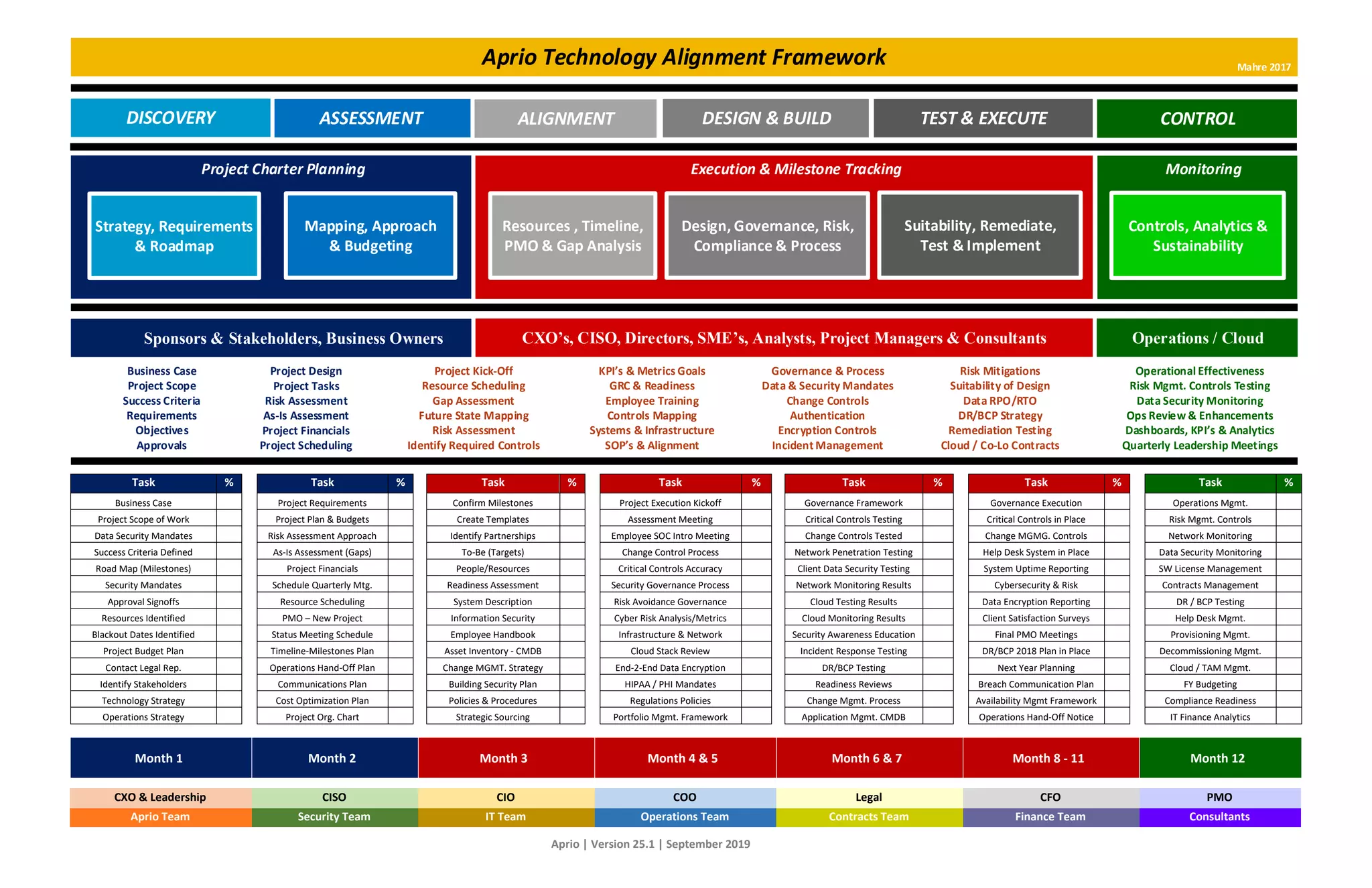
The document outlines a comprehensive project charter focusing on planning, execution, and milestone tracking in technology governance and compliance. It details various aspects including risk management, control implementation, resource scheduling, and data security mandates for successful project management within an organization. Additionally, it emphasizes the need for assessment, monitoring, and continuous improvement throughout the project's lifecycle.