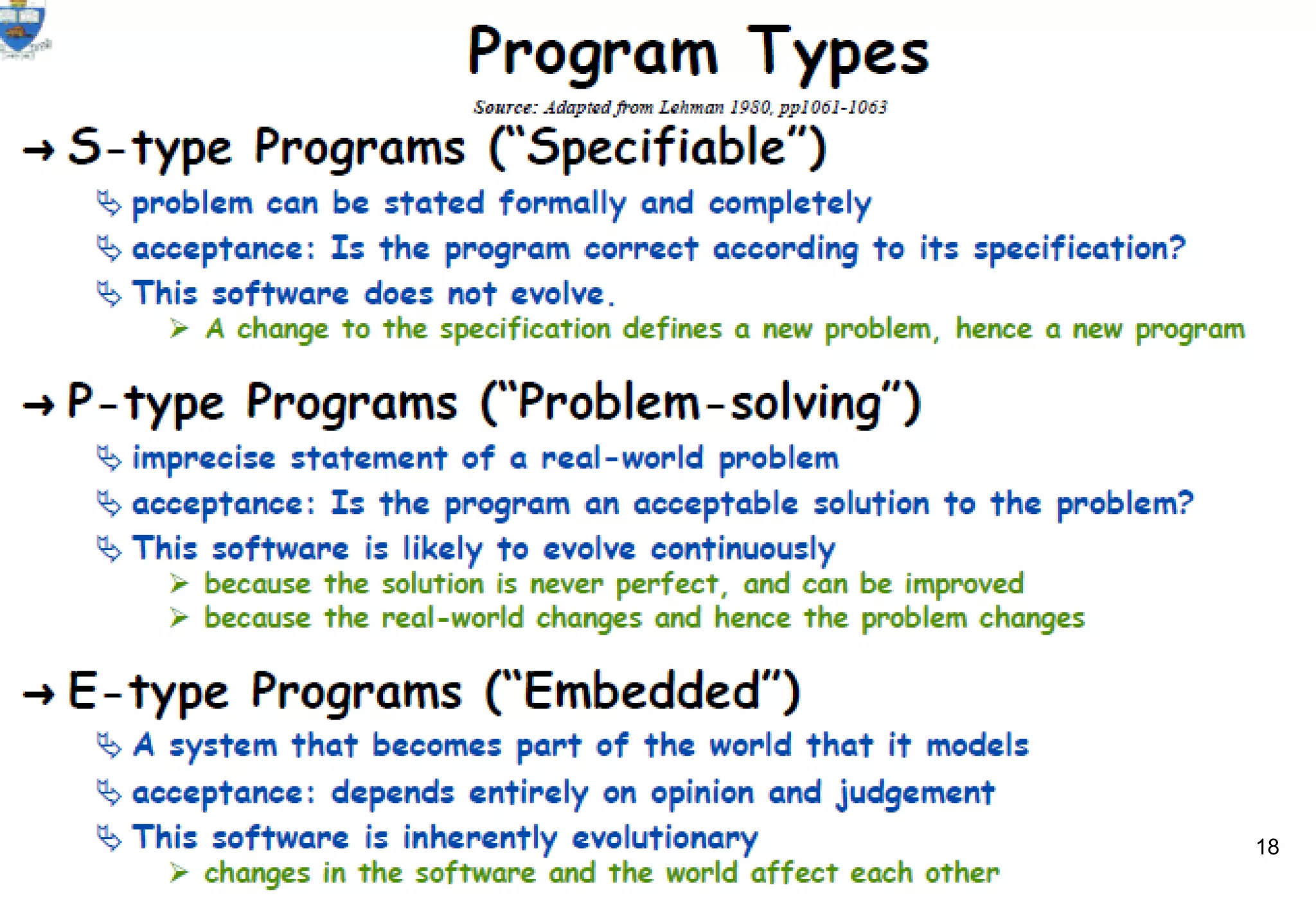
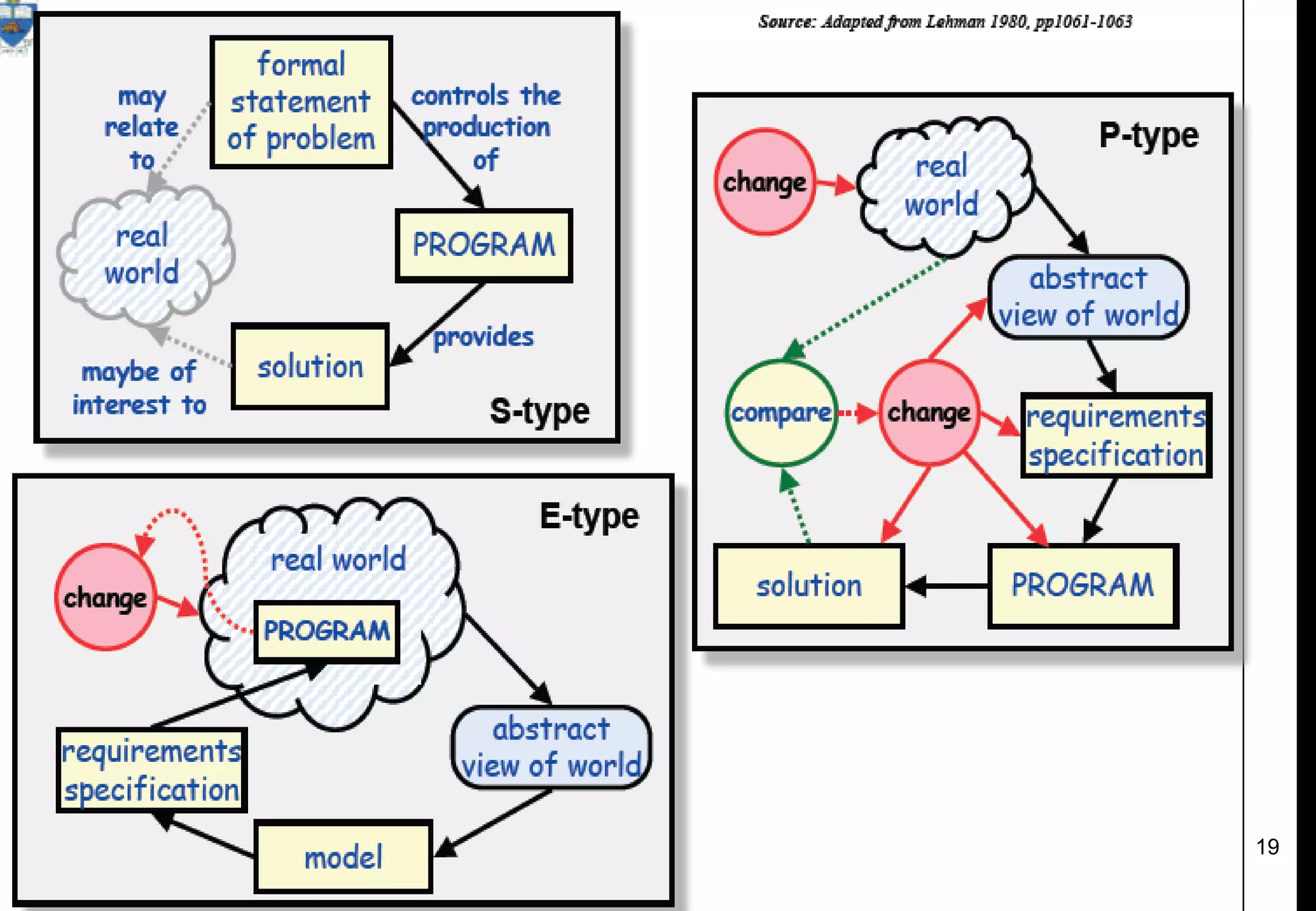
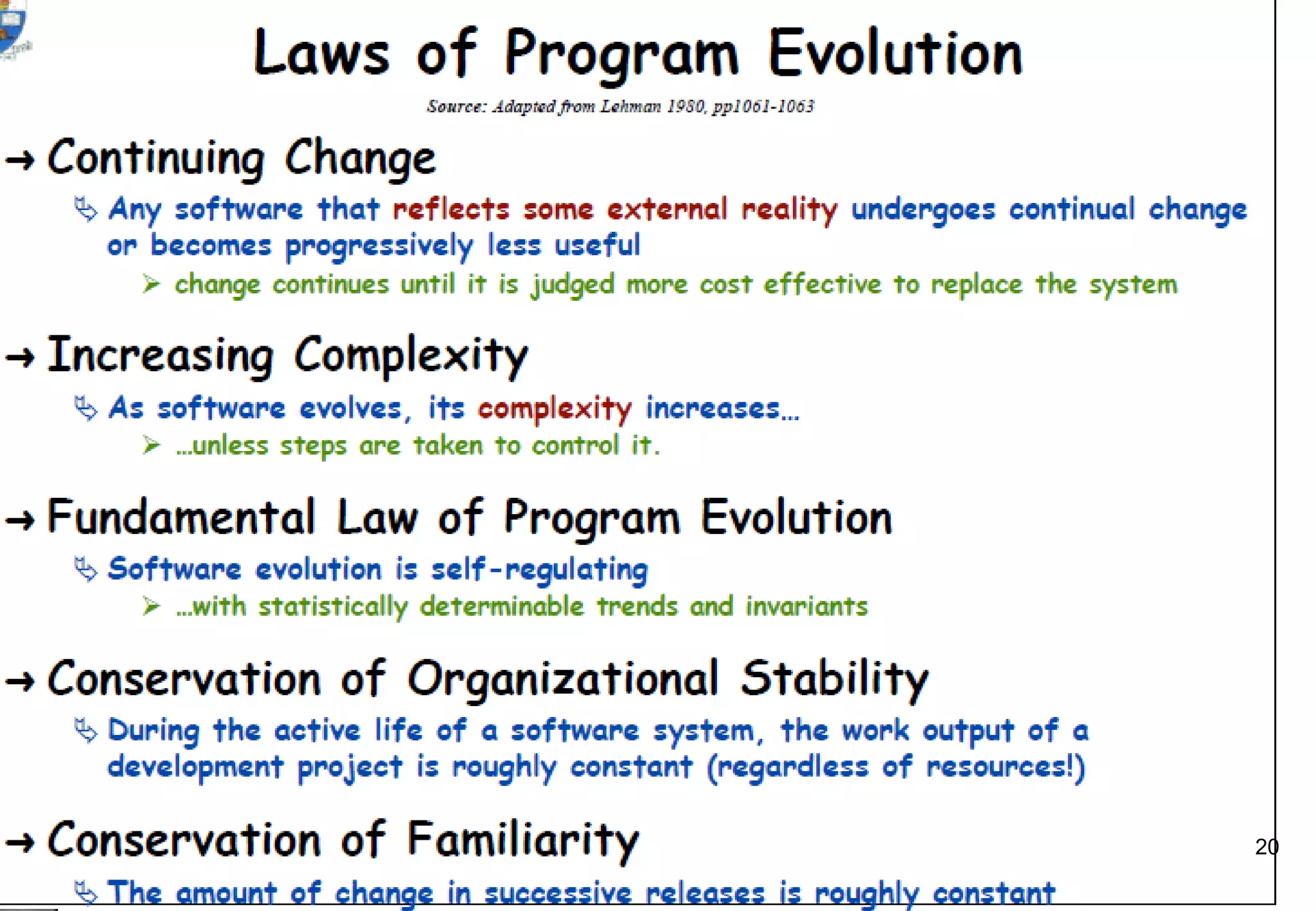
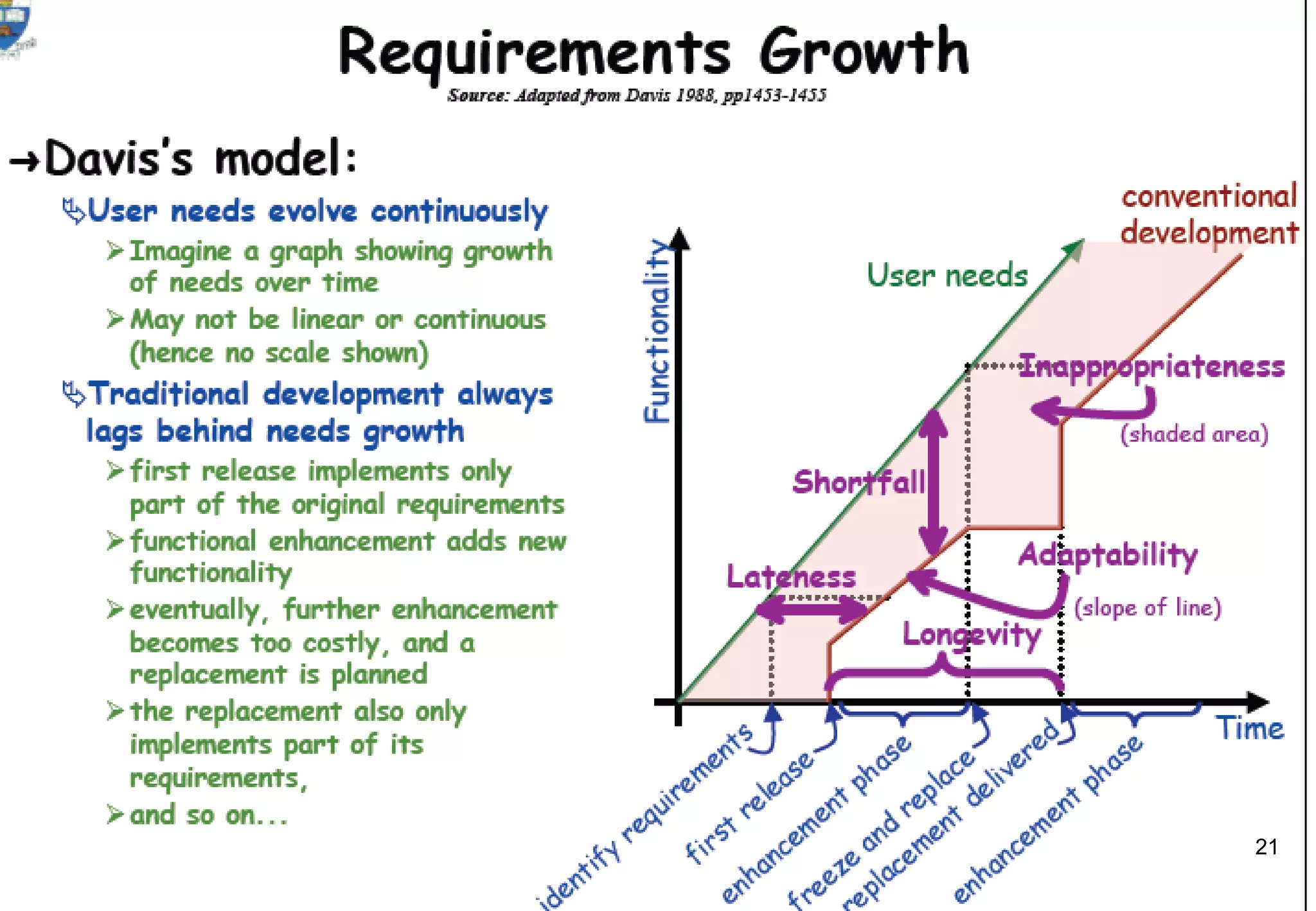
