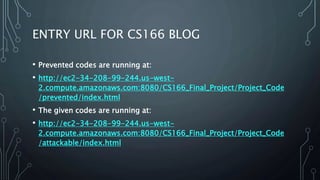
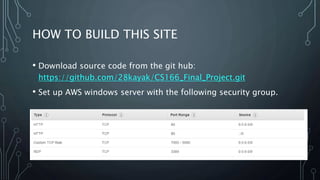
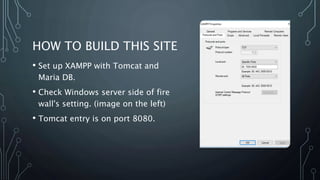
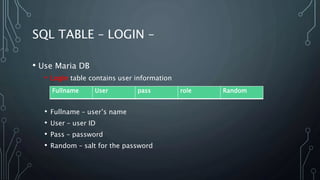
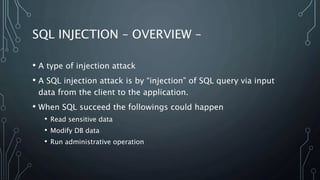
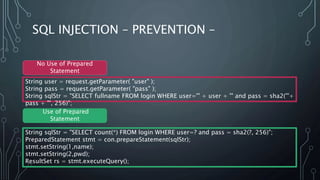
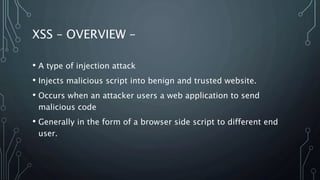
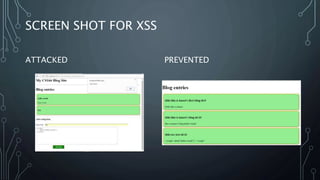
This document describes a final project for a computer science course involving various cybersecurity vulnerabilities and techniques for preventing them. It discusses SQL injection and demonstrates how to prevent it using prepared statements. It also covers cross-site scripting (XSS), cross-site request forgery (CSRF), and ways to mitigate these risks, such as input validation and using synchronized tokens. The project code repository and demo sites for vulnerable and secure code are provided.