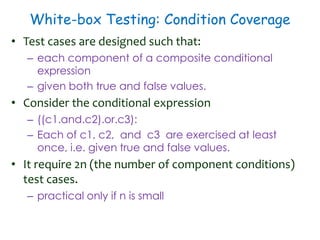
1) Software testing techniques like unit testing, white-box testing, and path testing were discussed. Unit testing involves equivalence partitioning and boundary value analysis. White-box testing requires knowledge of internal structure and aims for statement, branch, and path coverage.
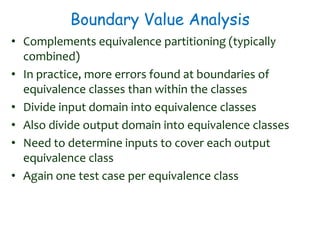
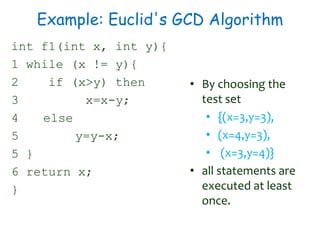
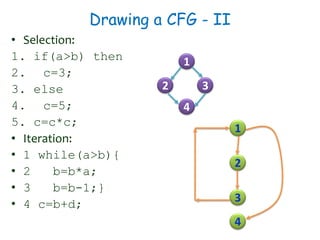
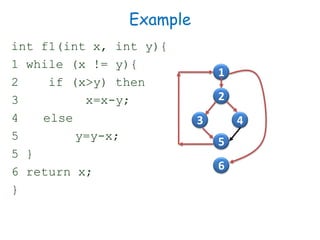
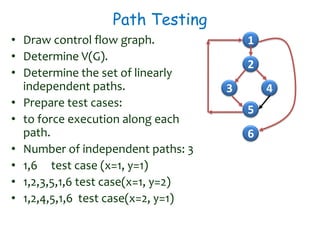
2) Equivalence partitioning divides inputs into classes and one test per class is sufficient. Boundary value analysis tests boundaries of classes. Path coverage requires designing test cases to execute all linearly independent paths in a program.
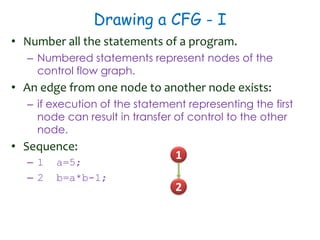
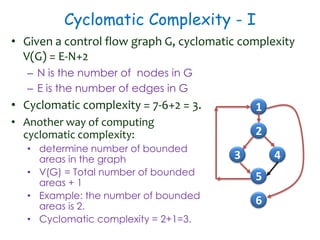
3) Cyclomatic complexity provides a lower bound on number of test cases needed for path coverage. It is computed based on number of edges and nodes in a control flow graph. Automated testing tools can help with regression and UI testing.