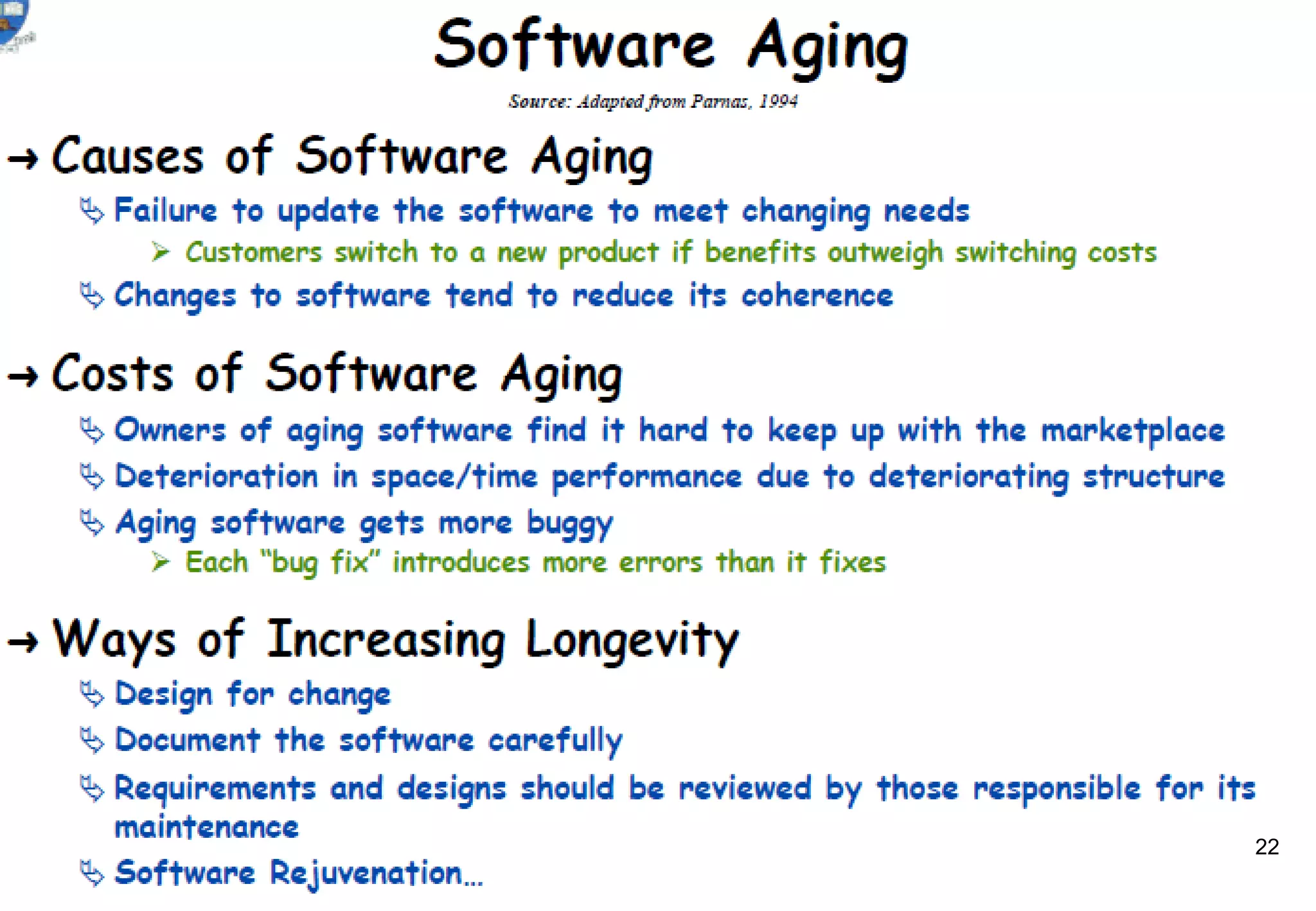
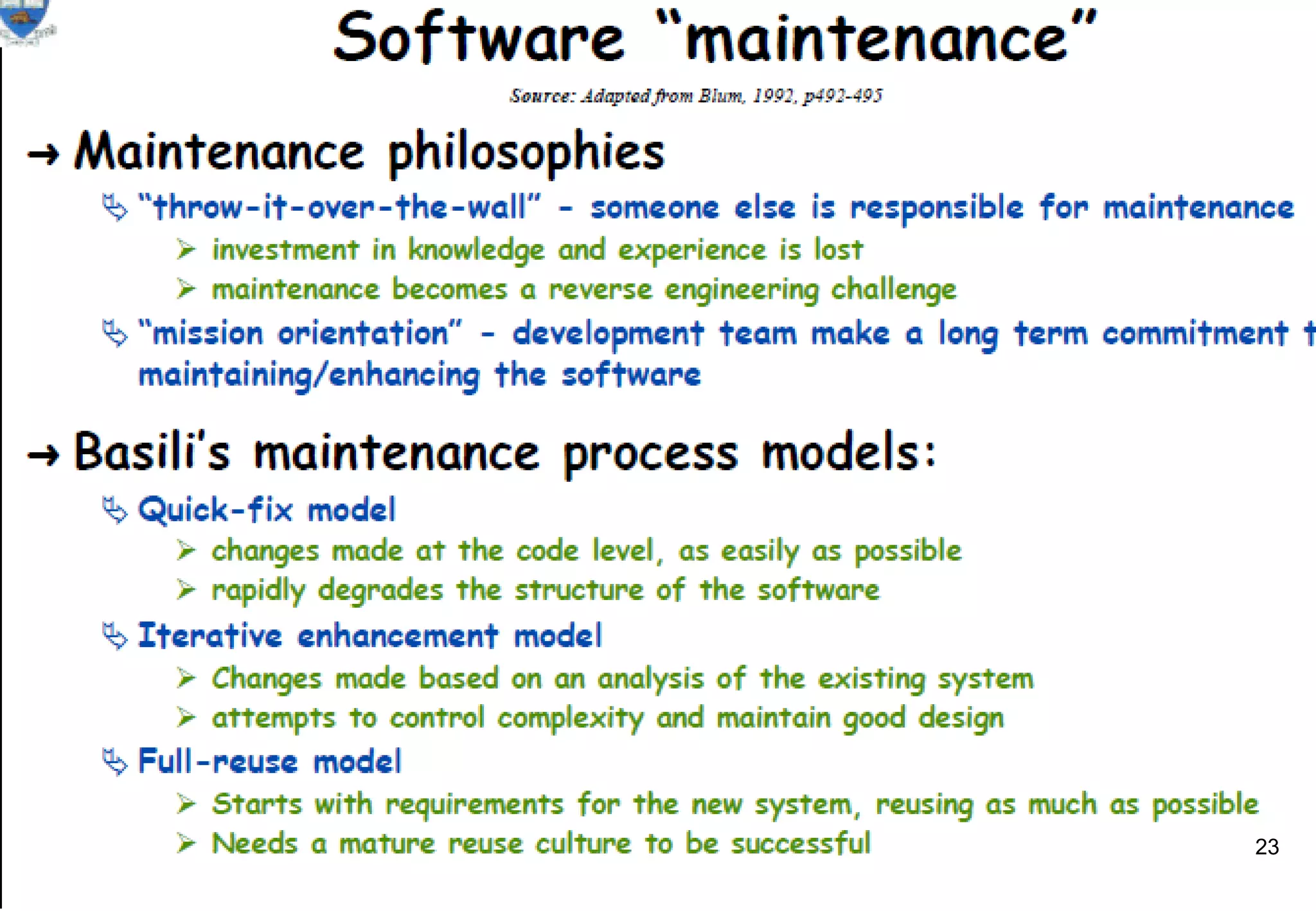
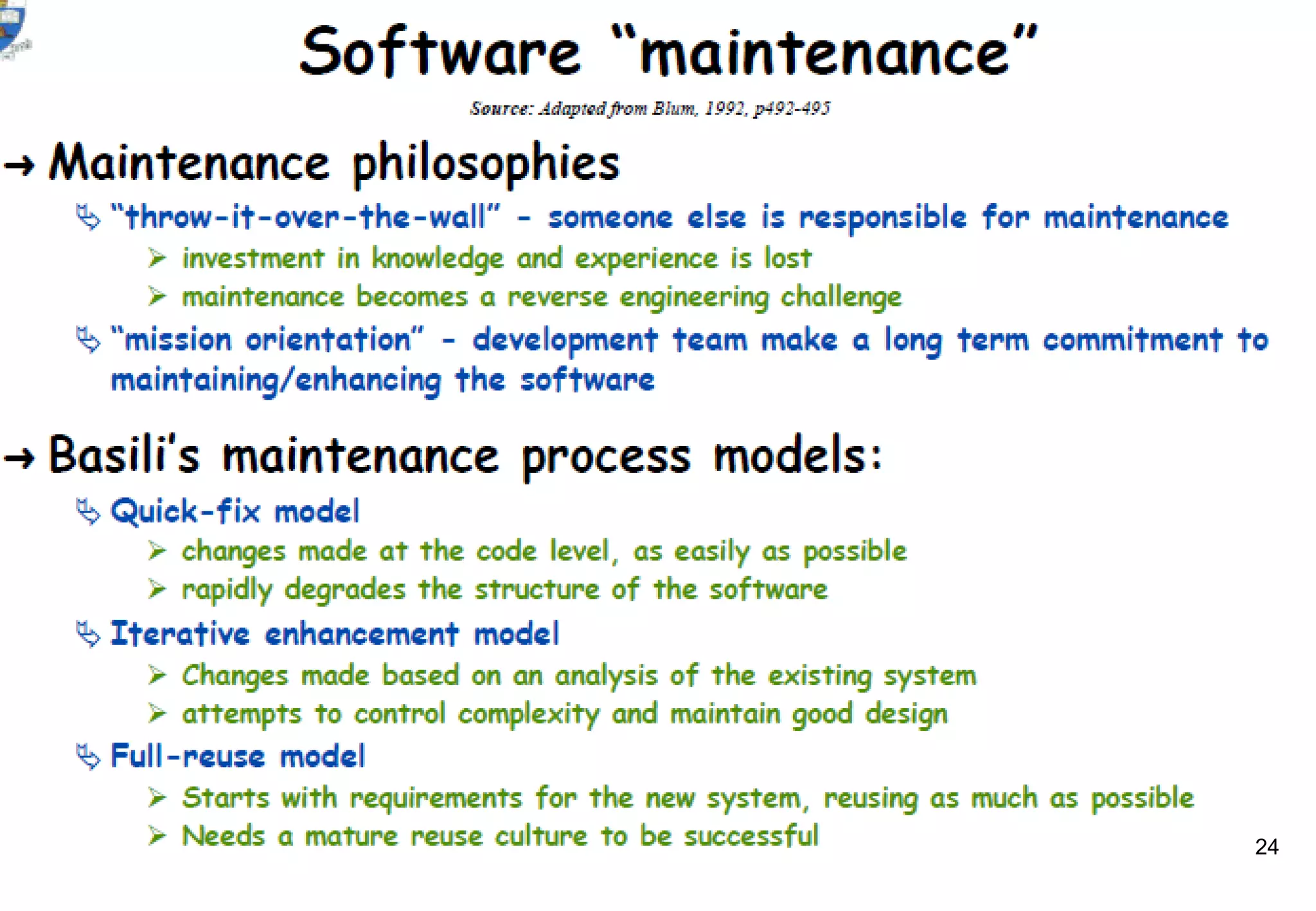
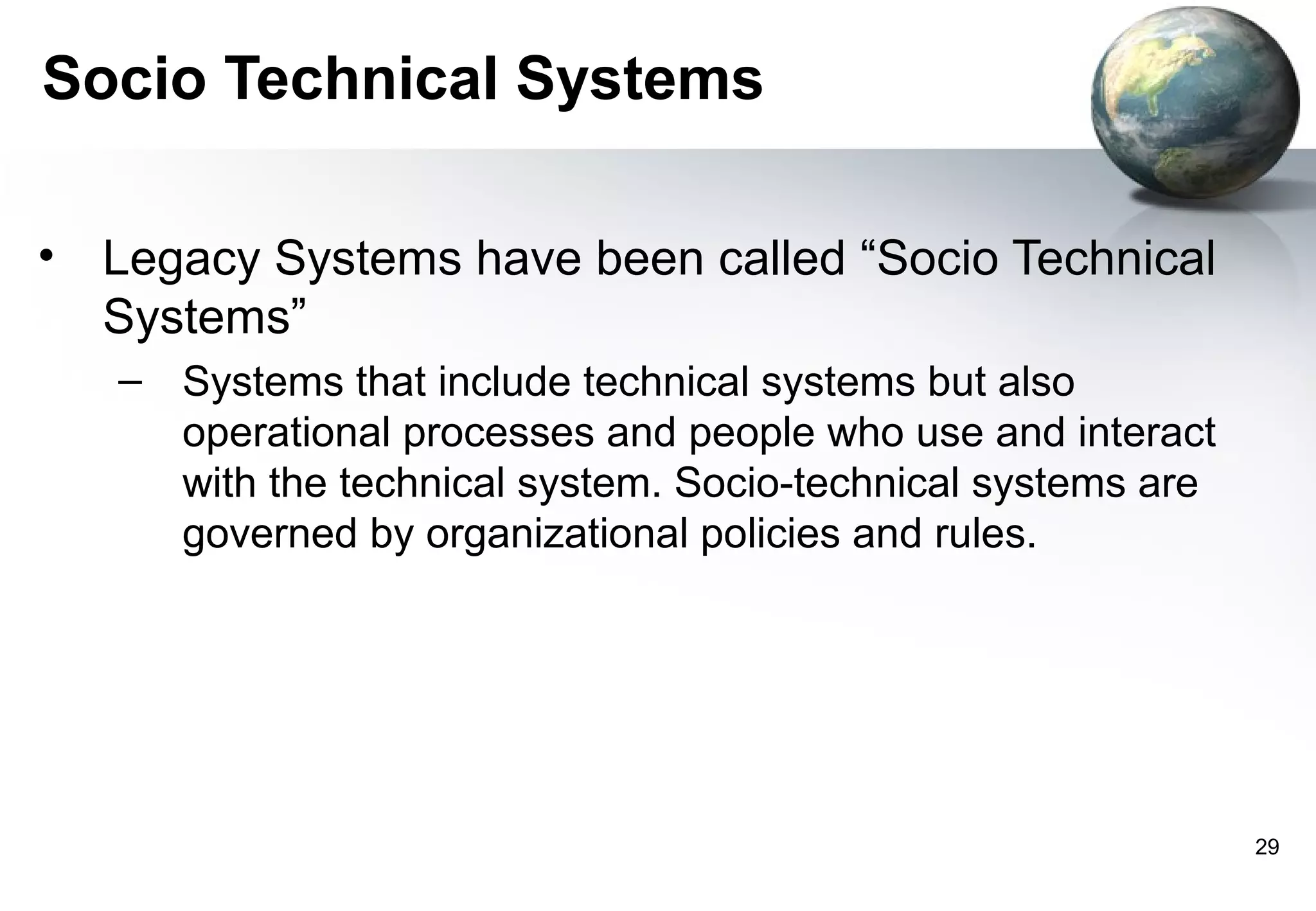
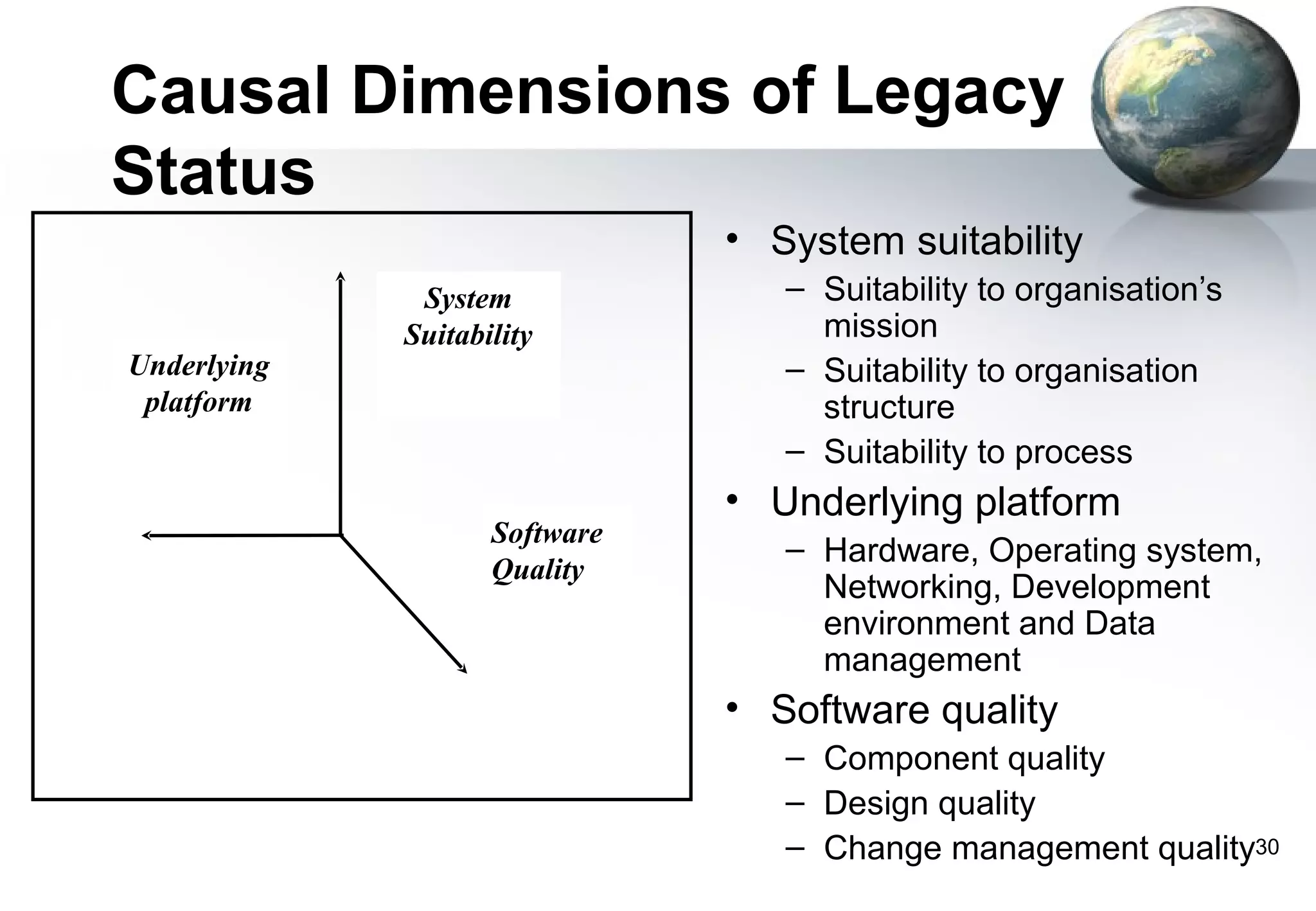
