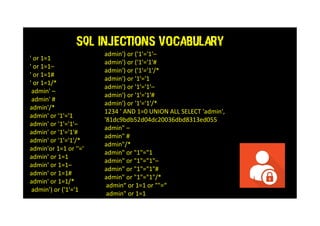
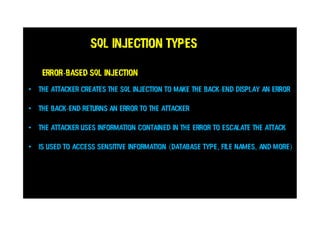
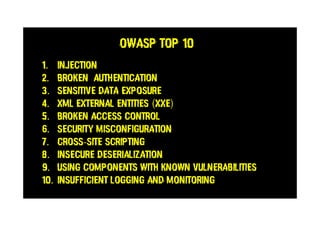
This document discusses SQL injections and how every tester needs to know about them. It covers the different types of SQL injections like error-based, union-based, boolean-based and time-based injections. Examples are provided for each type. The document also discusses ways to protect against SQL injections like parameterized statements, input validation, and access control. It emphasizes the importance of security testing and being aware of injection vulnerabilities.











![SQL INJECTIONS EXAMPLES
qalab@gmail.com
xxx’) OR 1=1--]
SELECT * FROM users WHERE email=‘qalab@gmail.com’ AND password=md5(‘xxx’) OR 1=1--]’);](https://image.slidesharecdn.com/sql-210228074119/85/SQL-INJECTIONS-EVERY-TESTER-NEEDS-TO-KNOW-17-320.jpg)