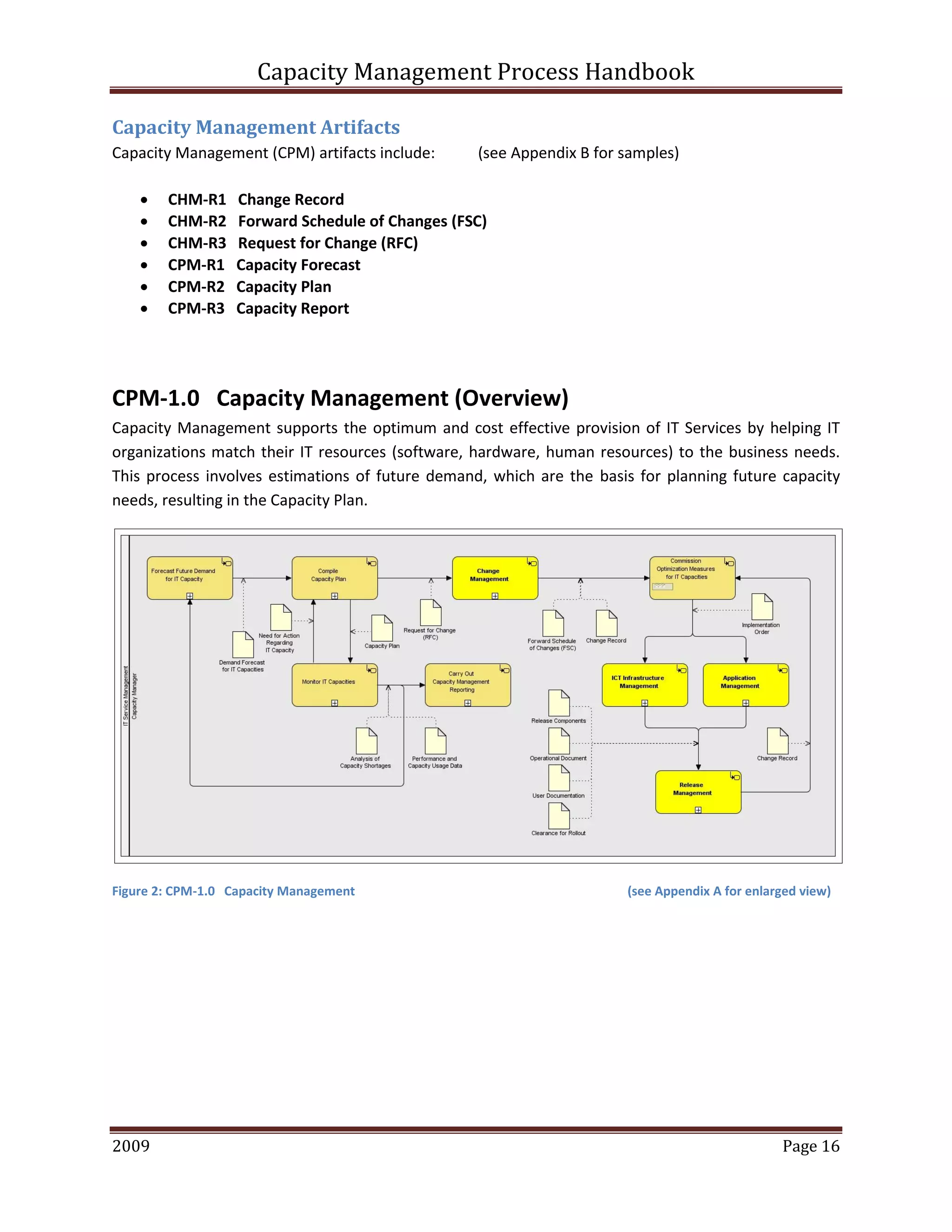
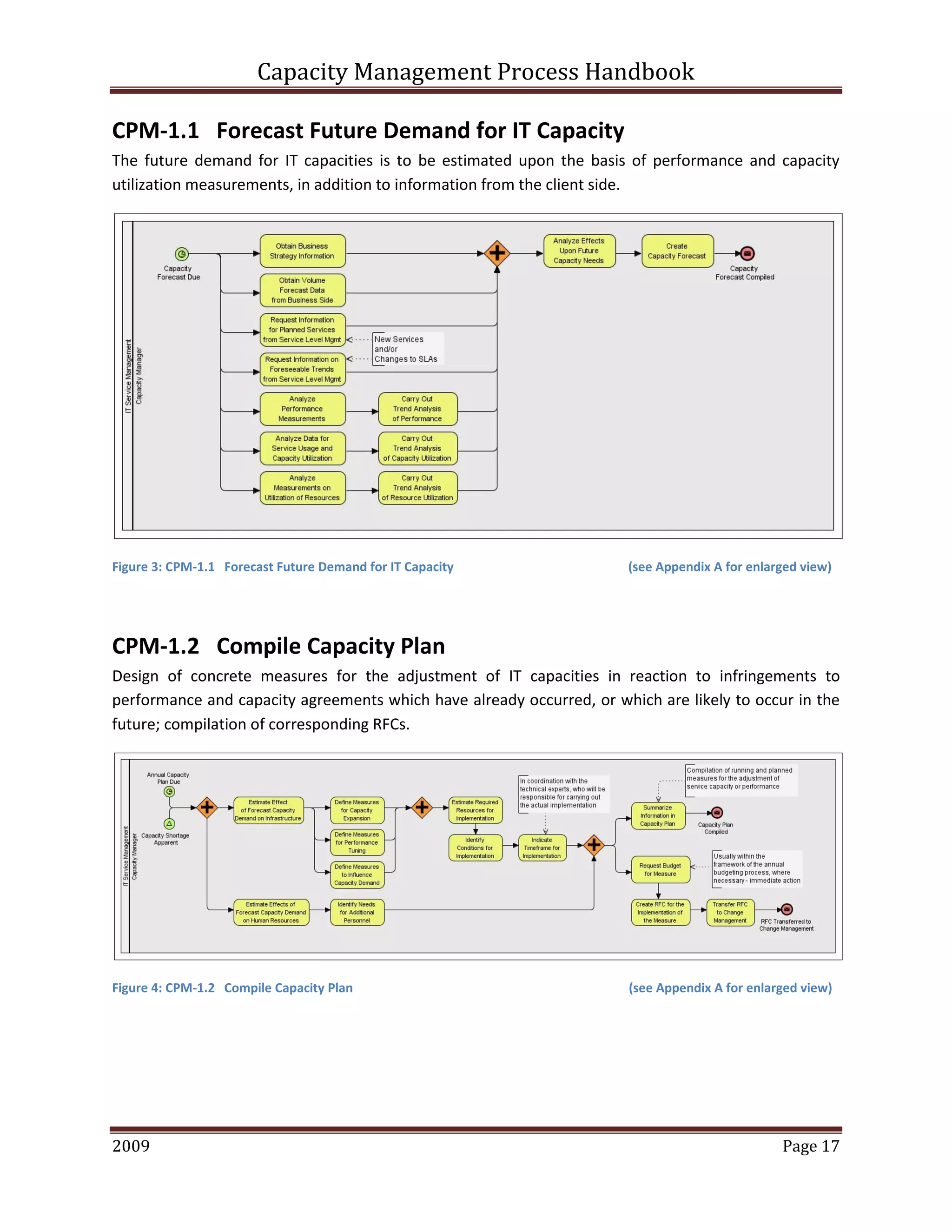
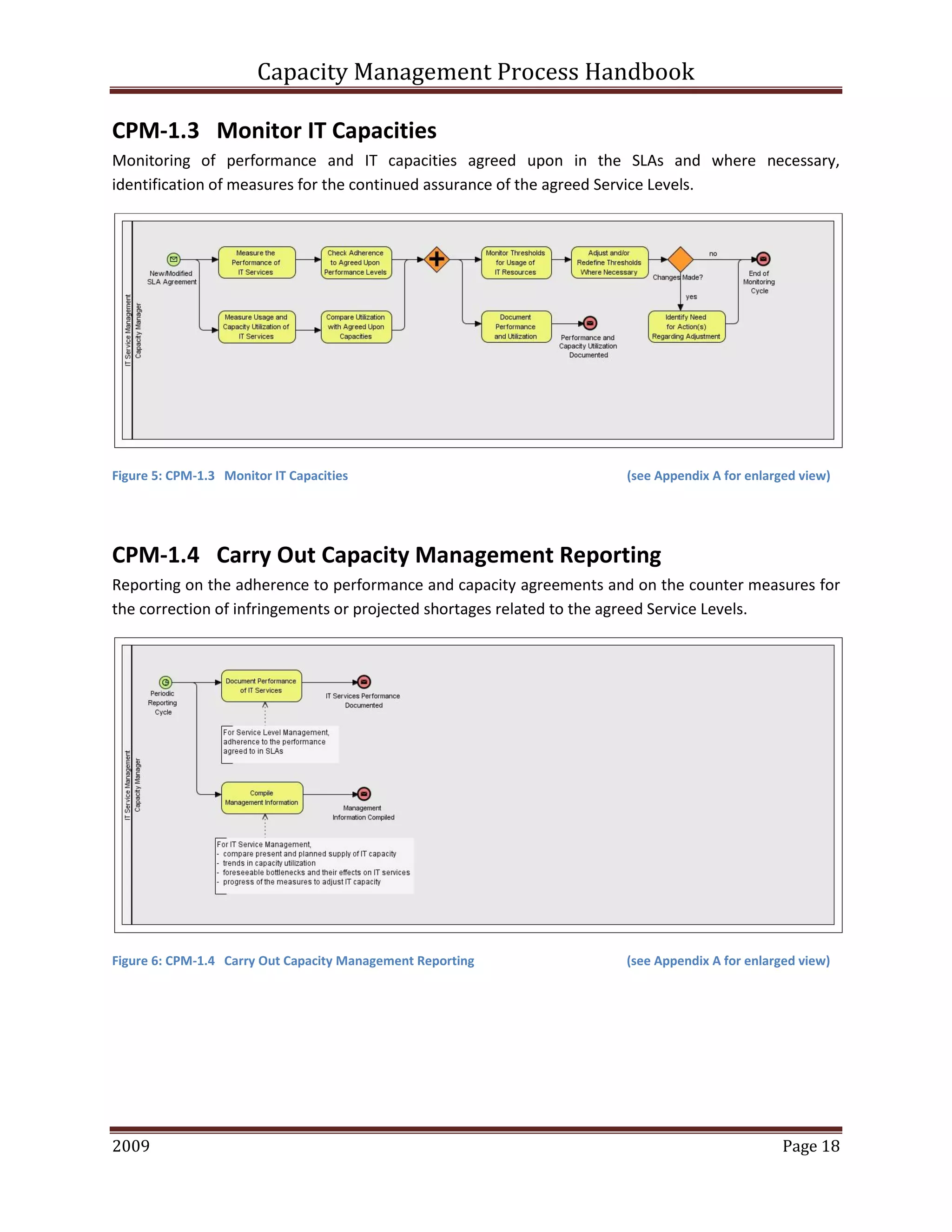
This document provides an overview of capacity management processes and concepts. It discusses key ITIL processes like incident management, problem management, change management and others. It then focuses on capacity management, describing the different levels of capacity planning from business to service to component. The document outlines the key activities, roles and artifacts of a capacity management process. It also discusses concepts like capacity planning, storage capacity planning and capacity models.