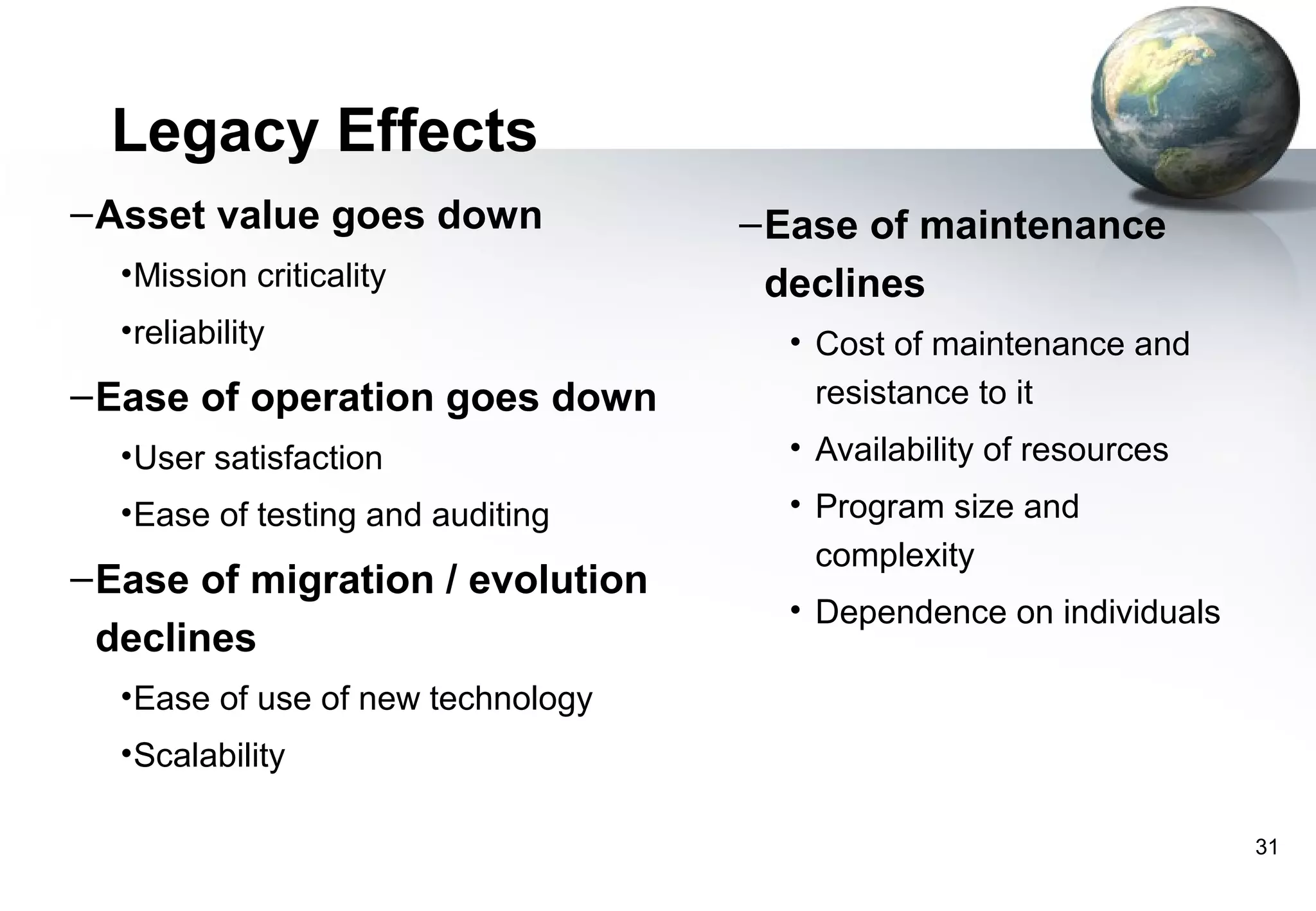
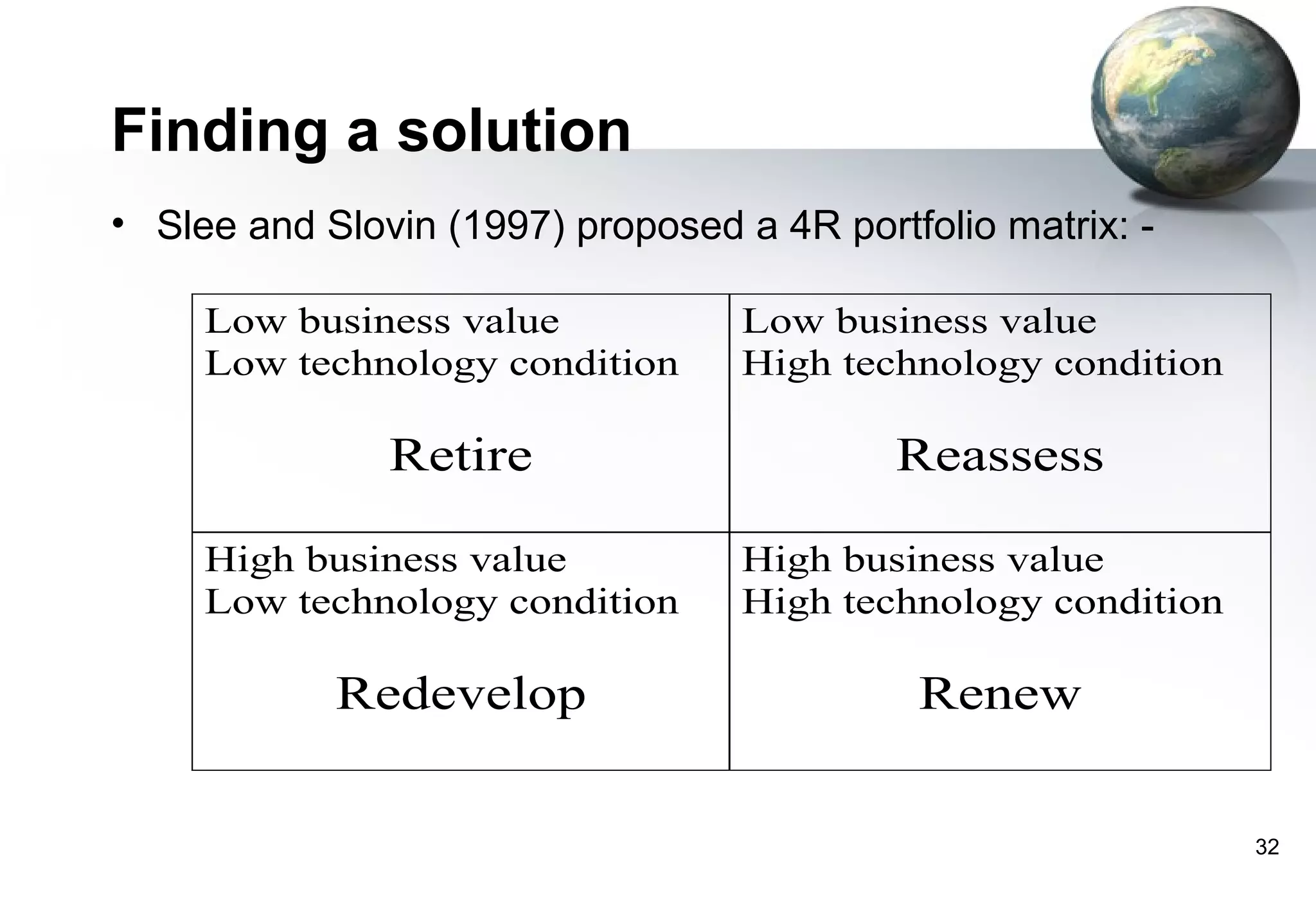
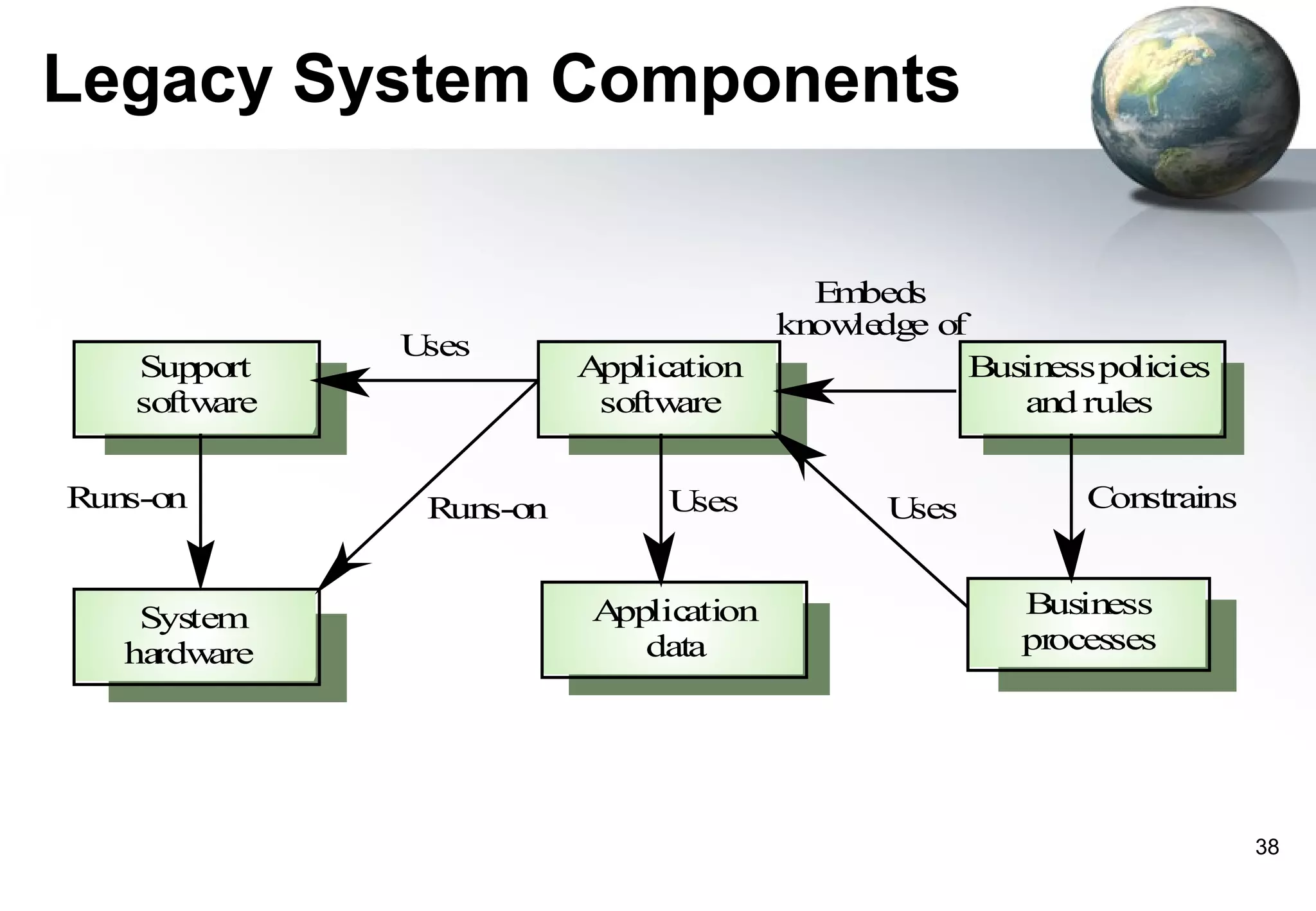
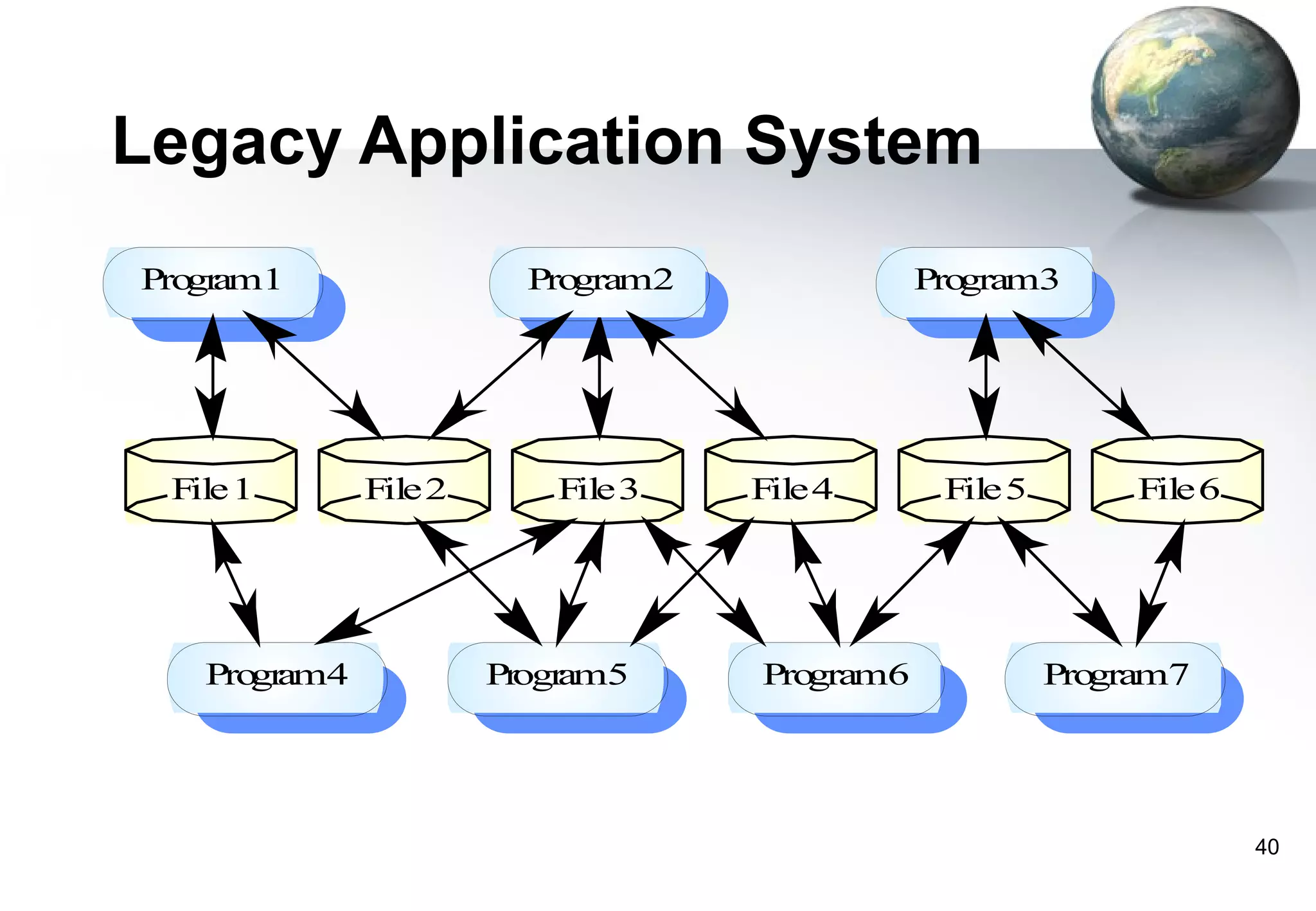
