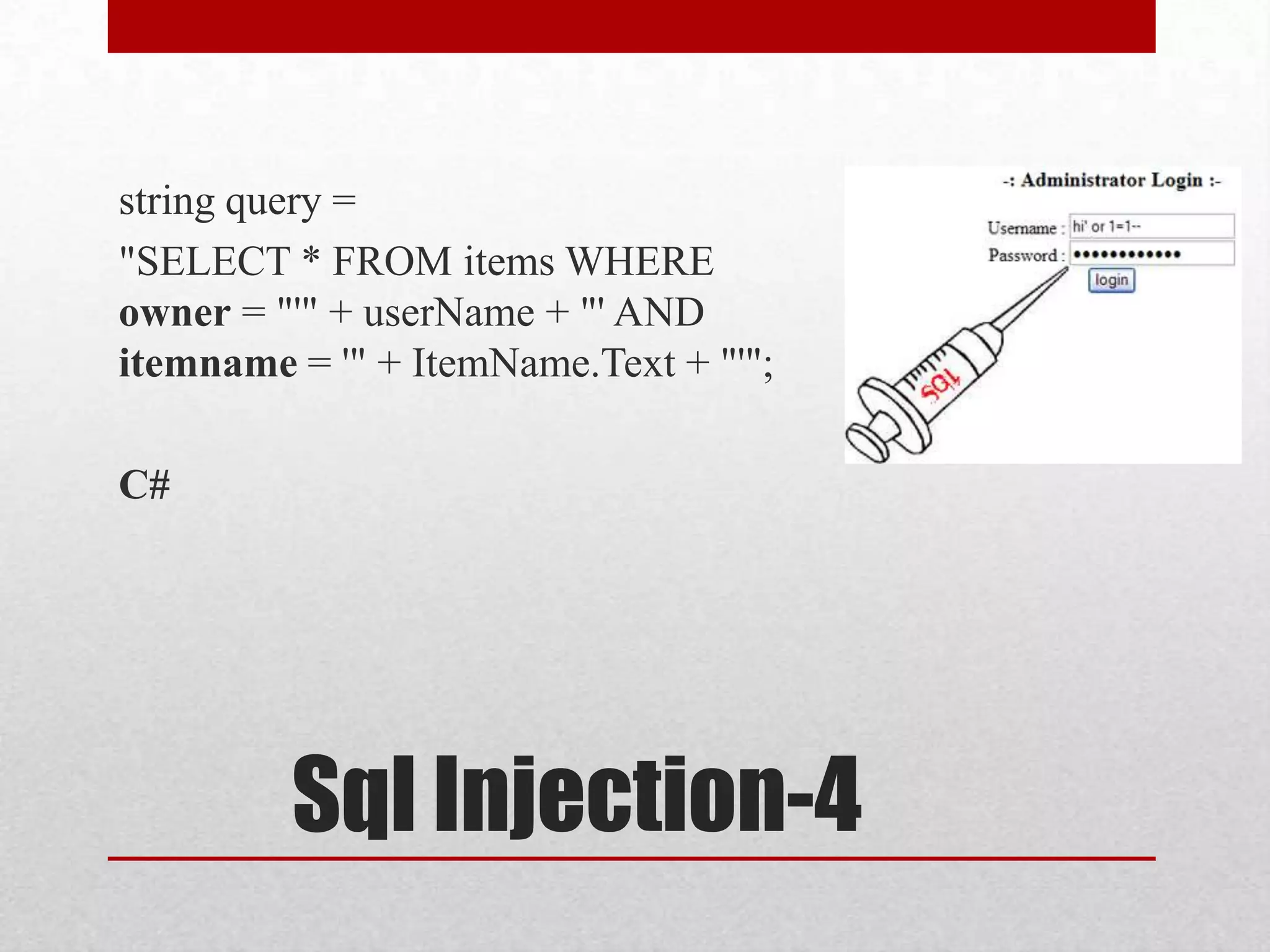
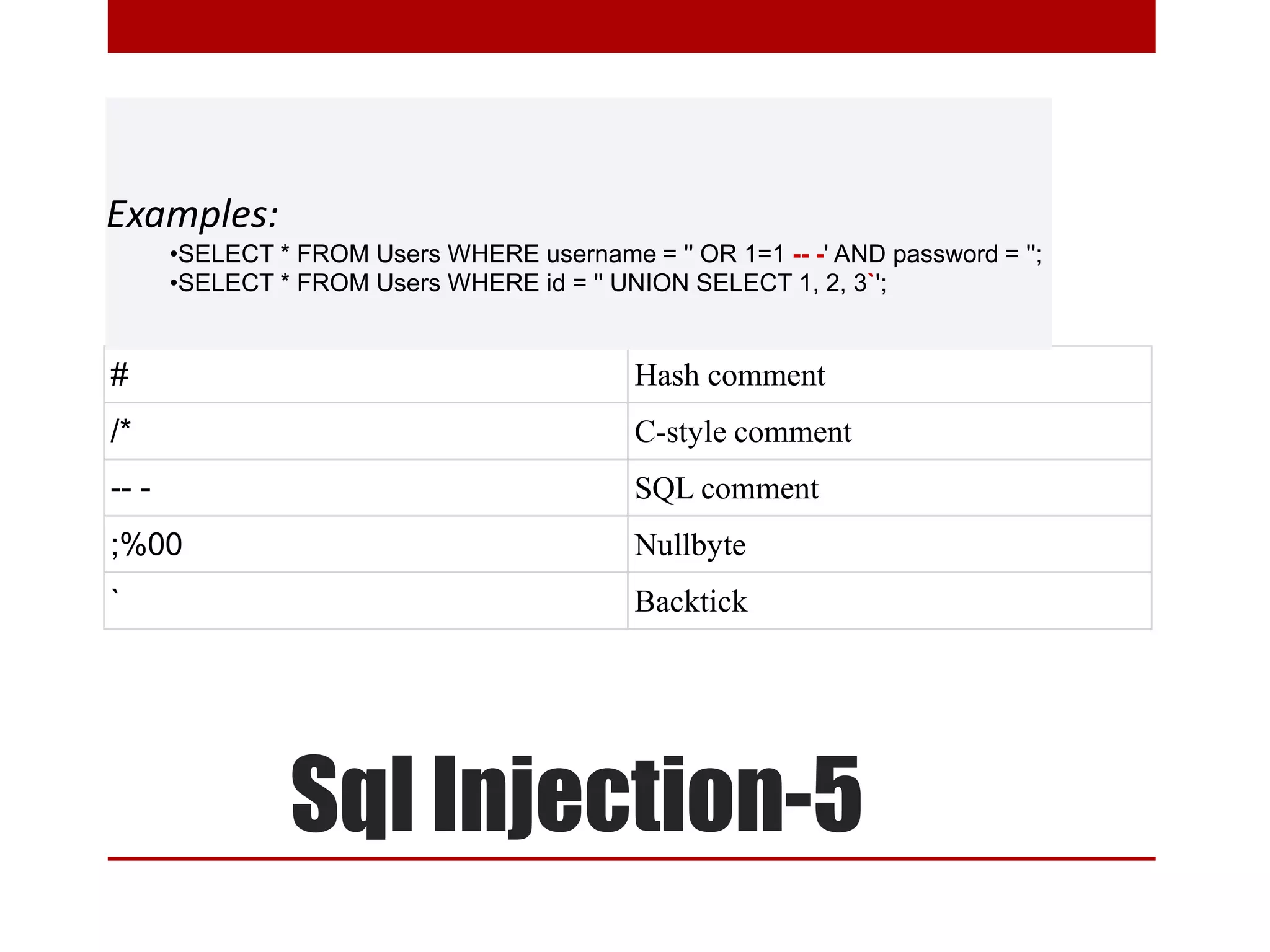
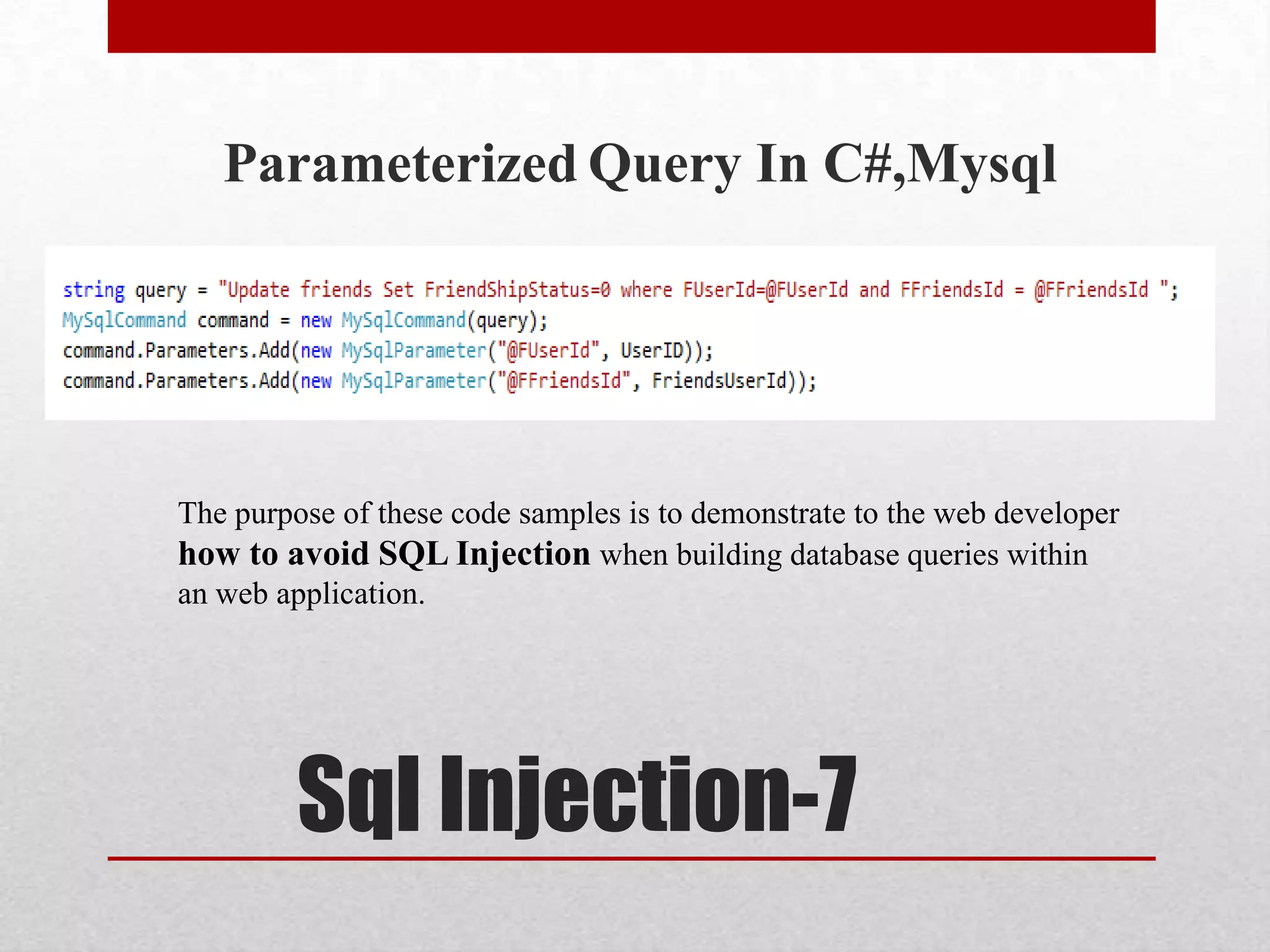
This document discusses various topics related to web security. It begins with an introduction to security mindsets and thinking like an attacker. It then discusses real-world examples of cyberwar between countries. It provides case studies on the Stuxnet virus. It introduces the security tools OWASP WebGoat, Web Scarab, Beef, and SET for demonstrations. It also mentions using QR codes and the future of web security.