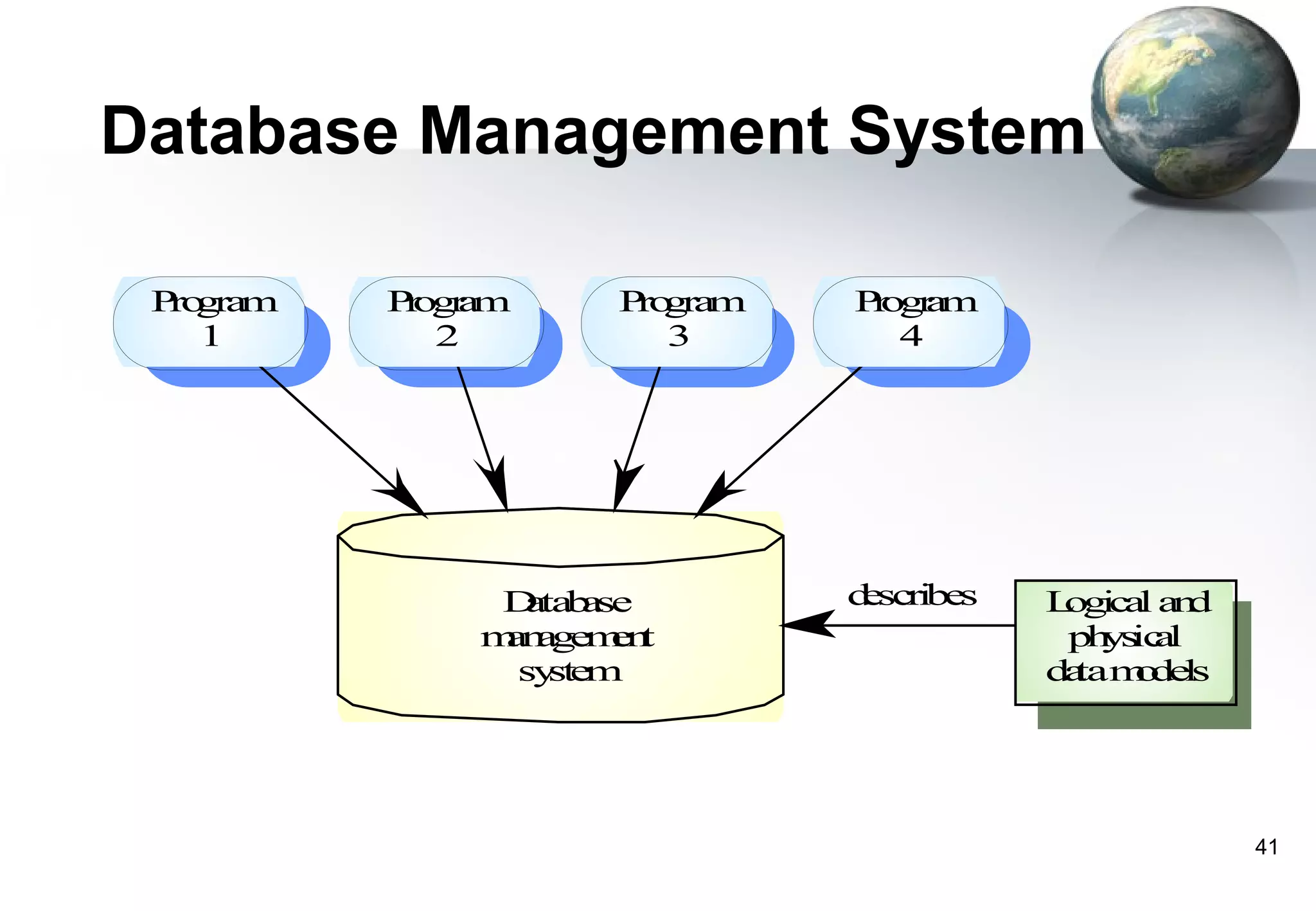
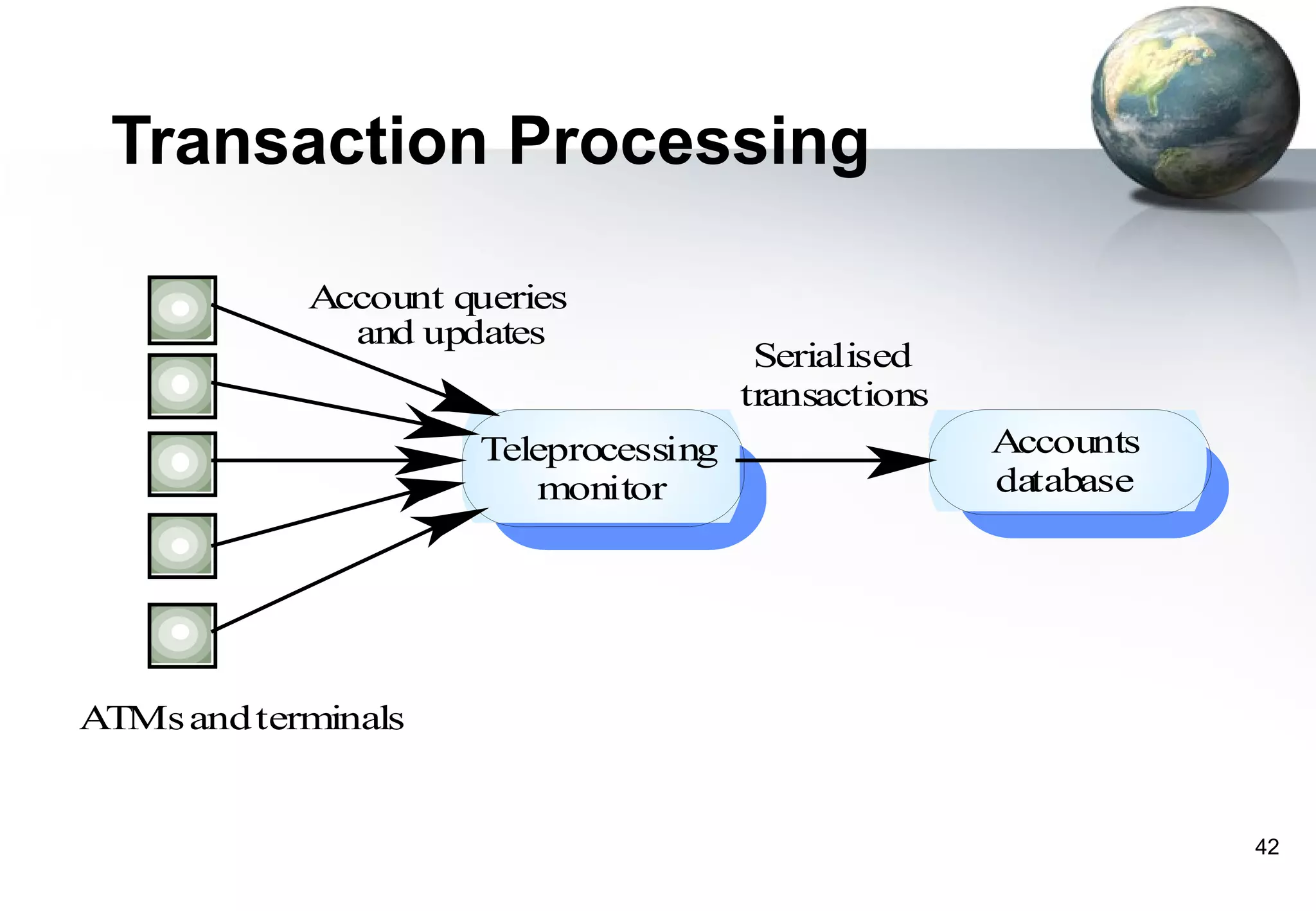
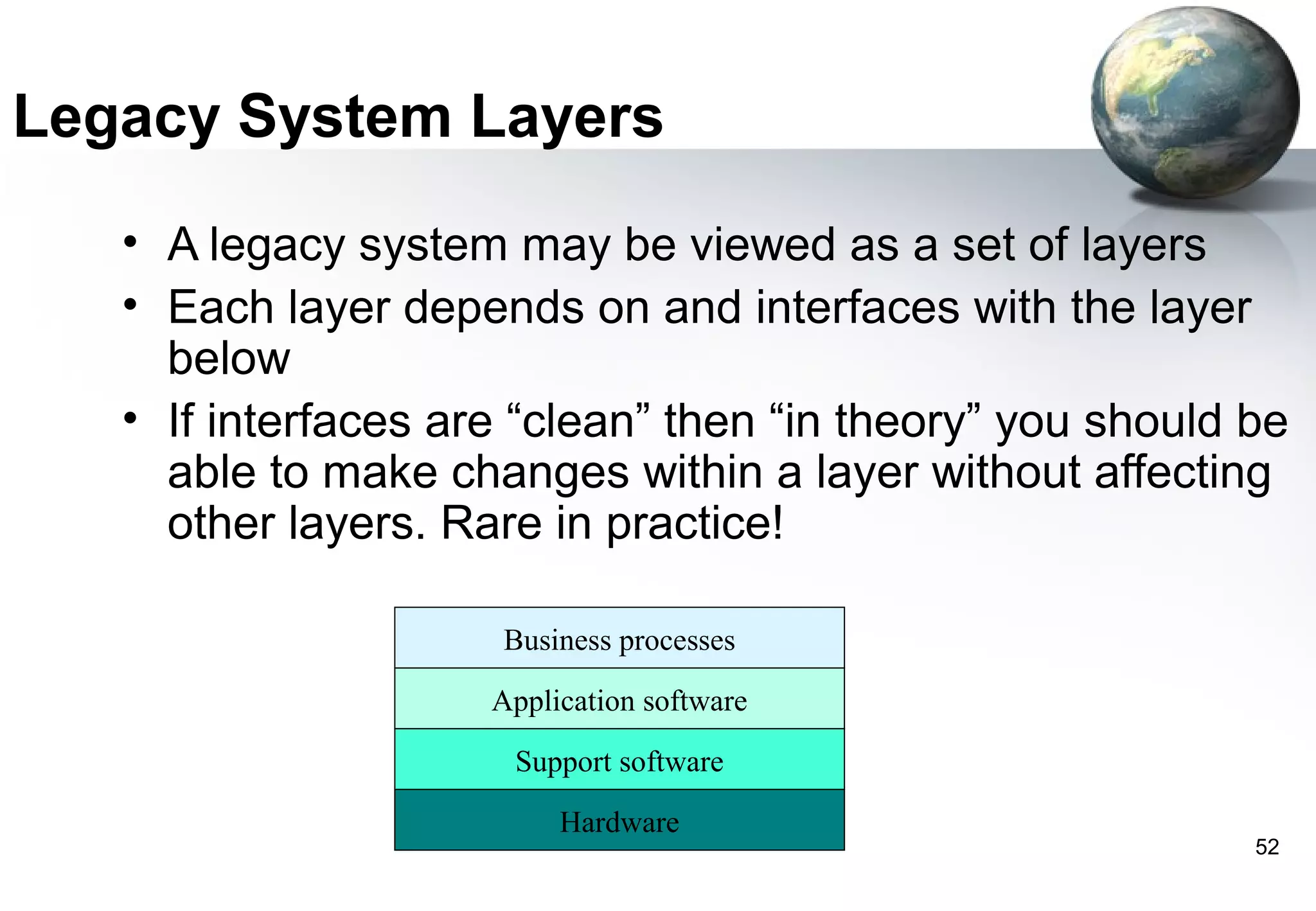
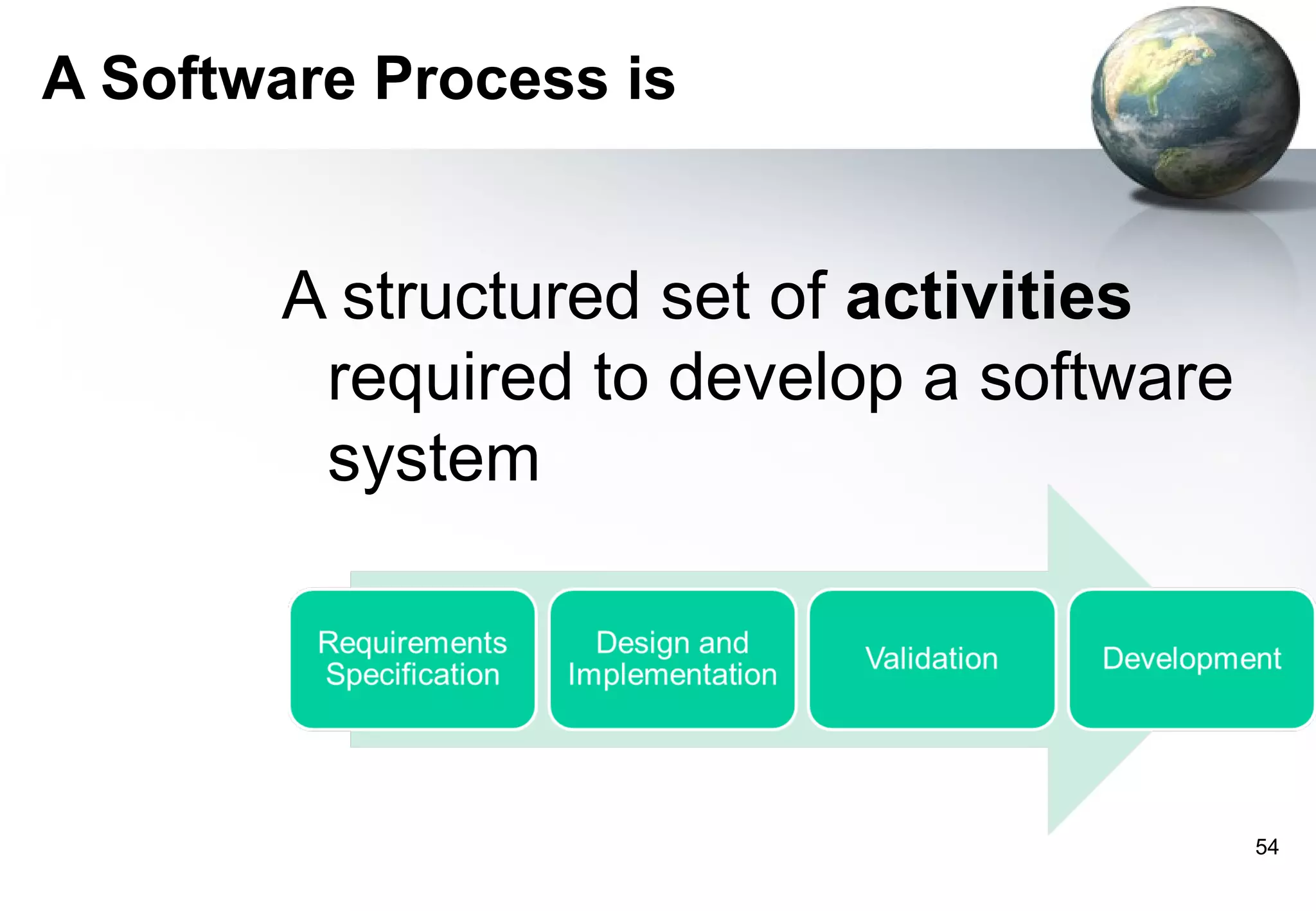
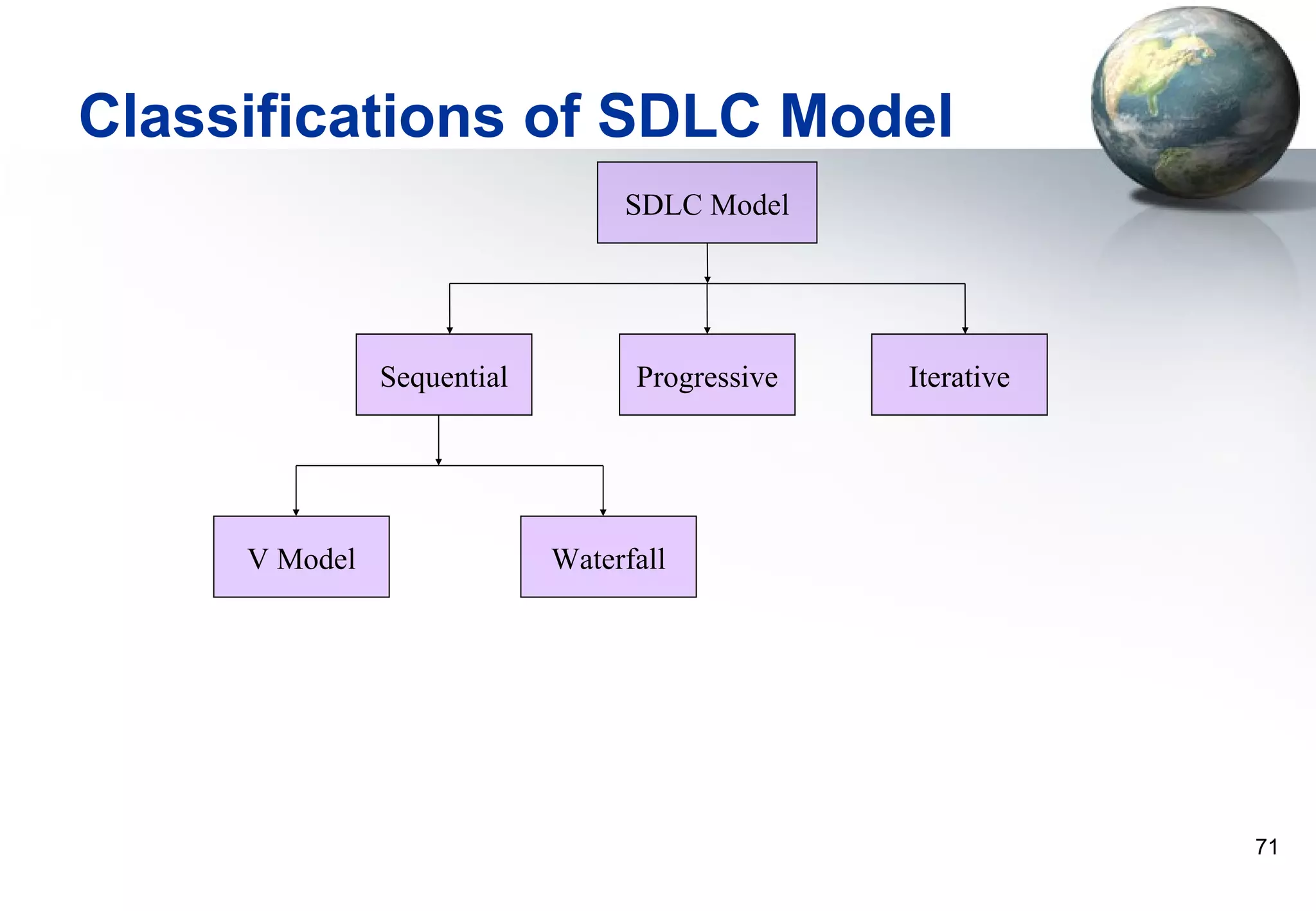
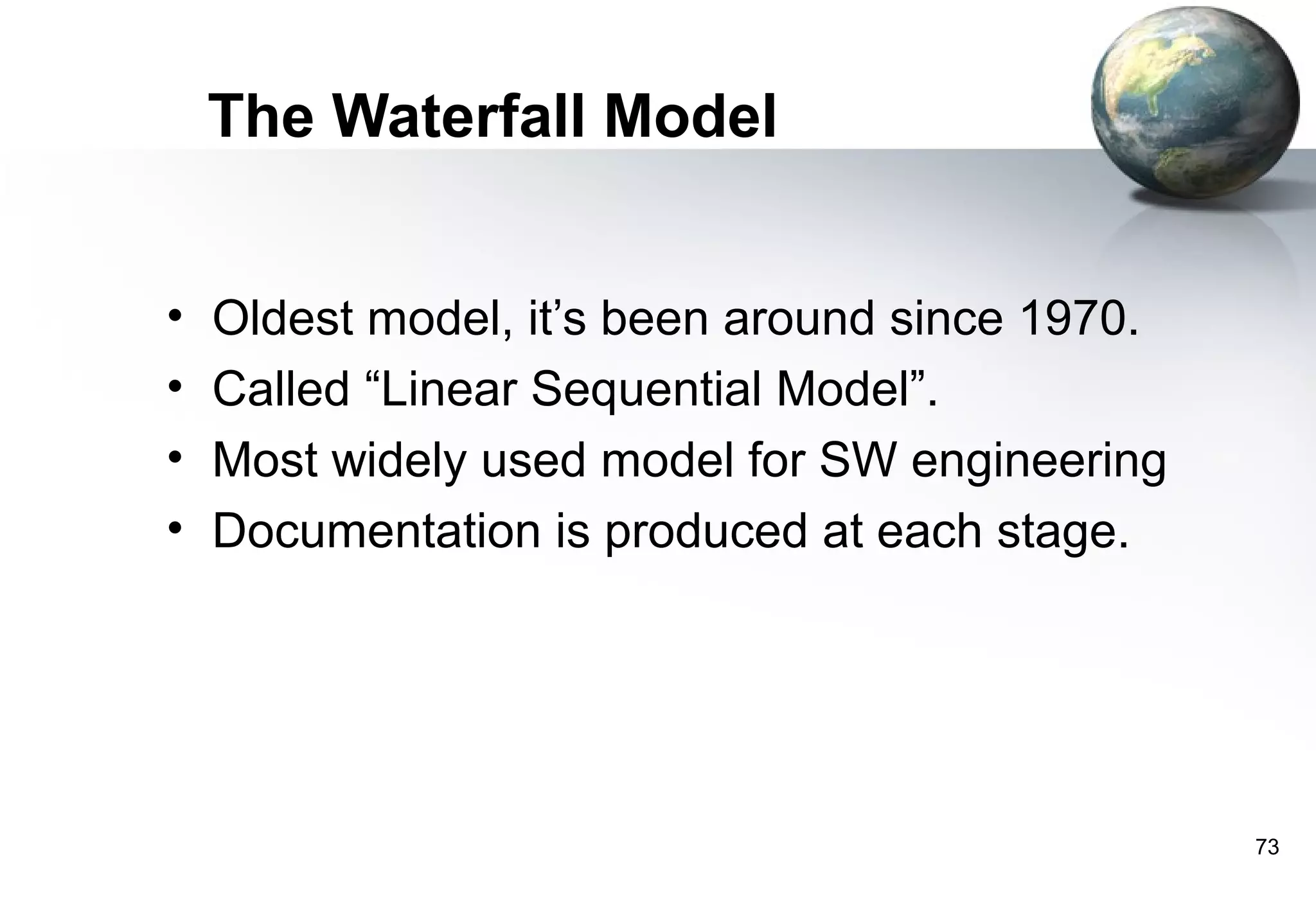
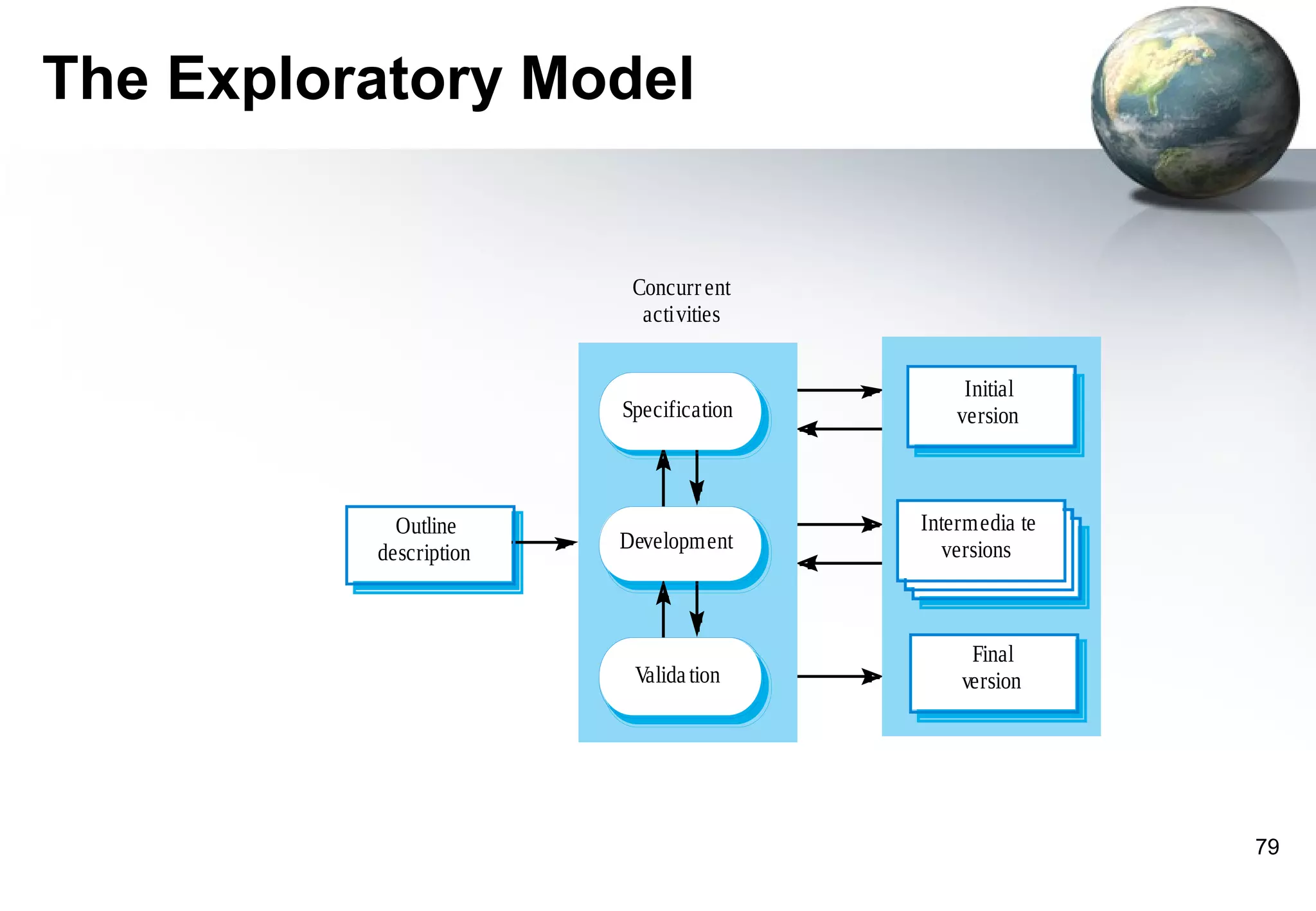
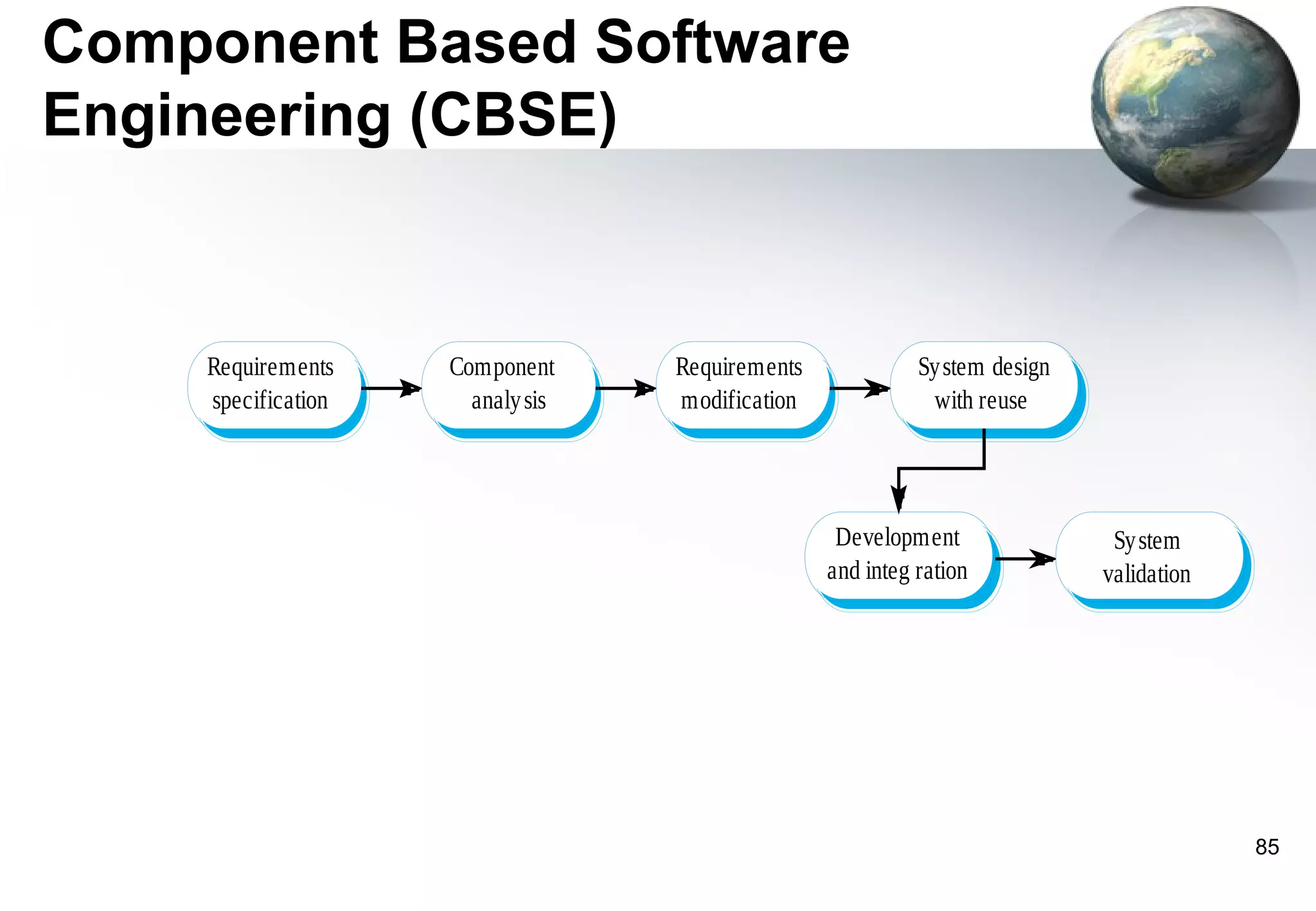
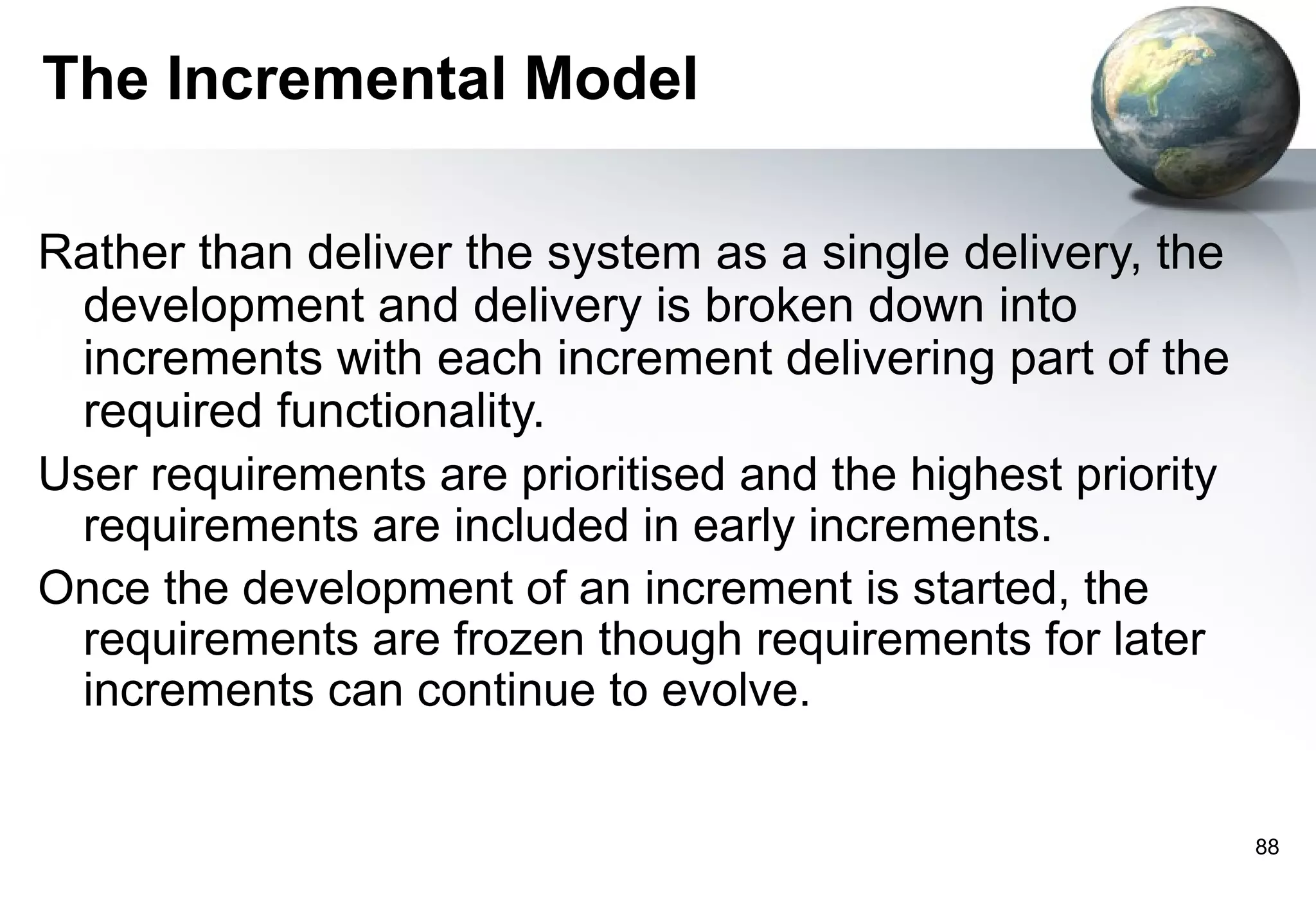
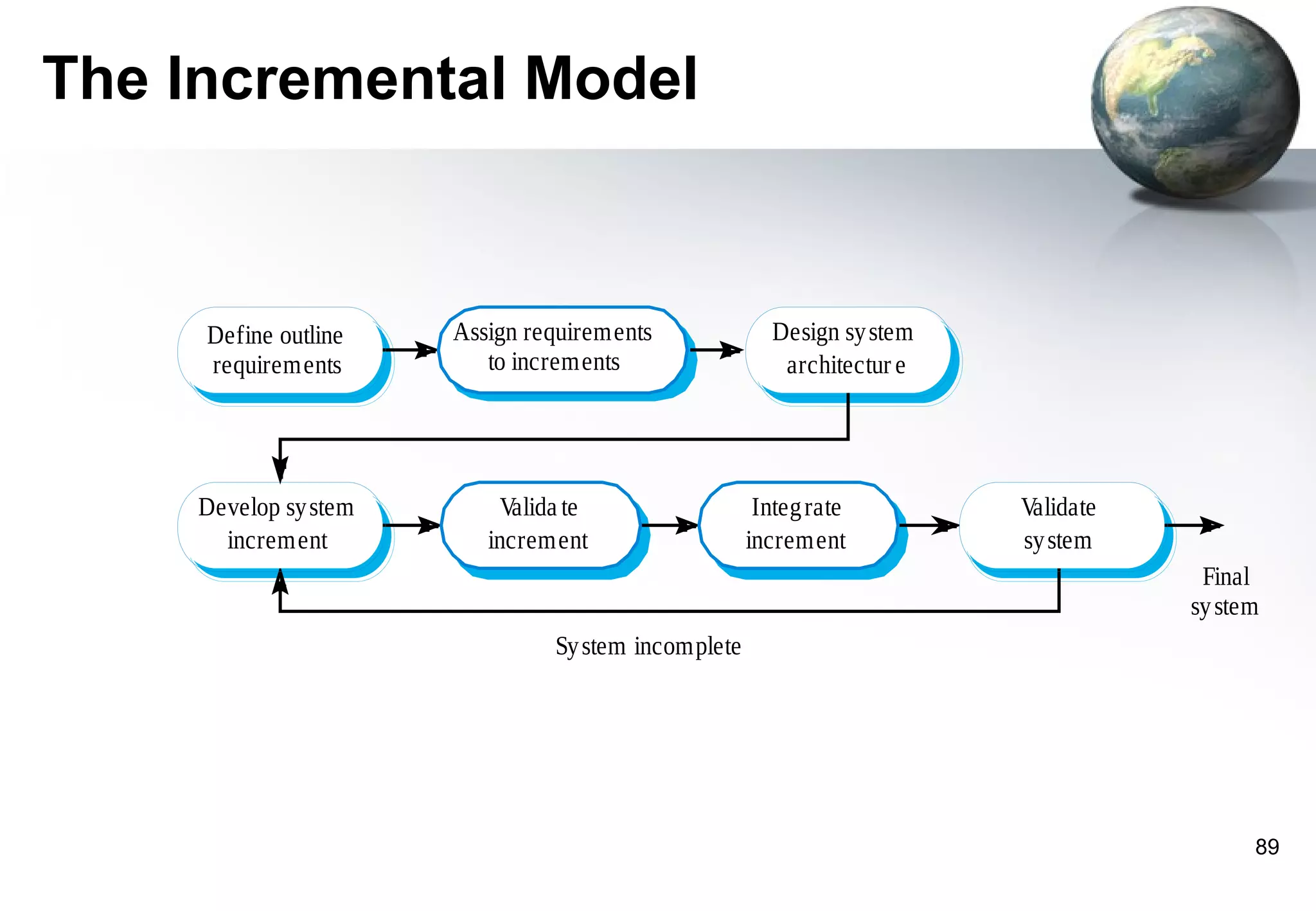
1) Legacy systems are older software systems that have been in use for a long time and are often critical to business operations.
2) They were often developed years ago using outdated technologies and have evolved over many years of customizations and changes.
3) Replacing legacy systems carries significant business risks due to a lack of complete documentation and embedded business rules not formally documented elsewhere. Changing legacy systems can also be very expensive.